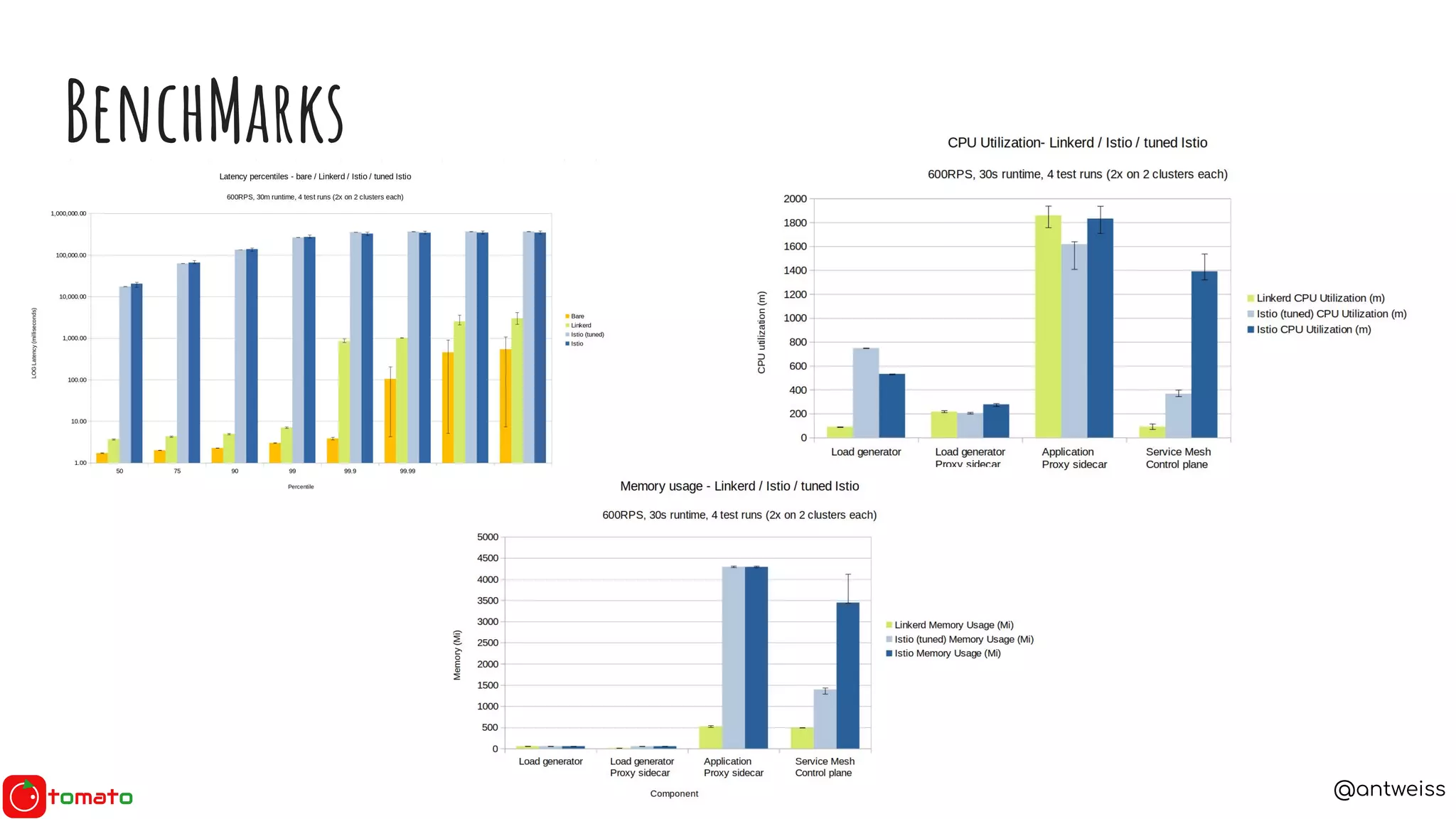
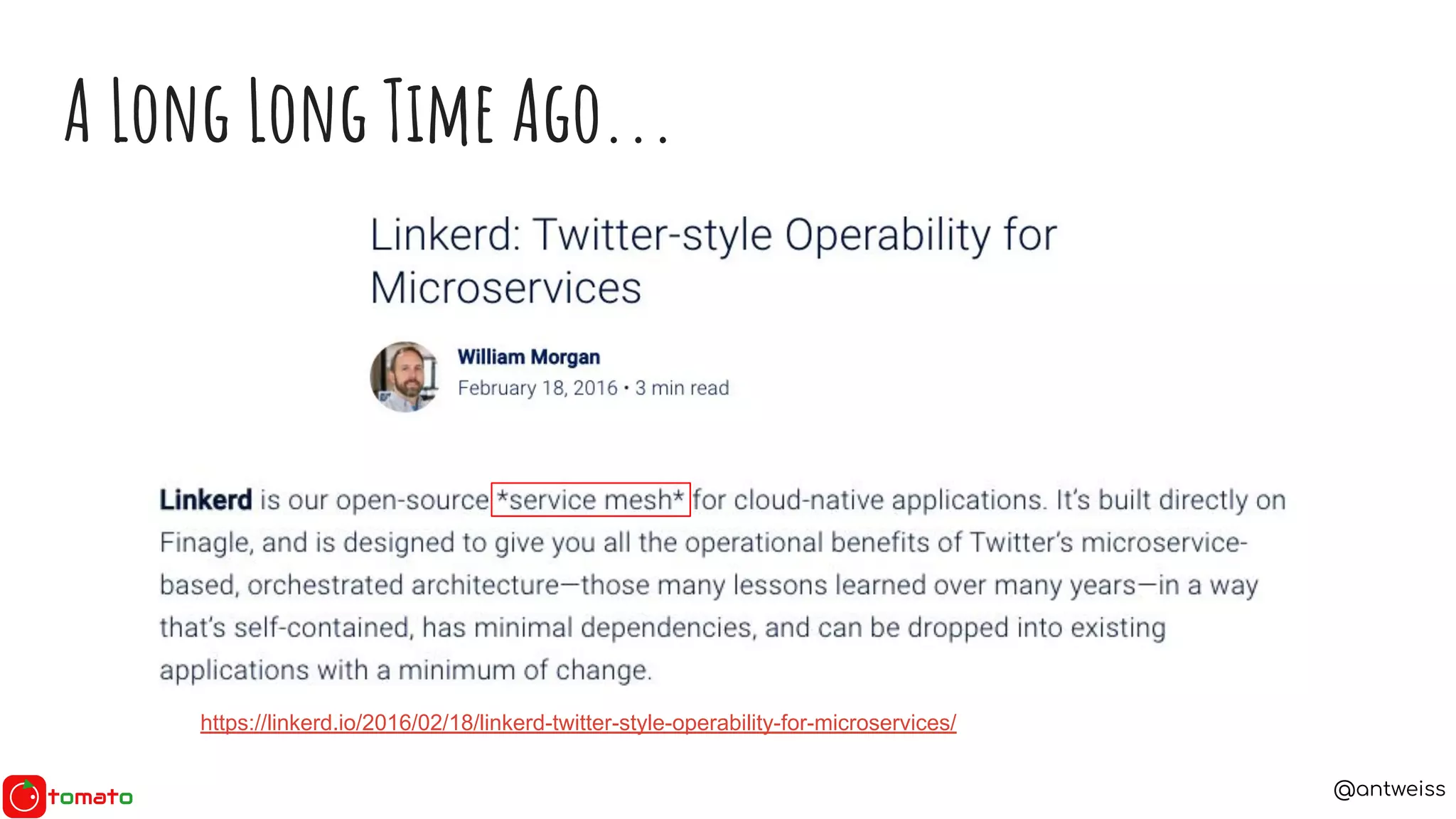
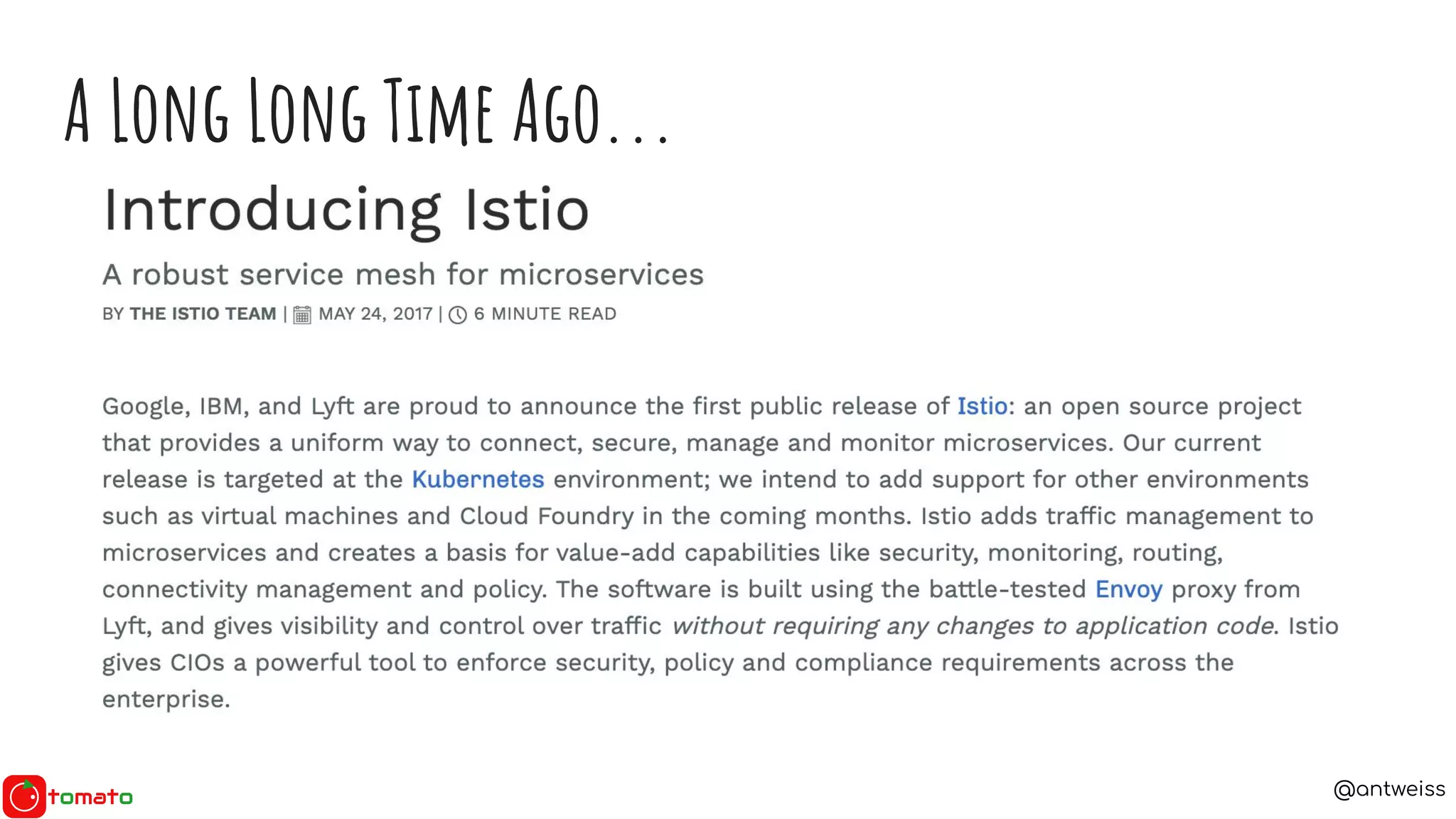
The document discusses the need for service meshes in microservices architecture, highlighting various implementations such as Istio, Linkerd, and Consul Connect. It poses essential questions related to service meshes, including their cost, selection, and functionality. The content also references the Service Mesh Interface (SMI) for standardizing service mesh operations and compares different service meshes based on manageability, observability, and complexity.













