Embed presentation
Download as PDF, PPTX





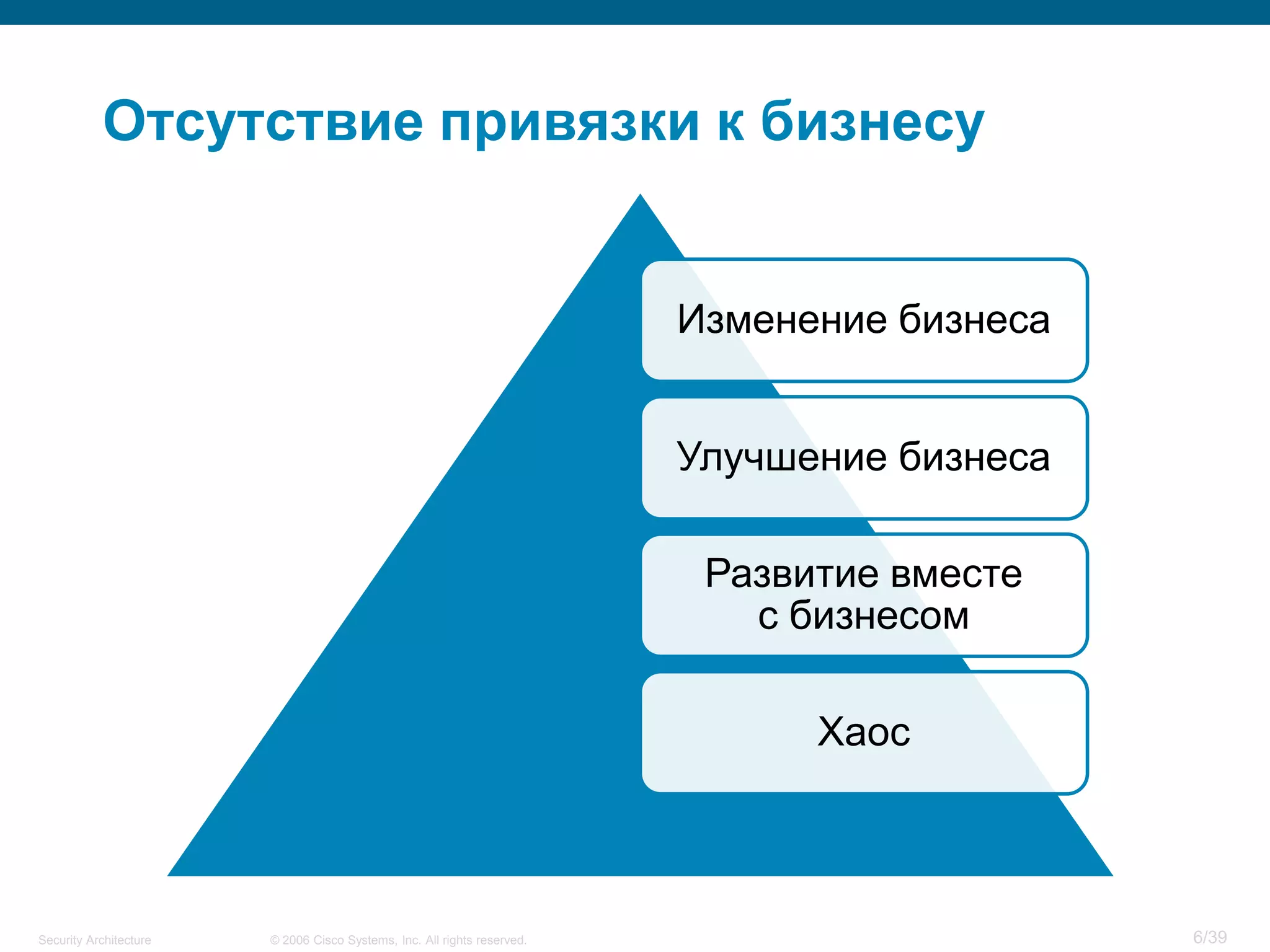

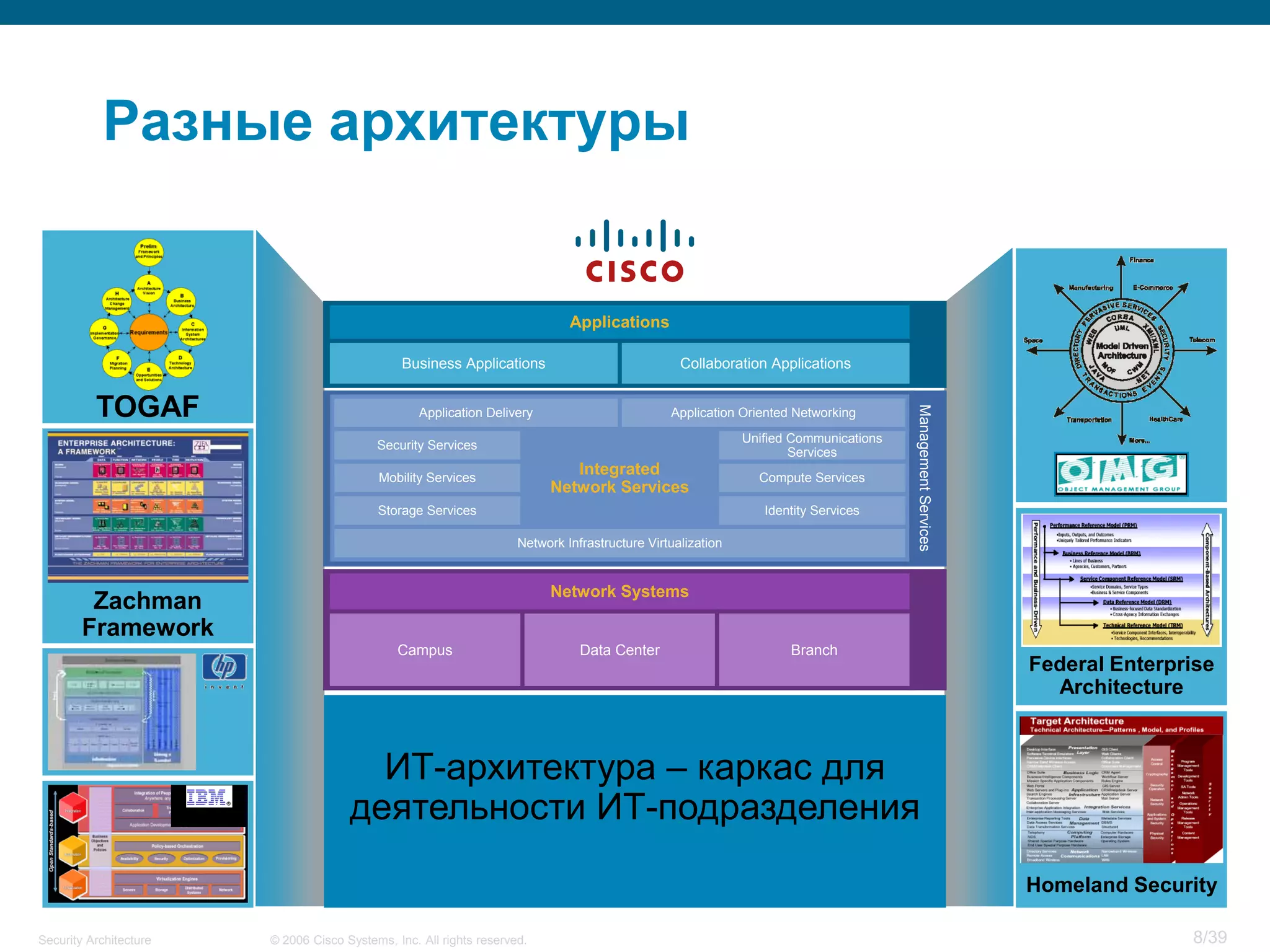






