1. DNSSEC introduces additional complexity for monitoring domains that requires testing for DNSSEC-specific issues like signature and key expiration.
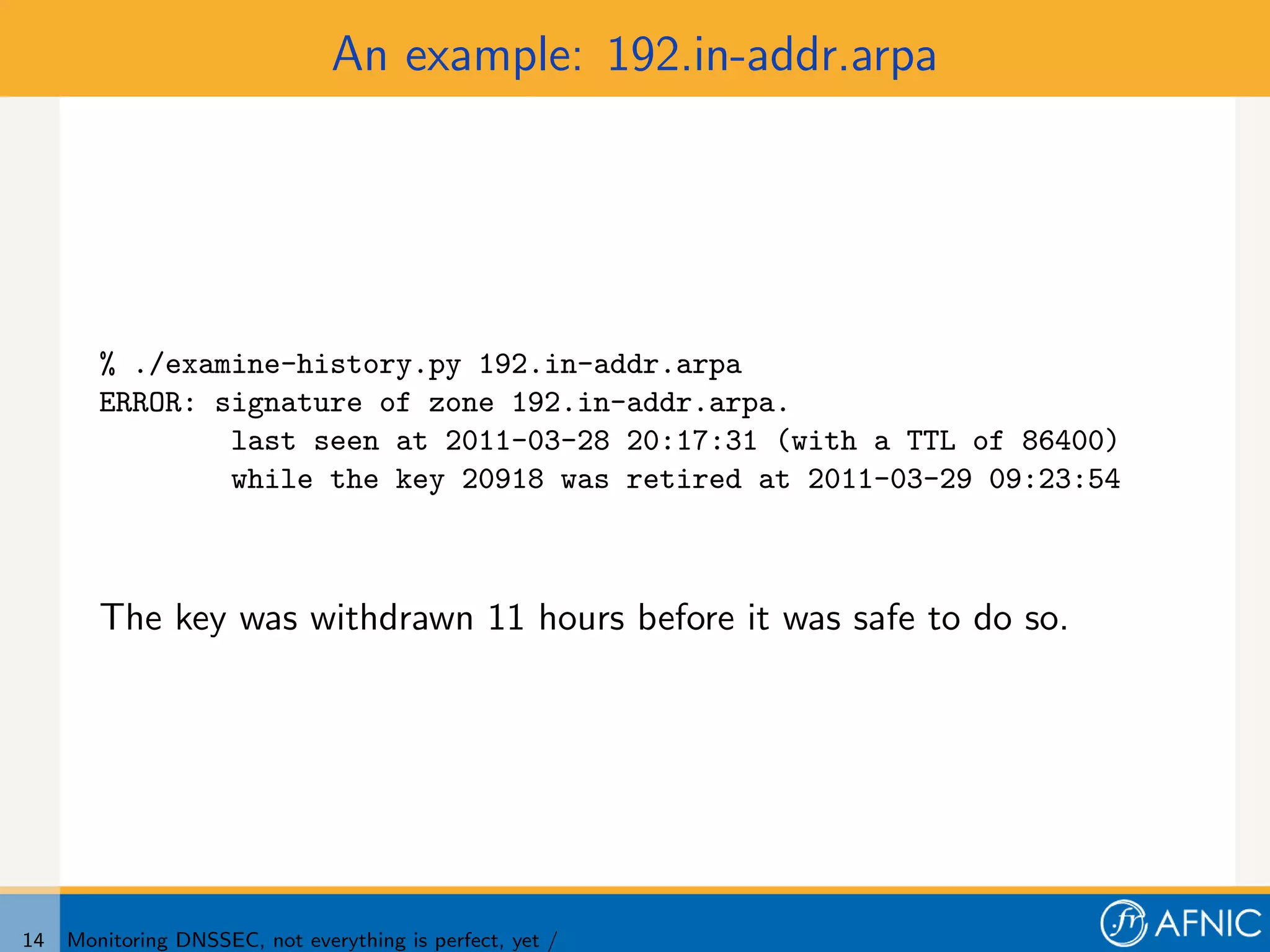
2. An example of monitoring issues in .FR include a key deletion that made the zone no longer signed which monitoring did not detect, and two other signature errors that revealed gaps in the monitoring.