![@antweiss
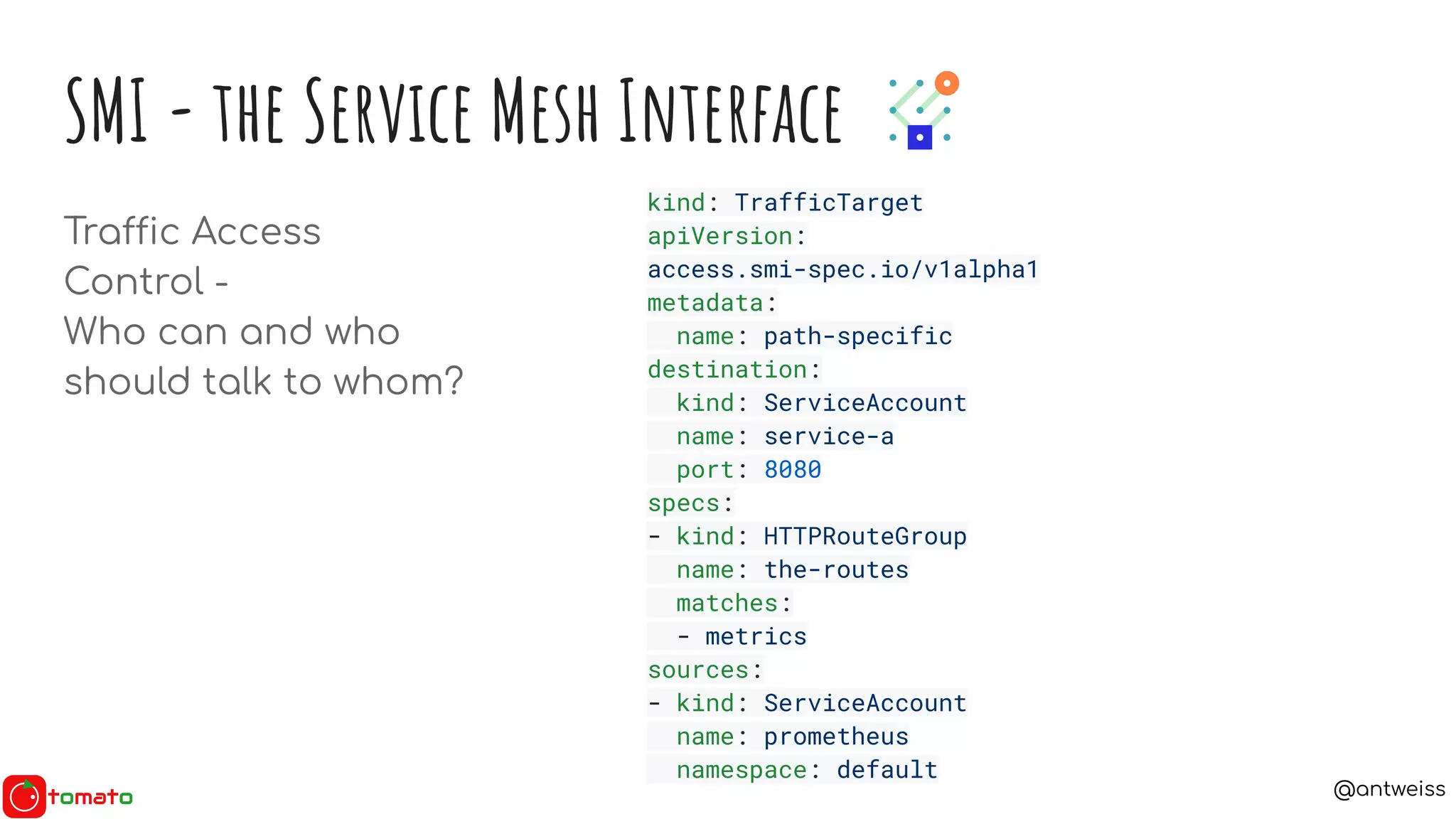
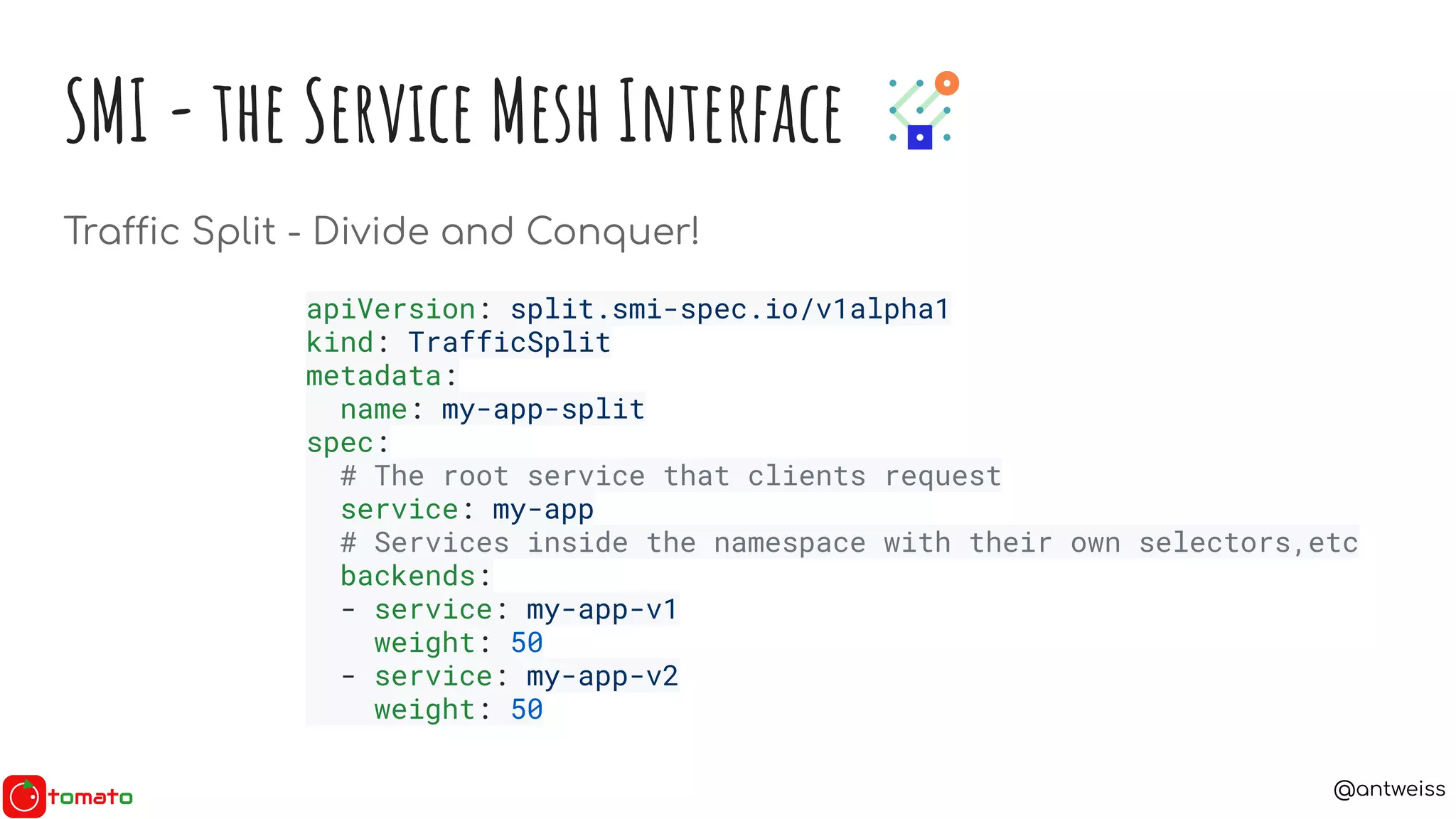
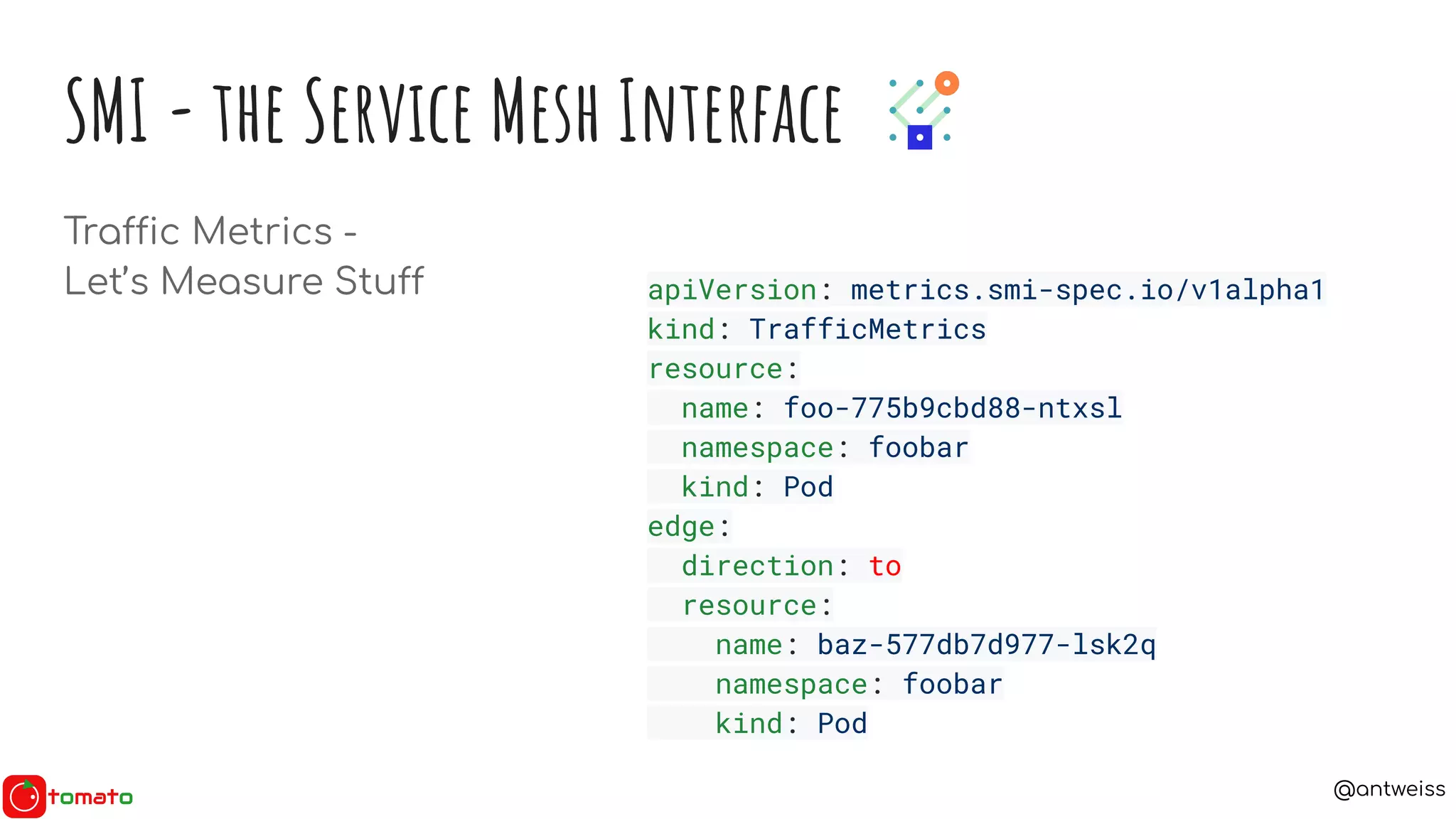
