The document presents a technical overview of JSON Web Tokens (JWT) and JavaScript Object Signing and Encryption (JOSE), detailing their functions as identity tokens. It discusses the structure and purpose of JWTs, including claims, and explains the use of JOSE for signing and encryption through JWS and JWE. Additionally, it introduces jose4j, an open-source Java implementation of the JOSE specification, providing examples of its applications and advantages.



![4
jose4j Overview
• Open source (free as in beer) Java implementation of the JOSE specification suite
– Get yours at https://bitbucket.org/b_c/jose4j
• Relies solely on the JCA APIs for cryptography
• 100% (Dammit Mike!) 97.5% Algorithm Support
• Reference[able] implementation
– Fact checked the cookbook: http://tools.ietf.org/html/draft-ietf-jose-cookbook-02#appendix-A
• Completely free of intentional NSA backdoors
– (but I‟m open to “sponsorship” opportunities)
• Production ready: used throughout Ping Identity‟s products
• Rated the #1 JOSE implementation in the world (based on an unbiased survey of the library author‟s mother)
• Did I mention free? Easy too.
• All proceeds from sales go to a charity that provides comfort and support to dying
identity protocols living out their final days
• Take a stand against monoculture (did heartbleed teach us nothing?)
Copyright © 2014 Brian Campbell. All rights reserved.](https://image.slidesharecdn.com/iiw18-jose-can-you-see-4up-140506180415-phpapp01/75/JOSE-Can-You-See-4-2048.jpg)








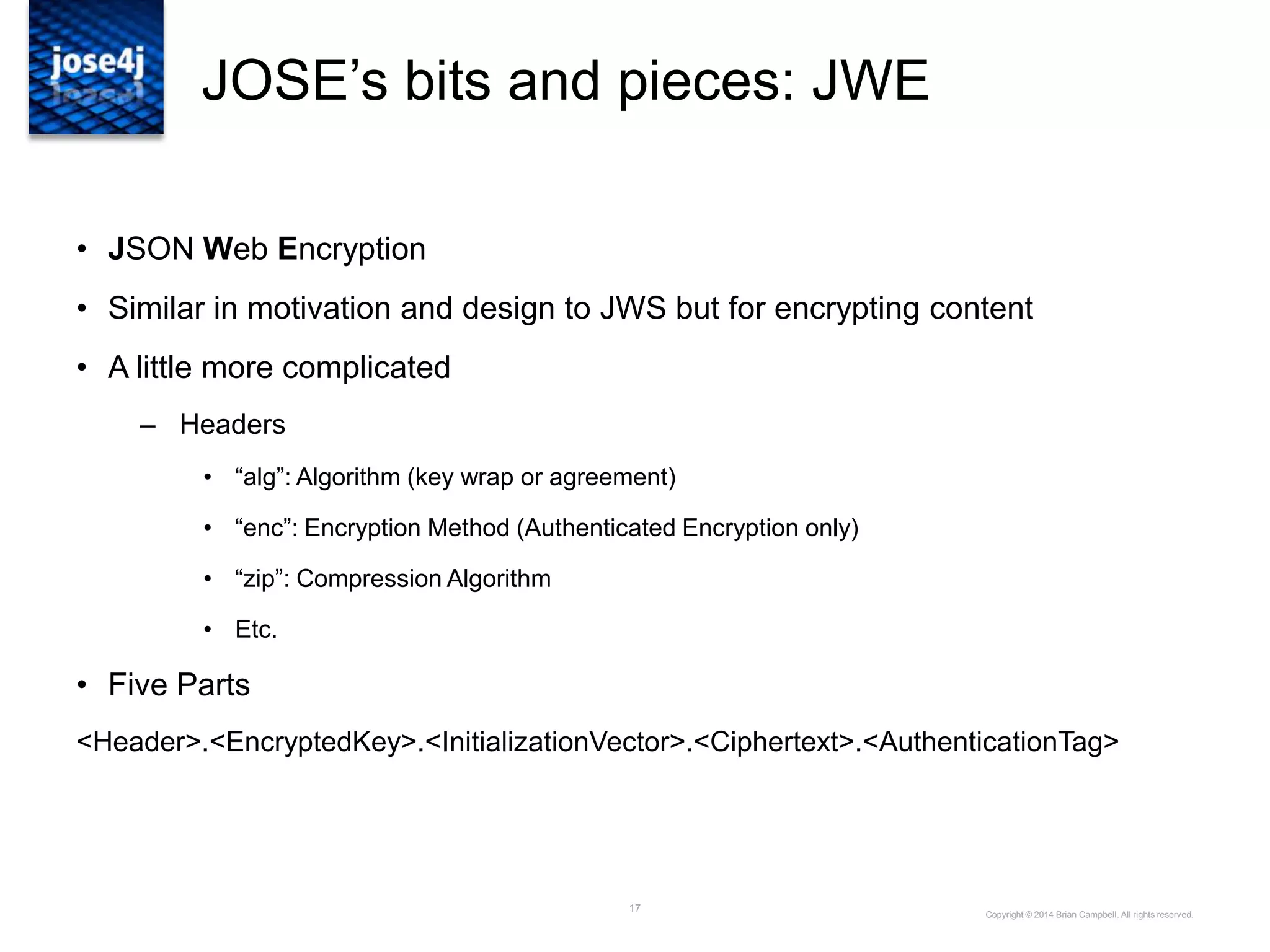
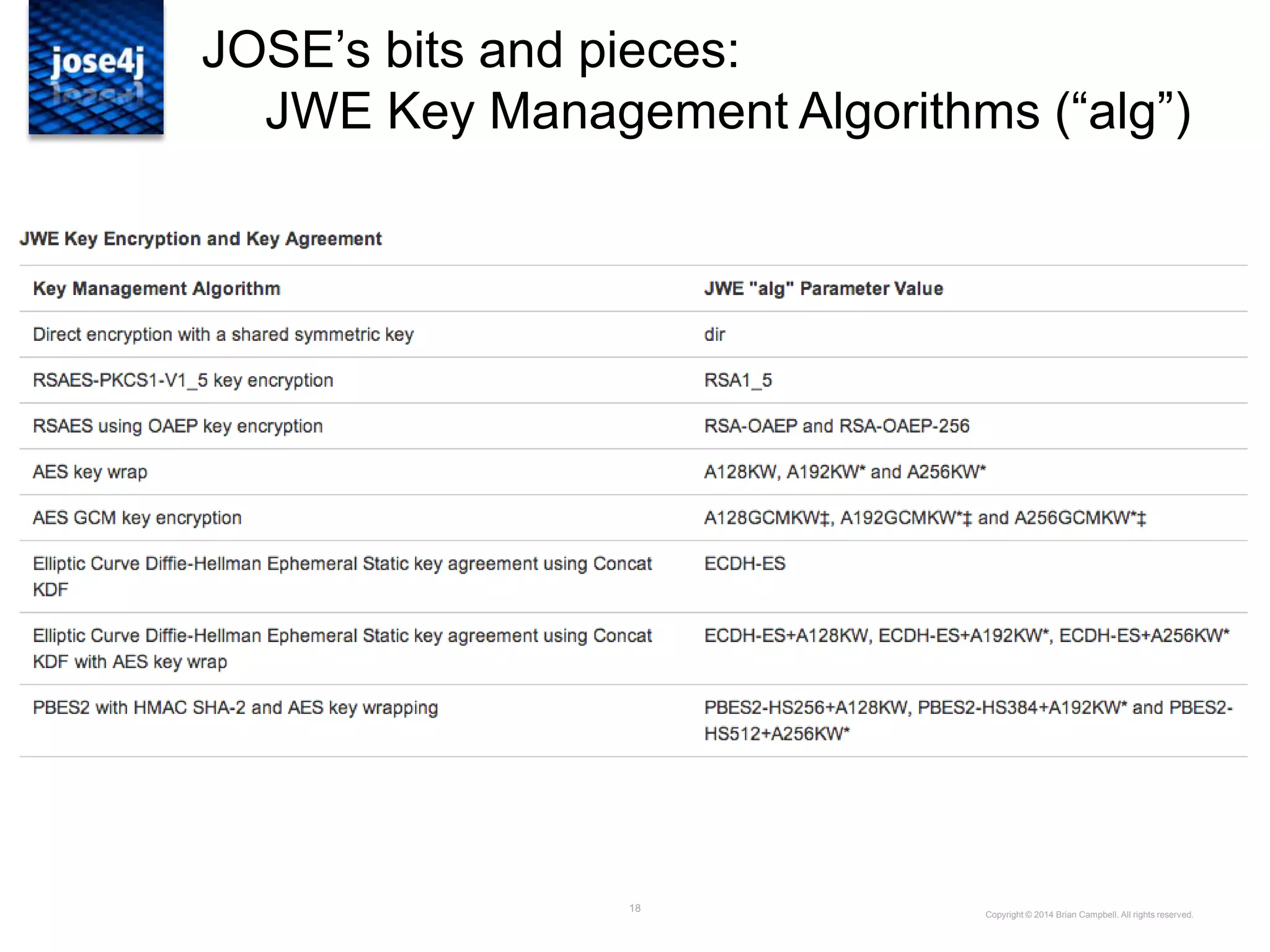
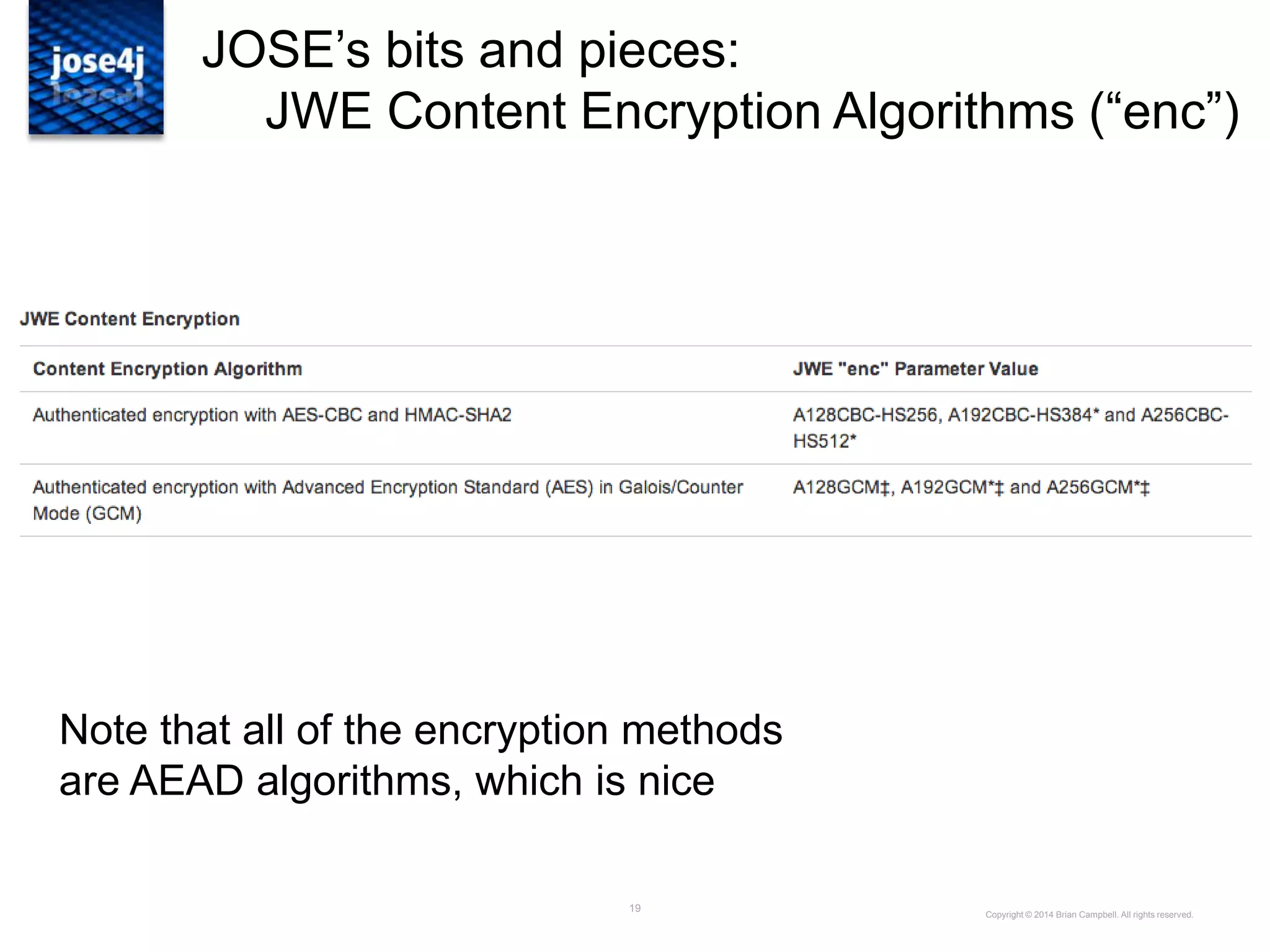






![29
JSON Web Key (JWK)
Copyright © 2014 Brian Campbell. All rights reserved.