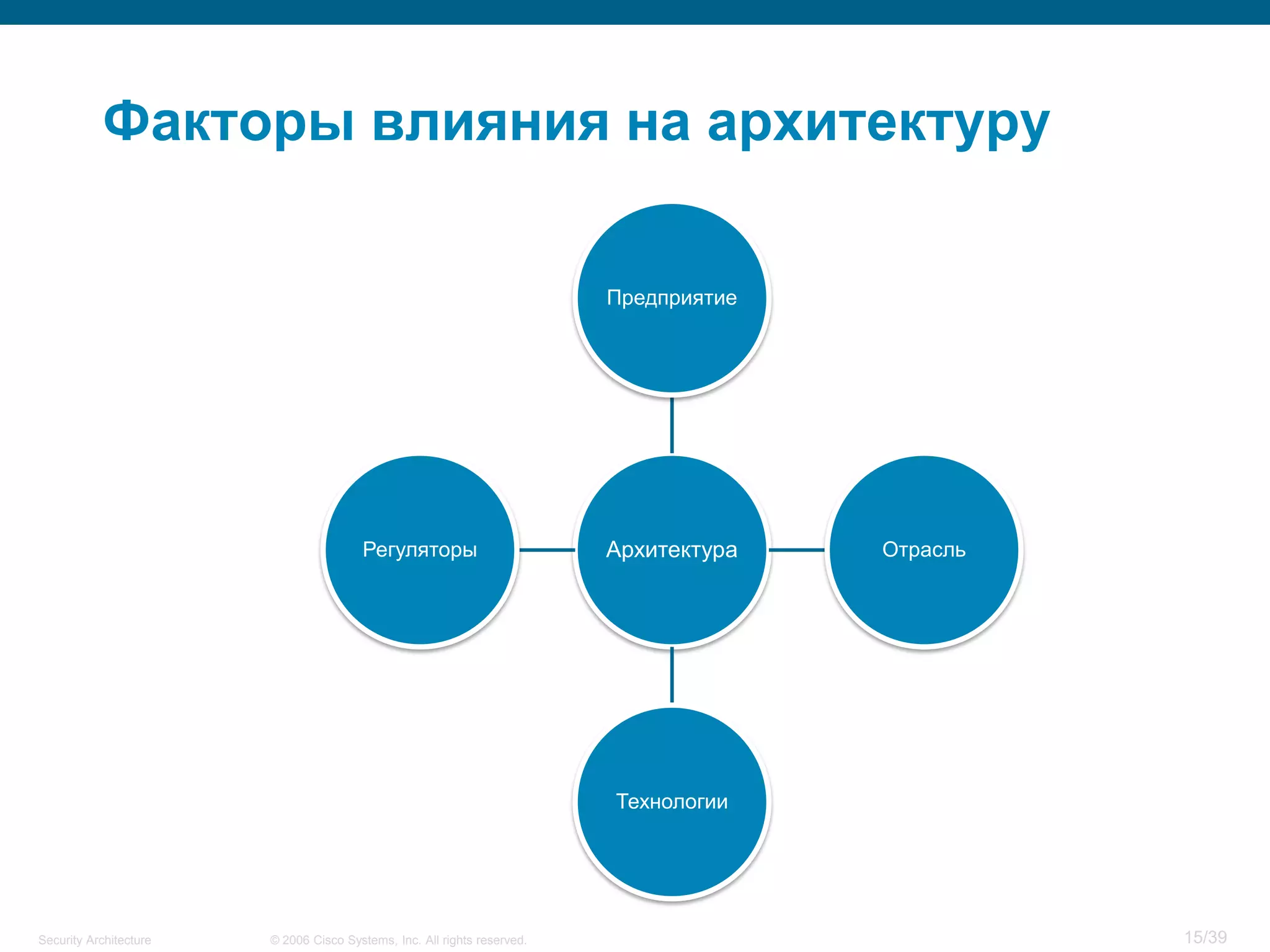
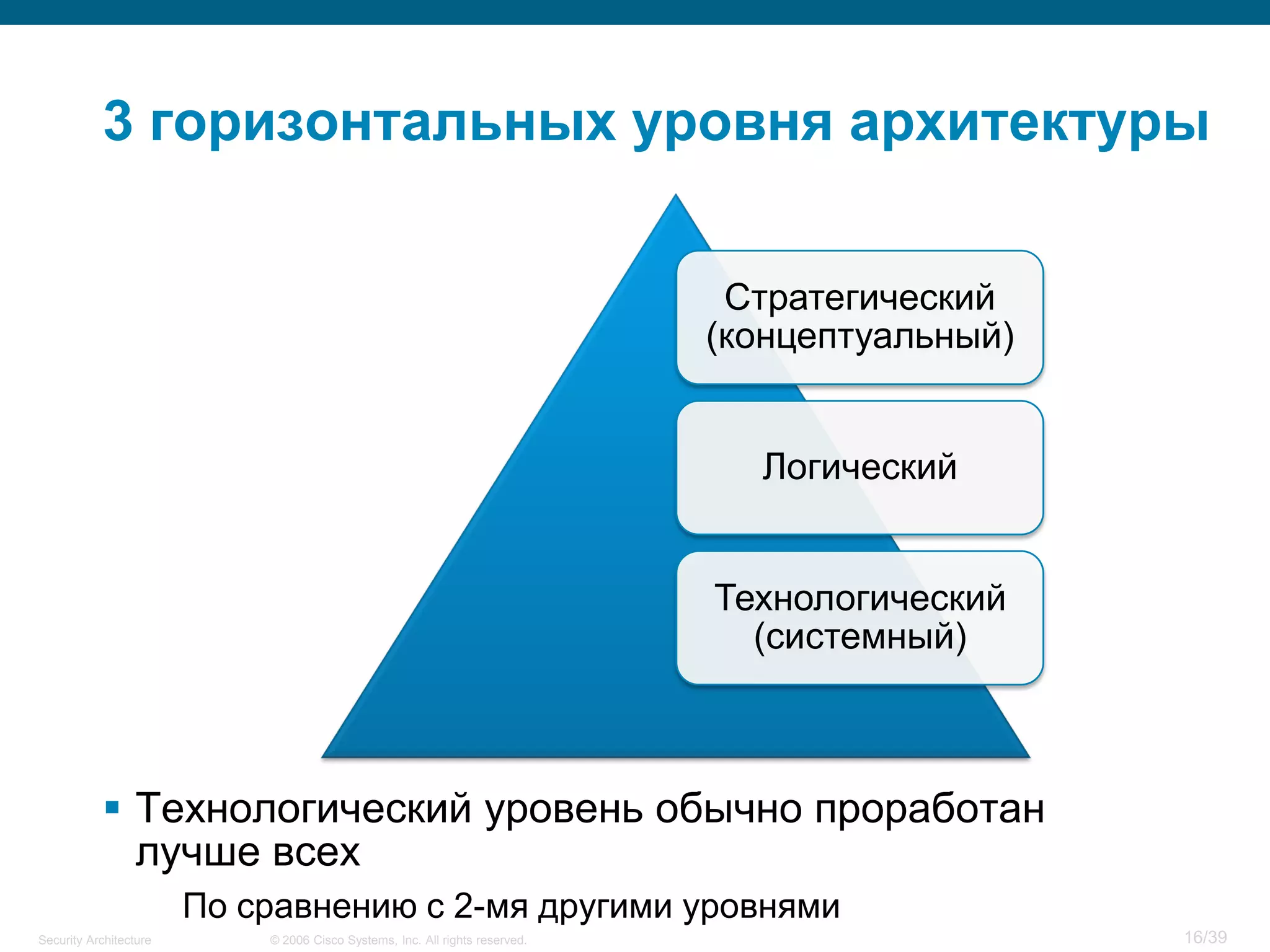
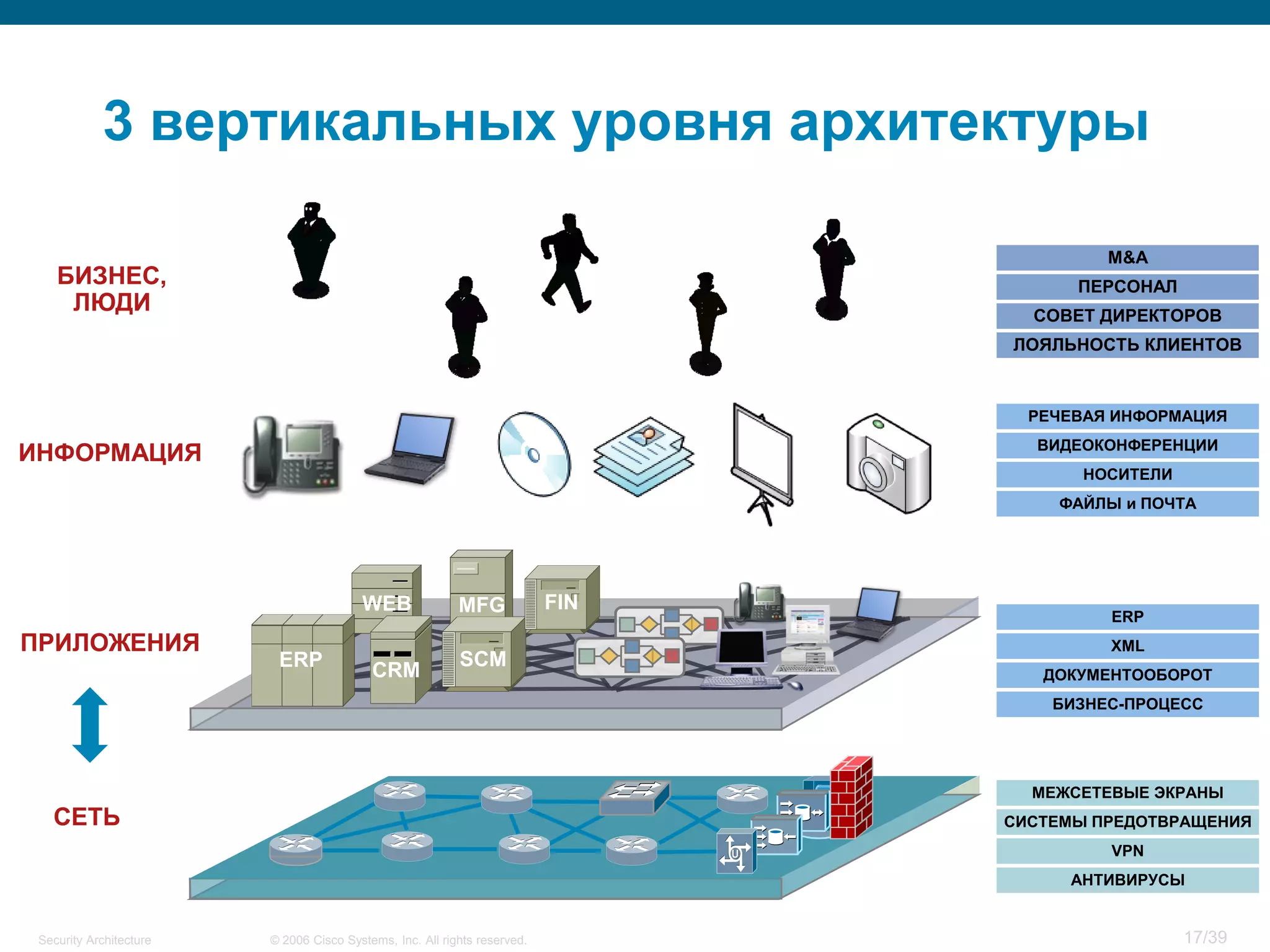