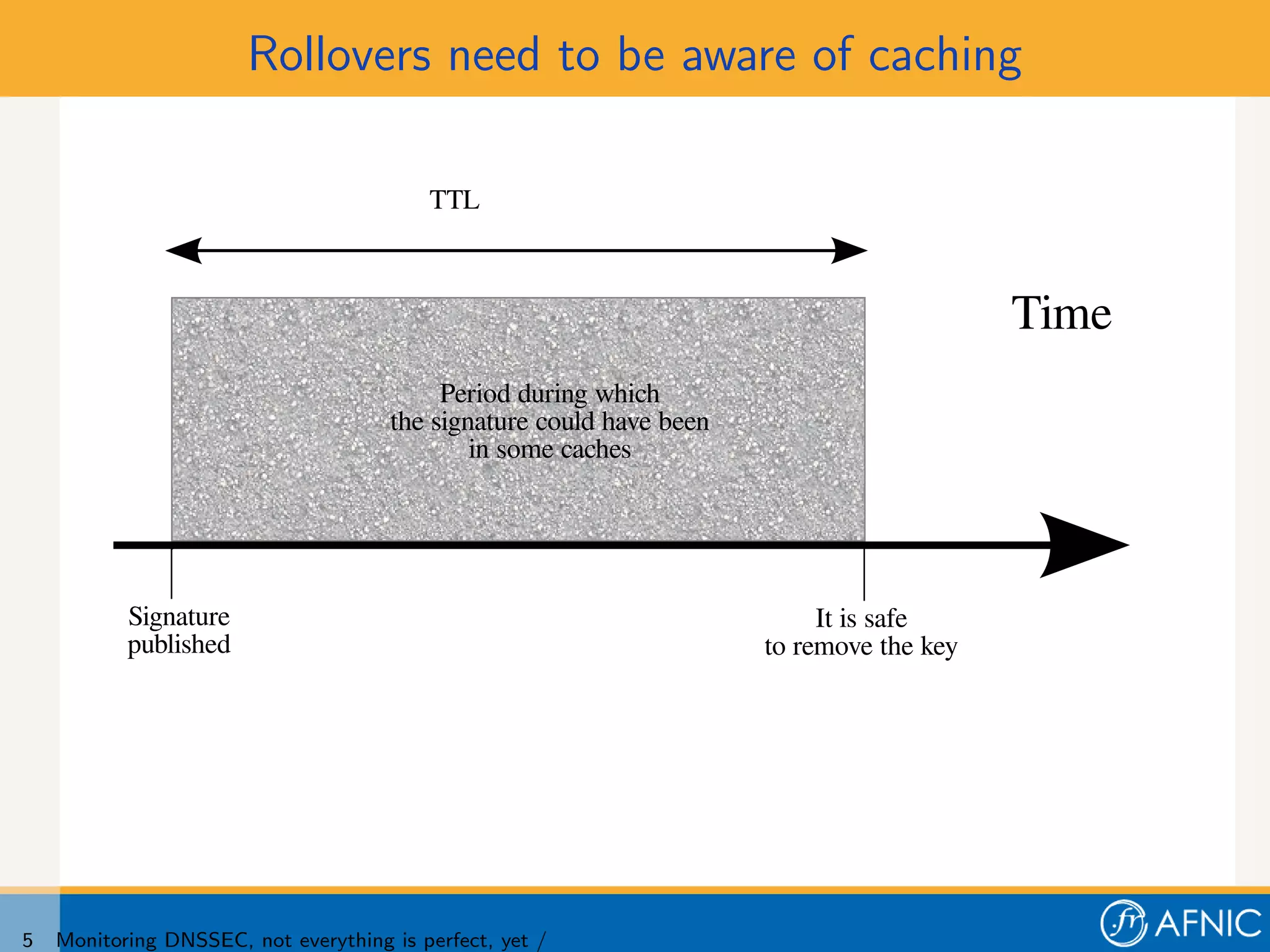
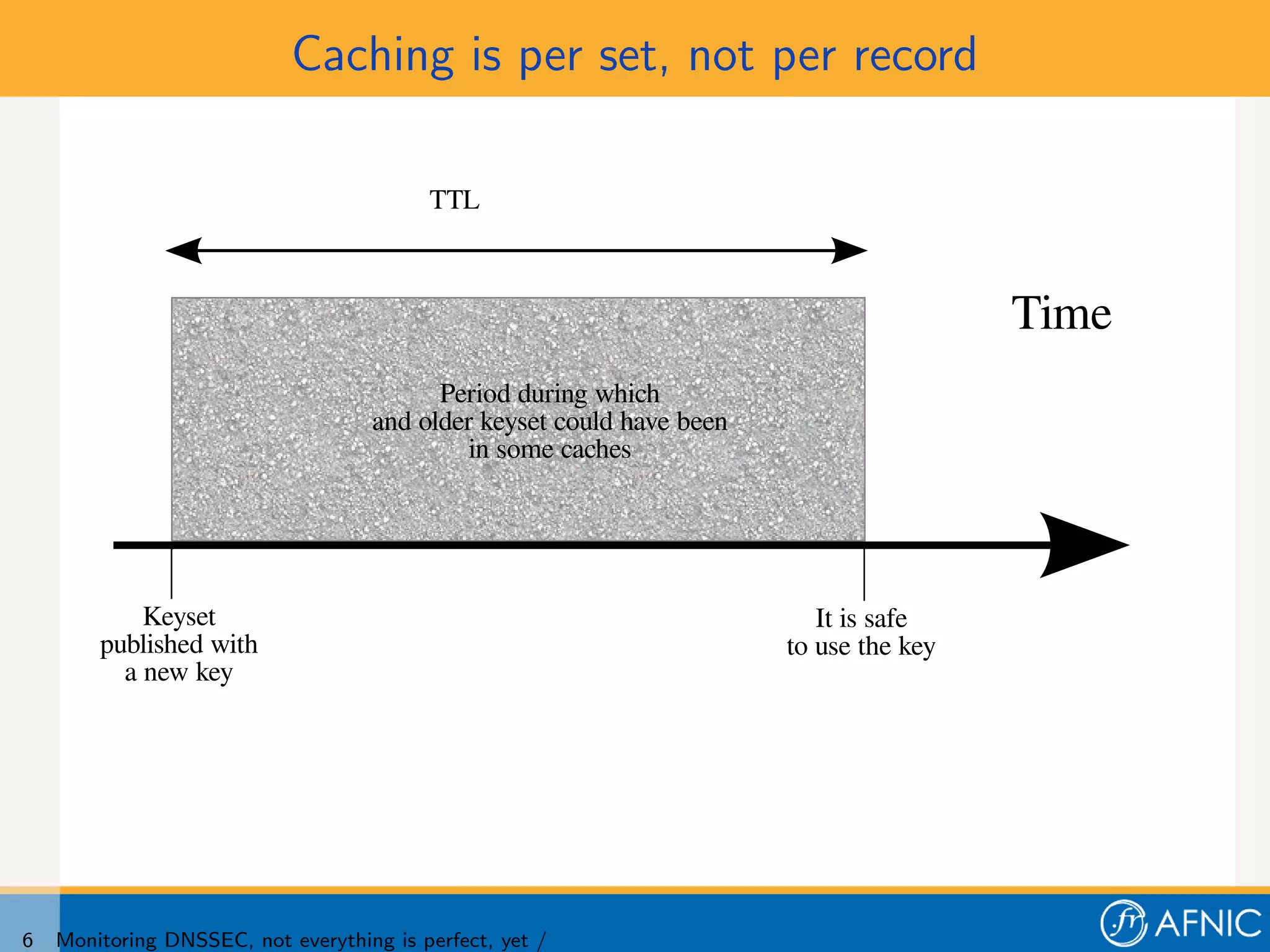
