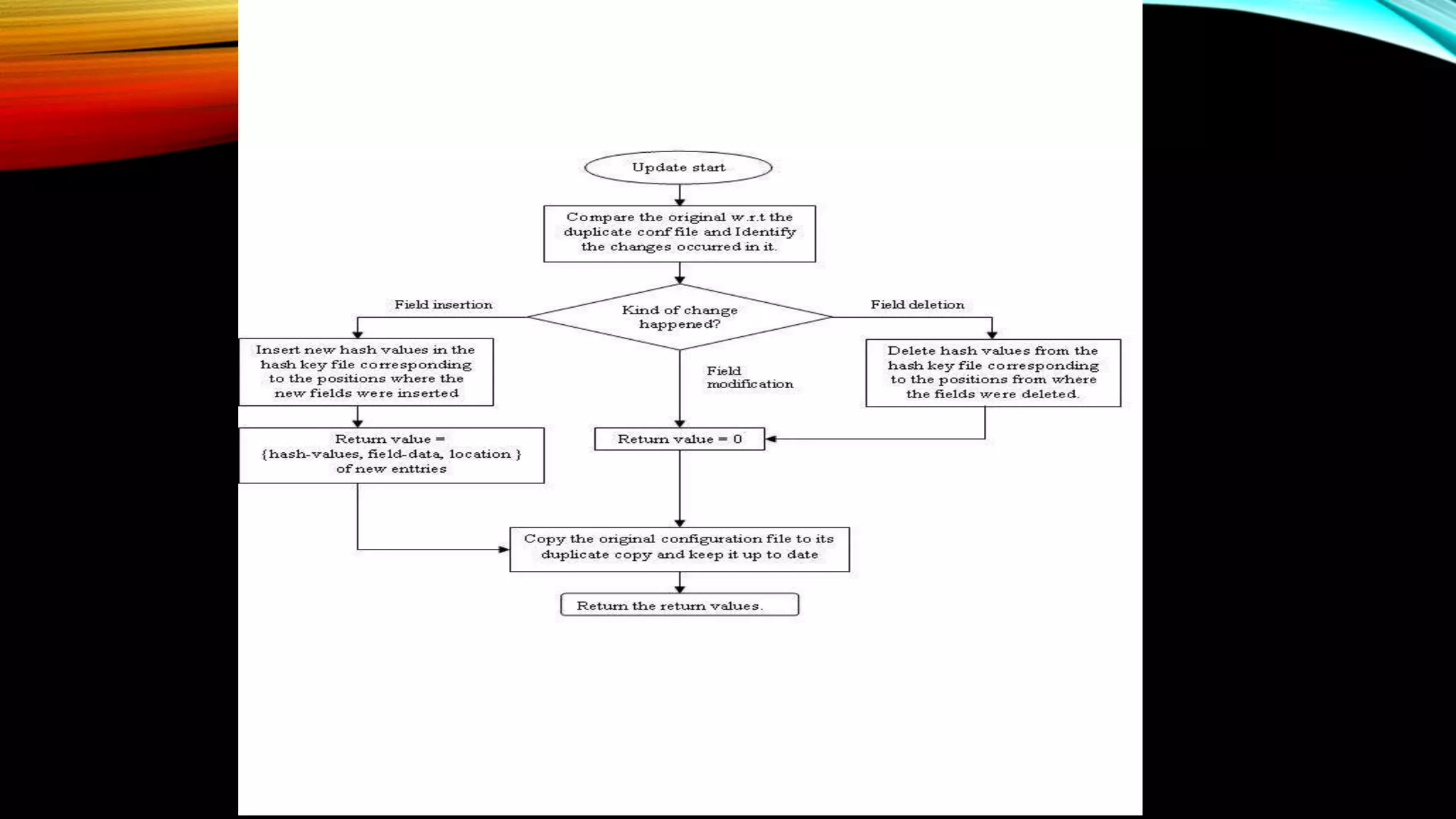
This document discusses hash tables and hashing algorithms. It describes how hash tables use a hashing function to map keys to indexes in an array, which allows for fast search, insertion and retrieval of data. There are several techniques discussed for handling collisions when two keys hash to the same index, including separate chaining, linear probing and double hashing. The basic operations of a hash table are searching, inserting and deleting elements.