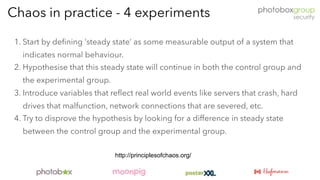
Dinis Cruz, a CISO, discusses chaos engineering as a method for enhancing security in distributed systems by conducting controlled experiments to ensure system resilience during disruptions. Key principles include defining steady state metrics, performing hypothesis-driven testing, and automating continuous experiments to manage risks effectively. Cruz emphasizes the importance of visibility in security practices and frames chaos engineering as integral to modern change management.