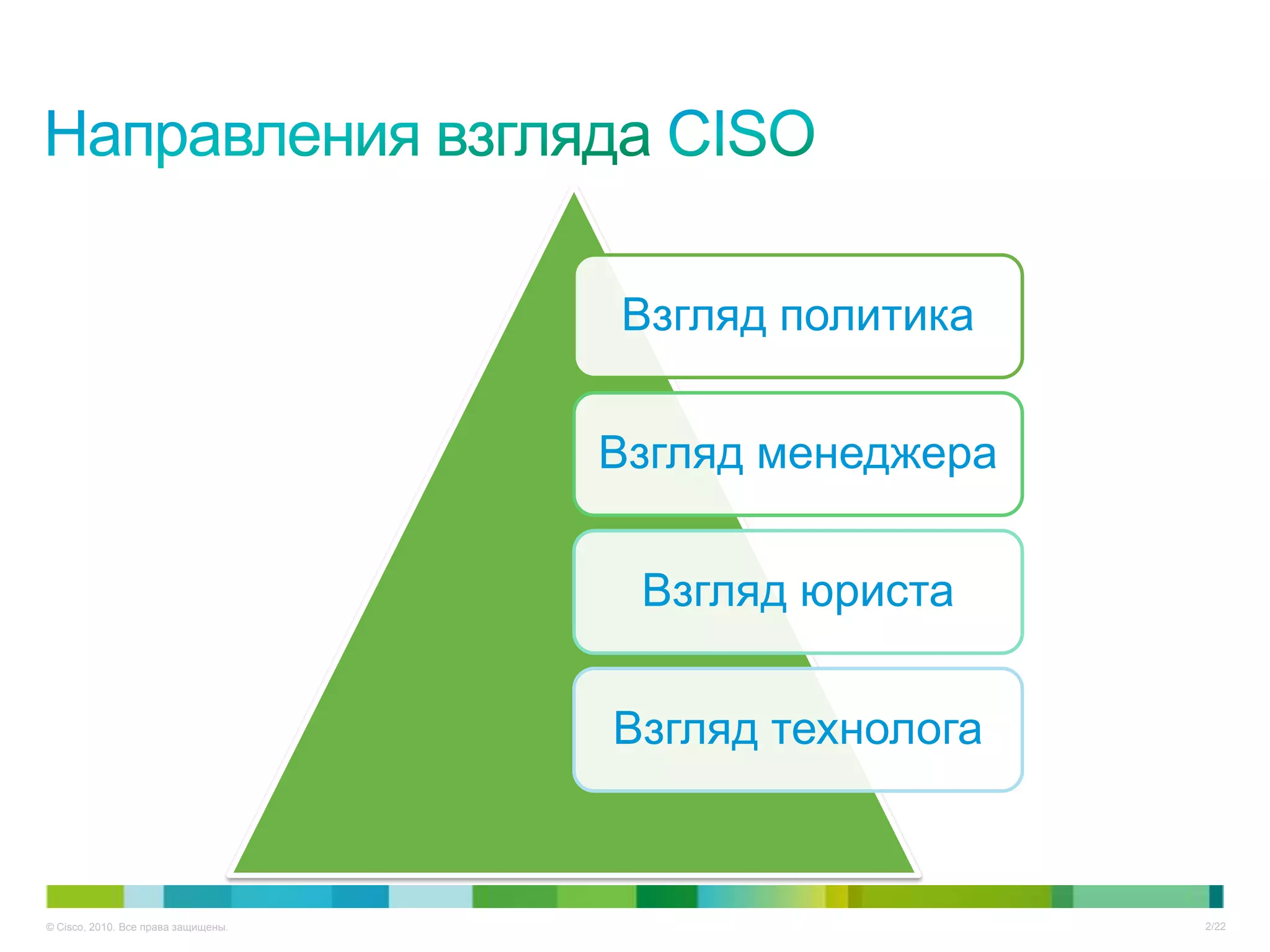
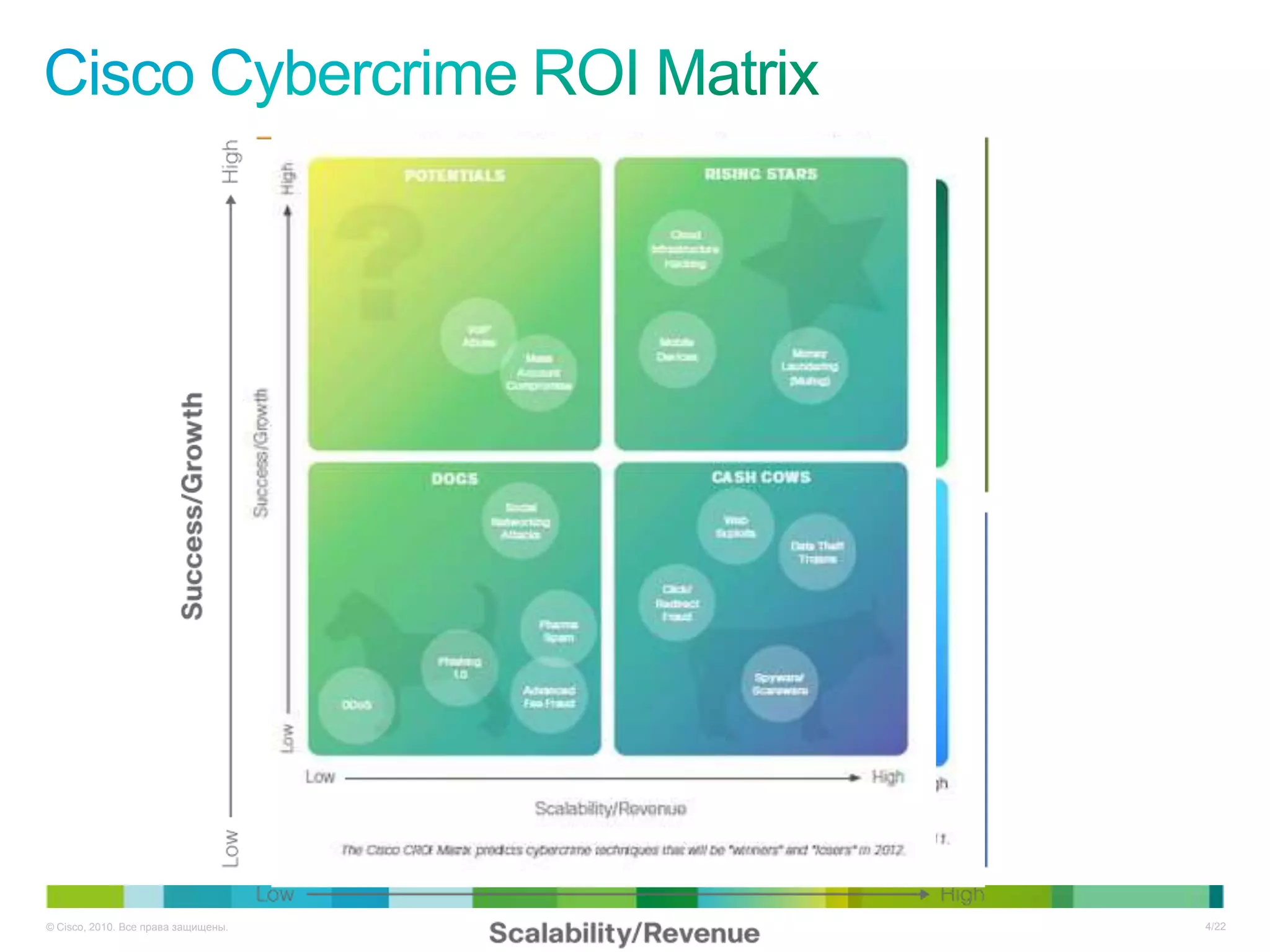
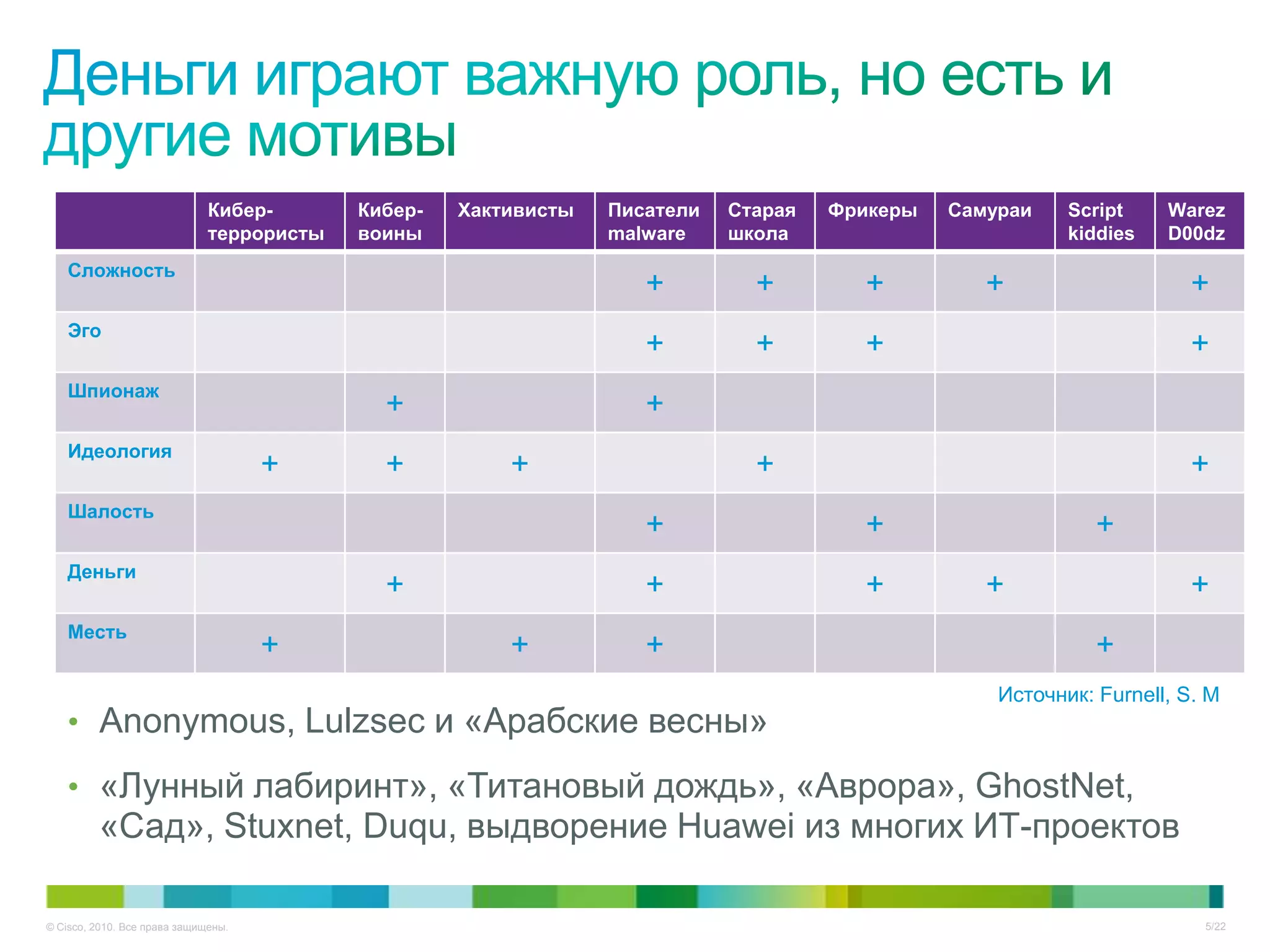
