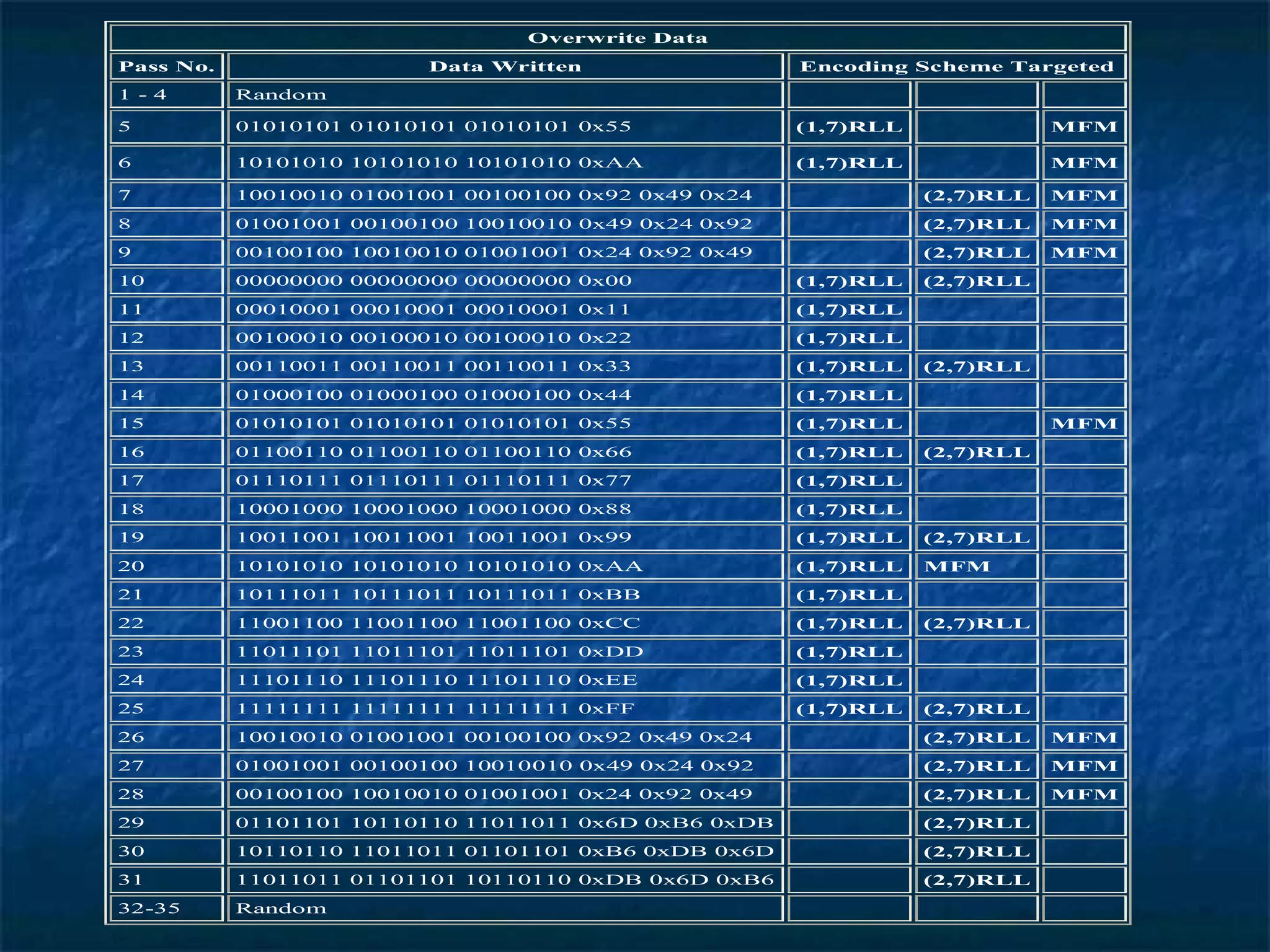
The document provides an overview of data recovery, detailing methods for retrieving deleted or inaccessible data from electronic storage and the various causes of data loss. It discusses techniques and software for recovery, as well as the importance of secure deletion methods to prevent unauthorized data recovery. Additionally, it reviews the uses of data recovery in both everyday scenarios and law enforcement applications, along with recommendations for securely deleting data.