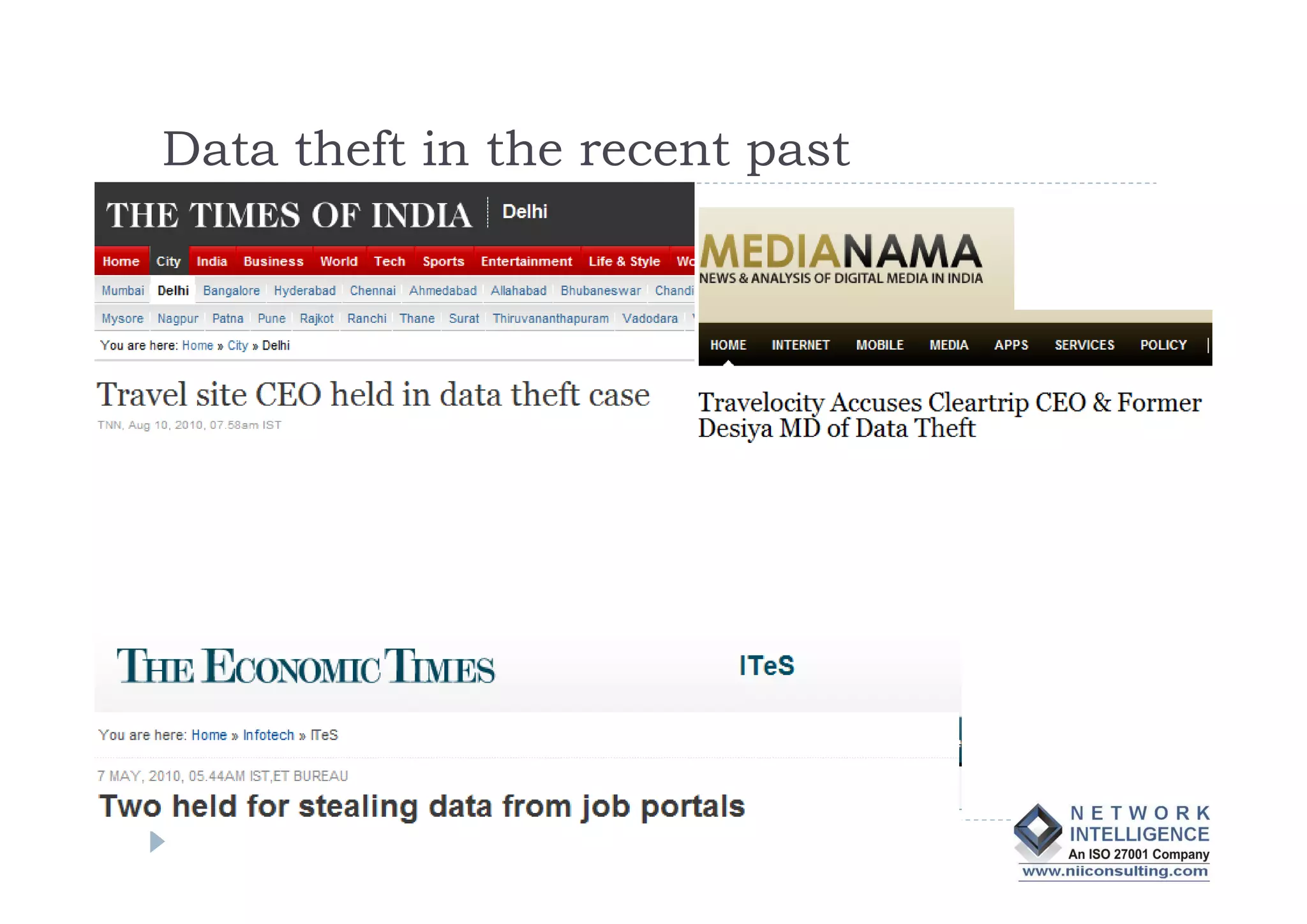
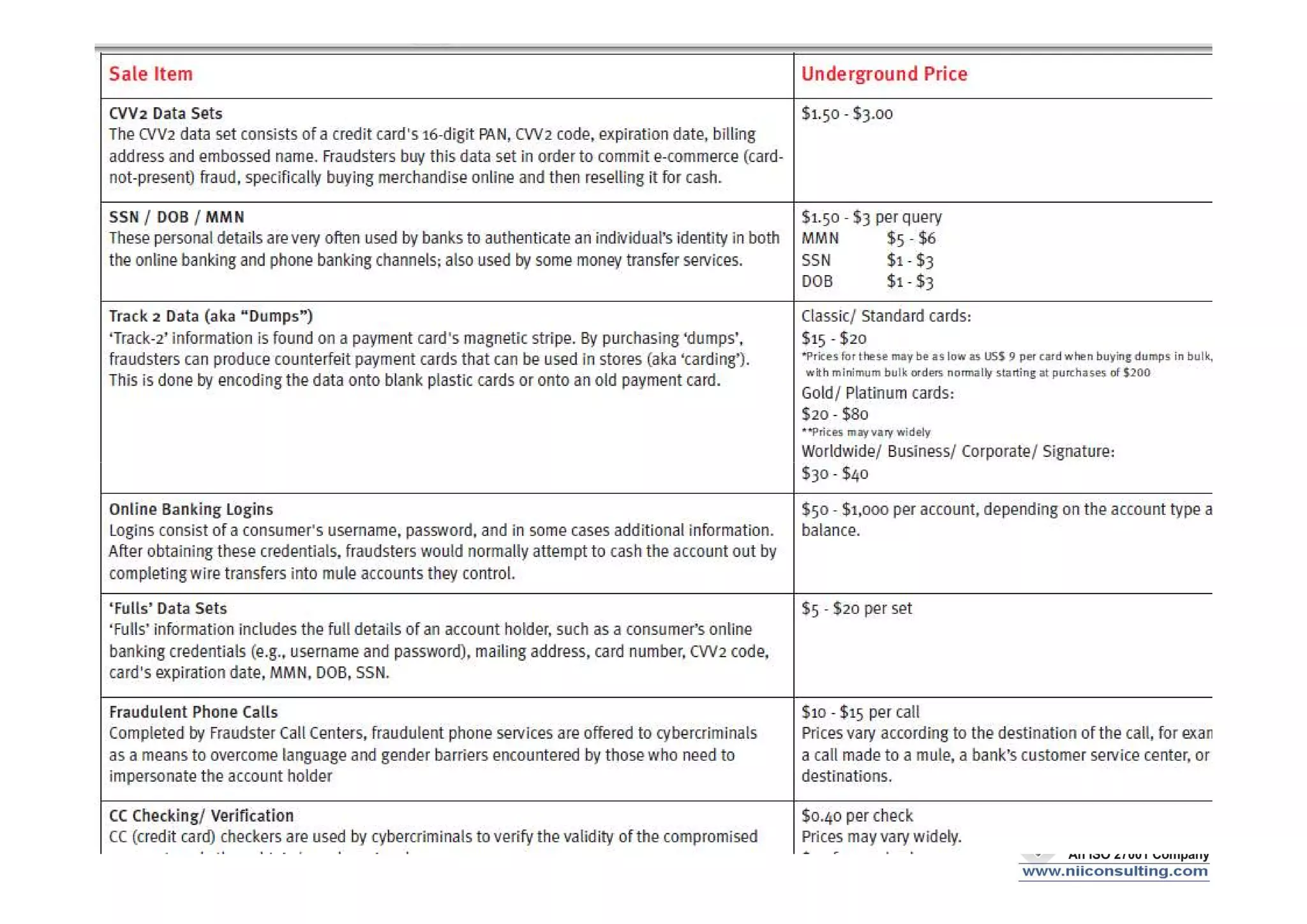
