In 2025, cross-border data transfers are becoming harder to manage—not because there are no rules, the regulatory environment has become increasingly complex. Legal obligations vary by jurisdiction, and risk factors include national security, AI, and vendor exposure. Some of the examples of the recent developments that are reshaping how organizations must approach transfer governance:
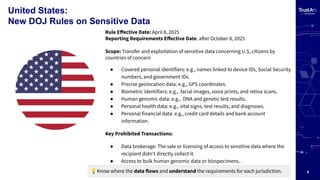
- The U.S. DOJ’s new rule restricts the outbound transfer of sensitive personal data to foreign adversaries countries of concern, introducing national security-based exposure that privacy teams must now assess.
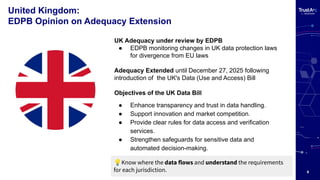
- The EDPB confirmed that GDPR applies to AI model training — meaning any model trained on EU personal data, regardless of location, must meet lawful processing and cross-border transfer standards.
- Recent enforcement — such as a €290 million GDPR fine against Uber for unlawful transfers and a €30.5 million fine against Clearview AI for scraping biometric data signals growing regulatory intolerance for cross-border data misuse, especially when transparency and lawful basis are lacking.
- Gartner forecasts that by 2027, over 40% of AI-related privacy violations will result from unintended cross-border data exposure via GenAI tools.
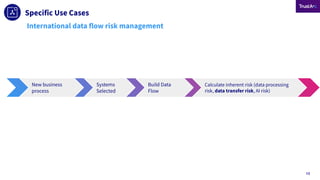
Together, these developments reflect a new era of privacy risk: not just legal exposure—but operational fragility. Privacy programs must/can now defend transfers at the system, vendor, and use-case level—with documentation, certification, and proactive governance.
The session blends policy/regulatory events and risk framing with practical enablement, using these developments to explain how TrustArc’s Data Mapping & Risk Manager, Assessment Manager and Assurance Services help organizations build defensible, scalable cross-border data transfer programs.
This webinar is eligible for 1 CPE credit.