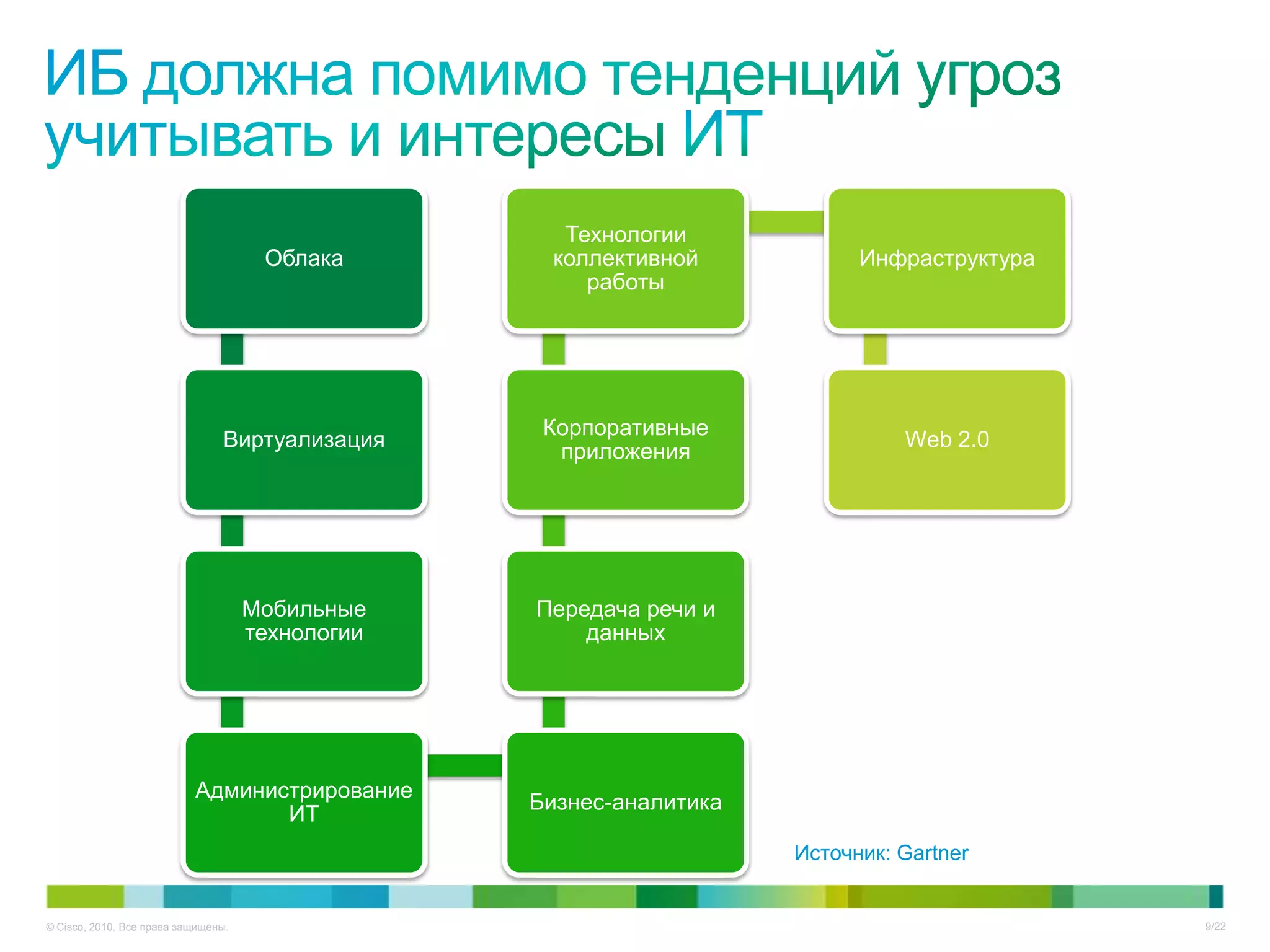
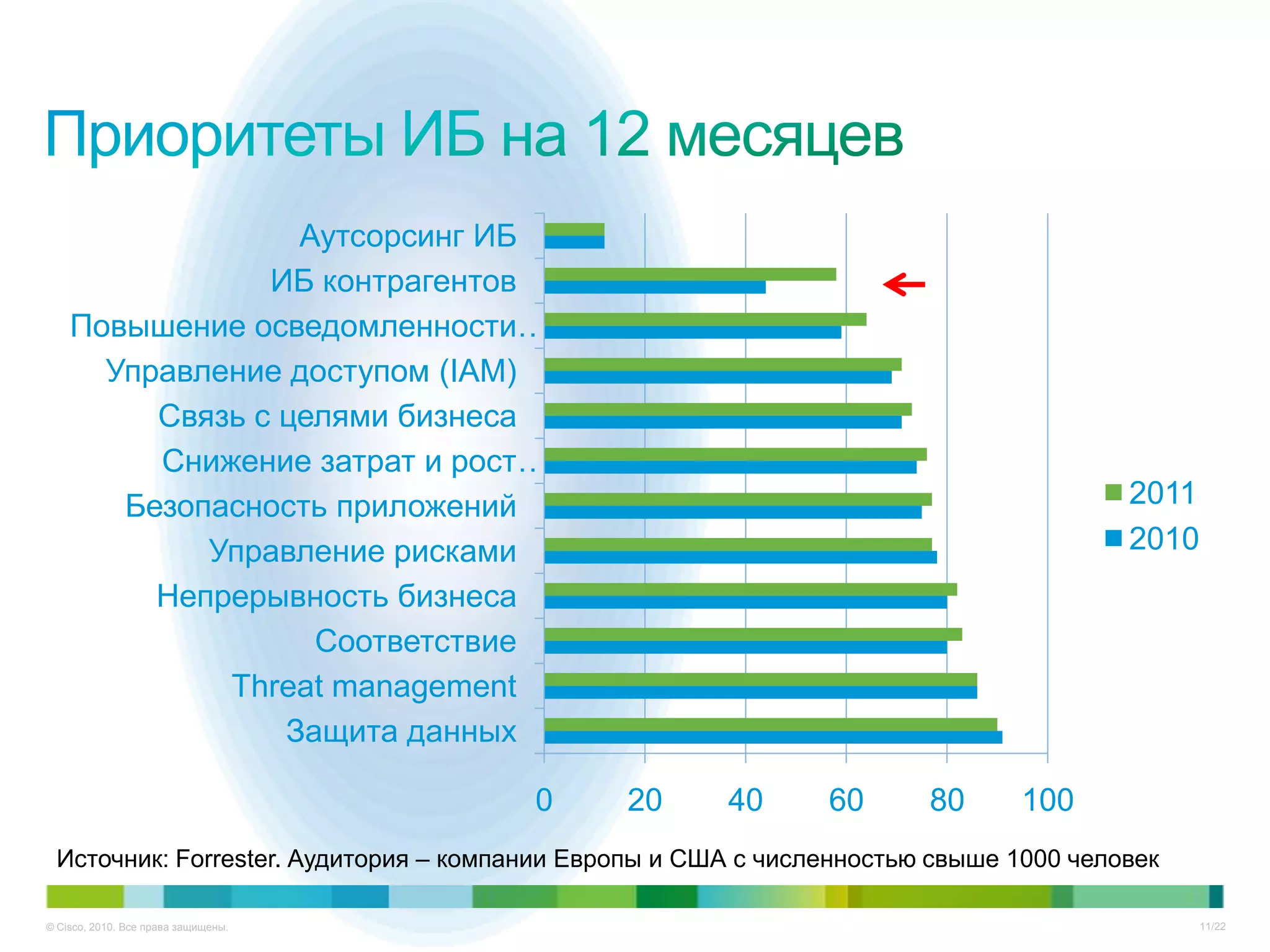