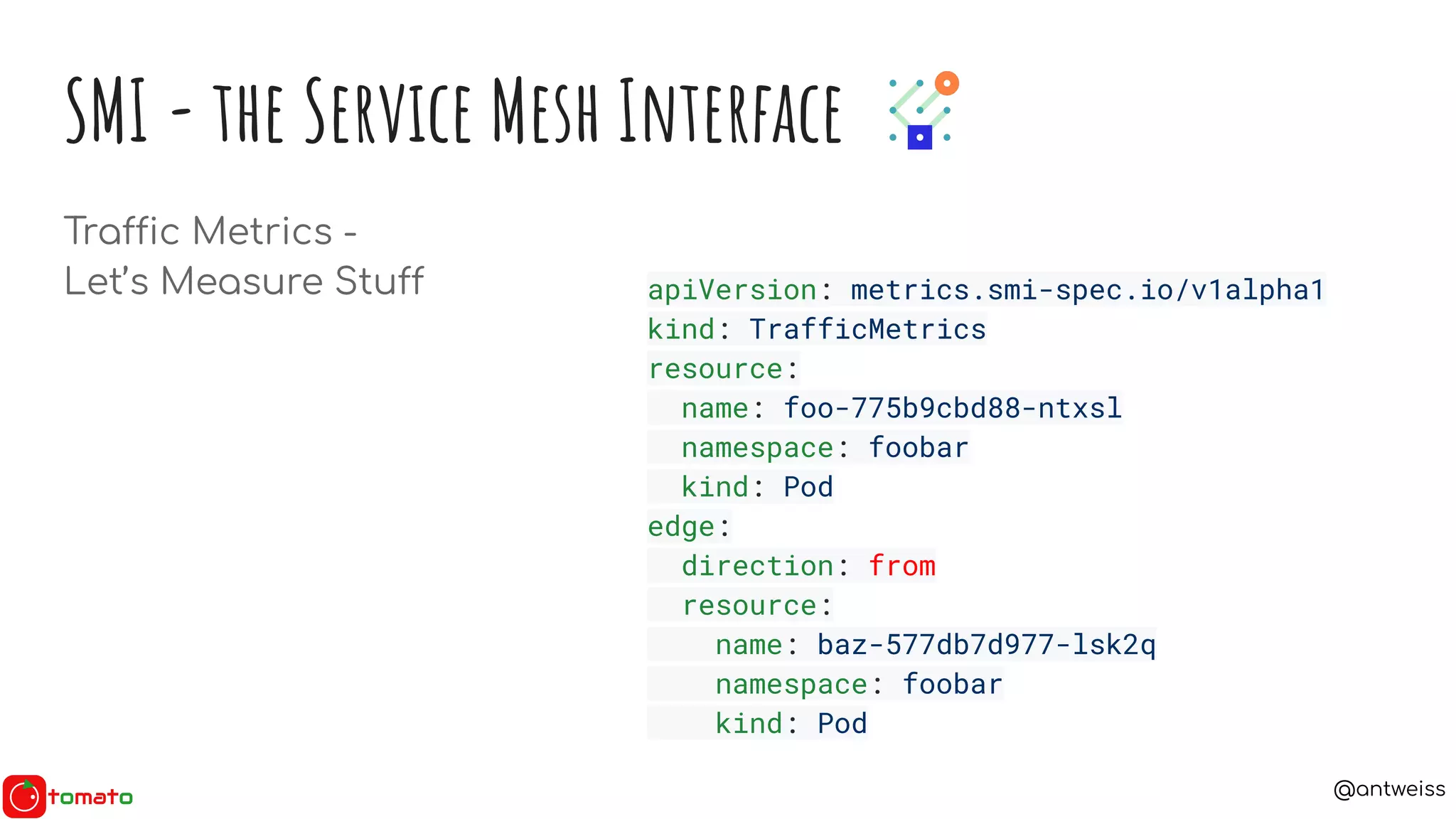
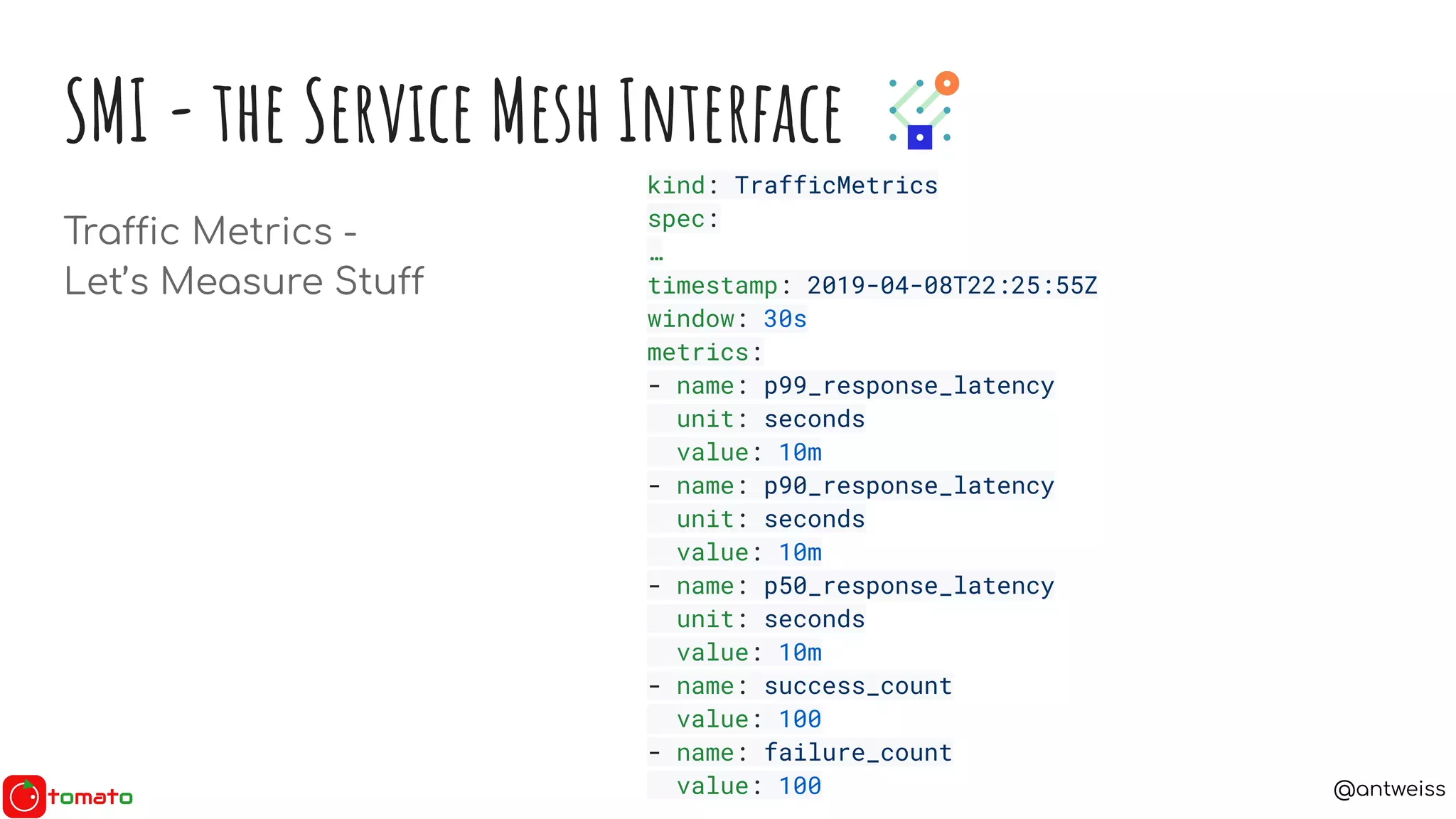
SMI - the Service Mesh Interface
Traffic Spec - what does the traffic look like?
apiVersion: specs.smi-spec.io/v1alpha1
kind: HTTPRouteGroup
metadata:
name: the-routes
matches:
- name: metrics
pathRegex: "/metrics"
methods:
- GET
- name: health
pathRegex: "/healthz"
methods: ["*"]](https://image.slidesharecdn.com/4ghcpzdusnanm9qphw5k-signature-5f1e2423b9c9cc569d61e6d09f728557b53689dd2a8425acf3f88831d6a106b5-poli-191125093820/75/WTF-Do-We-Need-a-Service-Mesh-By-Anton-Weiss-21-2048.jpg)