NIST Risk Management Framework (RMF)
•Download as PPTX, PDF•
6 likes•9,709 views
Overview of the NIST Risk Management Framework (RMF)
Report
Share
Report
Share
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Cybersecurity Risk Management Program and Your Organization

Cybersecurity Risk Management Program and Your Organization
How To Present Cyber Security To Senior Management Complete Deck

How To Present Cyber Security To Senior Management Complete Deck
How to implement NIST cybersecurity standards in my organization

How to implement NIST cybersecurity standards in my organization
Risk Management Framework (RMF) STEP 4- Access Security Controls - NIST SP 80...

Risk Management Framework (RMF) STEP 4- Access Security Controls - NIST SP 80...
Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...

Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...
ISO 27001 - Information security user awareness training presentation - part 3

ISO 27001 - Information security user awareness training presentation - part 3
Viewers also liked
Viewers also liked (20)
Information System Sensitivity Level Impact Assessment (NIST SP 800-60v2r1)

Information System Sensitivity Level Impact Assessment (NIST SP 800-60v2r1)
(4) NIST SP 800-53 Revision 4 (security control enhancements omitted) 20140804

(4) NIST SP 800-53 Revision 4 (security control enhancements omitted) 20140804
Guide for Applying The Risk Management Framework to Federal Information Systems

Guide for Applying The Risk Management Framework to Federal Information Systems
RMF STEP 2: SELECT (NIST 800-53 Rev. 3 Controls, Enhancements and Supplementa...

RMF STEP 2: SELECT (NIST 800-53 Rev. 3 Controls, Enhancements and Supplementa...
Critical Security Controls v4 1 Mapped to NIST SP 800-53 Rev.4-final r6a

Critical Security Controls v4 1 Mapped to NIST SP 800-53 Rev.4-final r6a
NIST Policy Mapped to 800-53-800-53A-controls-and-objectives (Legal Size)

NIST Policy Mapped to 800-53-800-53A-controls-and-objectives (Legal Size)
INFOSECFORCE Risk Management Framework Transition Plan

INFOSECFORCE Risk Management Framework Transition Plan
Job aid framework-for-improving-critical-infrastructure-cybersecurity-core-jwd

Job aid framework-for-improving-critical-infrastructure-cybersecurity-core-jwd
Map Critical Security Controls (CSC) v5.0 to NIST SP 800-53 Revision 4 (Summa...

Map Critical Security Controls (CSC) v5.0 to NIST SP 800-53 Revision 4 (Summa...
Similar to NIST Risk Management Framework (RMF)
Our audits are designed to help you determine your SAP landscape's actual risk exposure and pinpoint areas that are open to potential attacks. They include everything from your infrastructure and SAP system parameters to individual component configurations and authorizations.
Also if your company's migration to SAP HANA or S/4HANA is right around the corner. An audit offers an ideal solution for safeguarding your systems and taking all the necessary security measures before you start your transition.
Our approach is based on SAP's security guidelines, the recommendations of the German Federal Office for Information Security (BSI), and the information security standard DIN ISO 27001.
Topics of focus:
• Challenges, tools and proven methods
• Advantages of a root cause analysis and of the resulting risks for your company
• Quick check vs. audit vs. penetrationtest
• Our project approach at a glance
• Recommendations for the follow-up of an Audit
-----------------------------------------------------------------------------------------
Für Informationen auf Deutsch, sprechen Sie uns gerne an: sast@akquinet.de
SAP Security & Compliance Audits. Find your vulnerabilities before you get hu...

SAP Security & Compliance Audits. Find your vulnerabilities before you get hu...akquinet enterprise solutions GmbH
Similar to NIST Risk Management Framework (RMF) (20)
Assessment ArchitectureSecurity Assessment Plan (SAP) System Name.docx

Assessment ArchitectureSecurity Assessment Plan (SAP) System Name.docx
Understanding the Risk Management Framework & (ISC)2 CAP Module 4: Life Cycle

Understanding the Risk Management Framework & (ISC)2 CAP Module 4: Life Cycle
SAP Security & Compliance Audits. Find your vulnerabilities before you get hu...

SAP Security & Compliance Audits. Find your vulnerabilities before you get hu...
Many companies and agencies conduct IT audits to test and assess the.docx

Many companies and agencies conduct IT audits to test and assess the.docx
A Monitor System in Data Redundancy in Information System

A Monitor System in Data Redundancy in Information System
Network Security & Assured Networks: TechNet Augusta 2015

Network Security & Assured Networks: TechNet Augusta 2015
CST 630 RANK Achievement Education--cst630rank.com

CST 630 RANK Achievement Education--cst630rank.com
CST 630 RANK Introduction Education--cst630rank.com

CST 630 RANK Introduction Education--cst630rank.com
CST 630 RANK Educational Specialist--cst630rank.com

CST 630 RANK Educational Specialist--cst630rank.com
More from James W. De Rienzo
More from James W. De Rienzo (11)
FedRAMP 2.0 Control-Implementation-Summary (CIS) v2 1 cross-matrixed with Fed...

