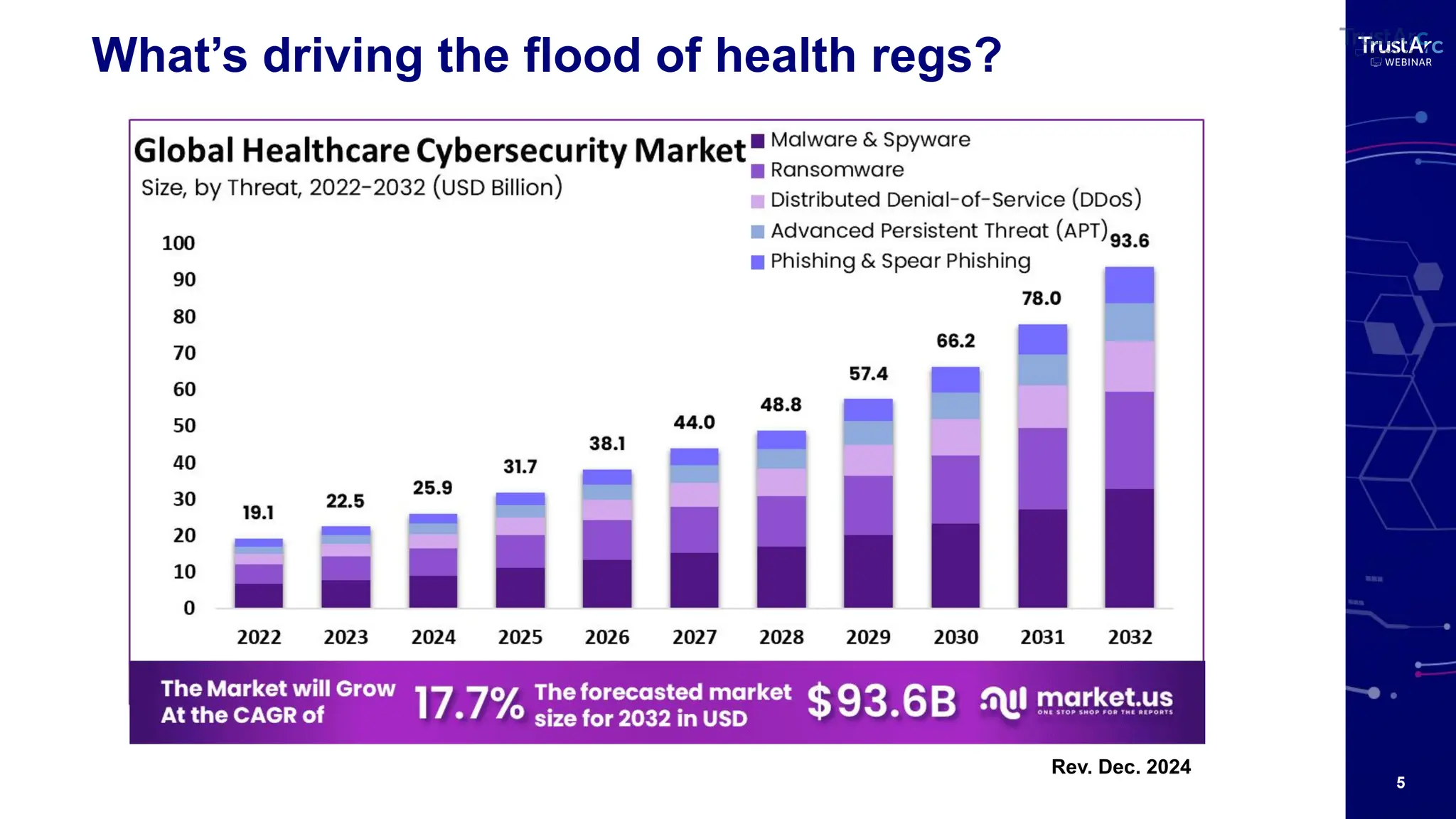
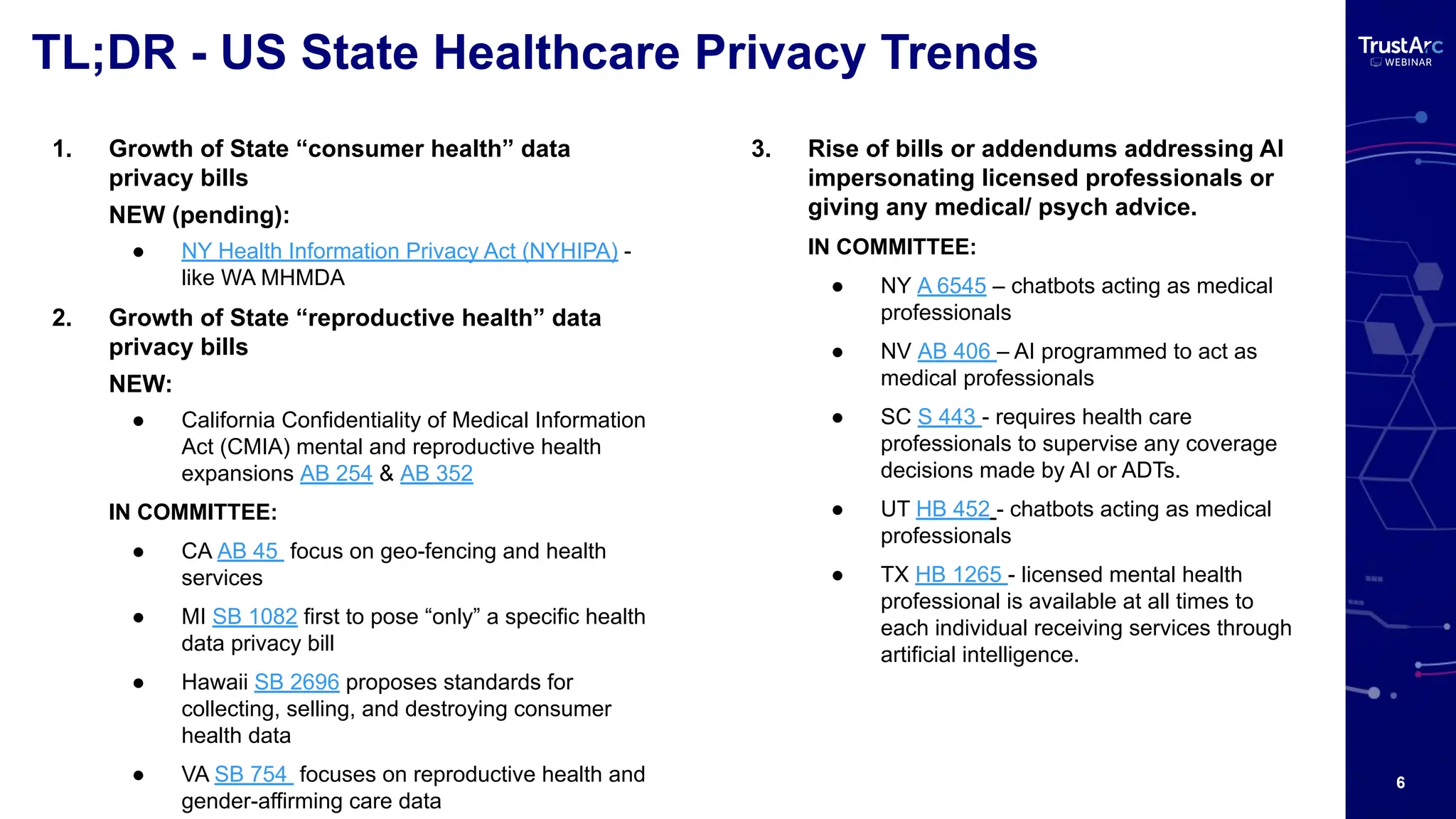
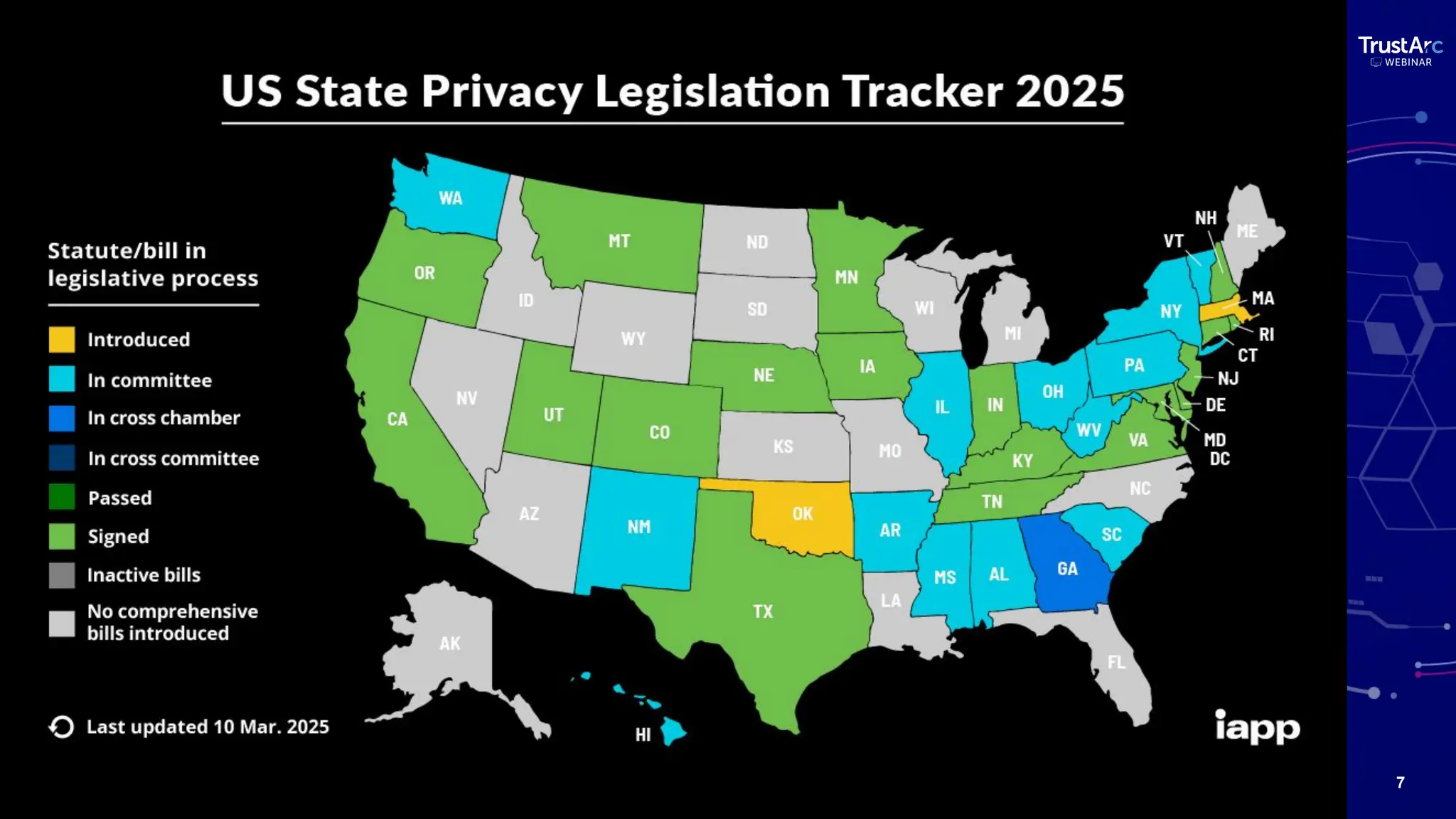
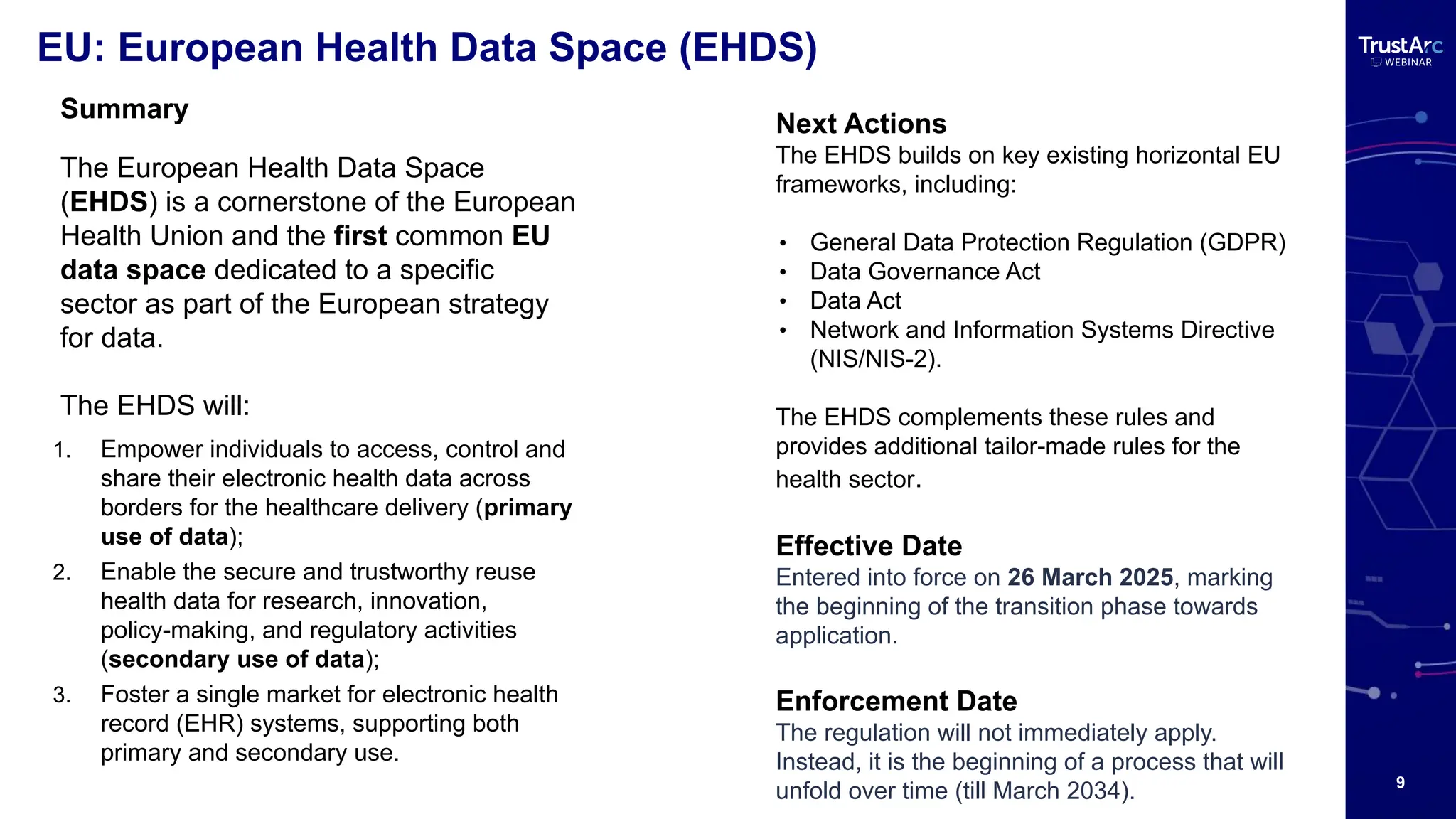
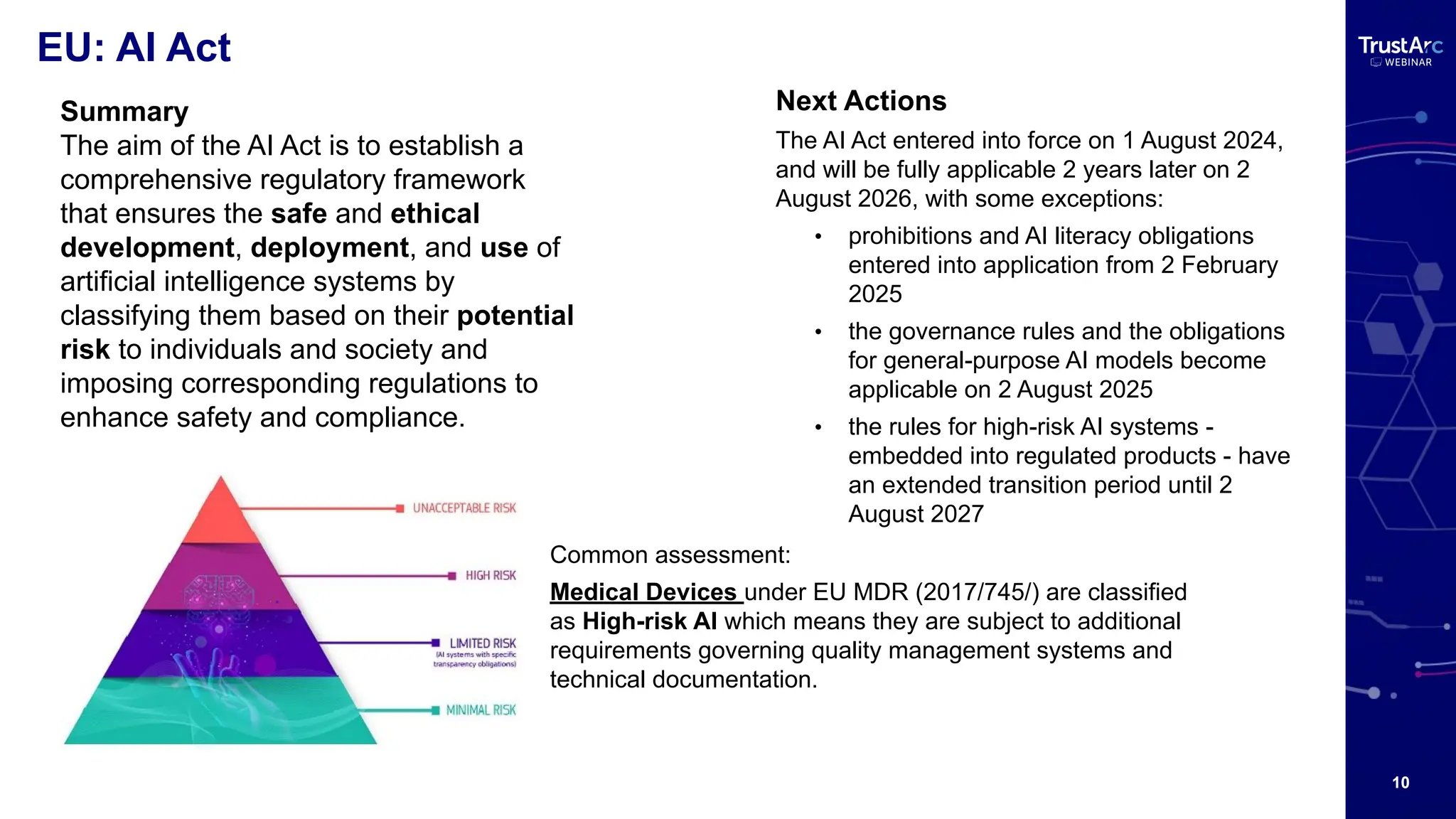
