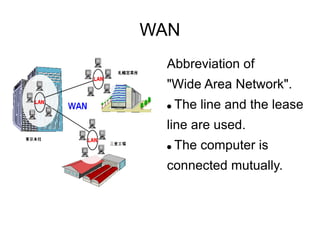
Encryption converts data during transmission to prevent unauthorized access. Virtual private networks (VPNs) allow secure connections between remote locations at a lower cost than dedicated lines. Wide area networks (WANs) connect computers over leased lines. Firewalls monitor network boundaries and block unauthorized external access to protect internal computer systems and data.