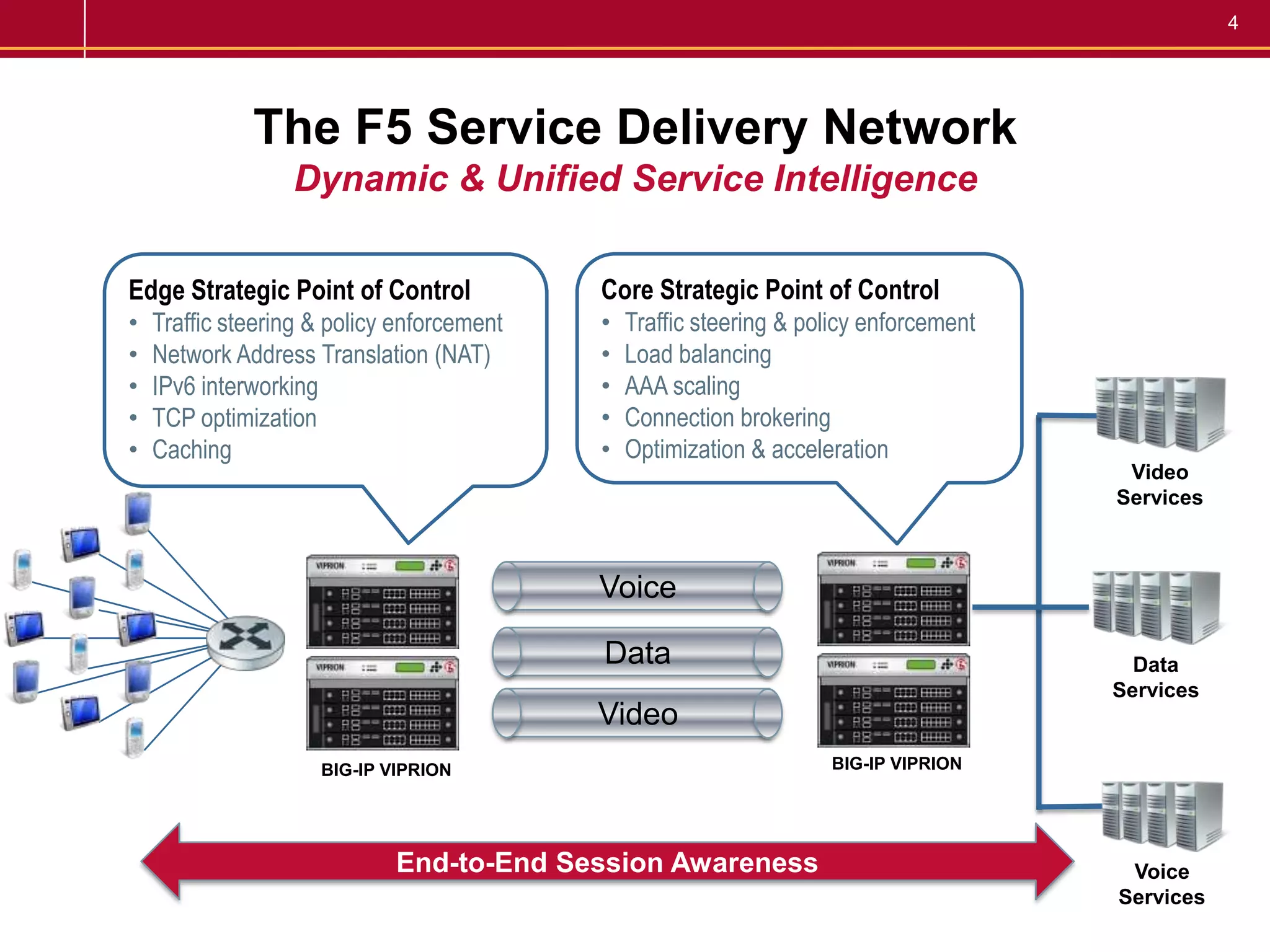
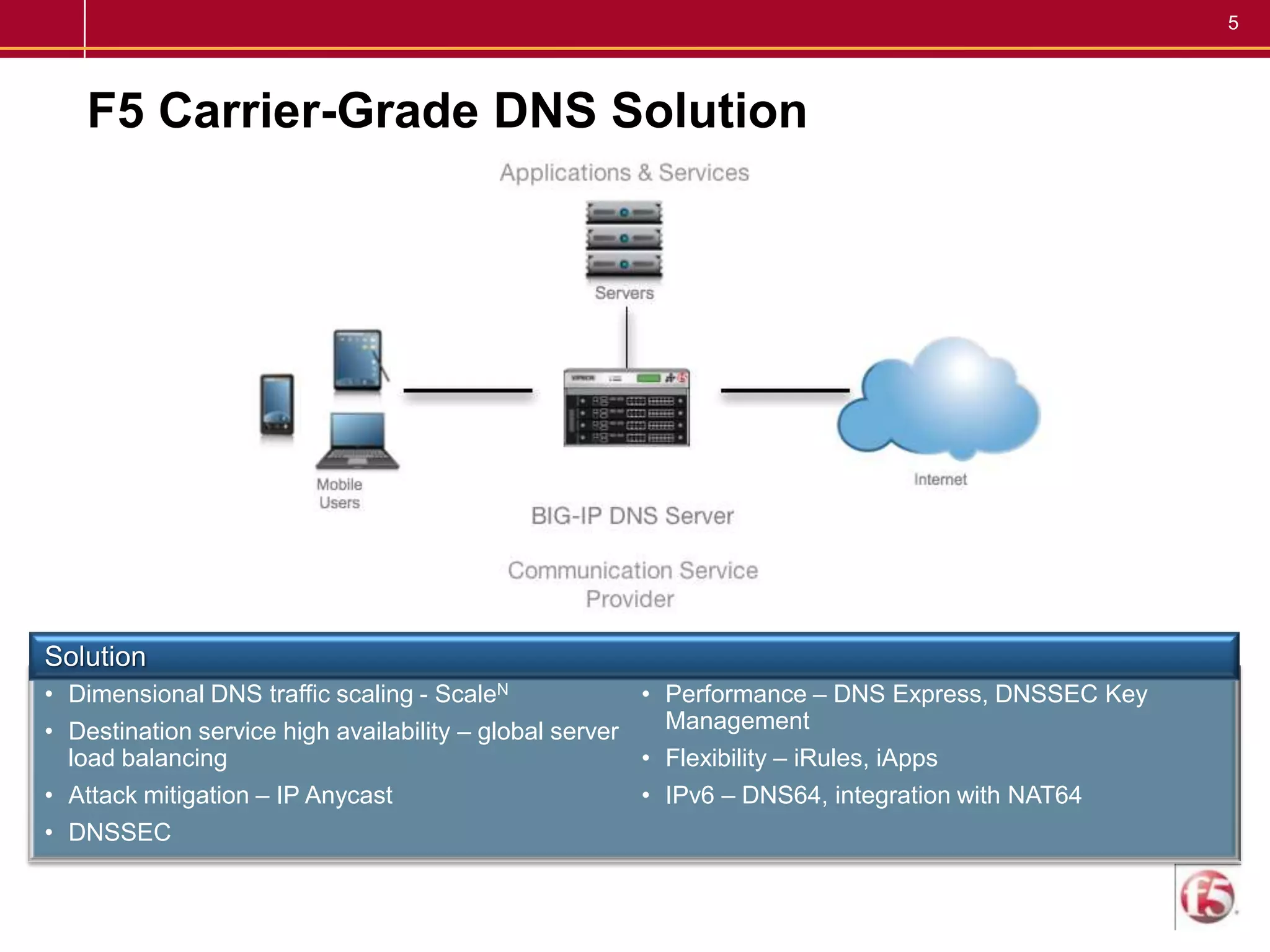
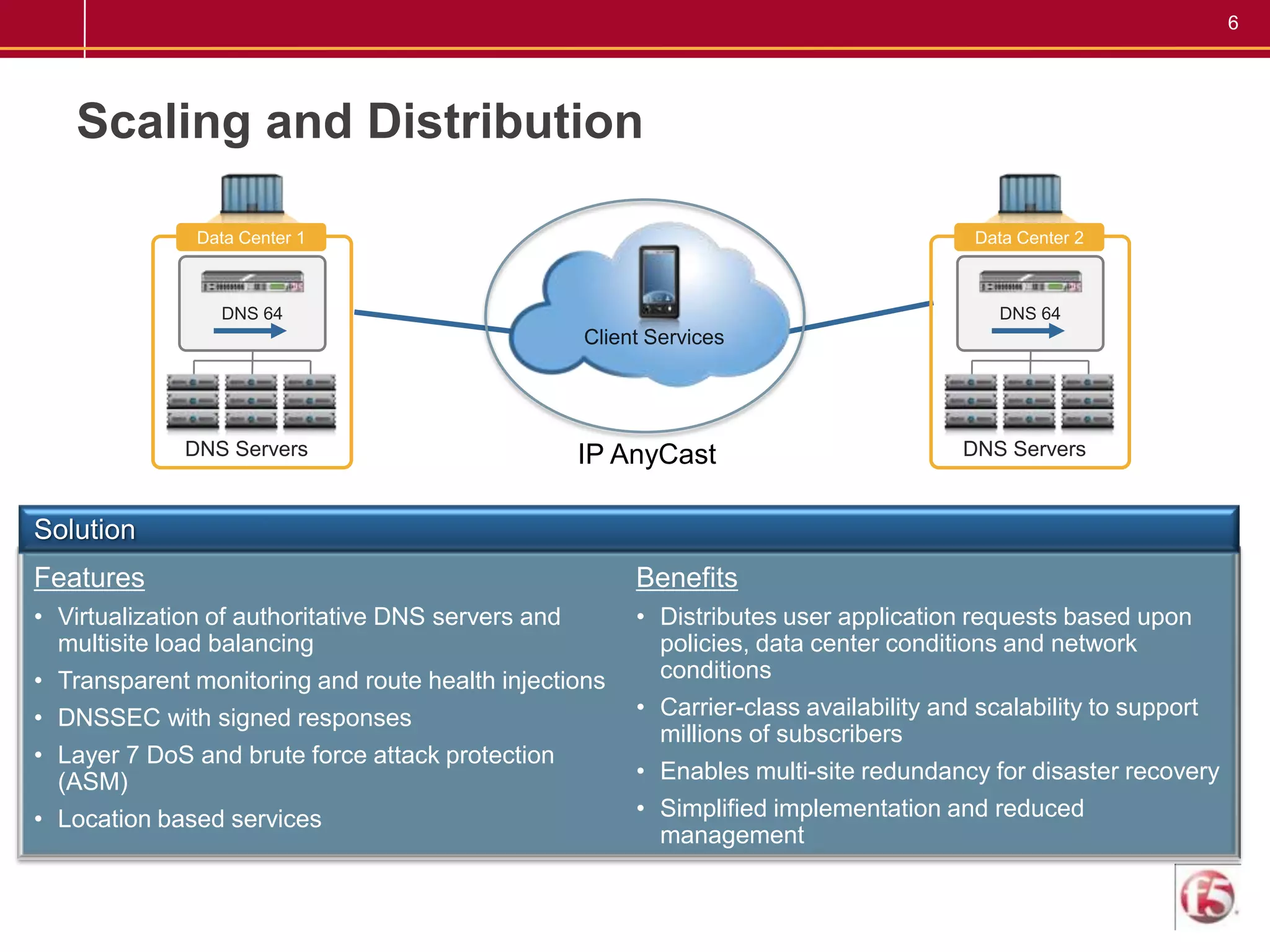
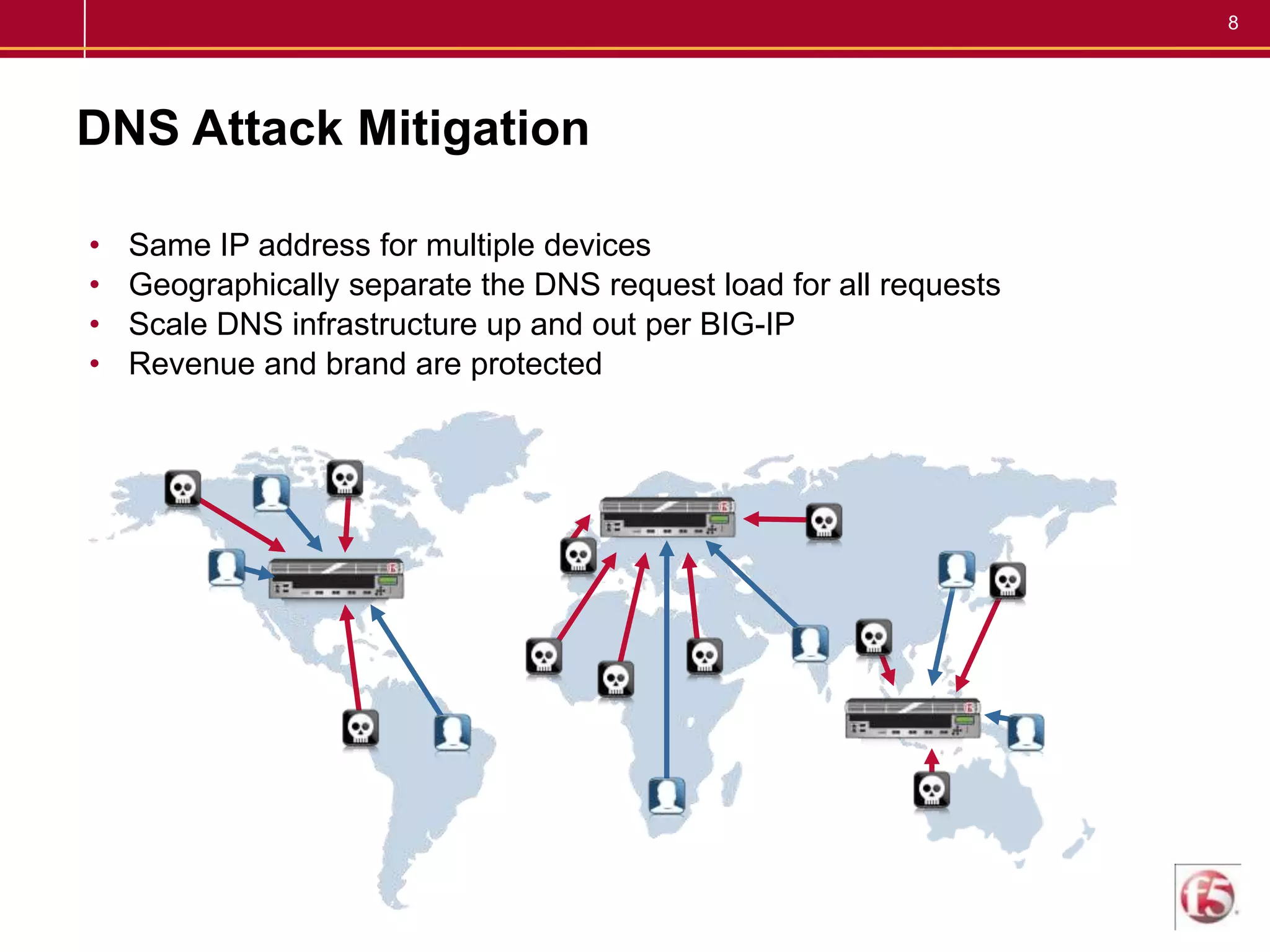
F5 provides a carrier-grade DNS solution for communications service providers that delivers high-speed DNS responses, high query rates, and secure transactions while integrating IPv4 and IPv6. It mitigates the impact of attacks when every second of delay can mean lost conversions, page loads, and customer satisfaction costing millions per year. The solution scales DNS traffic, provides service availability, and mitigates attacks through features like IP anycast, DNSSEC, and attack protection.