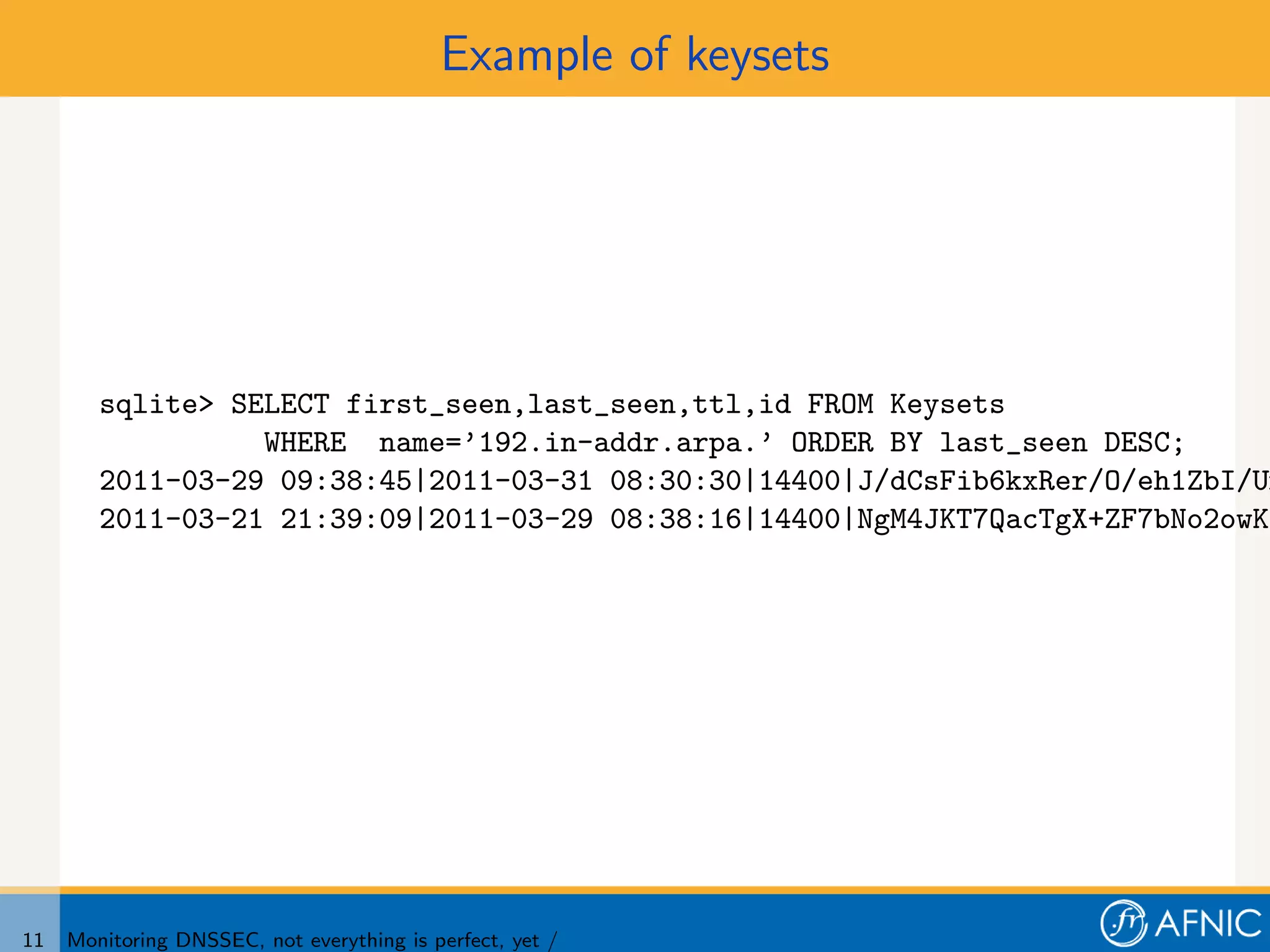
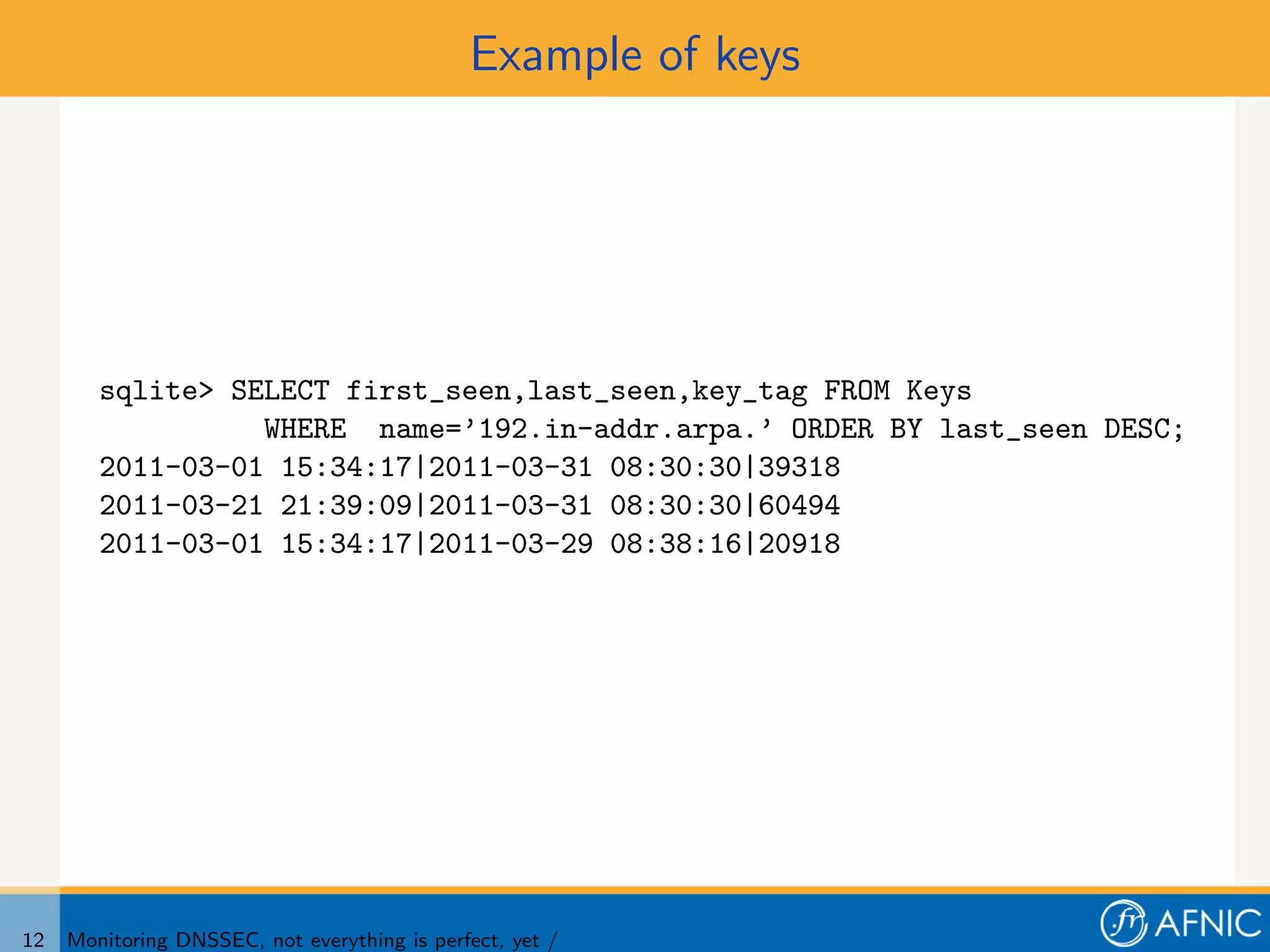
