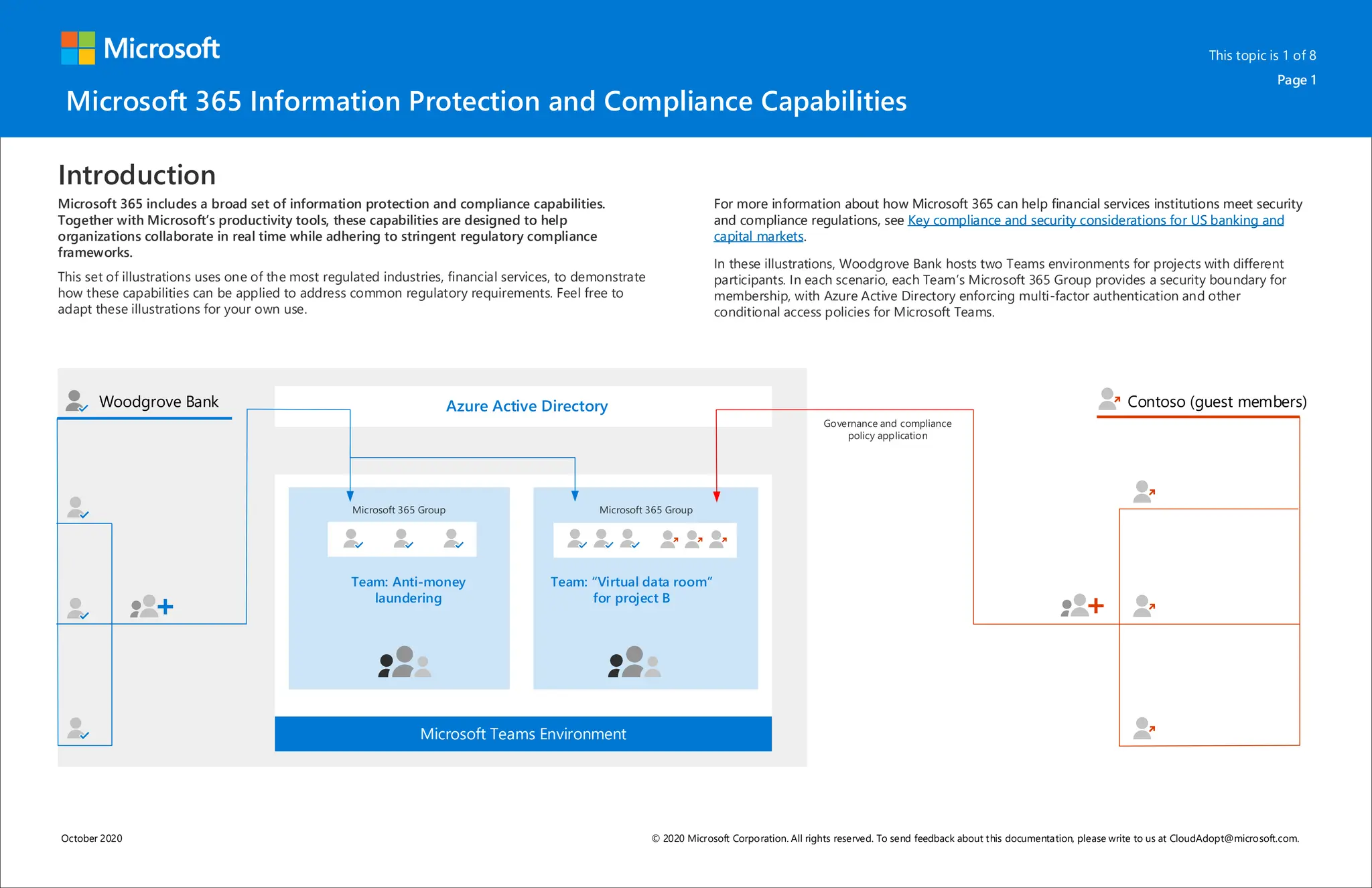
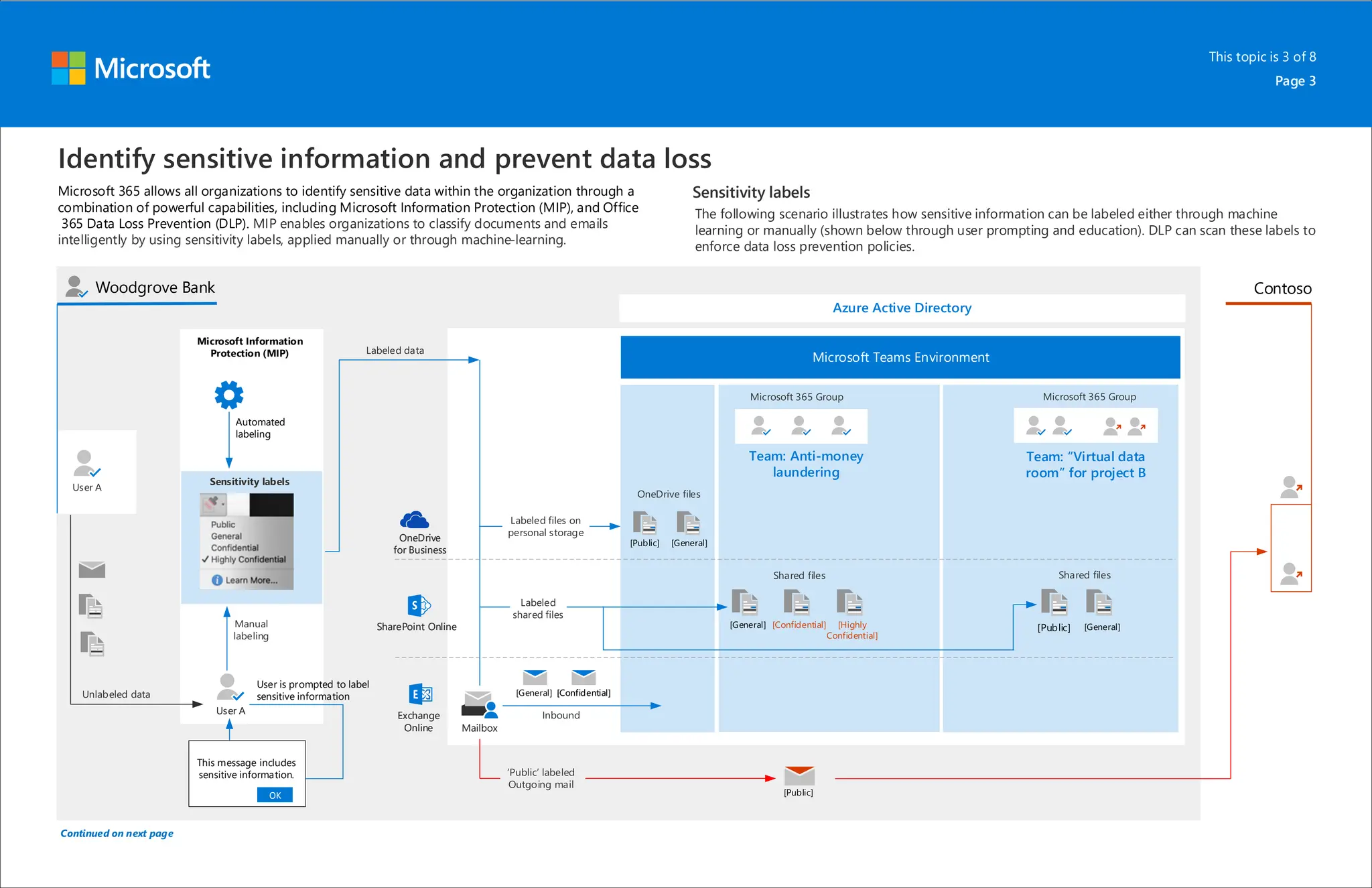
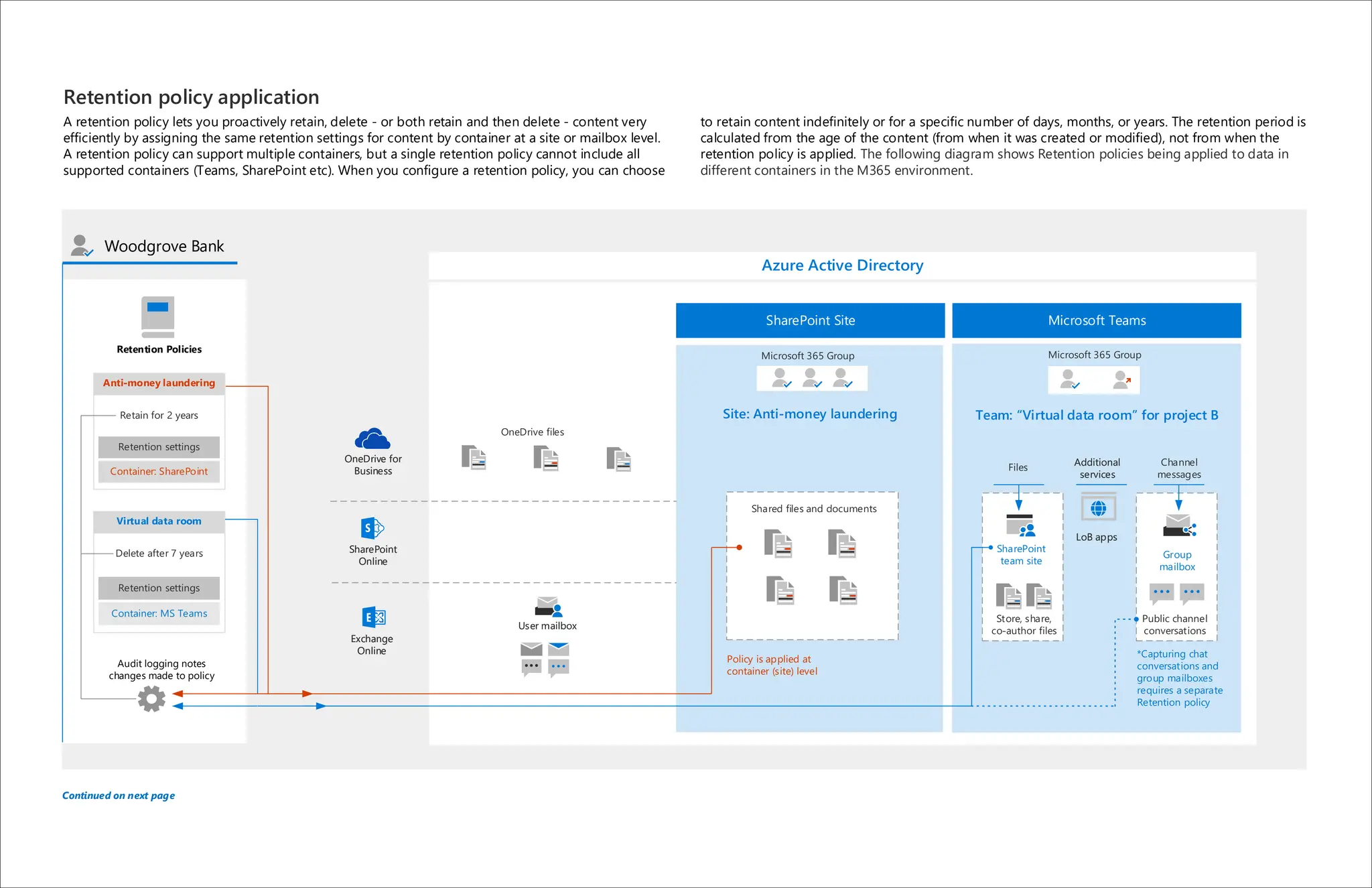
