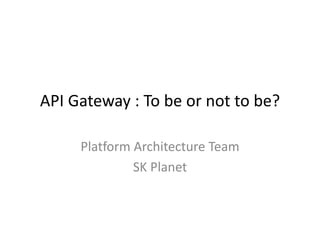
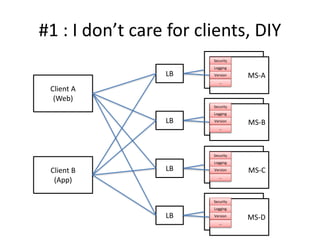
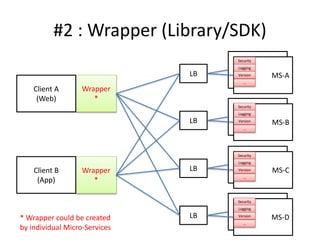
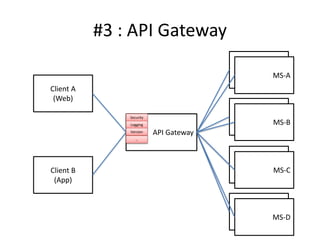
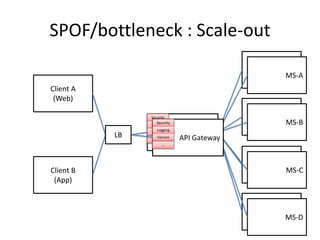
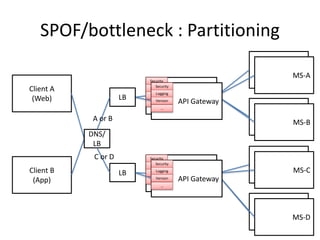
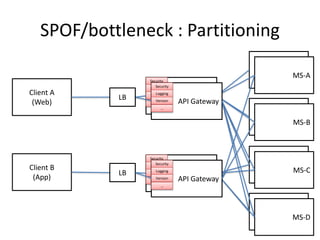
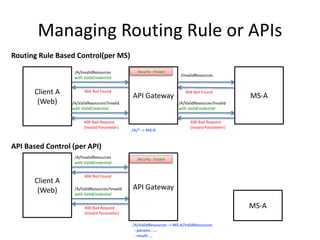
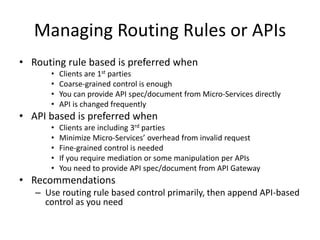
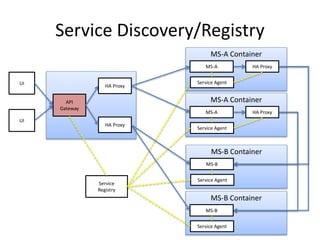
The document discusses different approaches for client access to micro-services in a micro-services architecture, focusing on DIY clients, wrappers, and API gateways. Each solution has its own pros and cons regarding complexity, security, manageability, and performance. Ultimately, while API gateways can introduce additional costs and potential bottlenecks, they are often recommended for better management and organization of service interactions.