FedRAMP 2.0 Control-Implementation-Summary (CIS) v2 1 cross-matrixed with Fed...
NIST NVD REV 4 Security Controls Online Database Analysis

NIST NVD REV 4 Security Controls Online Database Analysis
(3) Map Council on CyberSecurity's Critical Security Controls (CSC) Version 5...

(3) Map Council on CyberSecurity's Critical Security Controls (CSC) Version 5...
(1a) map csc 5 to nist sp 800 53 rev 4 (security control table portrait) 2014...

(1a) map csc 5 to nist sp 800 53 rev 4 (security control table portrait) 2014...
(2) map csc 5 to nist sp 800 53 rev 4 (controls & enhancements) 20140804

(2) map csc 5 to nist sp 800 53 rev 4 (controls & enhancements) 20140804
(1b) Map CSC v5.0 to NIST SP 800 53 Revision 4 (security control table landsc...

(1b) Map CSC v5.0 to NIST SP 800 53 Revision 4 (security control table landsc...
Policy. FedRAMP Security Assessment Plan (SAP) Template, Policy and Procedure...

Policy. FedRAMP Security Assessment Plan (SAP) Template, Policy and Procedure...
Information Assurance, A DISA CCRI Conceptual Framework

Information Assurance, A DISA CCRI Conceptual Framework
Recently uploaded
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
NIST Risk Management Framework (RMF)
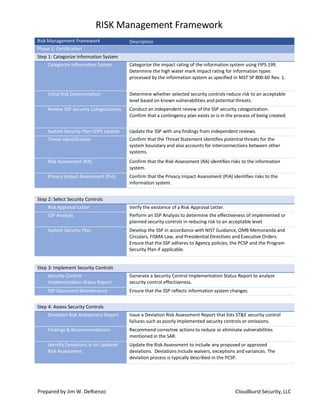
- 1. RISK Management Framework Risk Management Framework Description Phase 1: Certification Step 1: Categorize Information System Categorize Information System Categorize the impact rating of the information system using FIPS 199. Determine the high water mark impact rating for information types processed by the information system as specified in NIST SP 800-60 Rev. 1. Initial Risk Determination Determine whether selected security controls reduce risk to an acceptable level based on known vulnerabilities and potential threats. Review SSP Security Categorization Conduct an independent review of the SSP security categorization. Confirm that a contingency plan exists or is in the process of being created. System Security Plan (SSP) Update Update the SSP with any findings from independent reviews. Threat Identification Confirm that the Threat Statement identifies potential threats for the system boundary and also accounts for interconnections between other systems. Risk Assessment (RA) Confirm that the Risk Assessment (RA) identifies risks to the information system. Privacy Impact Assessment (PIA) Confirm that the Privacy Impact Assessment (PIA) identifies risks to the information system. Step 2: Select Security Controls Risk Approval Letter Verify the existence of a Risk Approval Letter. SSP Analysis Perform an SSP Analysis to determine the effectiveness of implemented or planned security controls in reducing risk to an acceptable level. System Security Plan Develop the SSP in accordance with NIST Guidance, OMB Memoranda and Circulars, FISMA Law, and Presidential Directives and Executive Orders. Ensure that the SSP adheres to Agency policies, the PCSP and the Program Security Plan if applicable. Step 3: Implement Security Controls Security Control Implementation Status Report Generate a Security Control Implementation Status Report to analyze security control effectiveness. SSP Document Maintenance Ensure that the SSP reflects information system changes. Step 4: Assess Security Controls Deviation Risk Assessment Report Issue a Deviation Risk Assessment Report that lists ST&E security control failures such as poorly implemented security controls or omissions. Findings & Recommendations Recommend corrective actions to reduce or eliminate vulnerabilities mentioned in the SAR. Identify Deviations in an Updated Risk Assessment Update the Risk Assessment to include any proposed or approved deviations. Deviations include waivers, exceptions and variances. The deviation process is typically described in the PCSP. Prepared by Jim W. DeRienzo Cloudburst Security, LLC
- 2. RISK Management Framework Risk Management Framework Plan of Actions and Milestones (POA&M) Description Update the POA&M Report to reflect progress in applying countermeasures that address weaknesses mentioned in the SAR. Project Plan Define the level of effort and resource requirements for conducting the ST&E: 1)Identify scope of effort (e.g., # of physical and virtual servers; Operating systems involved; # of applications; Geographic location of IT assets; Geographic location of security control staff). 2) Schedule demands (e.g., Reauthorization deadlines; POA&M deadlines). 3)Personnel/skills availability (e.g., Who is the Security Authorization Agent? Is an independent testing team available?). 