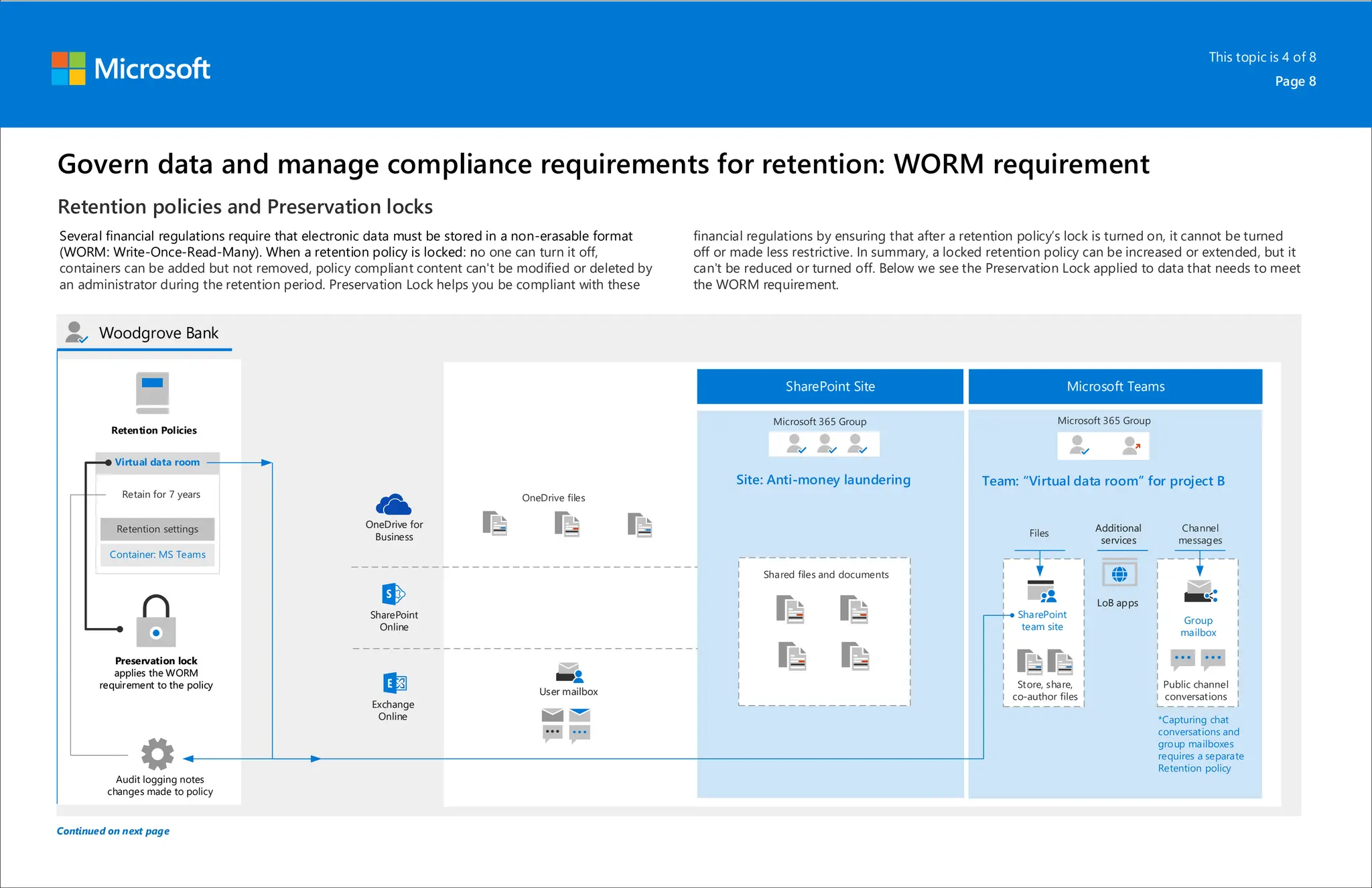
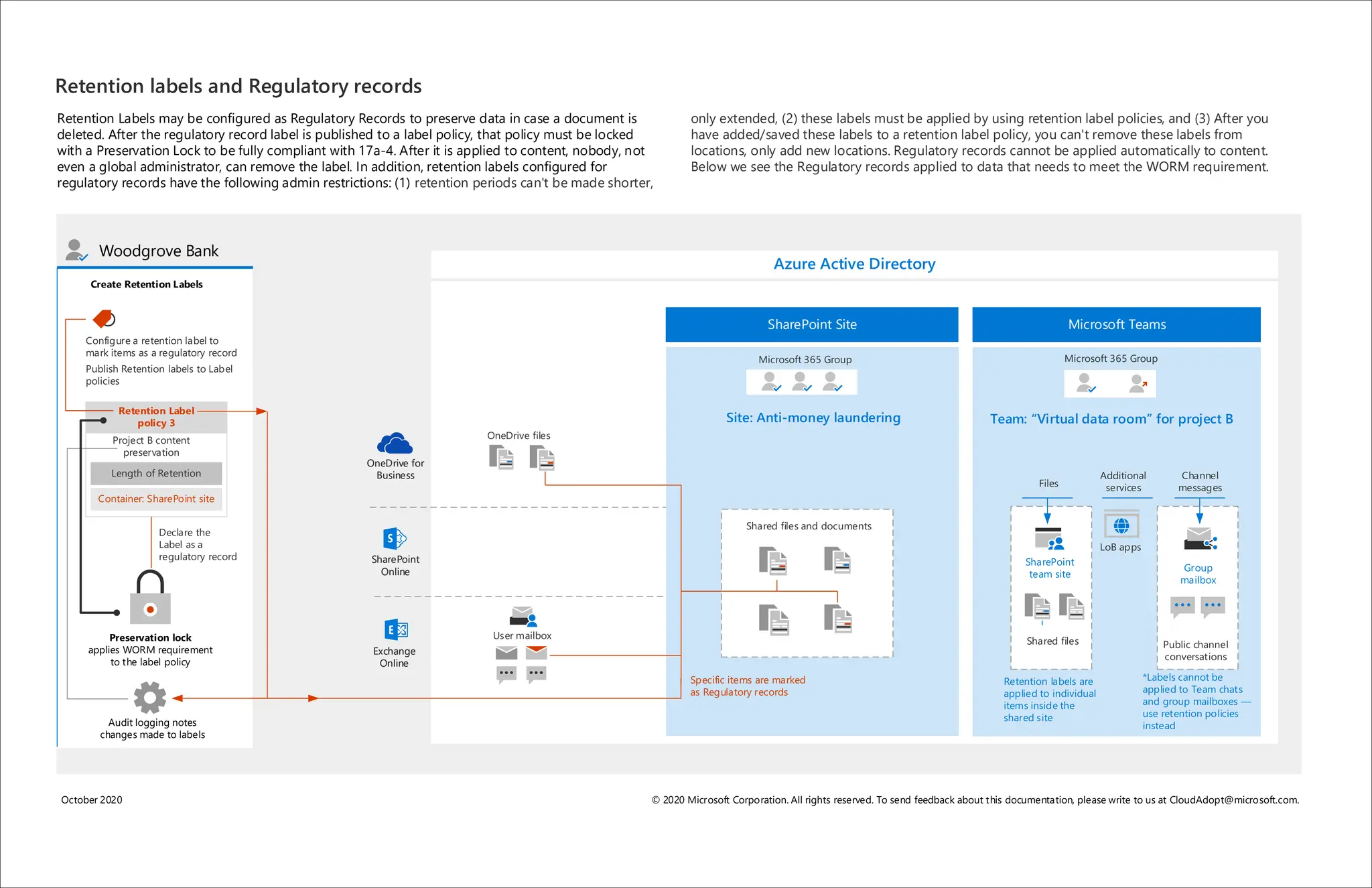
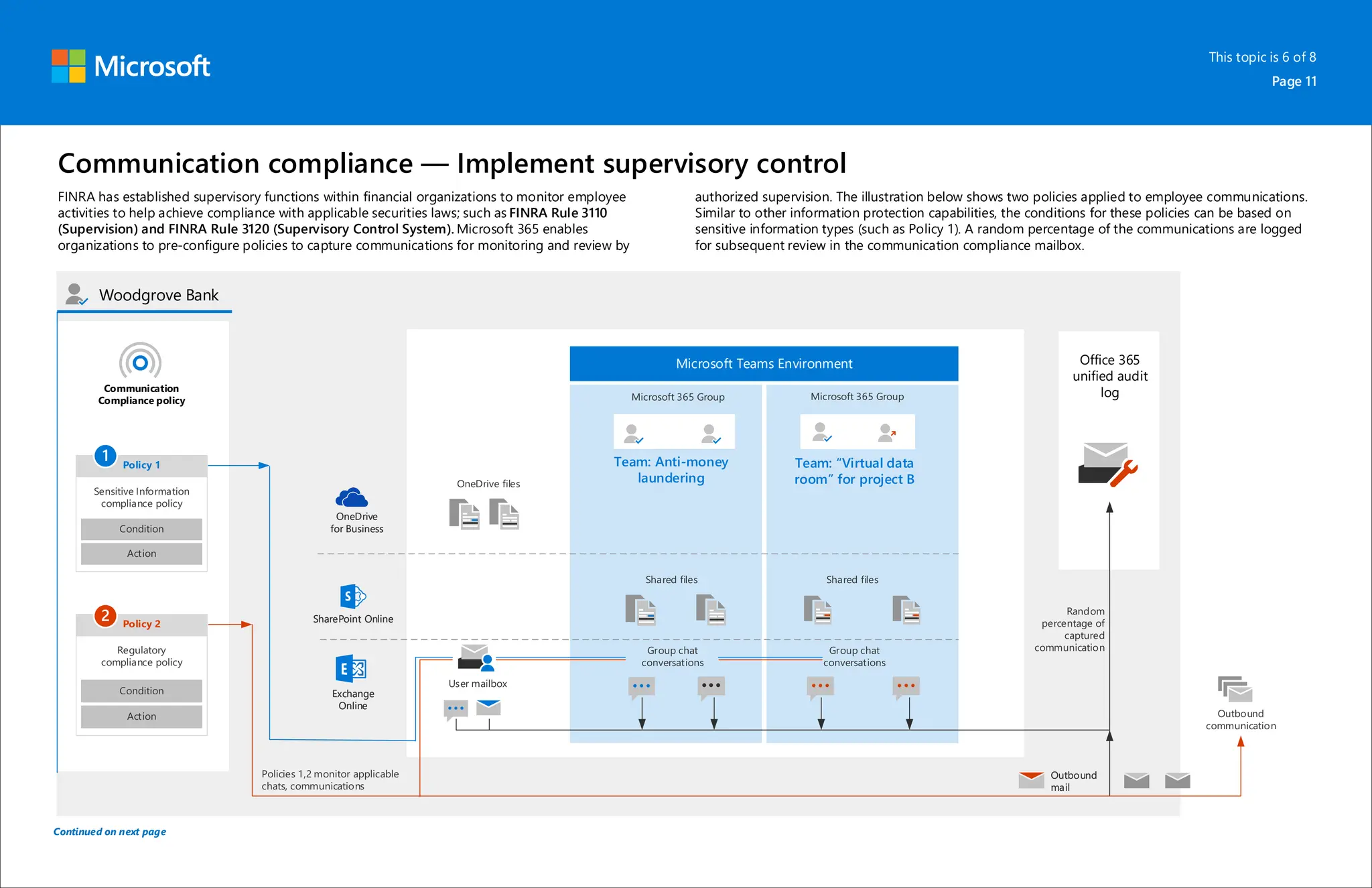
