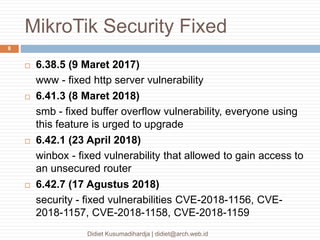
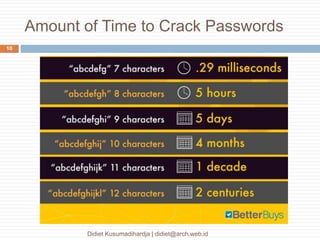
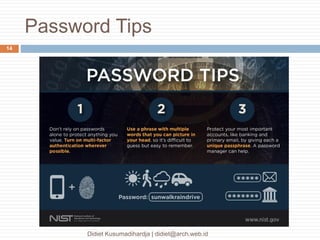
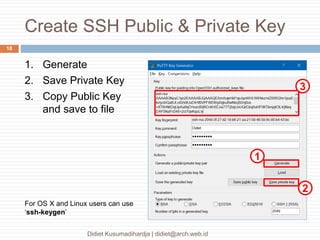
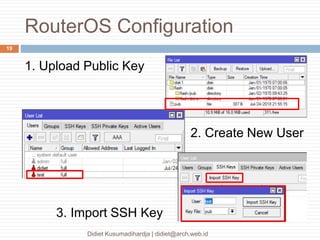
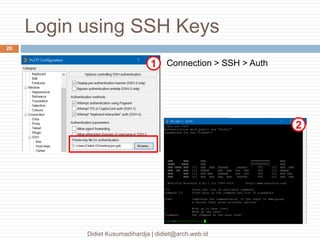
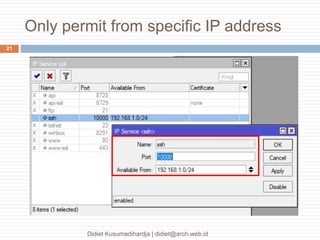
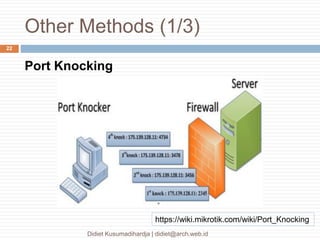
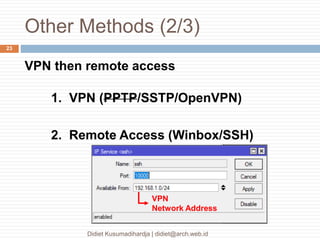
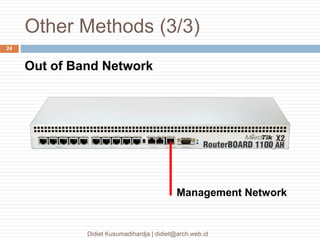
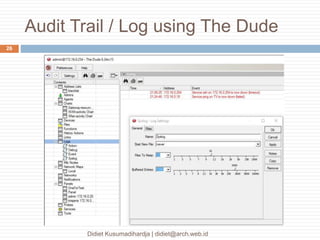
This document discusses the implementation of multi-factor authentication on MikroTik RouterOS, emphasizing security practices for network management. It details the necessary steps for generating and utilizing SSH keys, recommends securing access through specific IP addresses, and highlights additional security measures such as VPN and port knocking. The author, Didiet Kusumadihardja, is a seasoned IT professional with extensive experience in various IT services and emphasizes the importance of layered security strategies.