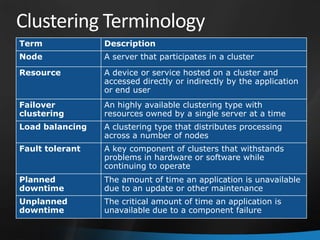
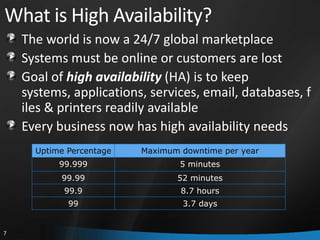
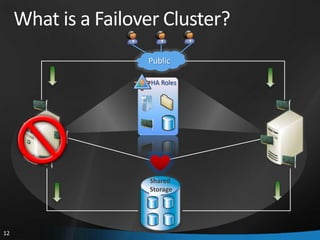
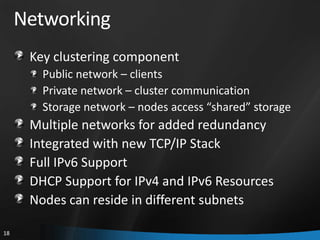
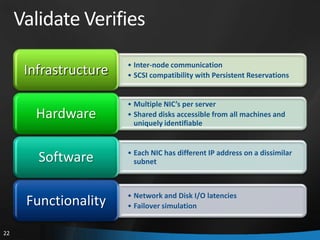
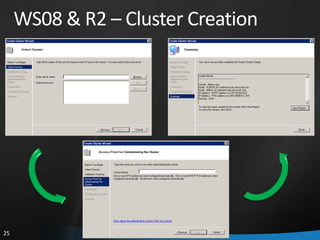
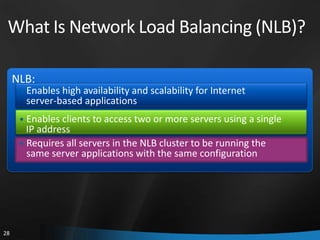
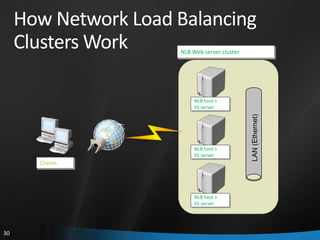
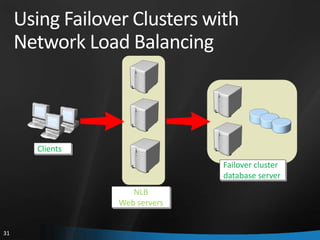
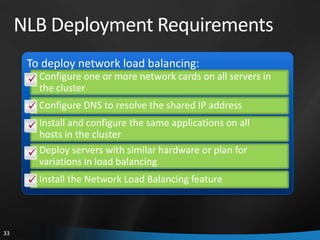
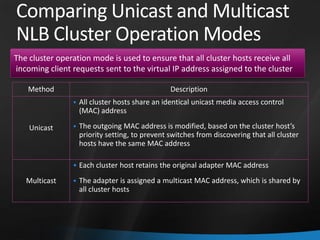
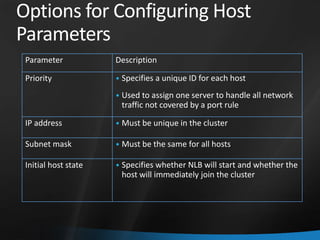
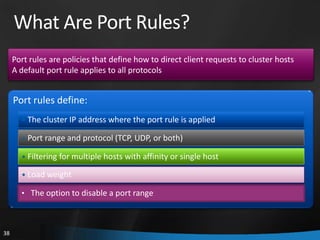
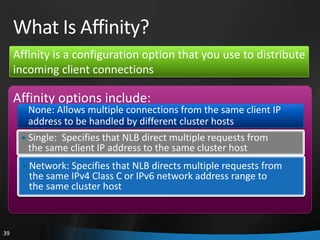
This document provides an overview of Windows Server 2008 R2 Failover Clustering and Network Load Balancing. It discusses what a cluster is, why they are used, and cluster terminology. It also covers the software and hardware requirements for failover clustering, and the process of validating and creating a cluster. For network load balancing, it describes how load balancing works, deployment requirements, and options for configuring host parameters and port rules.