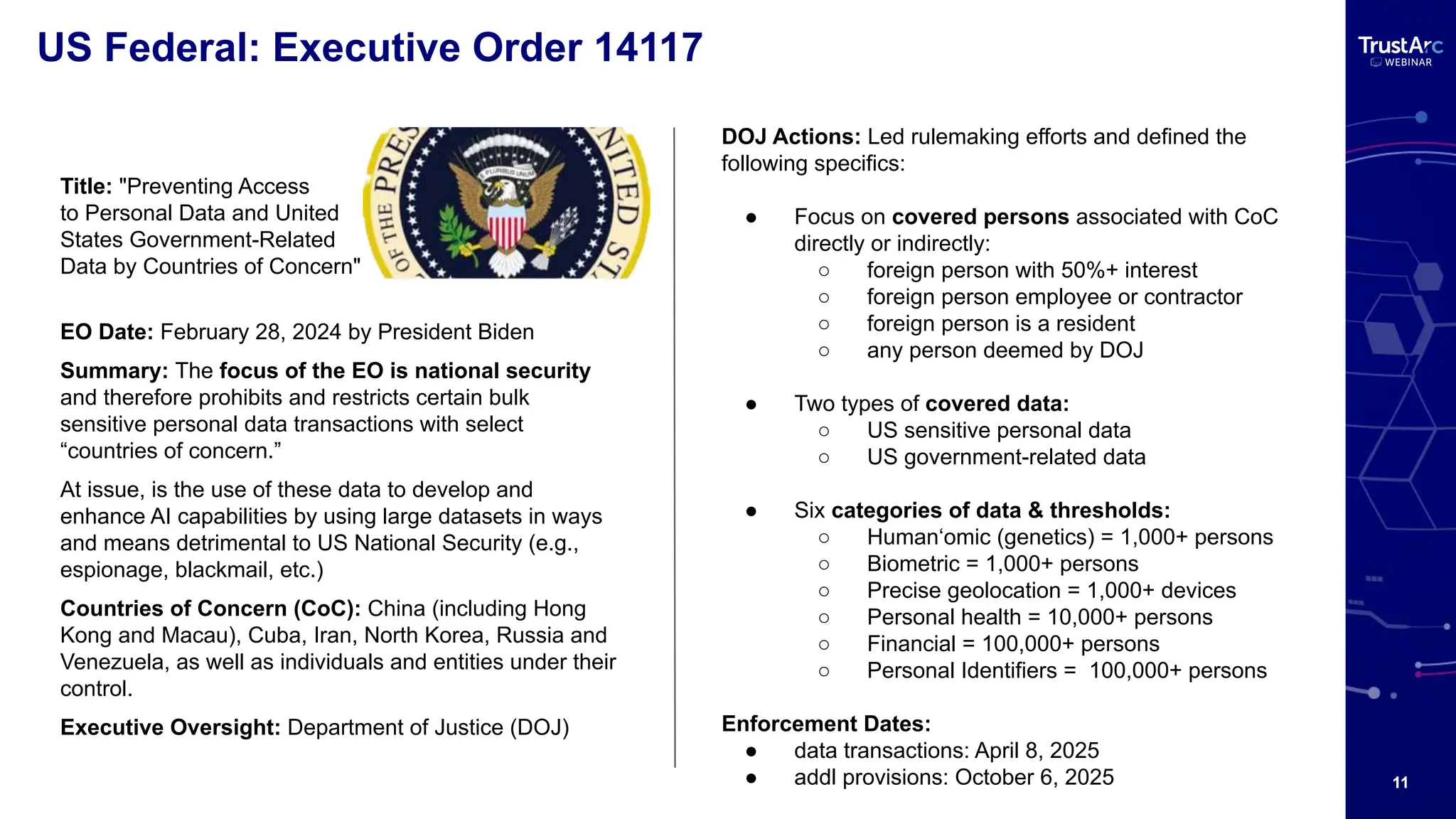
With increasing attention to healthcare privacy and enforcement actions proposed with the HIPPA Privacy Rules Changes planned for 2025, healthcare leaders must understand how to grow and maintain privacy programs effectively and have insights into their privacy methods.
Indeed, the healthcare industry faces numerous new challenges, including the rapid adoption of virtual health and other digital innovations, consumers’ increasing involvement in care decision-making, and the push for interoperable data and data analytics. How can the industry adapt?
Join our panel on this webinar as we explore the privacy risks and challenges the healthcare industry will likely encounter in 2025 and how healthcare organizations can use privacy as a differentiating factor.
This webinar will review:
- Current benchmarks of privacy management maturity in healthcare organizations
- Upcoming data privacy vulnerabilities and opportunities resulting from healthcare’s digital transformation efforts
- How healthcare companies can differentiate themselves with their privacy program