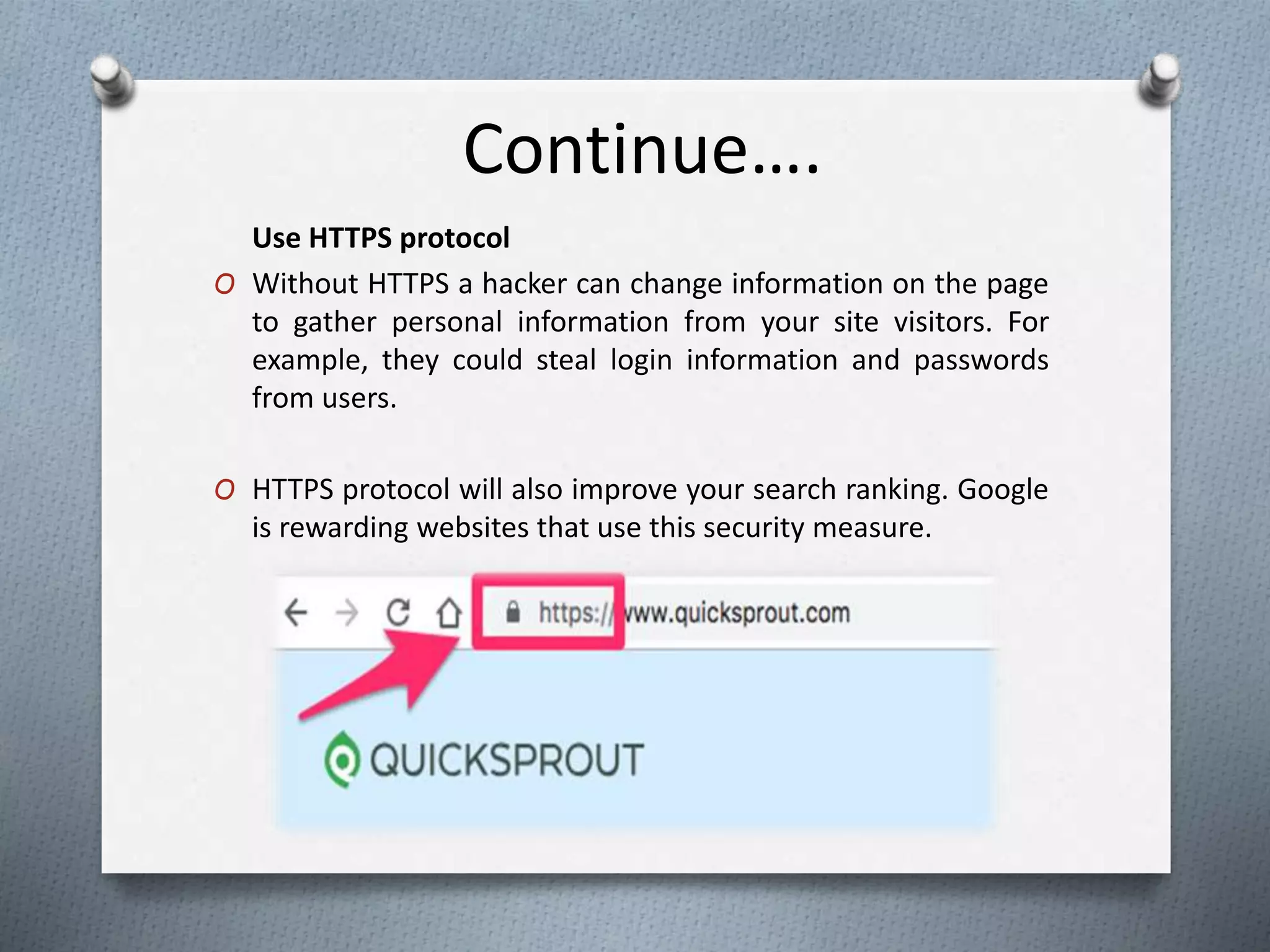
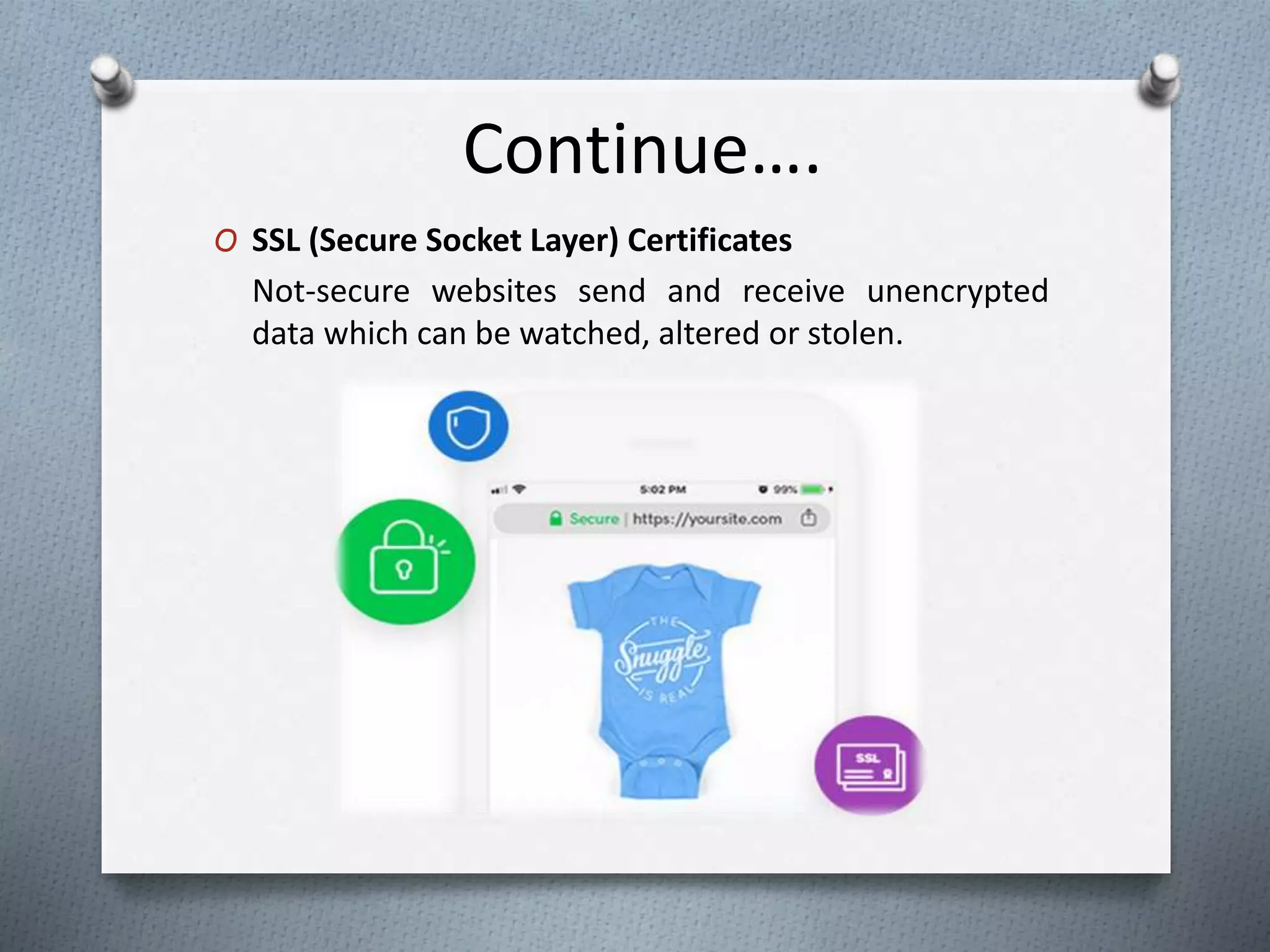
The document discusses the importance of web security, highlighting that over 50,000 websites are hacked daily and 43% of cybercrimes target small businesses. It outlines common security threats, available technologies for safeguarding websites, and best practices for improving website security, such as updating software and using HTTPS protocols. Additionally, it emphasizes the implications of inadequate security on SEO rankings and the significance of SSL certificates.