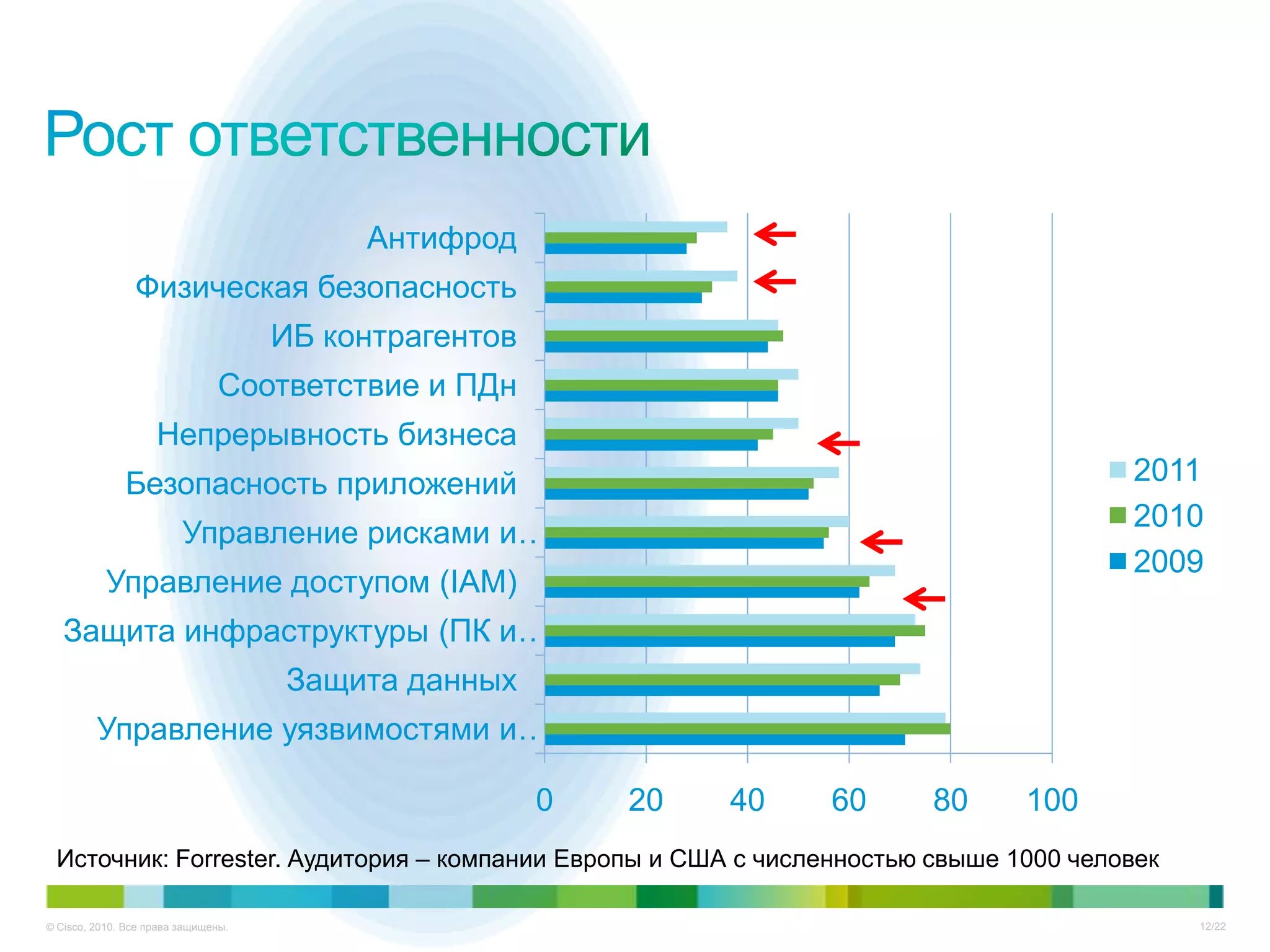
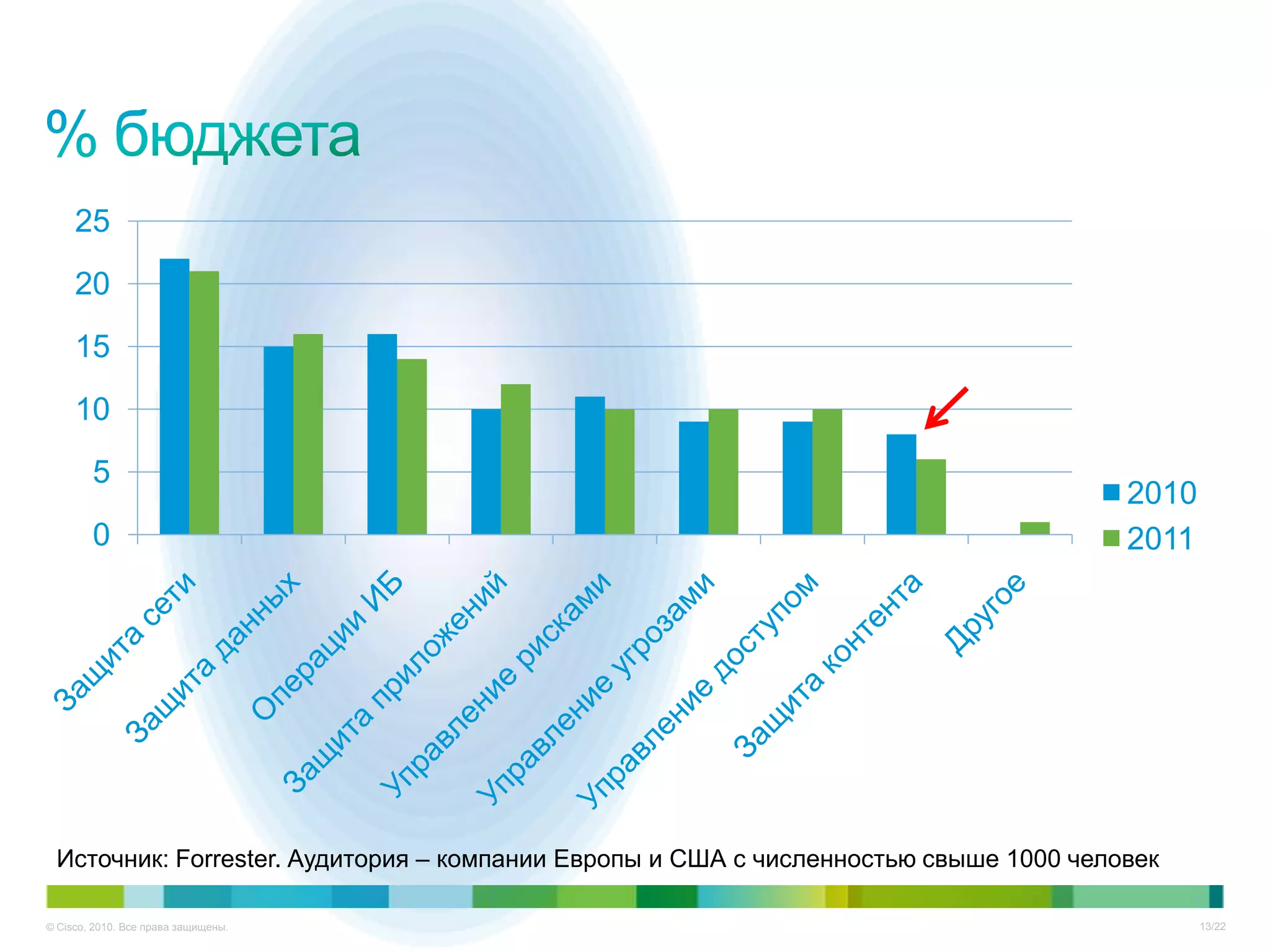
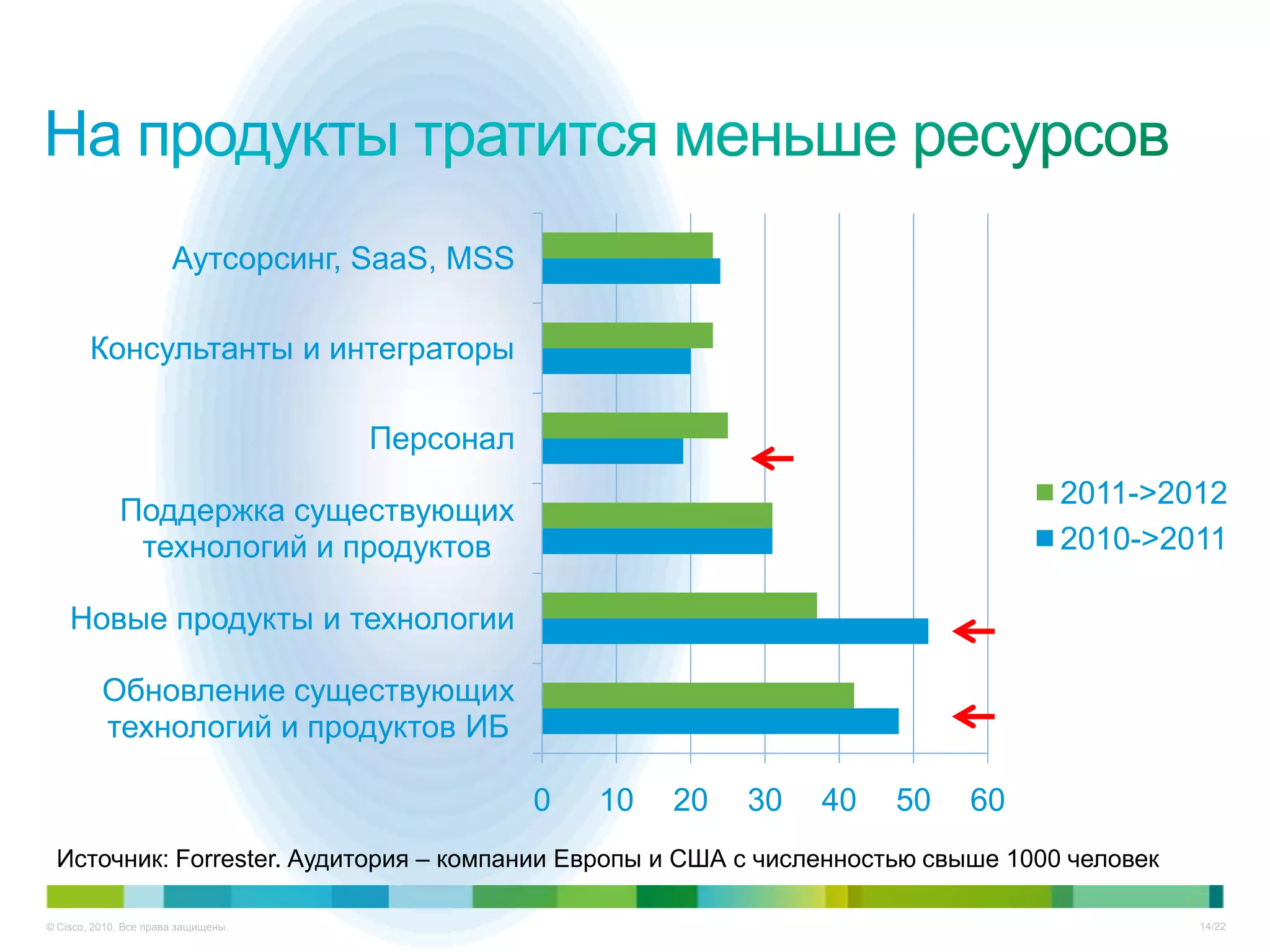