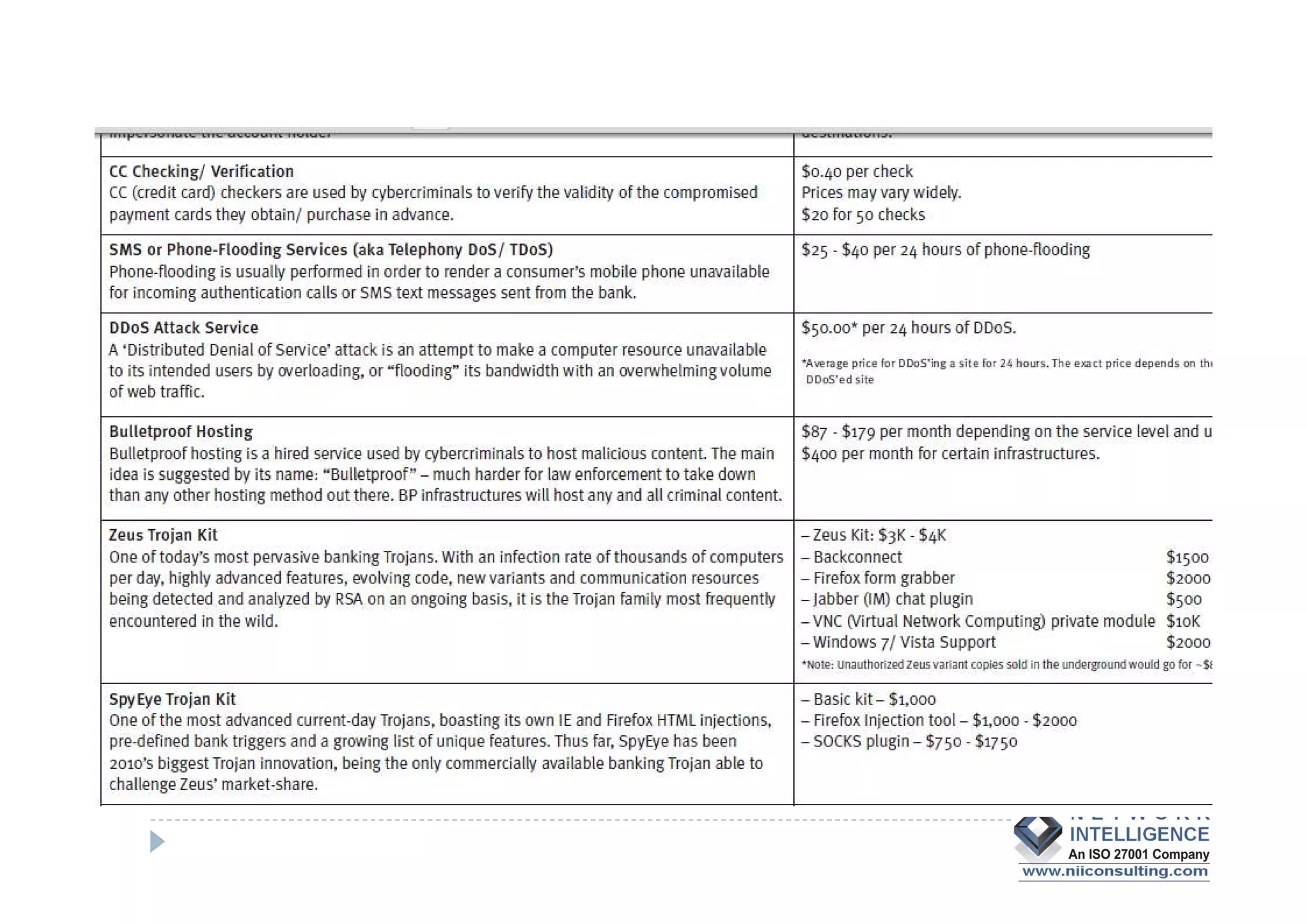
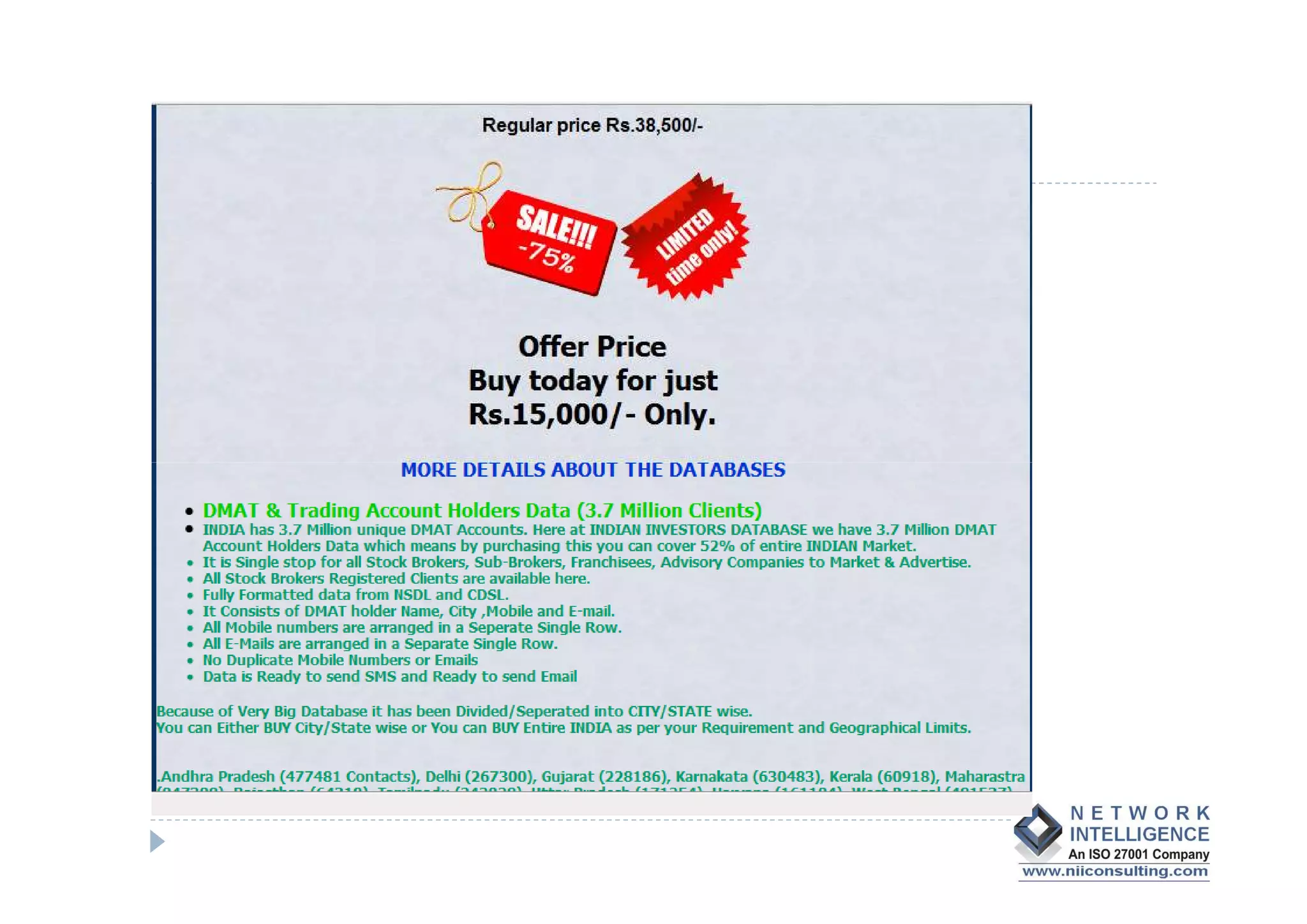