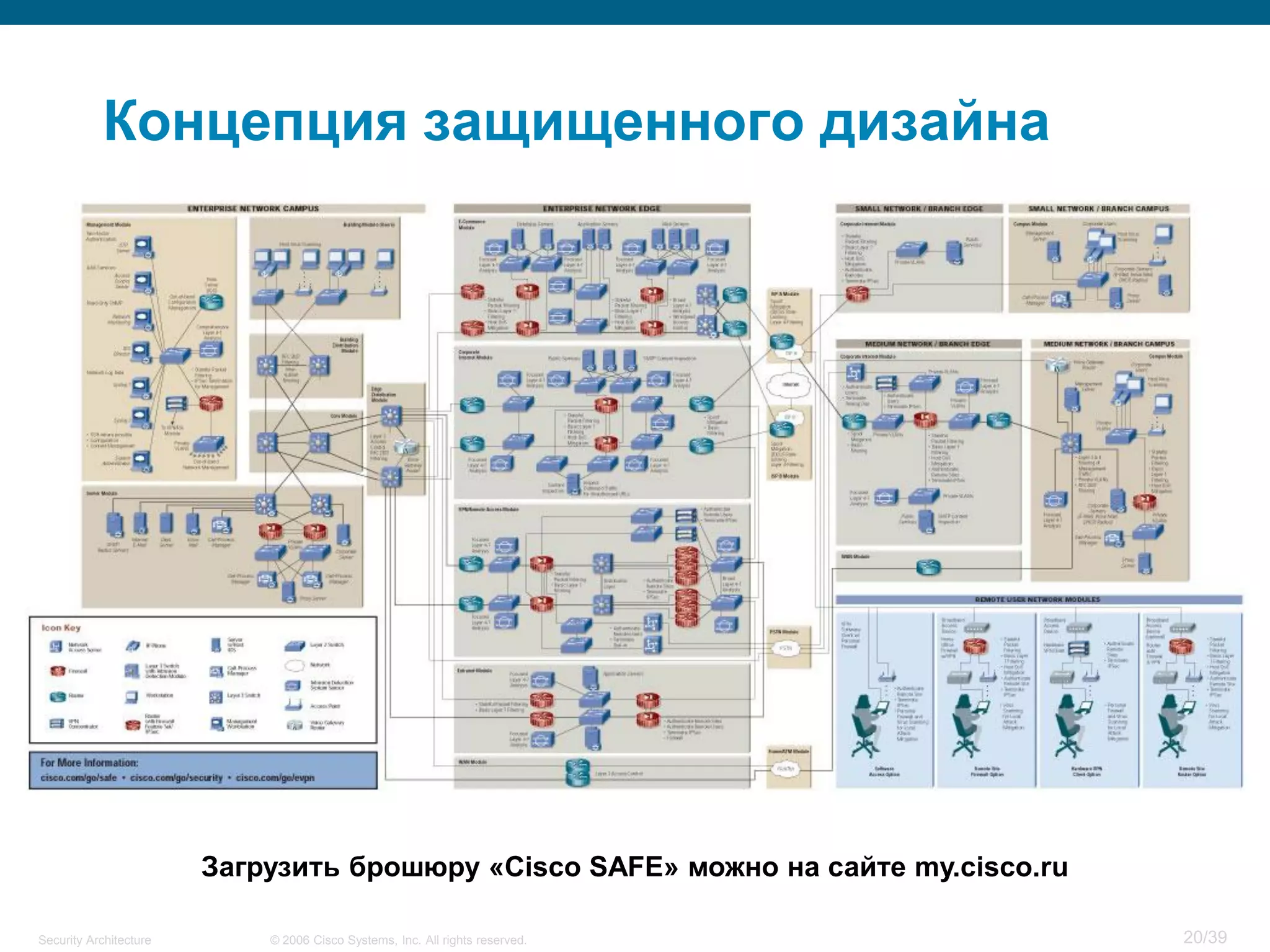

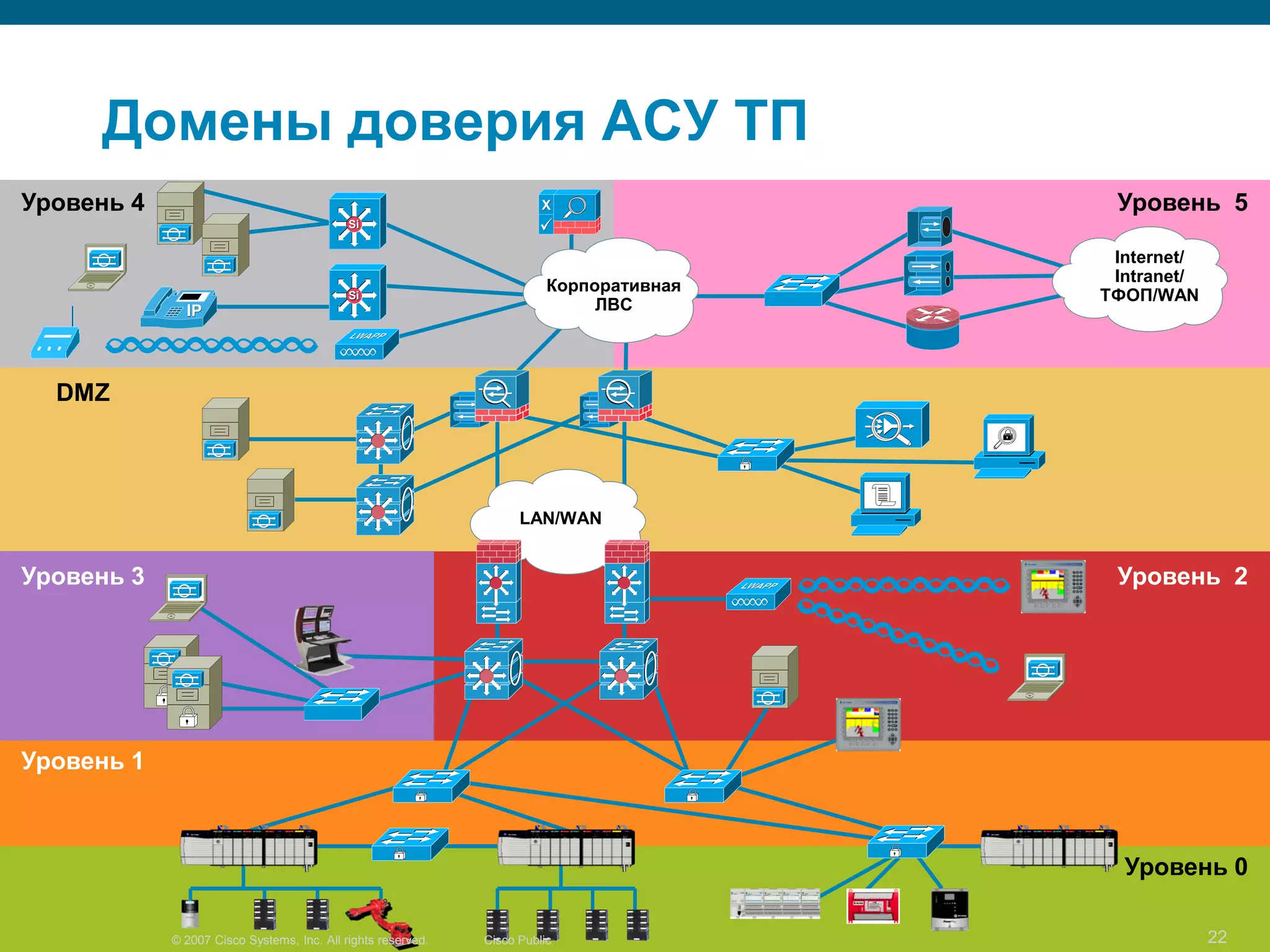

