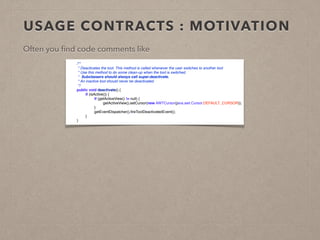
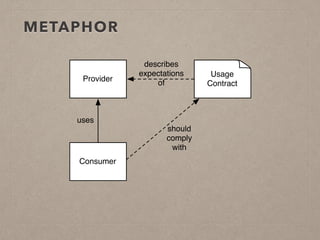
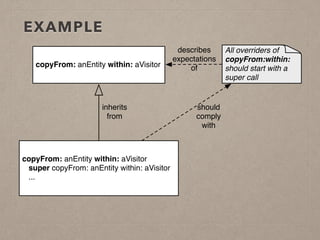
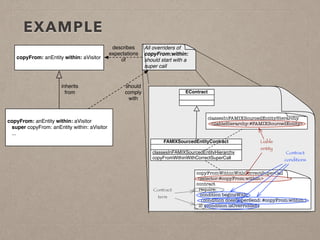
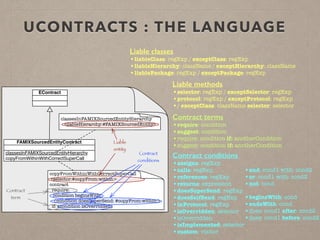
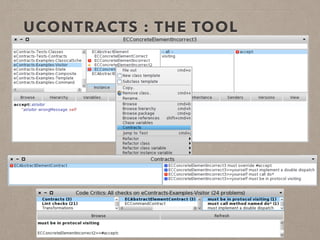
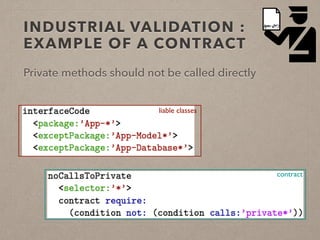
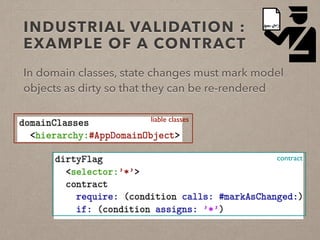
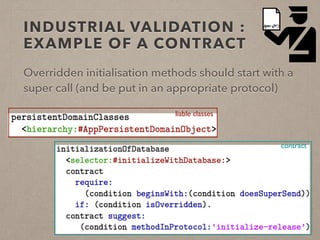
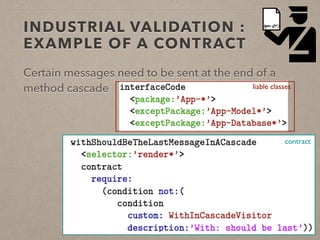
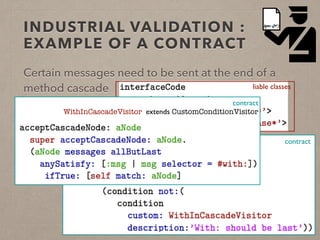
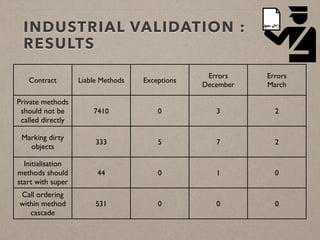
The document discusses usage contracts in software development, which aim to encode and enforce structural regularities within source code. It presents findings from a case study involving an interactive web application developed in Pharo Smalltalk, where various contract violations were identified during validations. The authors advocate for the integration of a proactive tool that offers immediate feedback to developers, enhancing their ability to maintain code quality and consistency.