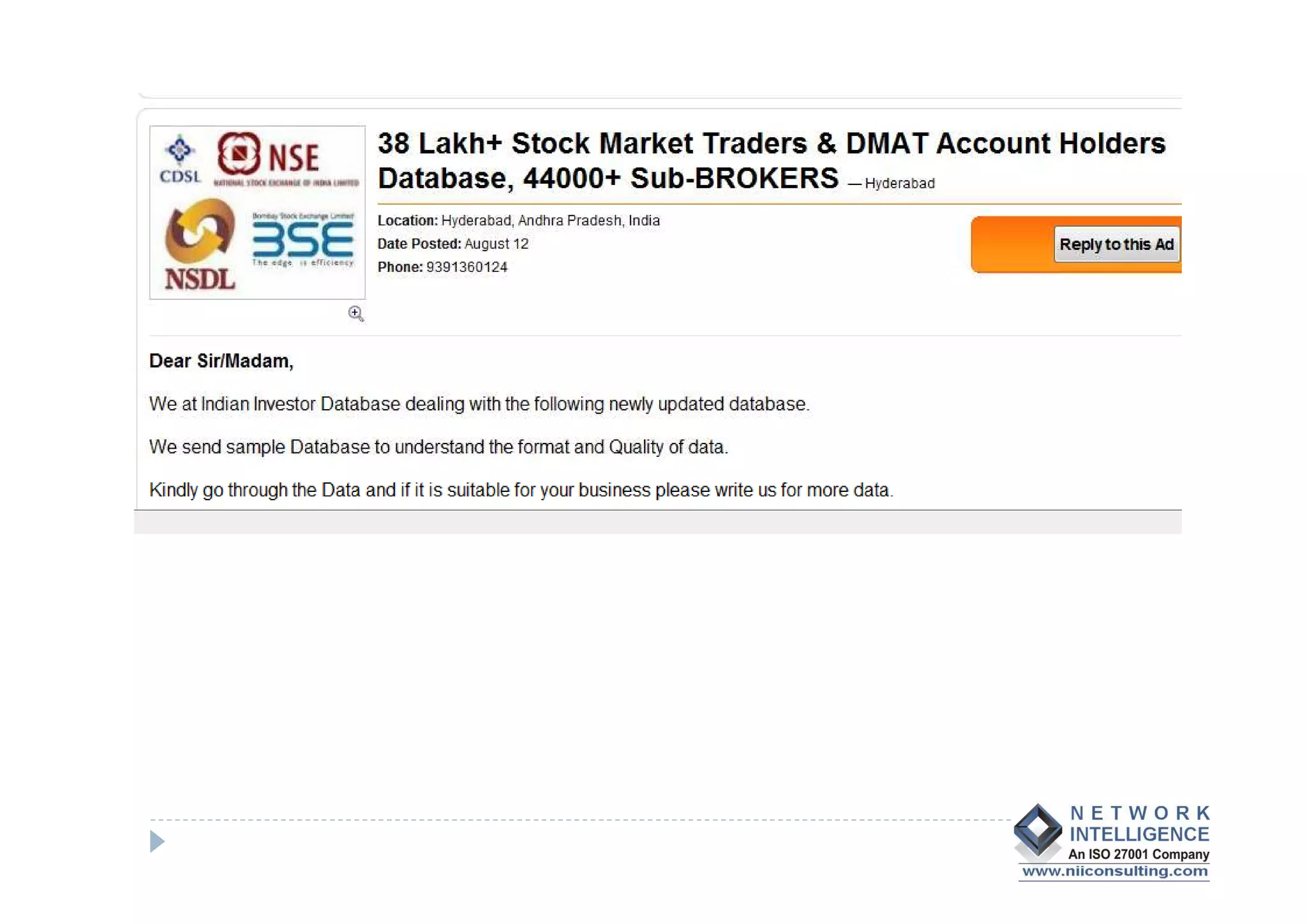
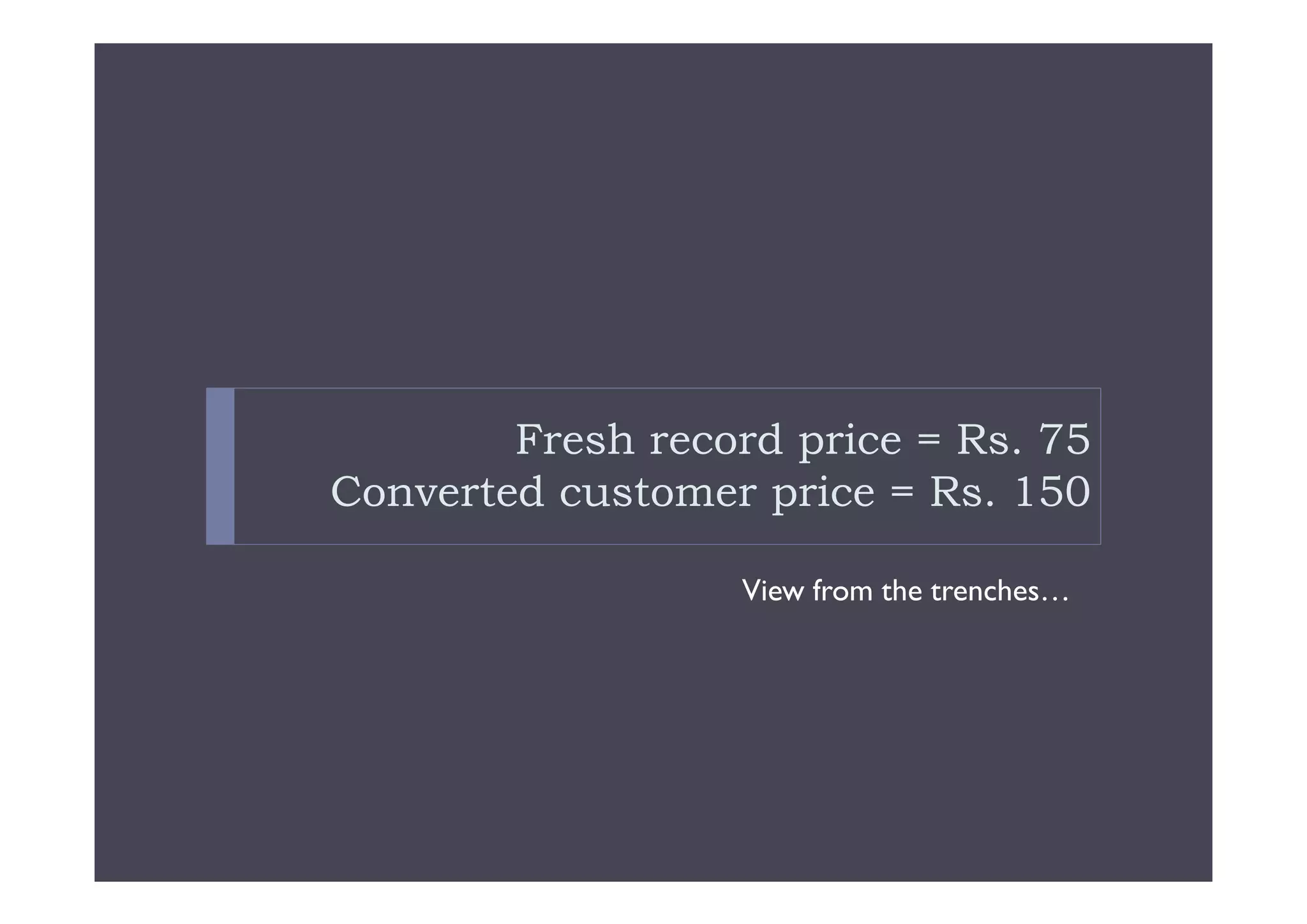
