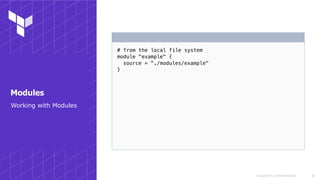
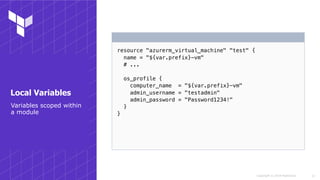
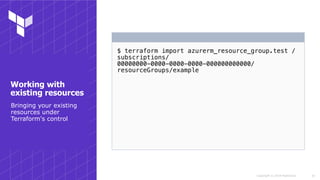
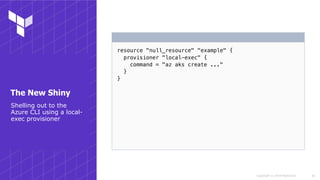
This document discusses various techniques for working with Terraform on Azure, including authenticating to Azure using different methods, working across subscriptions, referencing existing resources, using modules, and common gotchas. It covers authenticating via the Azure CLI, CloudShell, MSI, and service principals. It also discusses using local variables, multiple provider instances to work across subscriptions, data sources to reference existing resources, and importing resources. Techniques for working with preview functionality and resources not natively supported are presented. The document concludes with suggestions for using and testing modules.





![Copyright © 2018 HashiCorp
$ az login
Note, we have launched a browser for you to login. For old
experience with device code, use "az login --use-device-code"
You have logged in. Now let us find all subscriptions you have
access to...
[
{
"cloudName": "AzureCloud",
"id": "00000000-0000-0000-0000-000000000000",
"isDefault": true,
# ...
}
]
!6
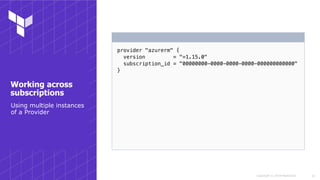
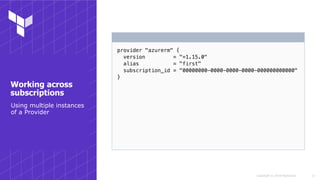
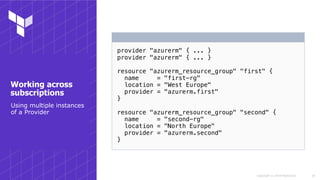
Using the Az CLI
Authenticating using
your Azure CLI
credentials](https://image.slidesharecdn.com/sydneyhug-workingwithterraformonazure-180919044711/85/Working-with-Terraform-on-Azure-6-320.jpg)



















![Copyright © 2018 HashiCorp
resource "azurerm_public_ip" "test" {
# ...
}
resource "azurerm_virtual_machine" "test" {
# ...
}
data "azurerm_public_ip" "test" {
# ...
depends_on = ["azurerm_virtual_machine.test"]
}
output "dynamic_public_ip_address" {
value = "${data.azurerm_public_ip.test.ip_address}"
}
!35
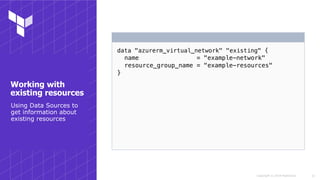
Common Got-ya's
Dynamic IP Addresses](https://image.slidesharecdn.com/sydneyhug-workingwithterraformonazure-180919044711/85/Working-with-Terraform-on-Azure-35-320.jpg)