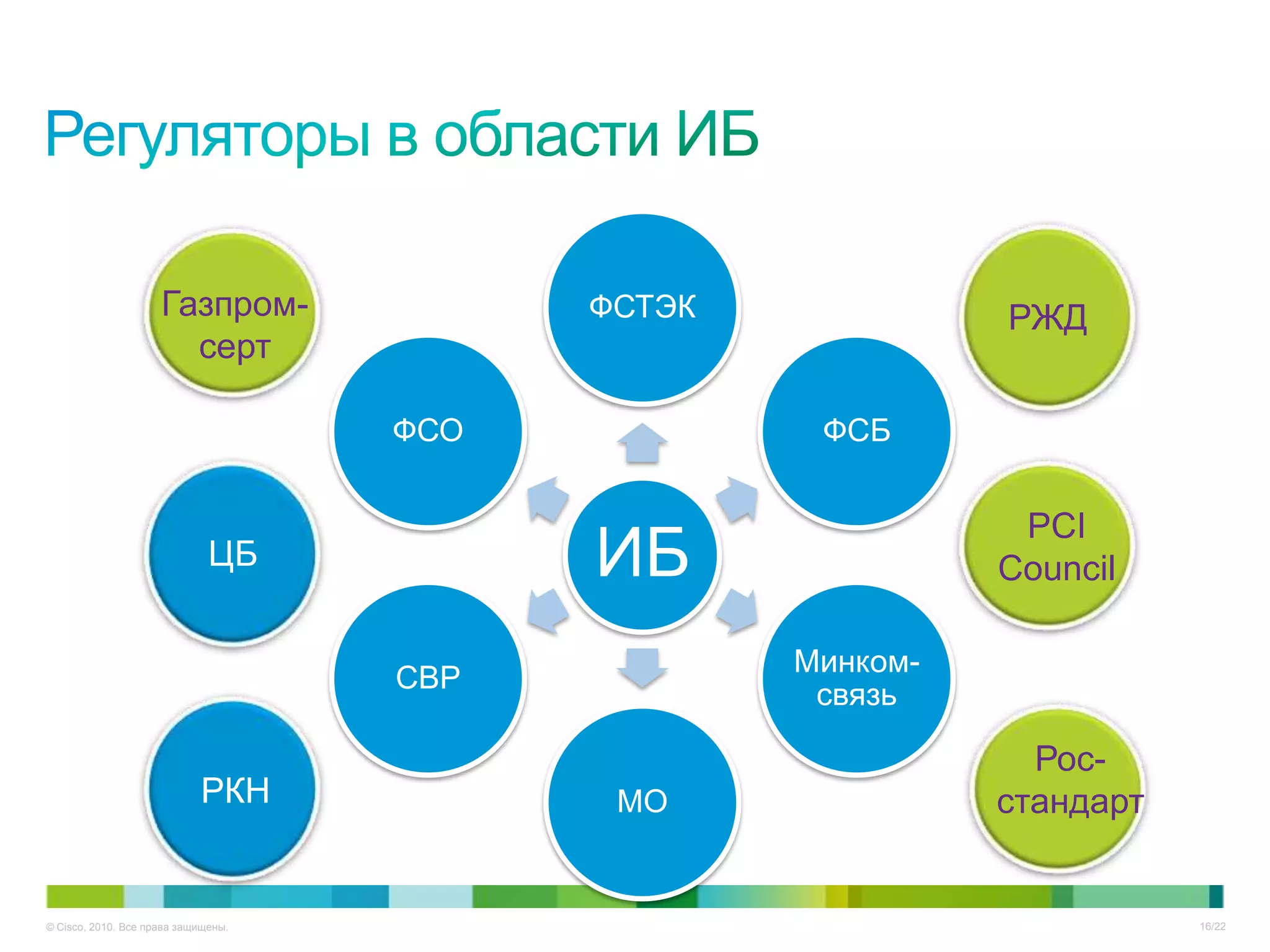
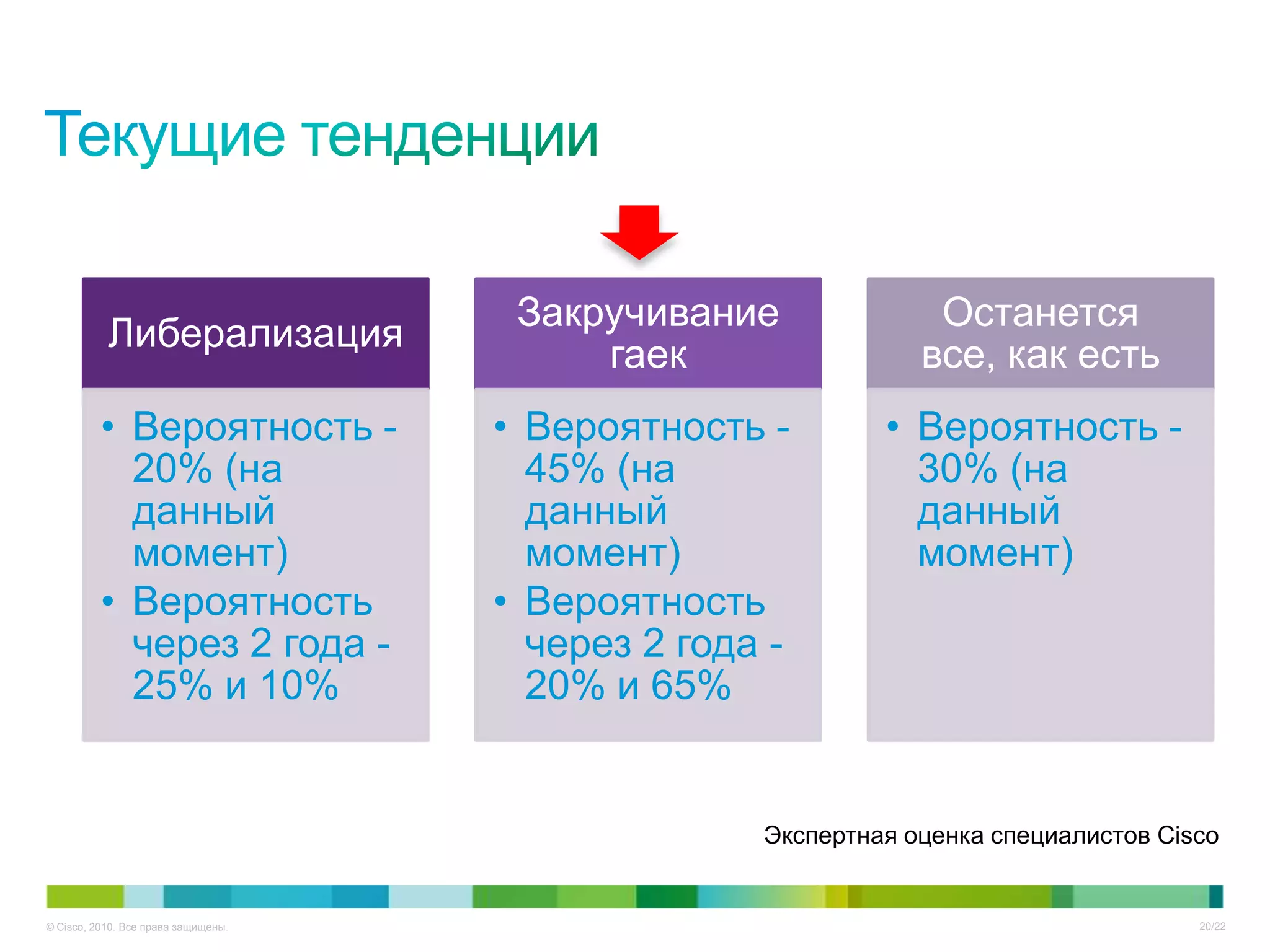
Документ описывает ключевые тенденции и угрозы в области информационной безопасности для CISO в 2012-2013 годах, включая рост атак на критические инфраструктуры и малый бизнес. Основное внимание уделяется новым угрозам, связанным с киберпреступностью, а также необходимости специальных подходов к защите облачных технологий и виртуализации. Отмечается важность соответствия новым законодательным требованиям и повышенной ответственности организаций в области безопасности данных.