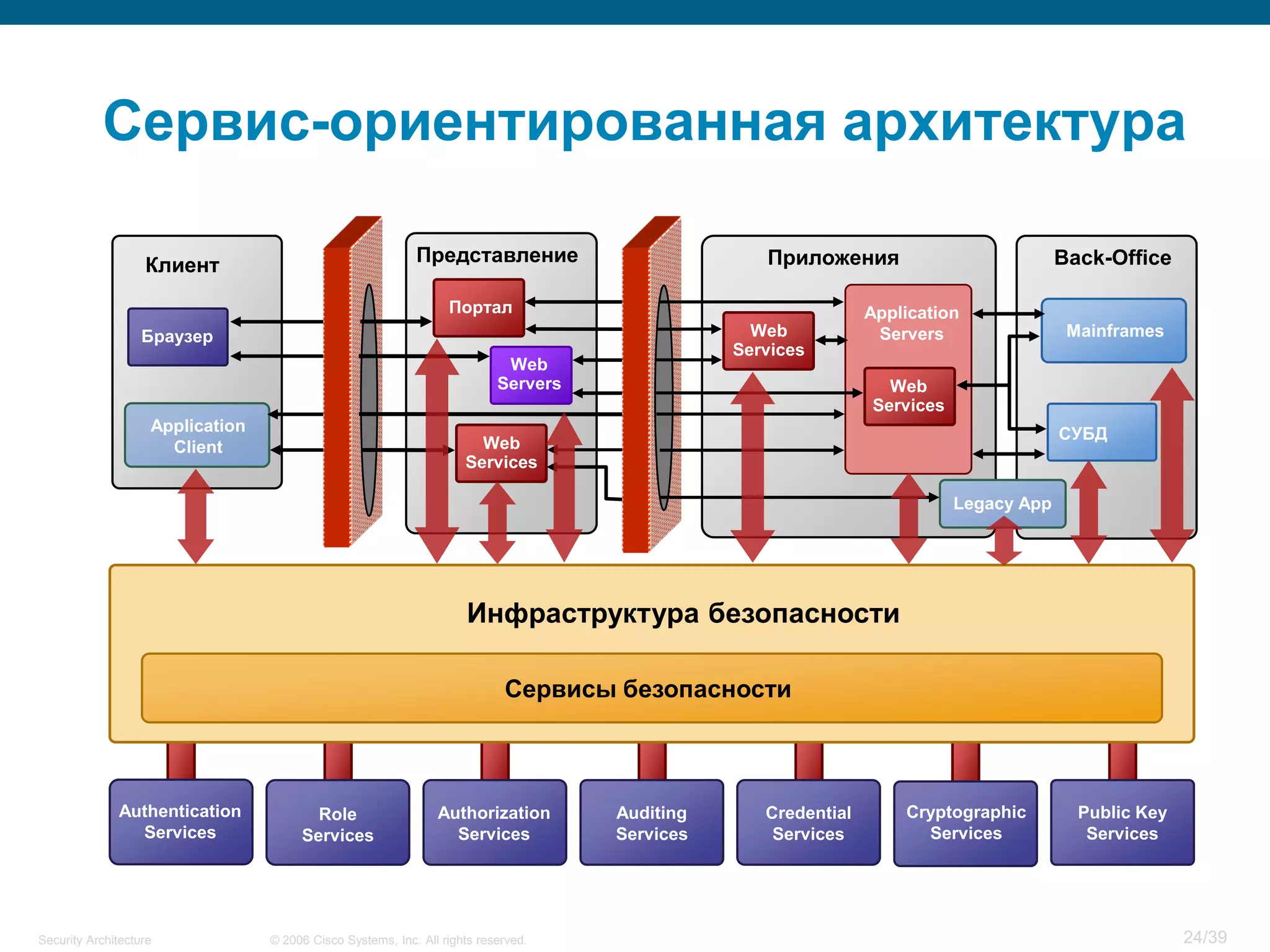
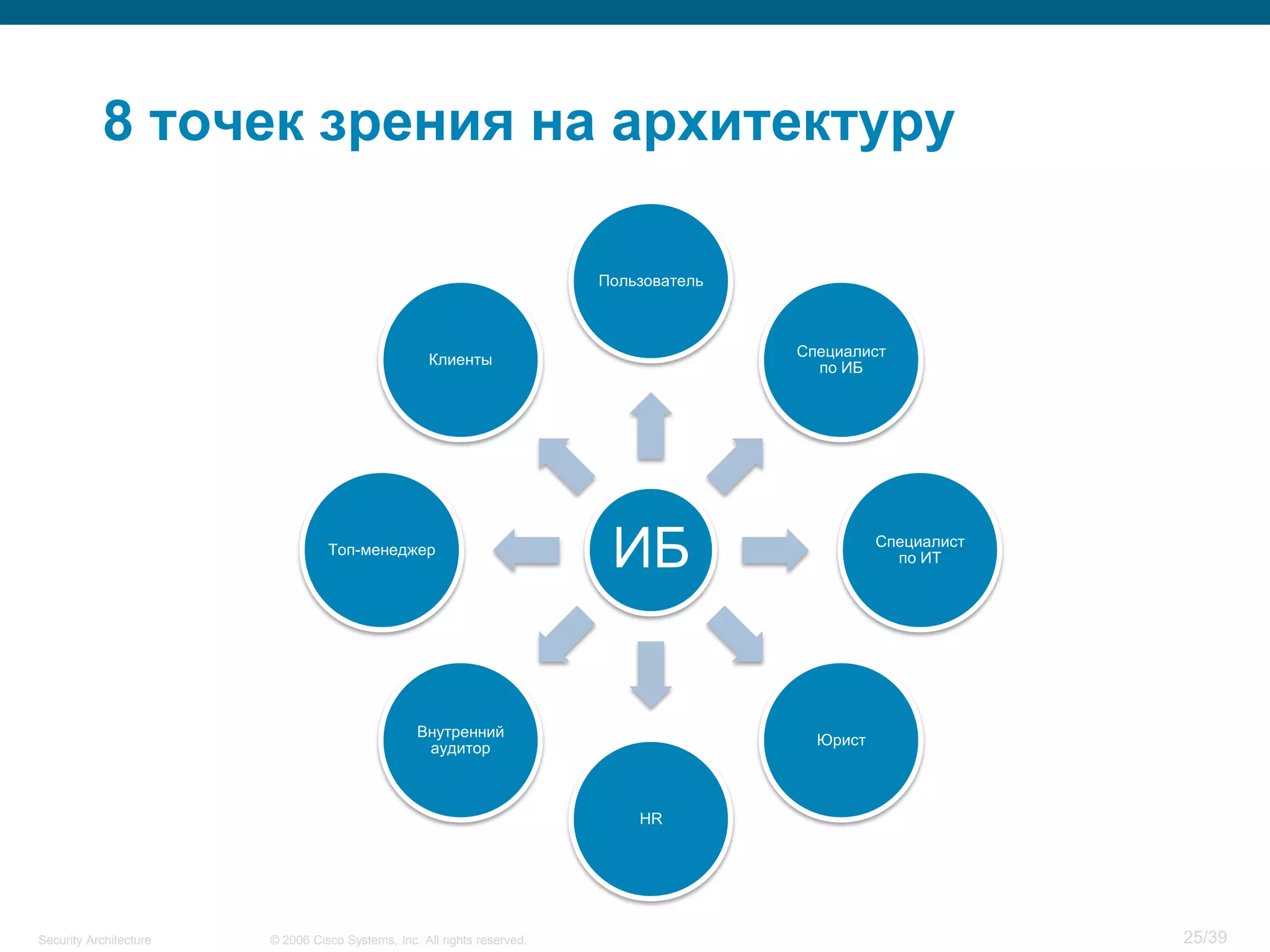


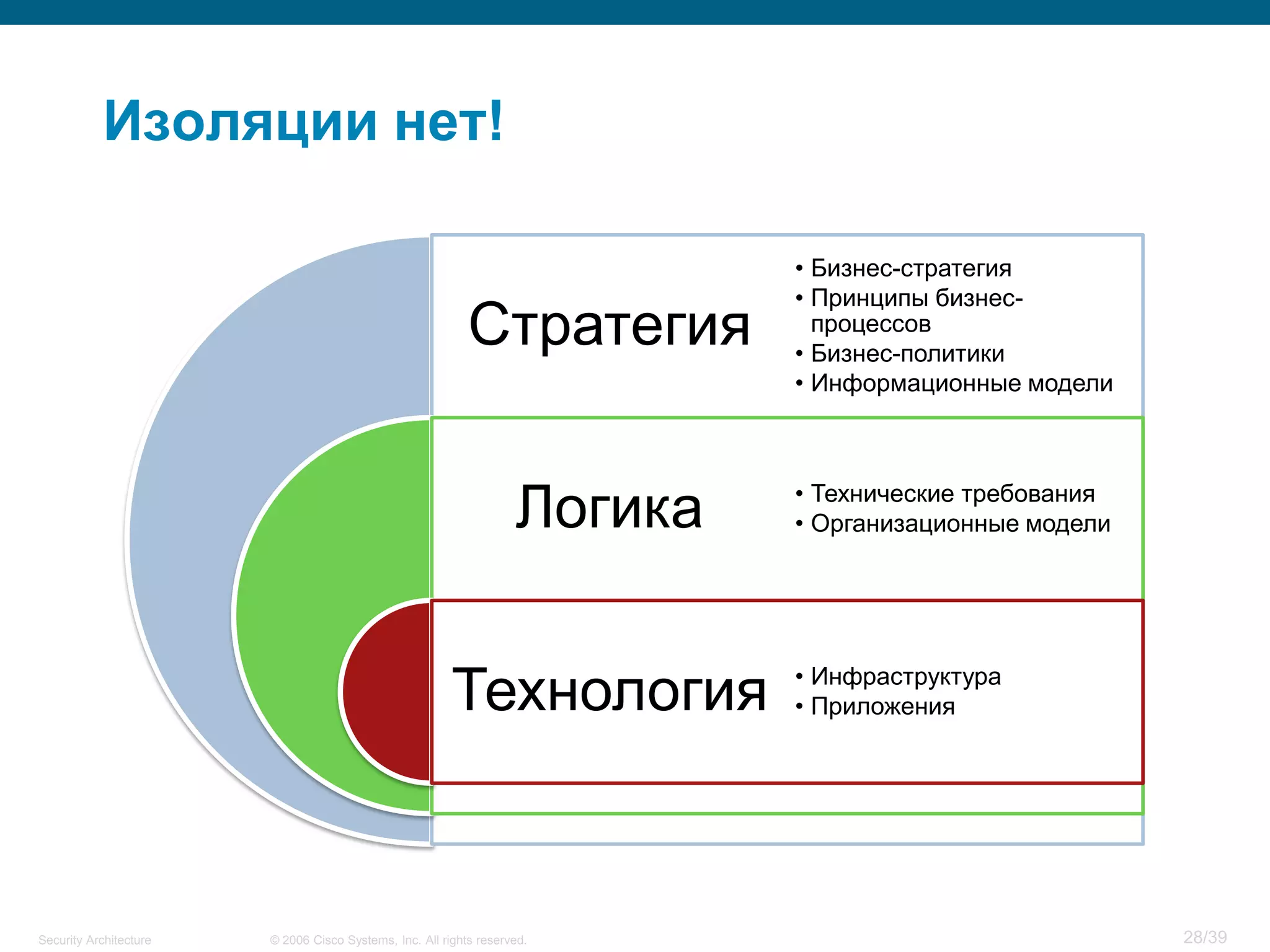
