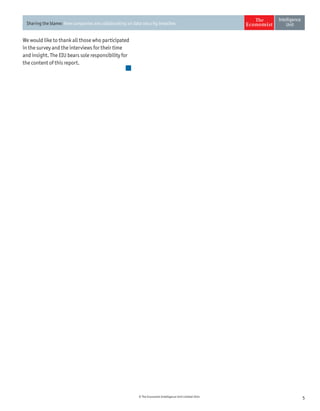
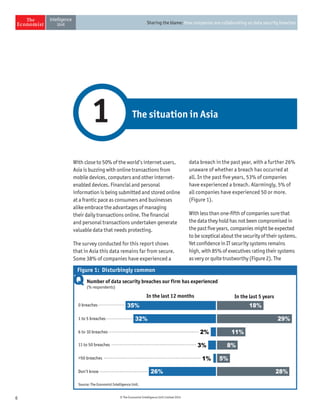
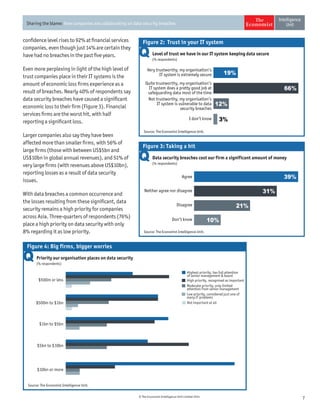
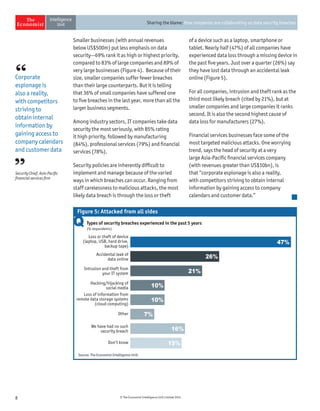
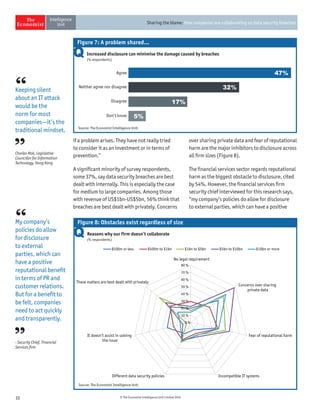
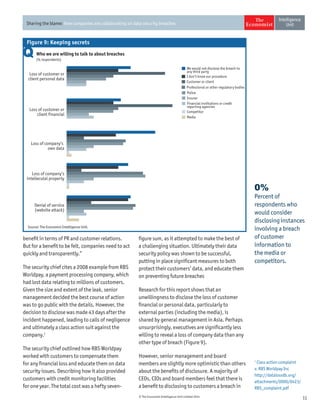
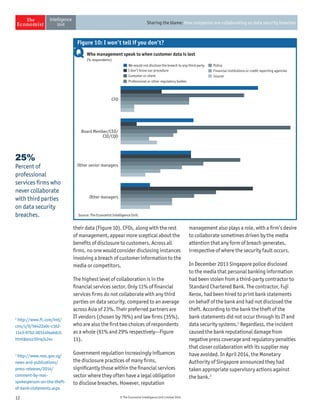
The document discusses the challenges companies face regarding data security breaches, highlighting that only 35% of firms are confident they haven't experienced a breach in the past year. It stresses the importance of collaboration among companies, governments, and third parties to manage and disclose data breaches, as nearly 40% of firms report significant economic losses due to these issues. Despite ongoing vulnerabilities, there is a noticeable high level of trust in IT systems, with 85% of executives believing their systems are secure, which contrasts sharply with the substantial financial impacts observed from breaches.