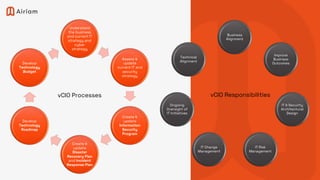
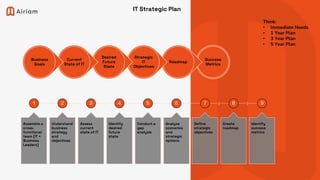
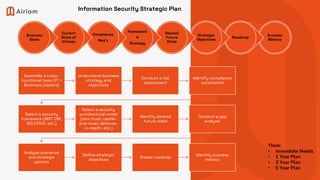
The document outlines a comprehensive IT and security strategy framework led by Art Ocain, detailing the processes for assessing and updating information security programs and disaster recovery plans. It emphasizes the importance of cross-functional collaboration, alignment with business objectives, and the establishment of strategic goals over immediate, 1-year, 3-year, and 5-year timelines. Key components include risk management, compliance with security frameworks, and the implementation of various cybersecurity controls and policies.