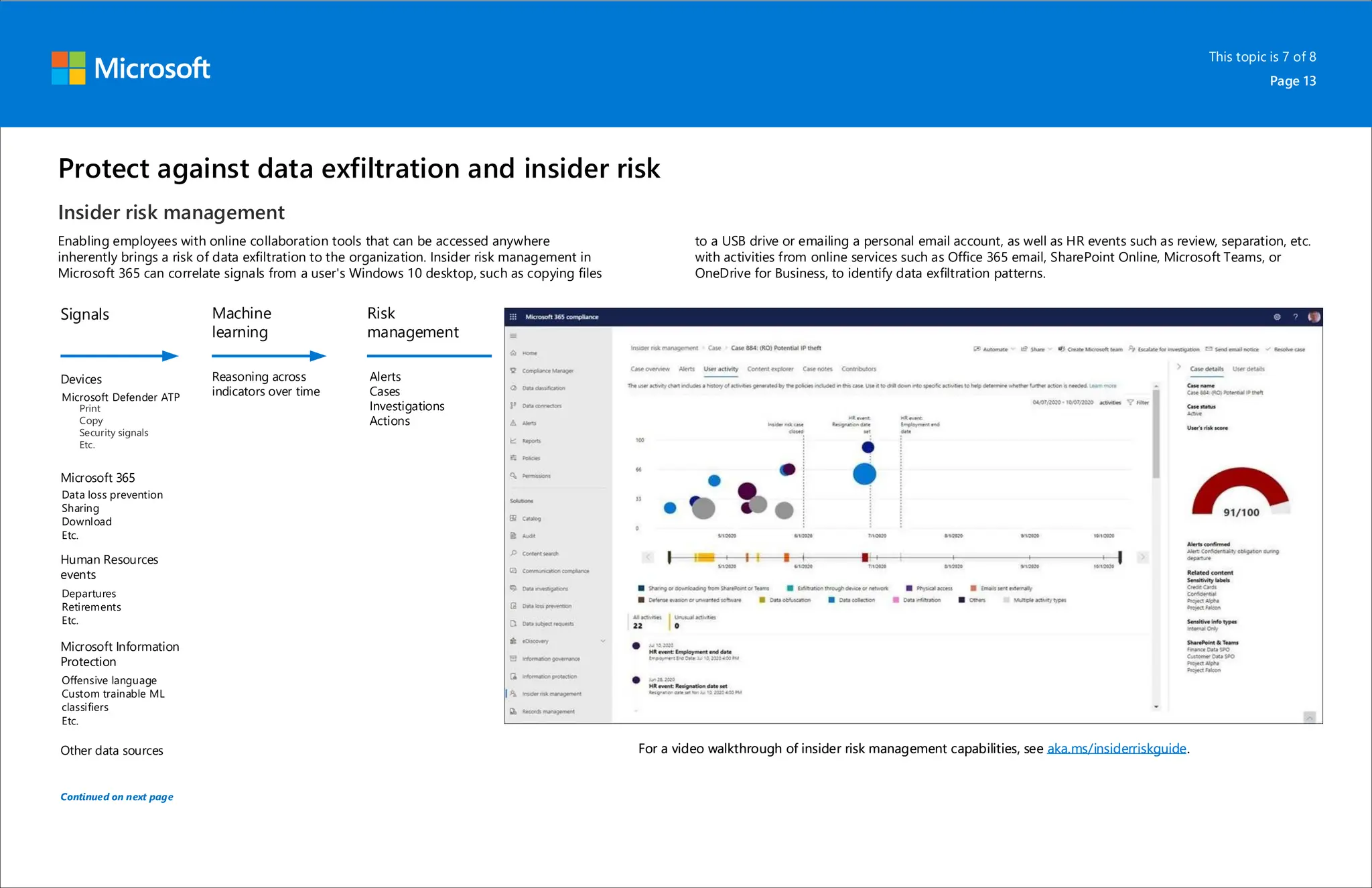
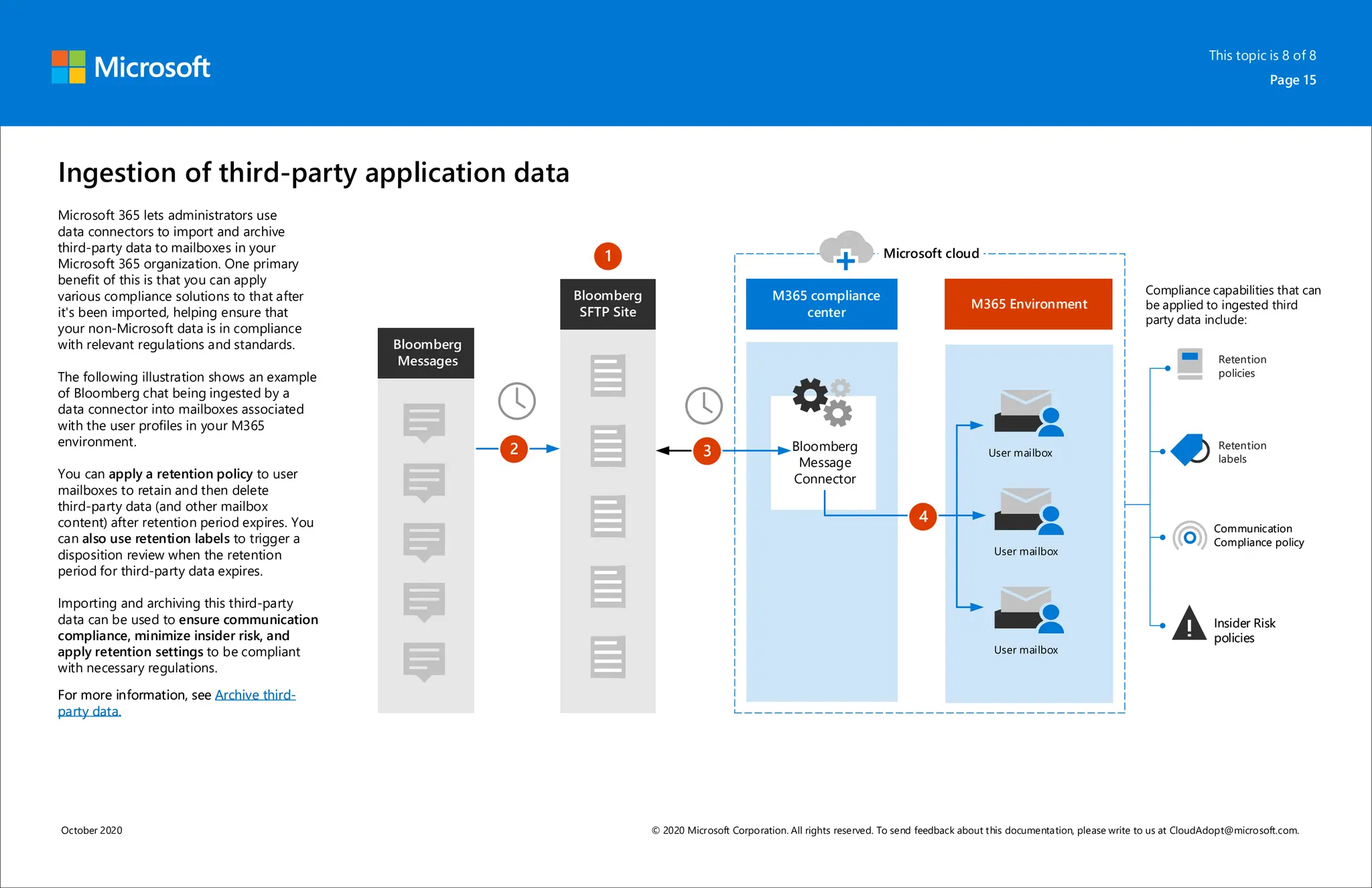
Microsoft 365 includes capabilities for information protection, compliance, and retention policies. These capabilities allow organizations to collaborate while meeting regulatory requirements. For example, a bank can use Teams environments and sensitivity labels to securely share information for internal projects. Data loss prevention policies can then prevent accidental sharing of sensitive labeled data outside the organization. Retention policies and labels help manage regulatory compliance for retaining data by automatically keeping information for specified periods.