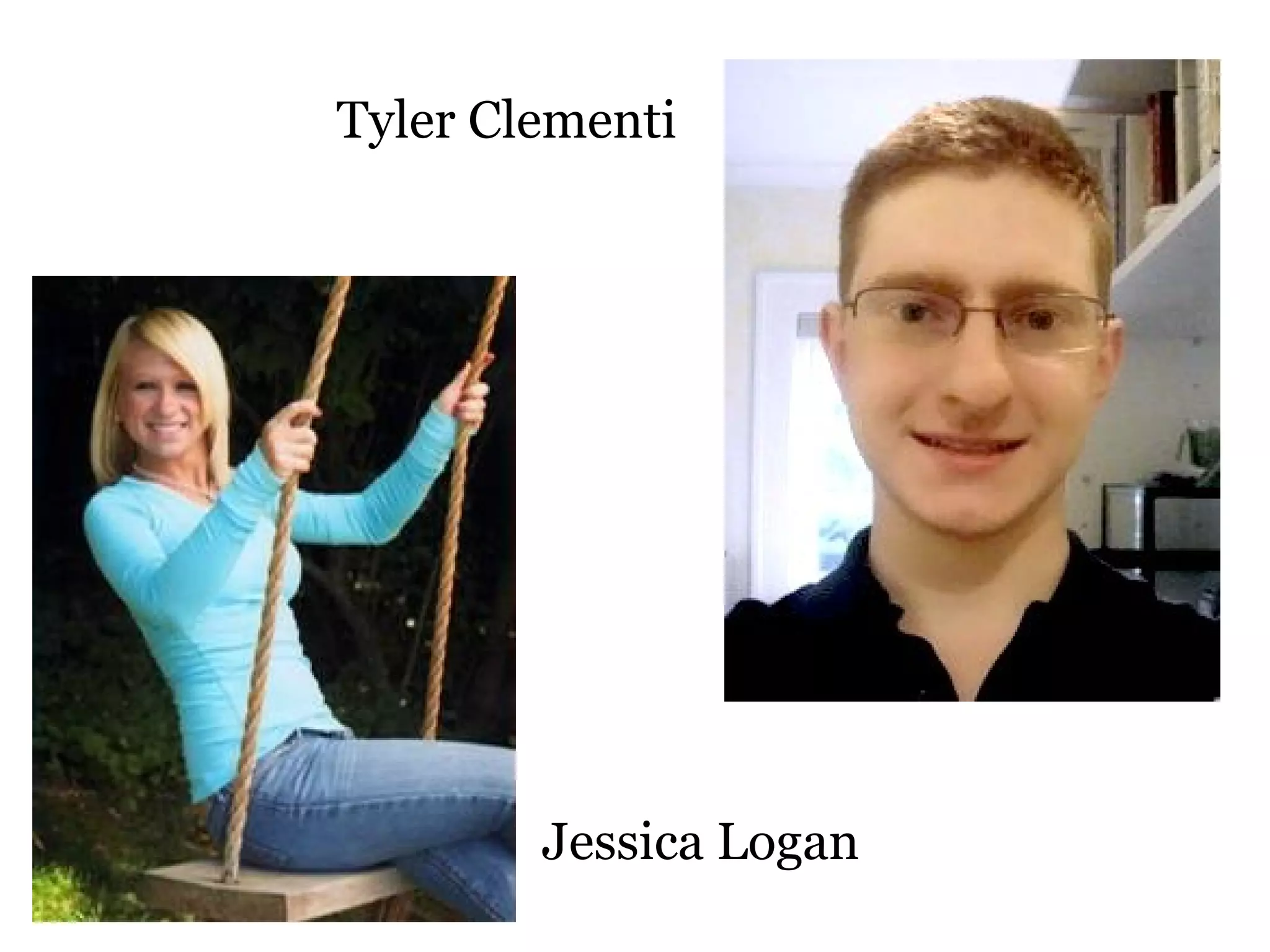
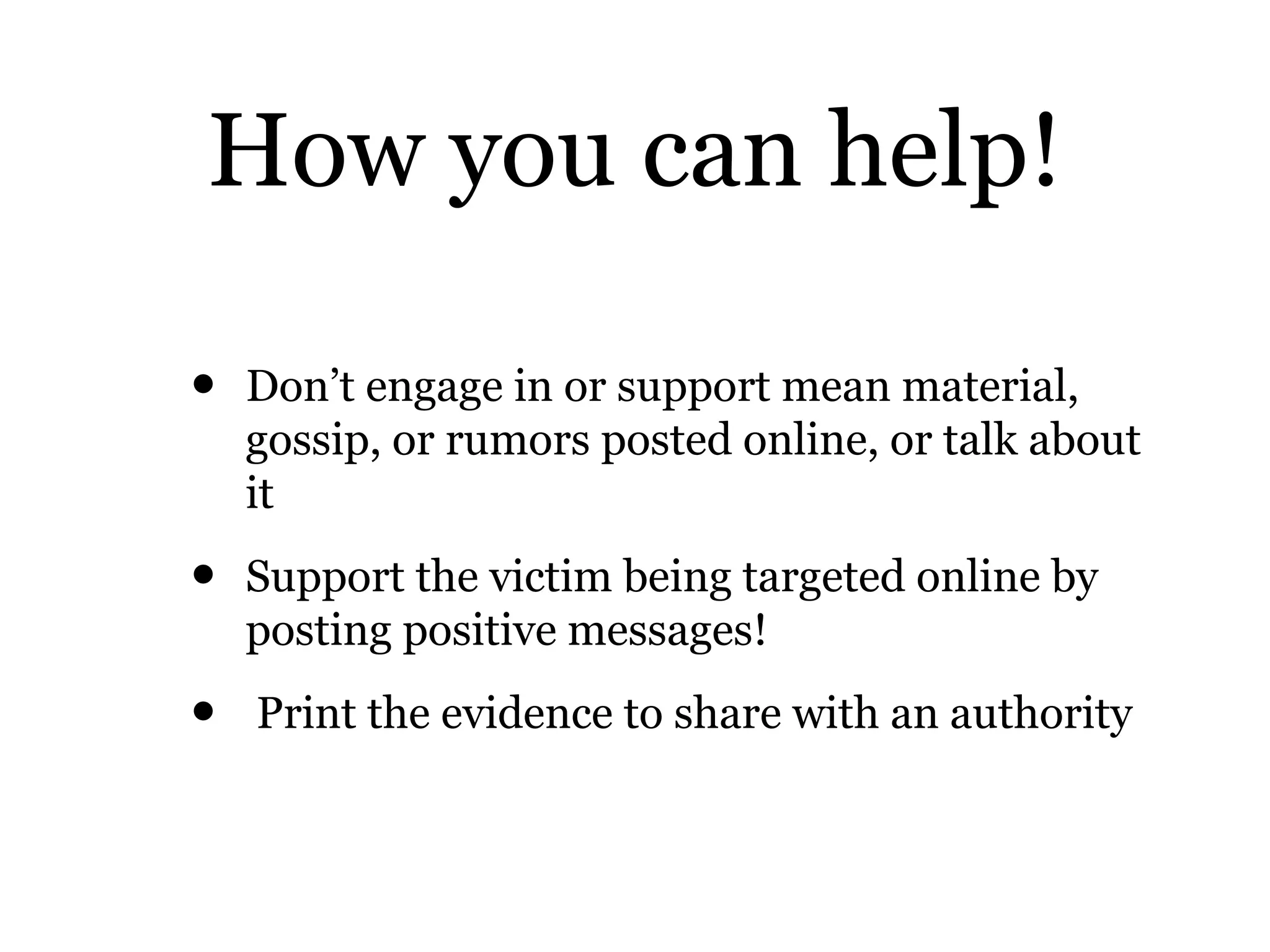
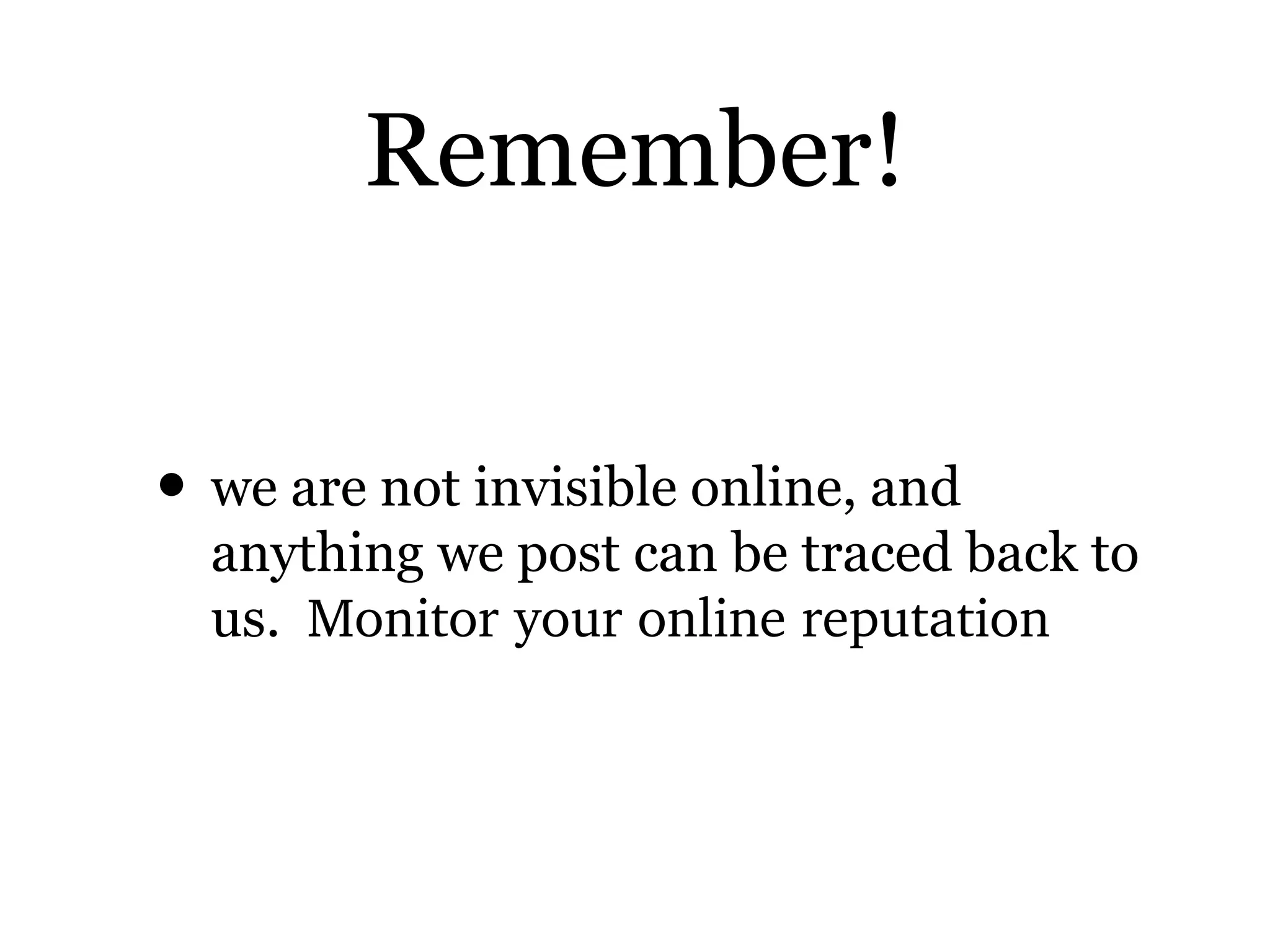
Cyberbullying involves bullying using electronic technology. Around half of teens have experienced cyberbullying, but only 1 in 10 tells their parents. Common causes include seeking revenge, entertainment, boosting ego, or social standing. Effects can include undermining confidence, poor school performance, stress, and even suicidal thoughts. While both genders engage in cyberbullying, females are twice as likely as males to be victims or perpetrators. New laws require schools to address cyberbullying and train staff to identify and prevent it.