4)Security Control Assessment (e.g., Evaluate security controls to verify that the controls are implemented correctly, operating as intended, and meeting the requirements of the SSP). Rules of Engagement Remain independent of system development and operations teams, as well as those responsible for correcting security deficiencies. Security Assessment Plan Conduct a comprehensive assessment of the management, operational and technical security controls for each General Support System (GSS) and Major Application (MA). Conduct technical assessments using a combination of automated tools and manual checks (e.g. vulnerability scans, packet analysis, pen tests and social engineering). Security Assessment Report (SAR) Using the approved ST&E test case procedures, assess each control and prepare the Security Assessment Report (SAR). A SAR is less than 10 pages and shows residual risk such as major issues or red flags to the system owner (i.e., % of management, operational and technical controls passed) ST&E Procedures Select or develop ST&E test cases to perform an assessment of each security control. Ensure that the DAA approves all selected ST&E test case procedures. ST&E Report Using the approved ST&E test case procedures, assess each control and prepare the ST&E Report. An ST&E Report is hundreds of pages based on individual test cases and artifacts (i.e., Contingency Plan). Prepared by Jim W. DeRienzo Cloudburst Security, LLC
- 3. RISK Management Framework Risk Management Framework Submit Security Authorization (SA) Package to DAA Description Assemble the final SA Package and submit to the DAA. The SA Package contains: Security Risk Assessment (RA) Approves System Security Plan (SSP) Completed Privacy Impact Assessments (PIA) Configuration Management Plan (CMP) Contingency Plan (CP) Security Test & Evaluation Report (ST&E Rpt.) Plan of Action and Milestones (POA&M) Security Assessment Report (SAR) Accreditation Decision letter (ATO) Interconnection Security Agreement (ISA) Memorandum of Understanding (MOU) / Memorandum of Agreement (MOA) Update Security Authorization Package Determine that the DAA has authorized any deviation from the baseline image prior to forwarding the Security Authorization Package to the DAA. Update the SSP and Risk Assessment based on the SAR. Vulnerability Assessment Provide an Executive Summary Report and a Technical Summary Report that shows vulnerabilities by IP Address, Open TCP/UDP Port and Common Vulnerability Enumeration (CVE). Include network devices, hosting providers, ISA partners, and local host checks for systems, applications and database servers. Local host checks must include credentialed scan results. Provide a Compliance Failure Report for USGCB, CIS, STIG, CAG 4.0, OWASP Top 10 or PII. Software code reviews are available upon request. Phase 2: Accreditation Step 5: Authorize Information System Accreditation Decision Letter Verify that the DAA has issued an Approval to Operate (ATO) based on the residual risks identified in the RA, and that the ATO includes any special conditions that apply. Accreditation Documentation Authority to Operate (ATO) - The system is authorized to operate under conditions outlined in the ATO letter. Interim Authority to Operate (IATO) - The system may operate, but has deficiencies that must be corrected within a specified time period. Denial/Revocation - The DAA denies or removes authorization to operate. Briefing materials Provide briefing materials to justify the risk decision. Recommendation Report Provide recommendations to correct, eliminate or reduce any deficiencies or vulnerabilities specified in the SAR. Prepared by Jim W. DeRienzo Cloudburst Security, LLC
- 4. RISK Management Framework Phase 3: Continuous Monitoring Step 6: Monitor Security Controls Configuration Management and Control Document Information System Changes - Determine that information system changes are documented. Security Impact Analysis - Analyze the security impact of proposed and actual system changes. Security Control Monitoring Security Control Selection - Selects controls for continuous monitoring assessment. Example: MA-4 (Remote Maintenance), SC-7 (Boundary Protection), SI-3 (Malicious Code Protection) Selected Security Control Assessment - Assess controls designated for continuous monitoring. Example: check VPN/remote access logs daily; check firewall rule set daily; update A/V daily. Status Report and Documentation Update System Security Plan - Periodically review and update the SSP Update POA&Ms - Review and update the POA&Ms Report Security Status to DAA - Report the security status of the information system to the System Owner, who in turn reports to the DAA. Prepared by Jim W. DeRienzo Cloudburst Security, LLC
