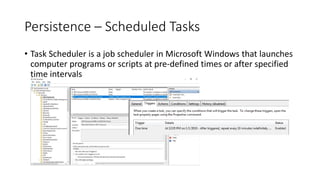
Persistence techniques allow threat actors to maintain access to systems across changes. This includes using services, the registry, scheduled tasks, and startup folders. Services can be configured to run automatically at startup under privileged accounts. The registry stores program settings and entries in the Run subkey launch software automatically. Scheduled tasks launch programs or scripts on a defined schedule. Applications placed in startup folders run every time the system starts up, either for a single or all users.