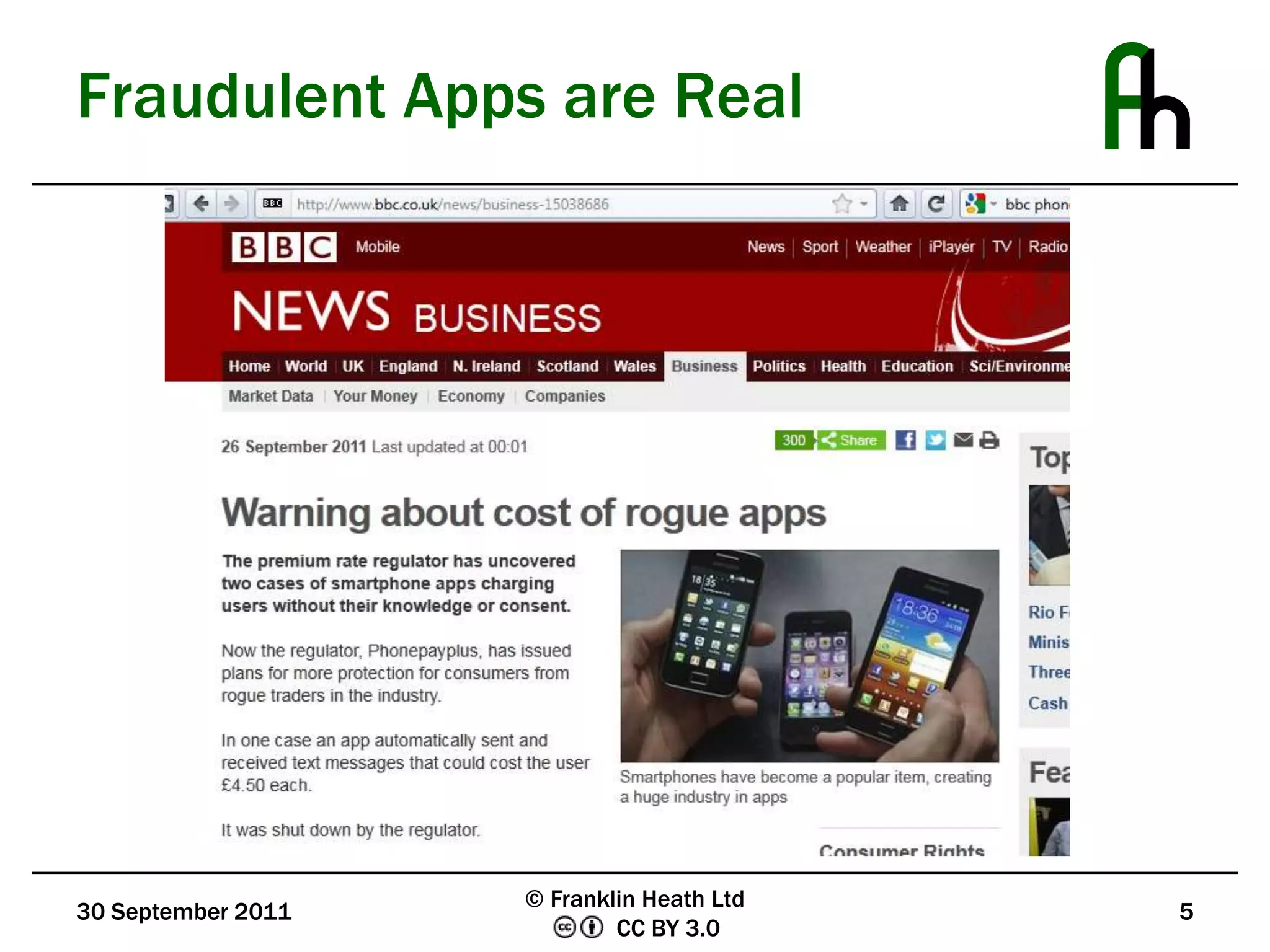
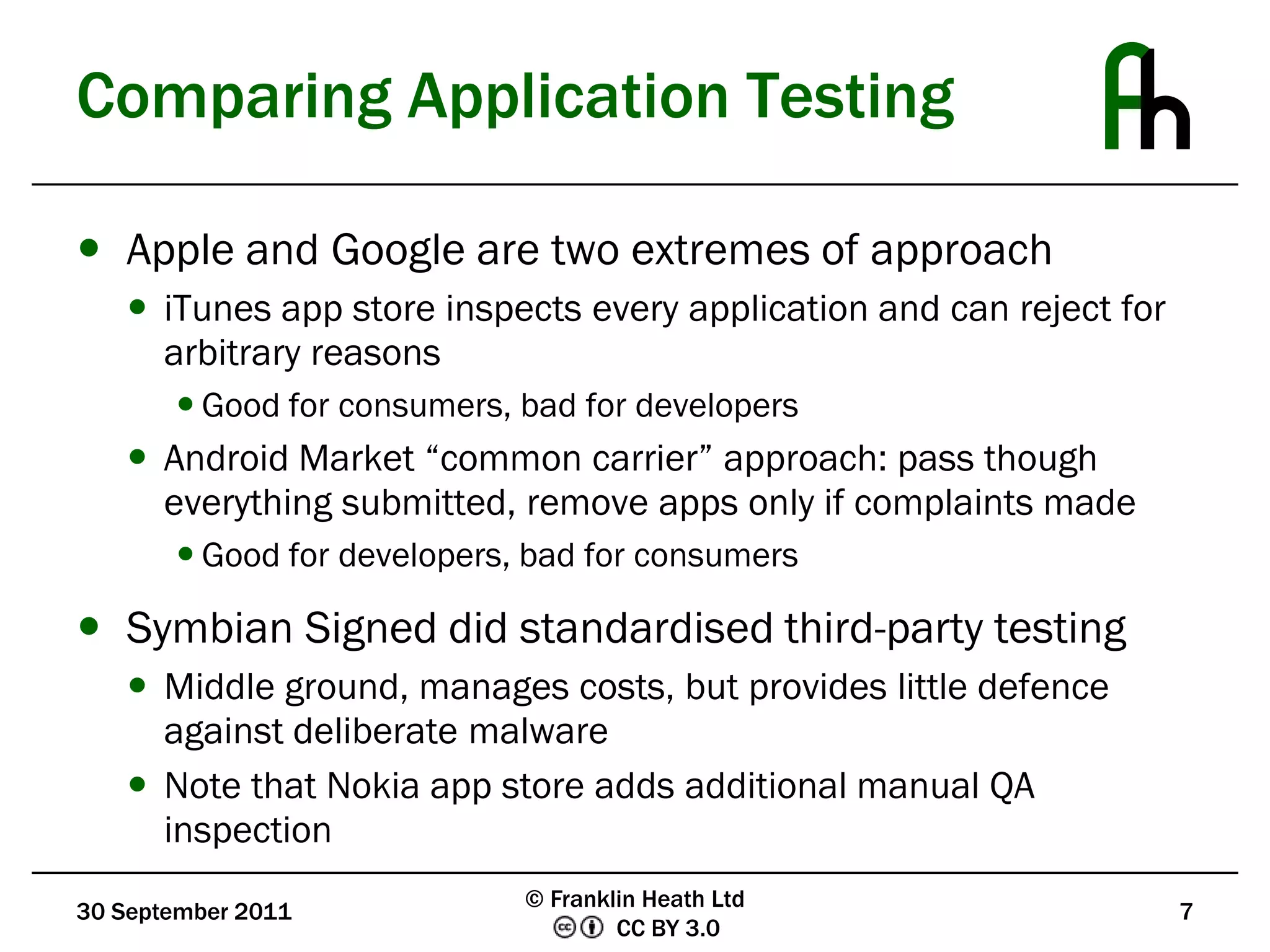
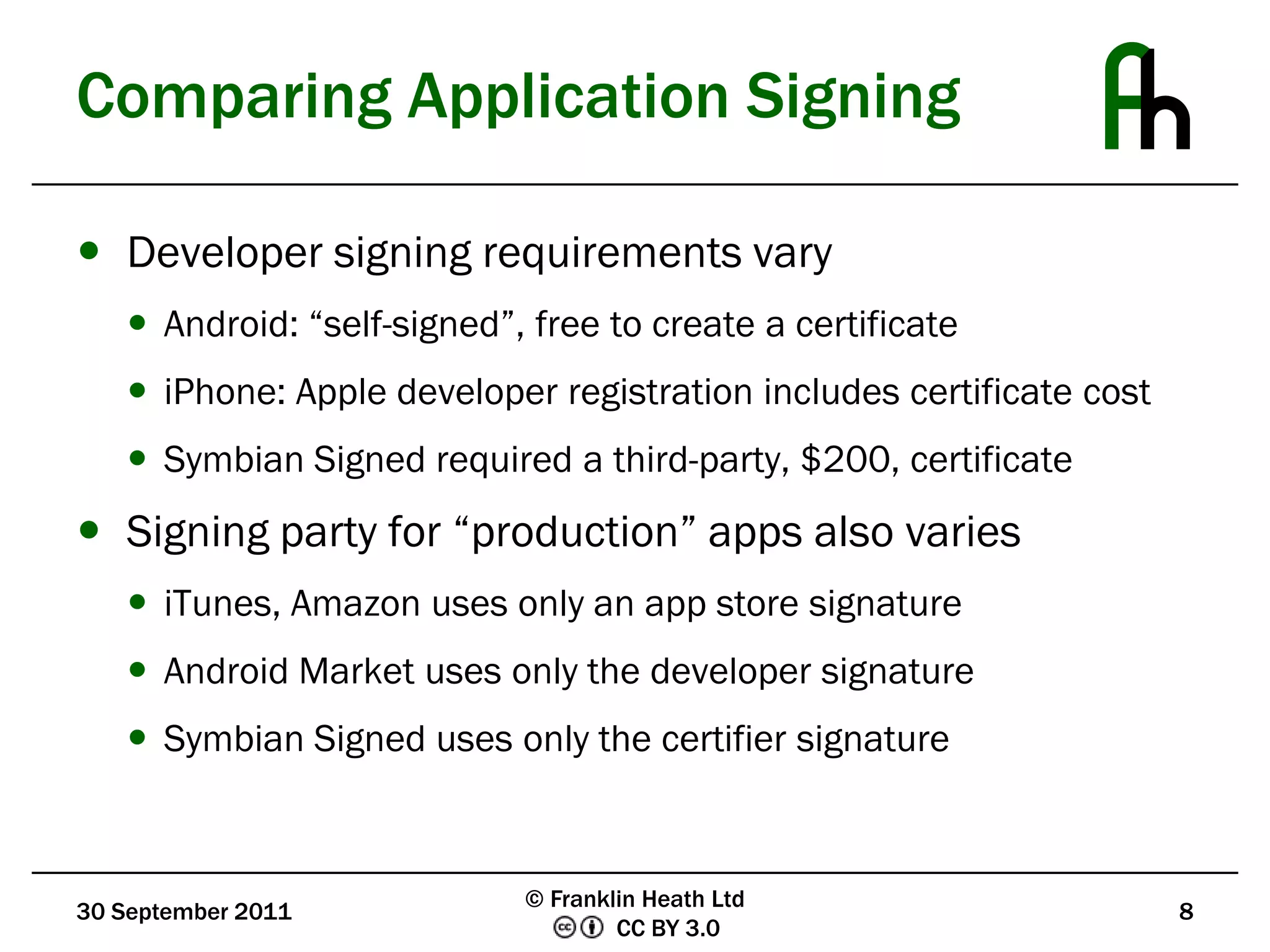
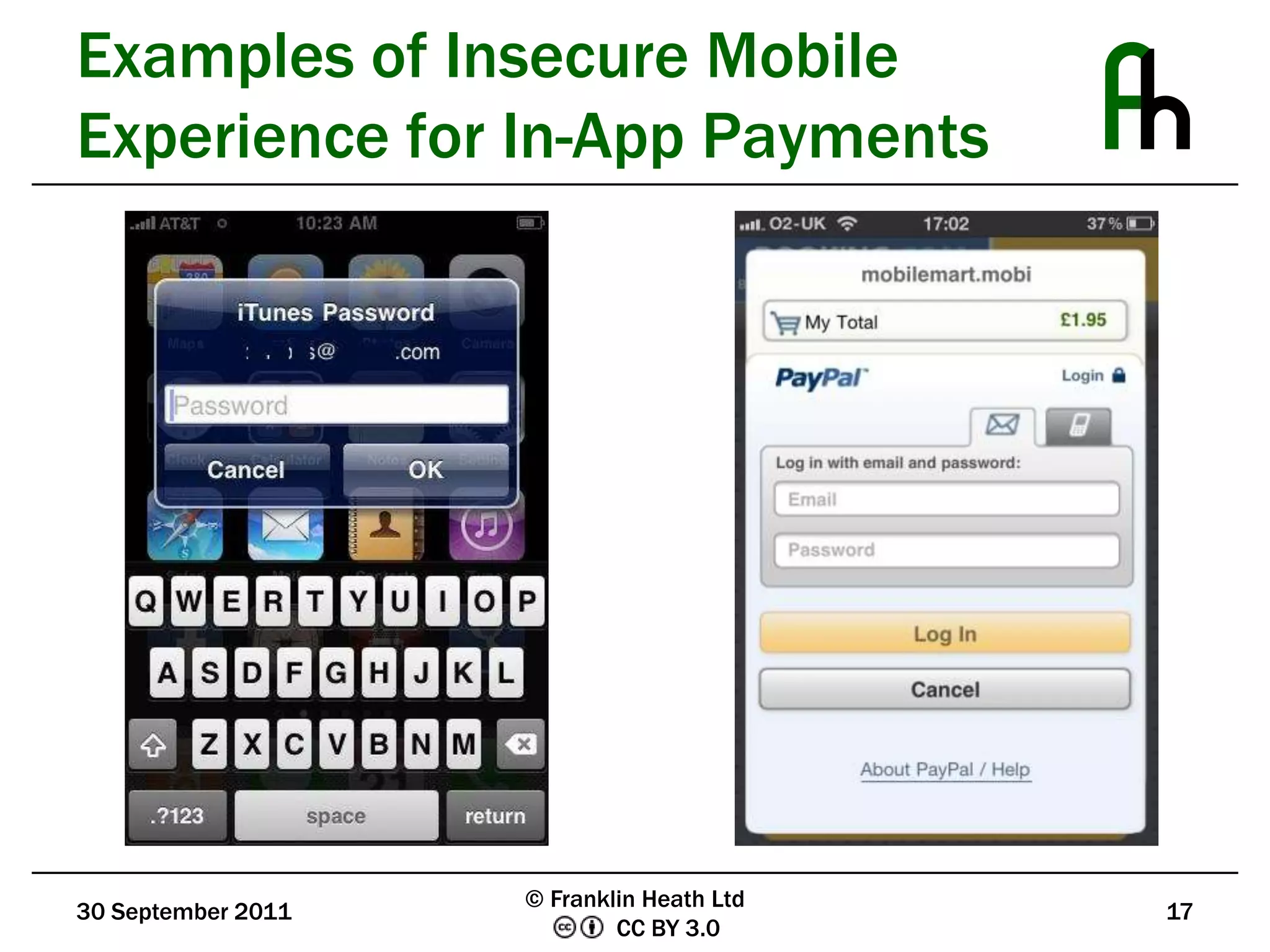
The document discusses mobile application security, outlining the need for improved security measures due to the rise of fraudulent apps that exploit mobile vulnerabilities for financial gain. It compares the security frameworks of major platforms like Apple and Google, highlighting disparities in application testing and developer signing requirements. The document also presents user-centric security solutions, such as notarized call recording and premium charge warnings, aimed at empowering consumers to manage their own security and financial information.

![TopicsWho the [heck] are you?Why can’t you turn this [stupid] security off?Comparing security frameworks on the main platformsWhat’s in it for me?Security apps that vendors and operators aren’t doingNotarised call recordingPremium charge warningTrustworthy viewport30 September 20112© Franklin Heath Ltd](https://image.slidesharecdn.com/mobilesecuritysticksandcarrots-110930094130-phpapp01/75/Mobile-Security-Sticks-and-Carrots-2-2048.jpg)