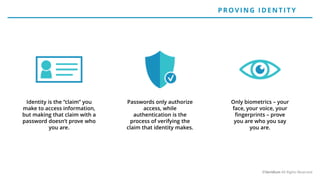
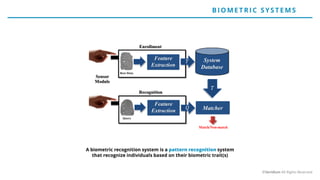
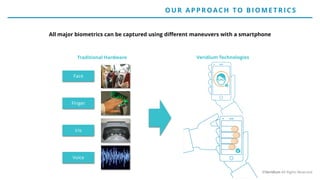
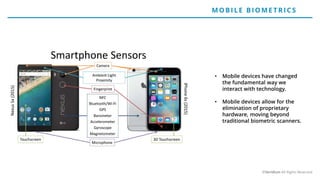
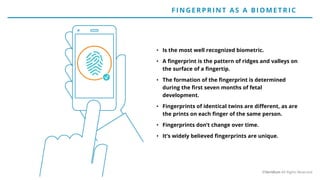
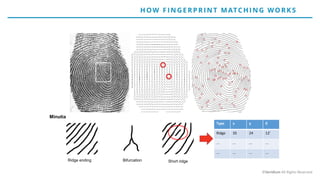
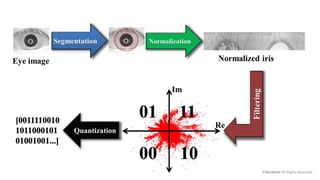
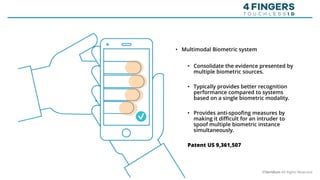
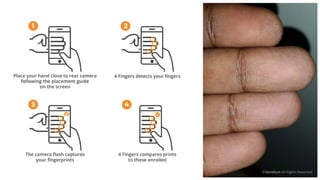
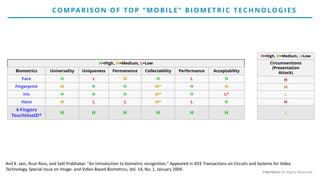
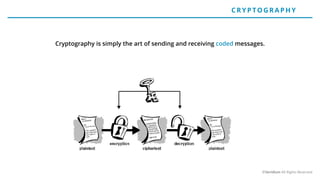
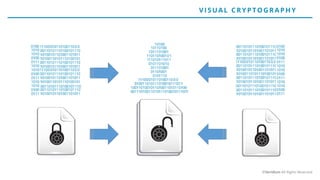
The document discusses the risks and rewards of biometric identifiers, focusing on their application in mobile technologies, including face, voice, fingerprint, and iris recognition. It highlights the importance of biometrics in proving identity and addresses privacy concerns associated with biometric data storage and security. The presentation also emphasizes the advantages of using a multimodal system like Veridium's 4 Fingers TouchlessID for improved recognition and security.