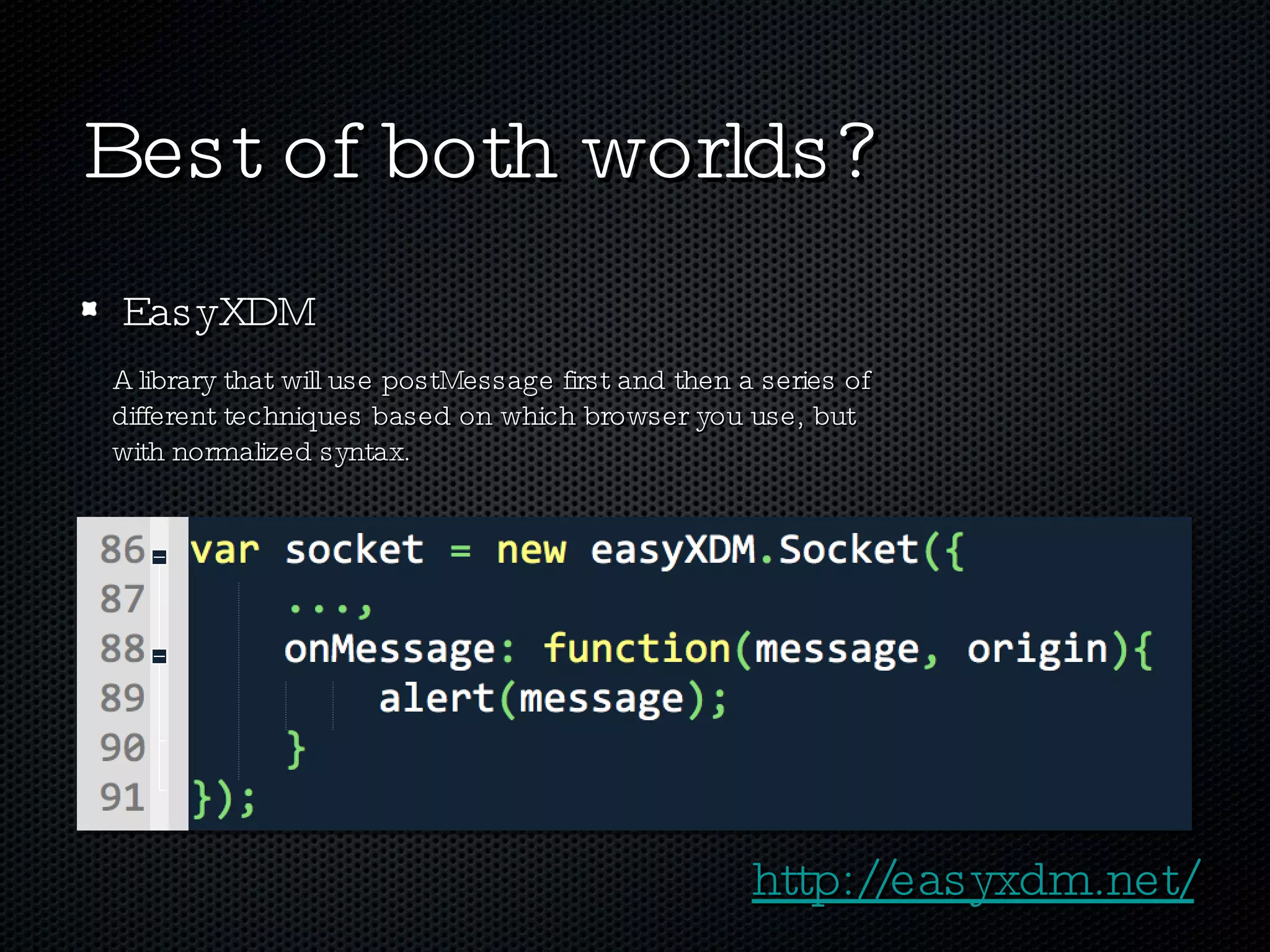
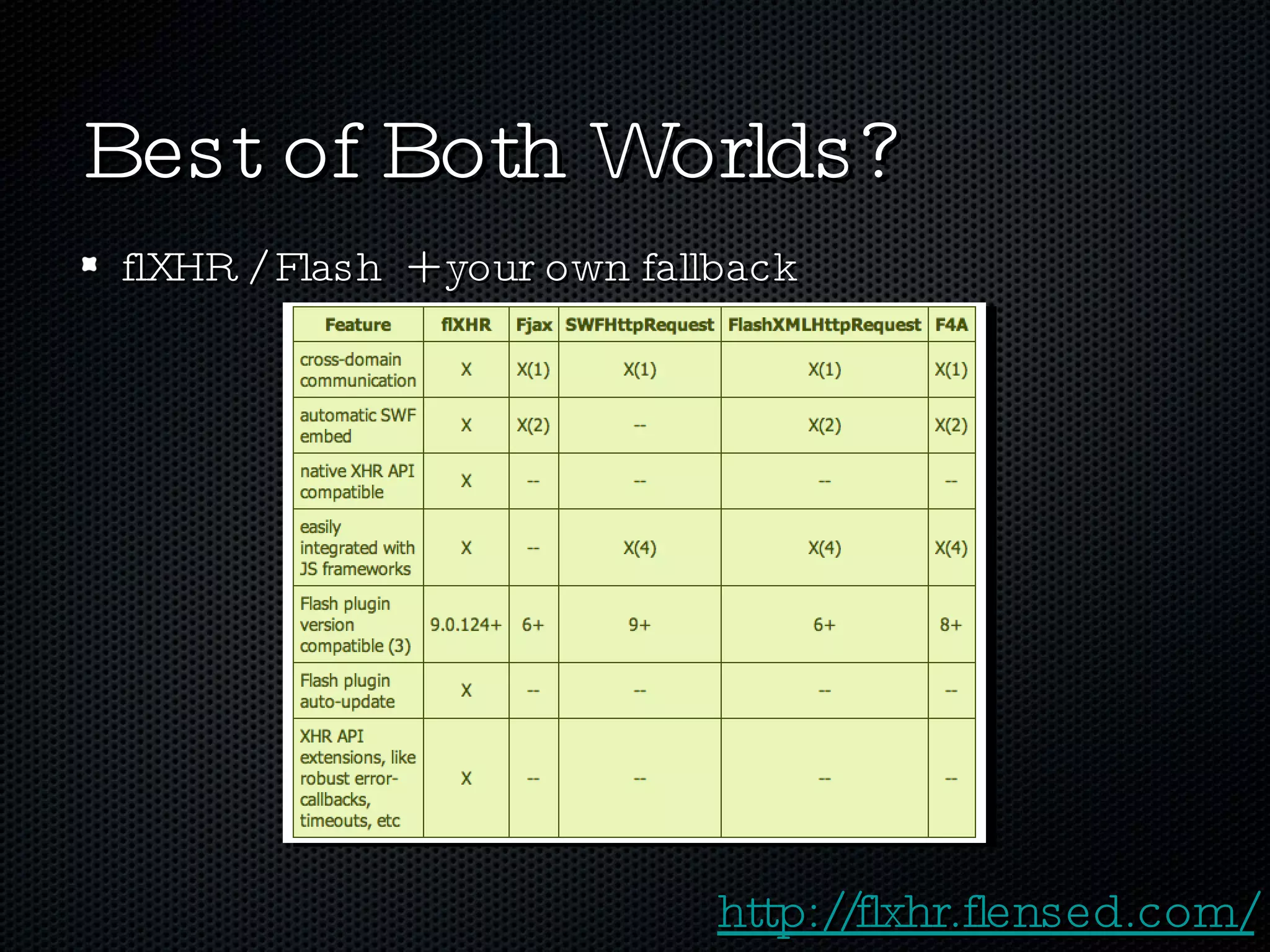
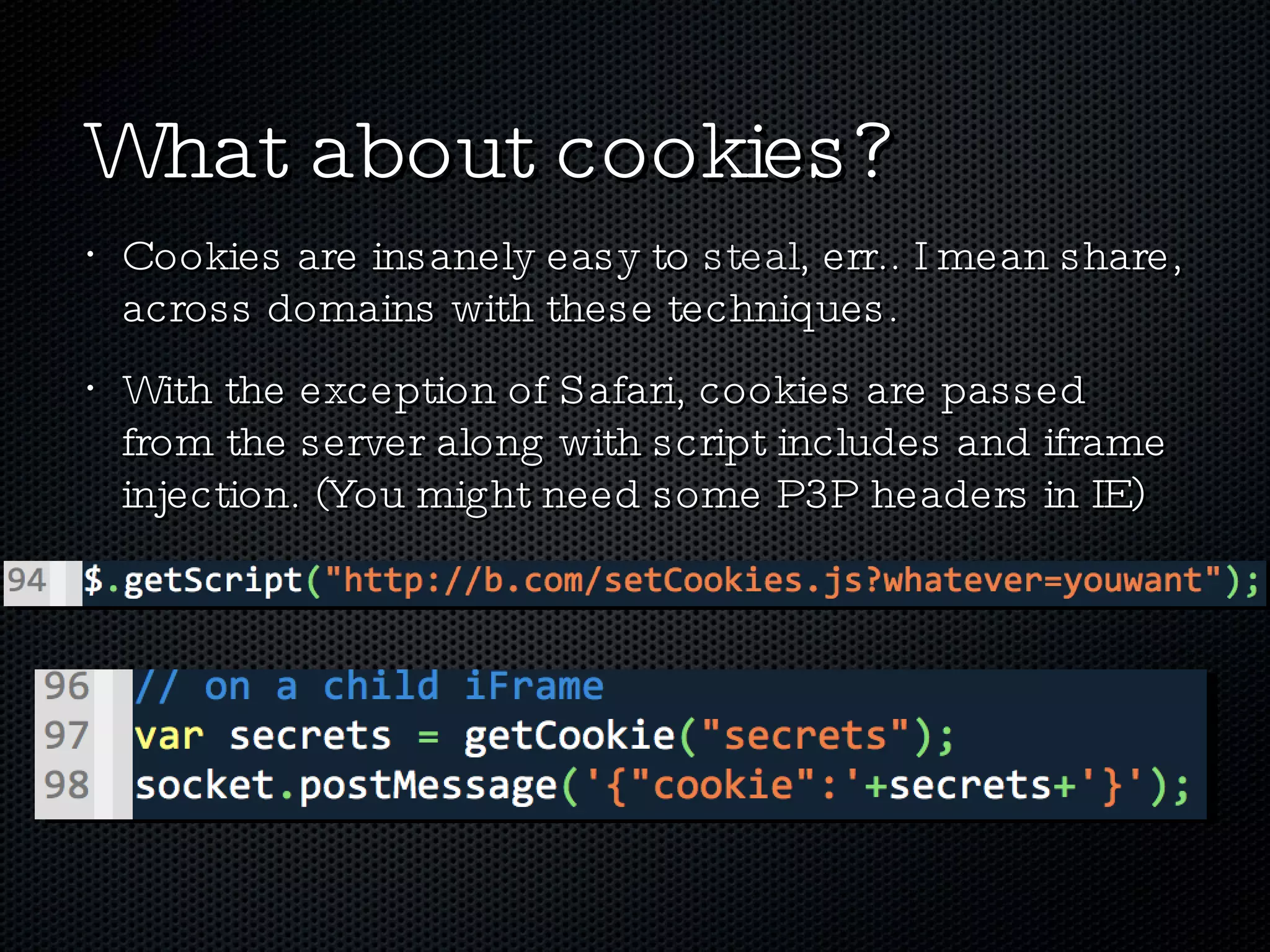
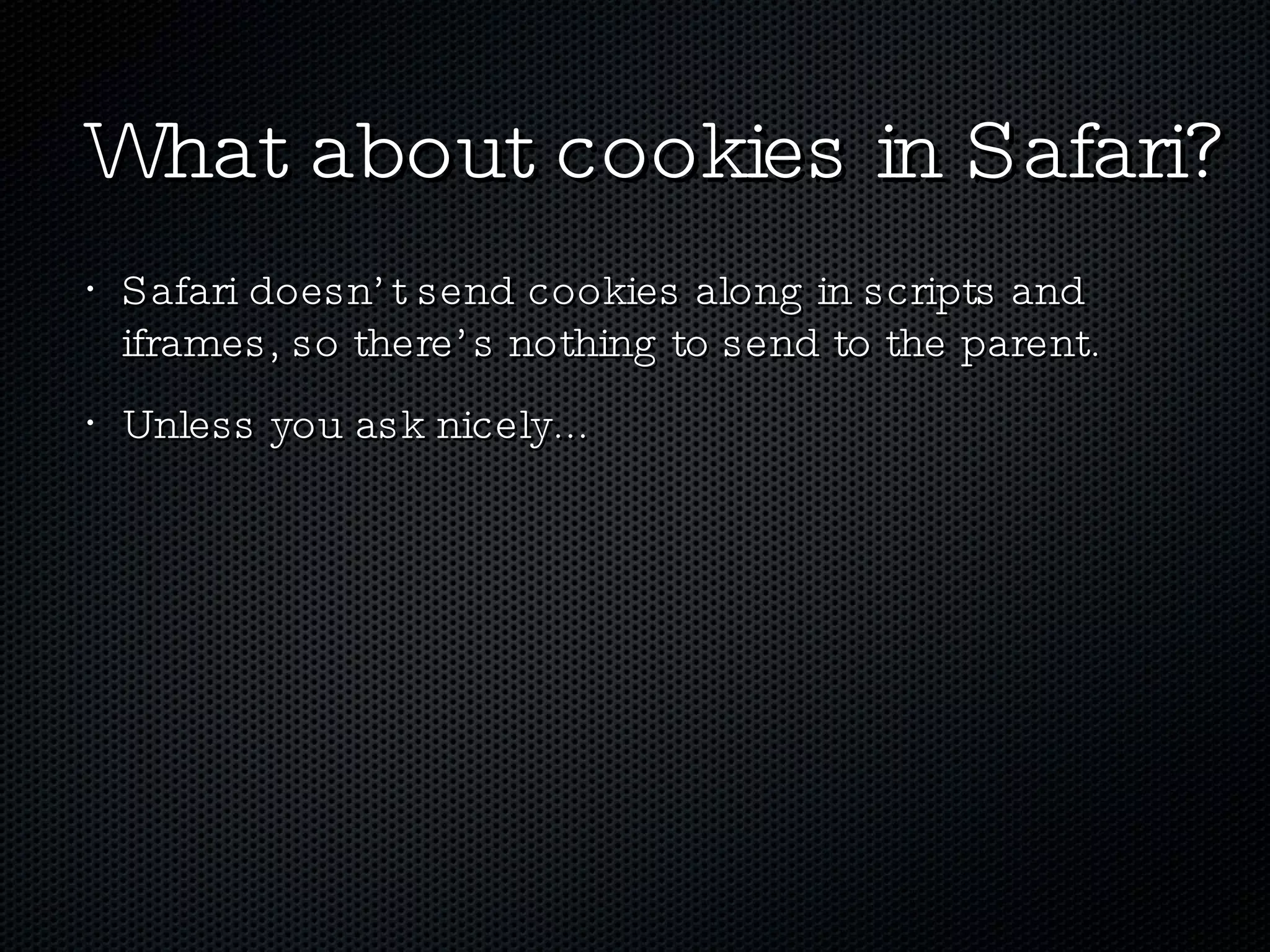
