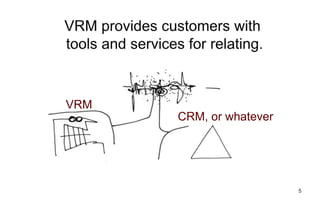
The document outlines how the Respect Network enhances Vendor Relationship Management (VRM) through personal cloud technologies and a trust network, promoting consumer control over personal data. Key examples include safe single-sign-on solutions, automatic change-of-address updates, intentcasting for targeted marketing, and improved customer service methods. It concludes with recommendations for businesses to adopt these technologies to empower customers and improve operational efficiency.