• JSON data structure representing cryptographic key(s) which can be
– included in a JWS/JWE/JWT header
– saved in a file
– used in place of self signed certificates
– published at an HTTPS endpoint and referenced
JWT/JWS Header
{"kid":"5",
"alg":"ES256"}
{"keys":[
{"kty":"EC",
"kid":"4",
"x":"LX-7aQn7RAx3jDDTioNssbODUfED_6XvZP8NsGzMlRo",
"y":"dJbHEoeWzezPYuz6qjKJoRVLks7X8-BJXbewfyoJQ-A",
"crv":"P-256"},
{"kty":"EC",
"kid":"5",
"x":"f83OJ3D2xF1Bg8vub9tLe1gHMzV76e8Tus9uPHvRVEU",
"y":"x_FEzRu9m36HLN_tue659LNpXW6pCyStikYjKIWI5a0",
"crv":"P-256"},
{"kty":"EC",
"kid":"6",
"x":"J8z237wci2YJAzArSdWIj4OgrOCCfuZ18WI77jsiS00",
"y":"5tTxvax8aRMMJ4unKdKsV0wcf3pOI3OG771gOa45wBU",
"crv":"P-256"}
]}](https://image.slidesharecdn.com/iiw18-jose-can-you-see-4up-140506180415-phpapp01/75/JOSE-Can-You-See-29-2048.jpg)

![31
Consuming a JWKS using jose4j
Copyright © 2014 Brian Campbell. All rights reserved.
String jwksJson =
"{"keys":[n" +
" {"kty":"EC",n"kid":"4",n" +
" "x":"LX-7aQn7RAx3jDDTioNssbODUfED_6XvZP8NsGzMlRo", n" +
" "y":"dJbHEoeWzezPYuz6qjKJoRVLks7X8-BJXbewfyoJQ-A",n" +
" "crv":"P-256"},n" +
" {"kty":"EC",n"kid":"5",n" +
" "x":"f83OJ3D2xF1Bg8vub9tLe1gHMzV76e8Tus9uPHvRVEU",n" +
" "y":"x_FEzRu9m36HLN_tue659LNpXW6pCyStikYjKIWI5a0",n" +
" "crv":"P-256"},n" +
" {"kty":"EC",n"kid":"6",n" +
" "x":"J8z237wci2YJAzArSdWIj4OgrOCCfuZ18WI77jsiS00",n" +
" "y":"5tTxvax8aRMMJ4unKdKsV0wcf3pOI3OG771gOa45wBU",n" +
" "crv":"P-256"}n" +
"]}";
JsonWebKeySet jwks = new JsonWebKeySet(jwksJson);
JsonWebKey jwk = jwks.findJsonWebKey("5", null, null, null);
System.out.println(jwk.getKey());](https://image.slidesharecdn.com/iiw18-jose-can-you-see-4up-140506180415-phpapp01/75/JOSE-Can-You-See-31-2048.jpg)