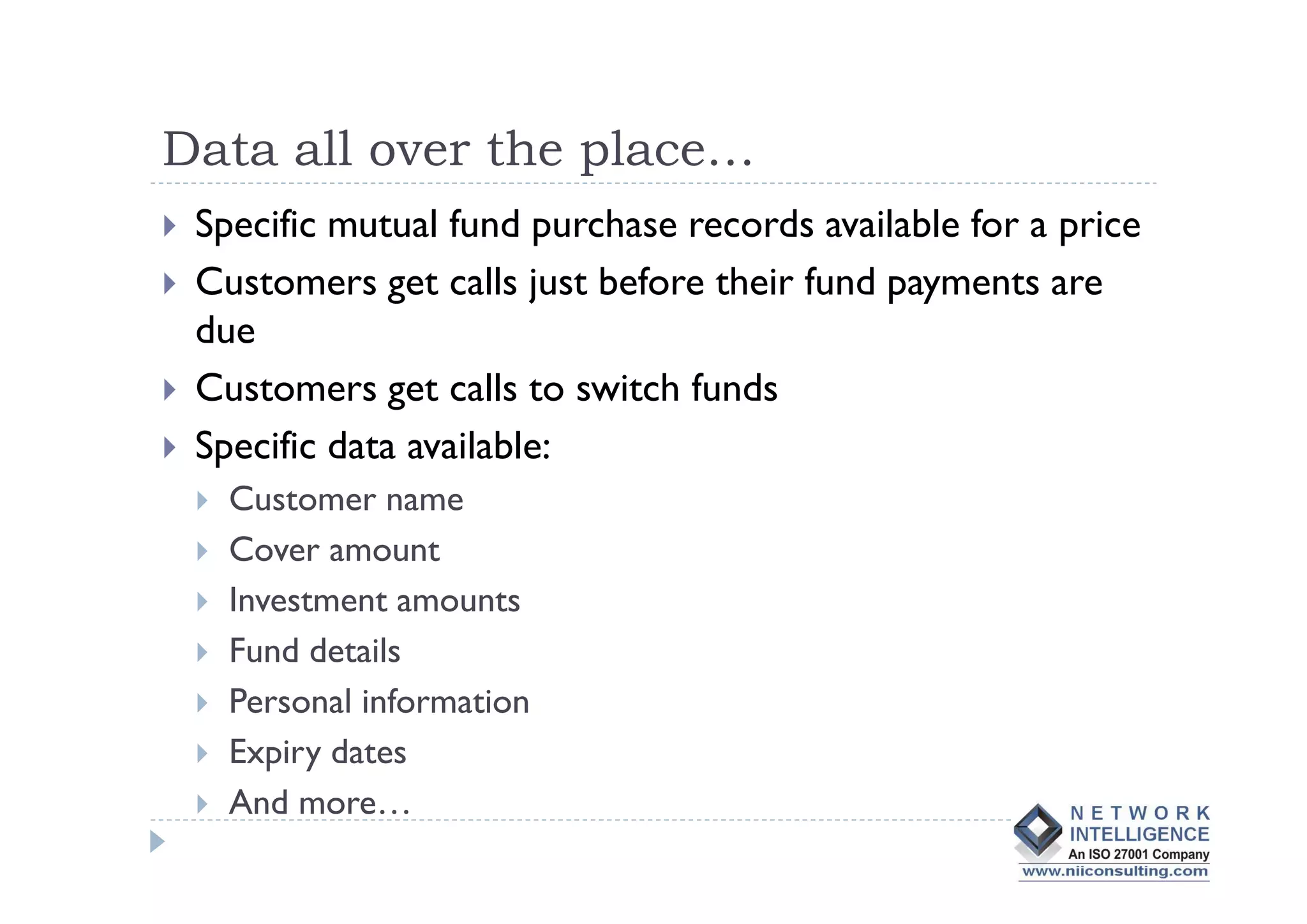
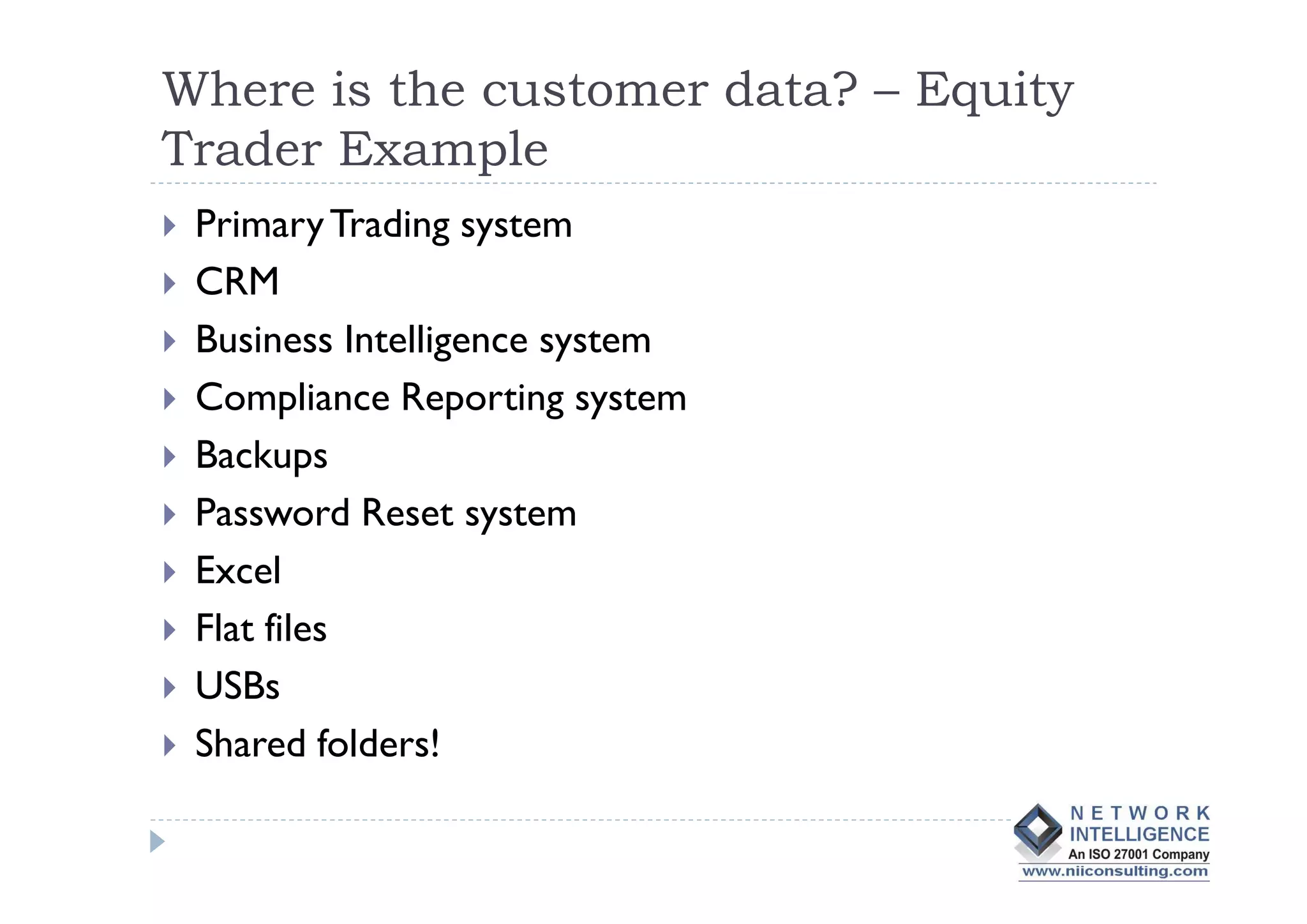
- Data theft of customer records from financial institutions is a serious and growing problem in India, with records being sold online for less than $0.01 each. Customer data is often not well protected and is spread across many different systems with broad access.