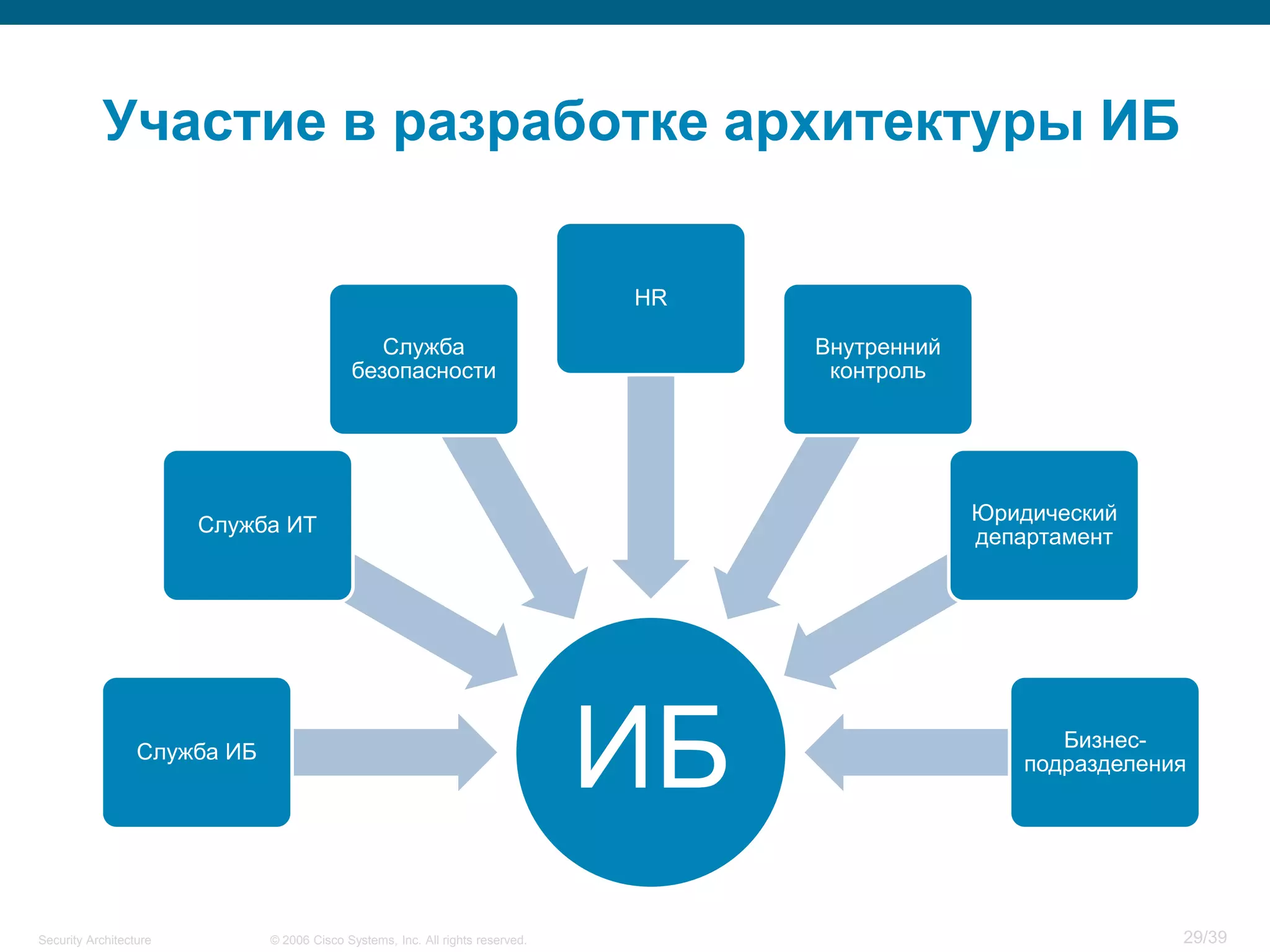











The document discusses information security architecture. It begins by asking why information security architecture is needed and what it is. It then discusses some of the technical problems organizations face, such as lack of standards and integration issues. Finally, it notes that security architecture describes the desired secure infrastructure structure and related components and interfaces.






































