This document discusses techniques for enumerating information from a target website or application, including:
1. Using search engines like Google to find publicly available information and hidden features.
2. Bruteforcing files, directories, and parameters to locate hidden areas. Tools like DirBuster can automate this process.
3. Analyzing error messages and response codes to infer application details and find vulnerabilities.
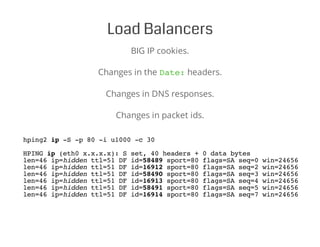
4. Fingerprinting server configuration details like virtual hosts, load balancers, alternative ports and access points.
5. The document provides examples of commands and techniques to practice these enumeration methods.


![Error Message Analysis
Requesting non-existent resources.
Supplying weird values to input fields.
Sending completely broken HTTP requests.
Use known tricks such as ?var[]=123for PHP apps.](https://image.slidesharecdn.com/webapplicationsecurity101-05enumeration-140724051828-phpapp01/85/Web-Application-Security-101-05-Enumeration-6-320.jpg)