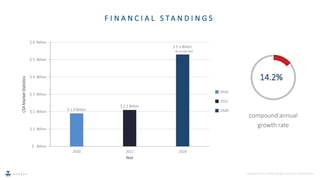
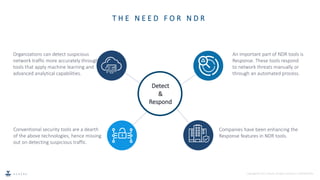
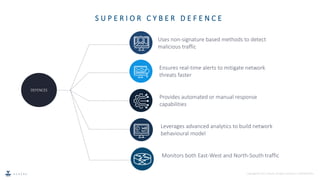
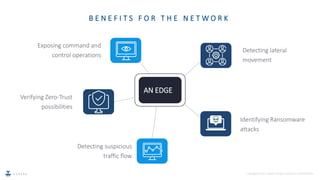
Network Detection and Response (NDR) is an emerging cybersecurity technique that uses machine learning and analytics to detect malicious network traffic in real-time, without relying on signatures. NDR tools monitor both internal and external network traffic to identify threats and respond either manually or automatically. As conventional tools lack these capabilities, NDR provides improved visibility and faster response times to mitigate network security risks.