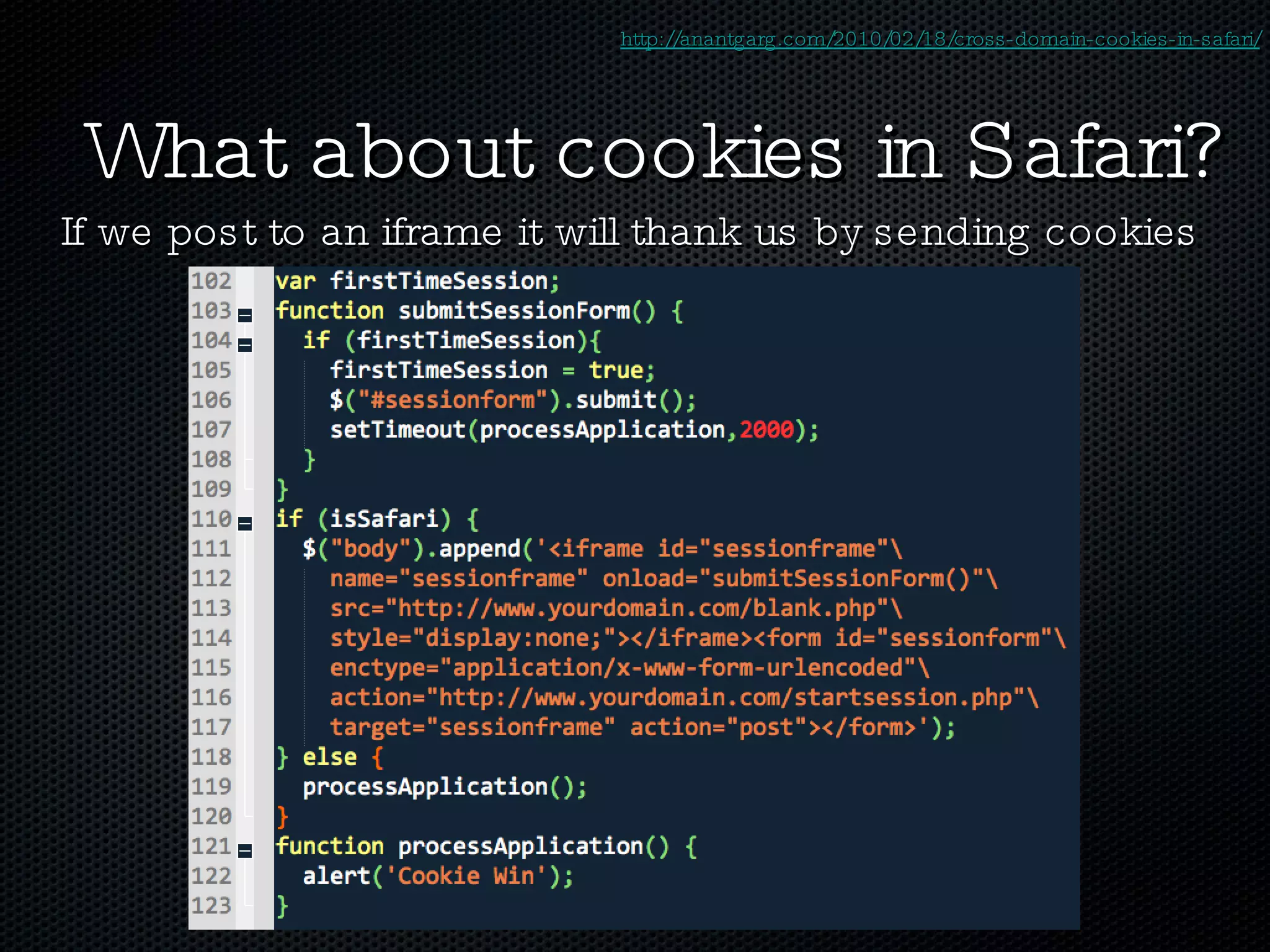
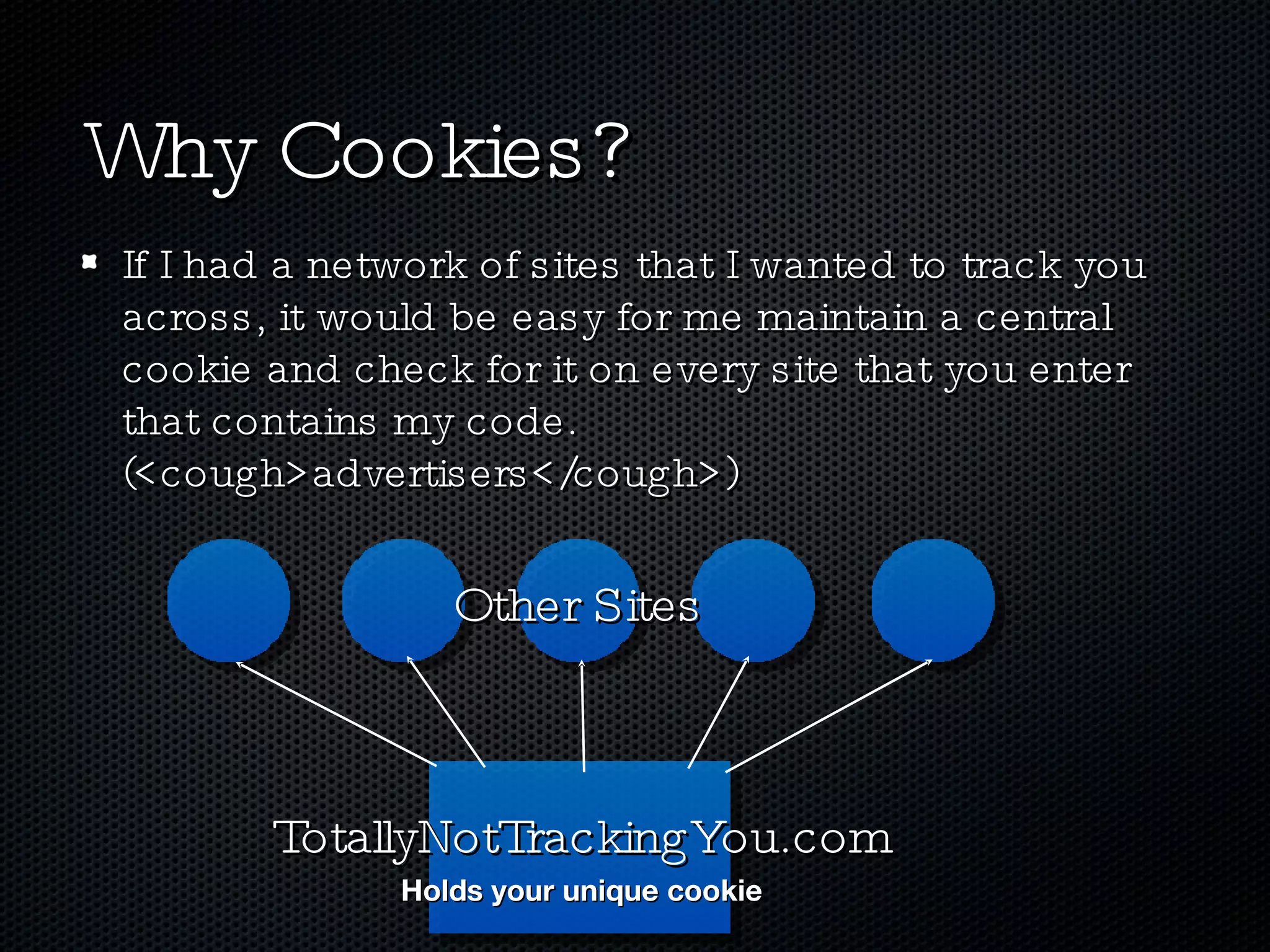
The document discusses various techniques for enabling cross-domain communication, particularly in web development, and highlights the importance of the Same-Origin Policy that protects data from unauthorized access. It explores methods like PostMessage, JSONP, CORS, and various hacky solutions, noting their advantages and limitations across different browsers. The document emphasizes that while cross-domain communication can be simplified, it also introduces significant security risks.















![Thanks! Alex Sexton AlexSexton [at] gmail [dot] com @SlexAxton http://yayQuery.com Special Thanks to : yayQuery Peeps, BazaarVoice, Aaron Dixon, Shawn Smith, EasyXDM, flXHR, Mozilla MDC](https://image.slidesharecdn.com/xdbarrier-100605150515-phpapp02/75/Breaking-The-Cross-Domain-Barrier-47-2048.jpg)