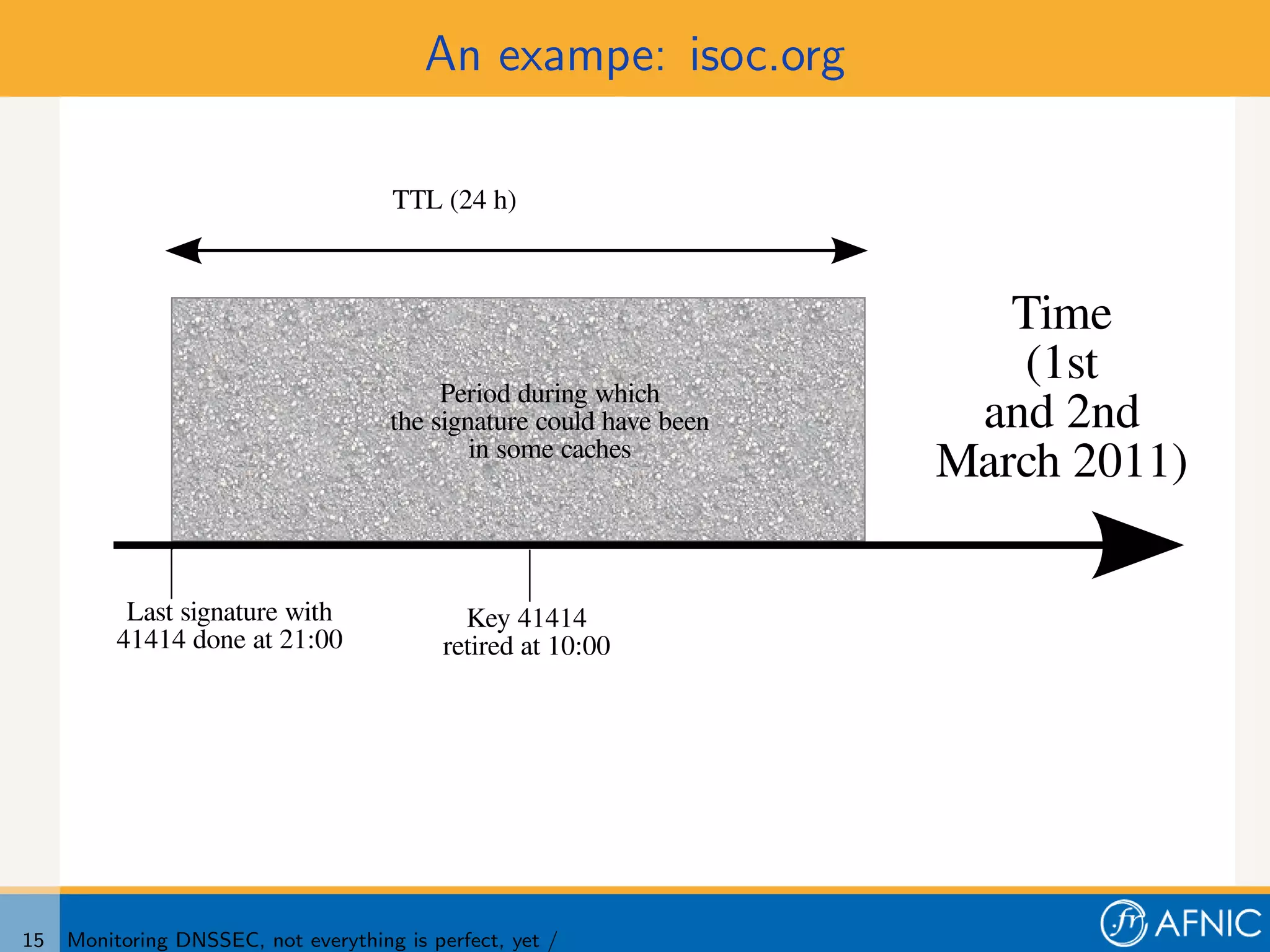
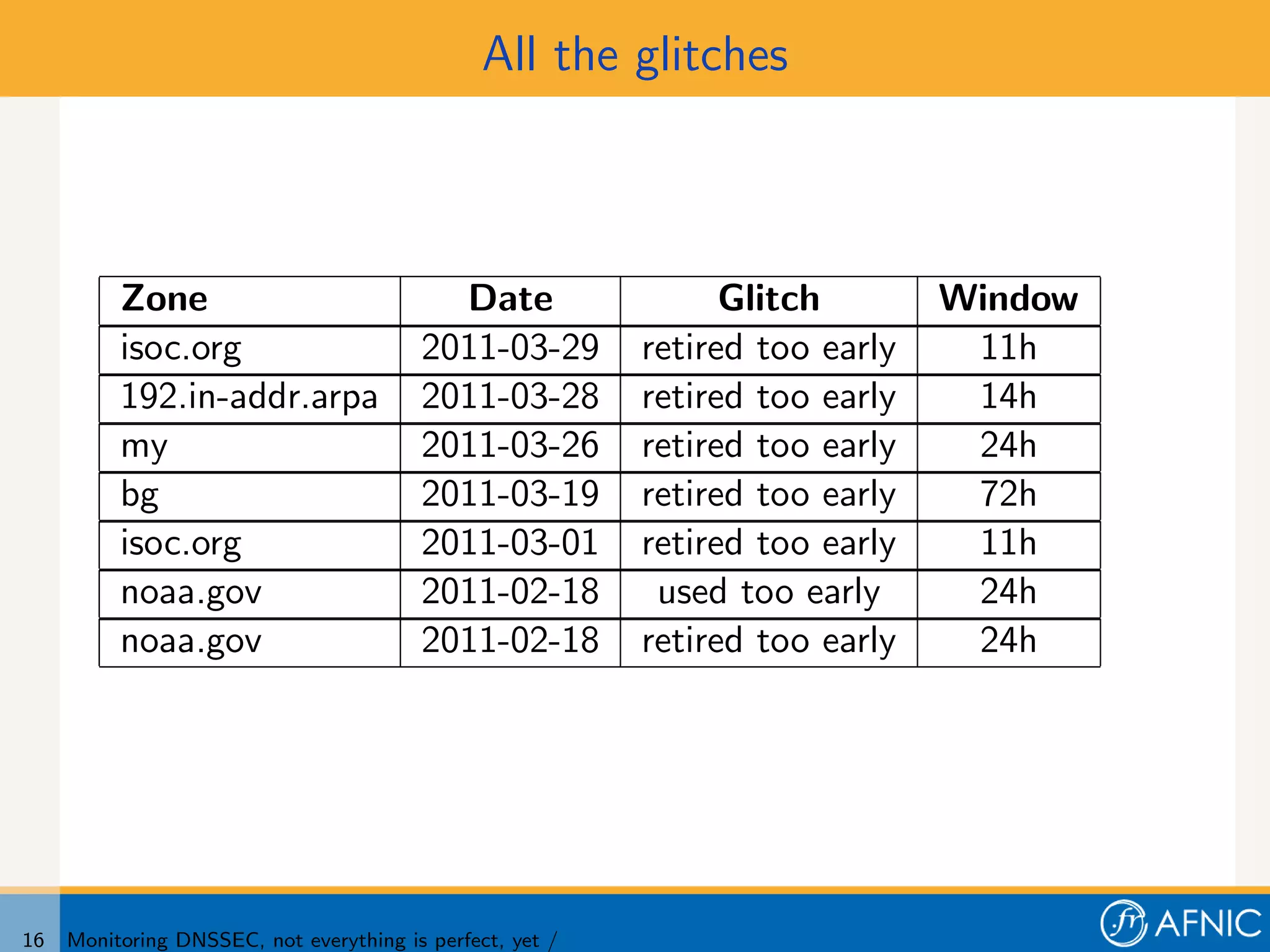
3. Proper monitoring of DNSSEC key rollovers requires taking into account caching times to ensure signatures have expired from caches before keys are removed. The presented tool analyzes timing of signatures, keys, and keysets to detect problems in rollovers.