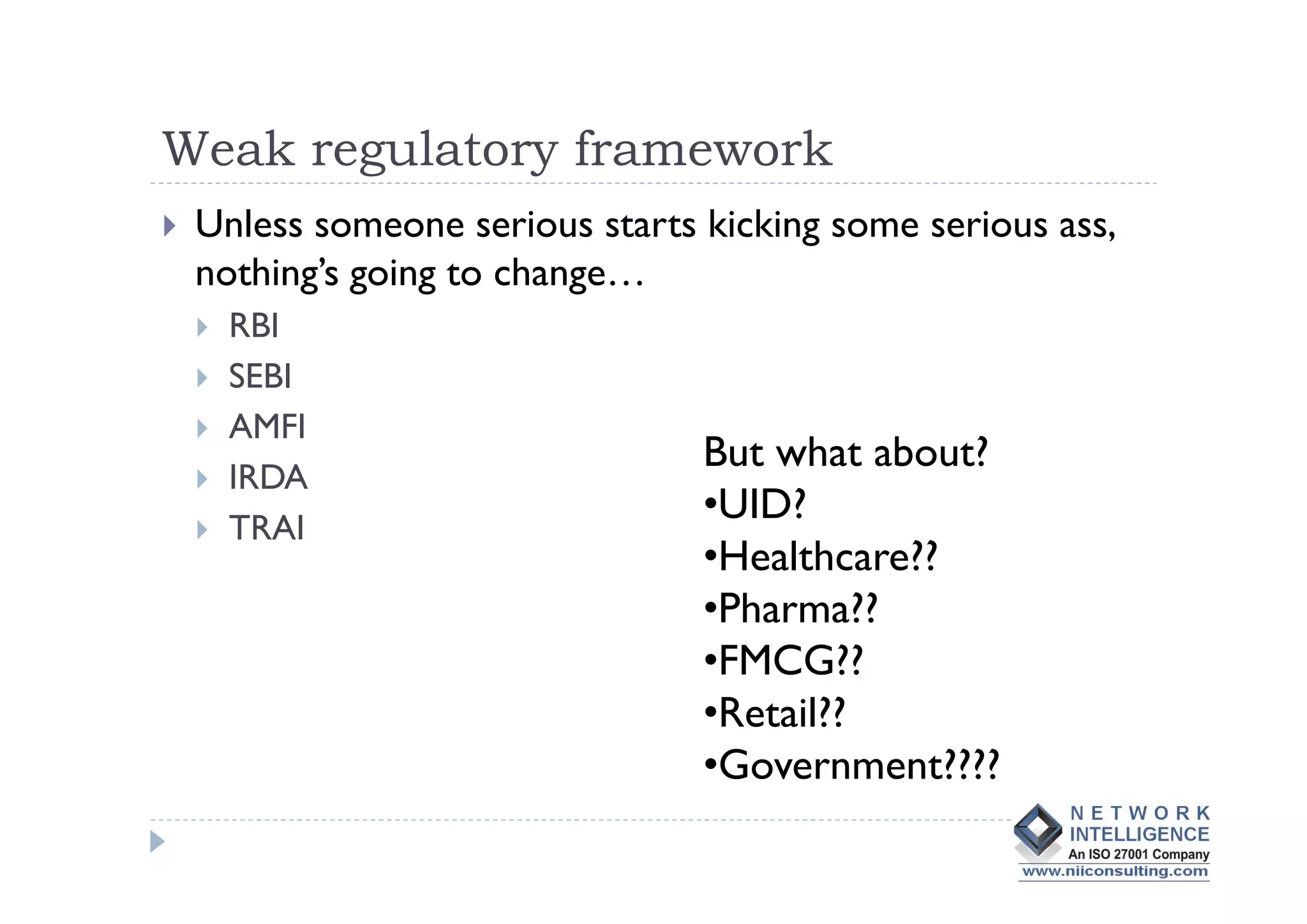
- Regulatory frameworks and enforcement are still weak, and many organizations do not prioritize data protection. Comprehensive solutions require changes to policies, processes, oversight of vendors, access controls, encryption, and other technologies. Stronger laws and regulations may also be needed to curb the problem.