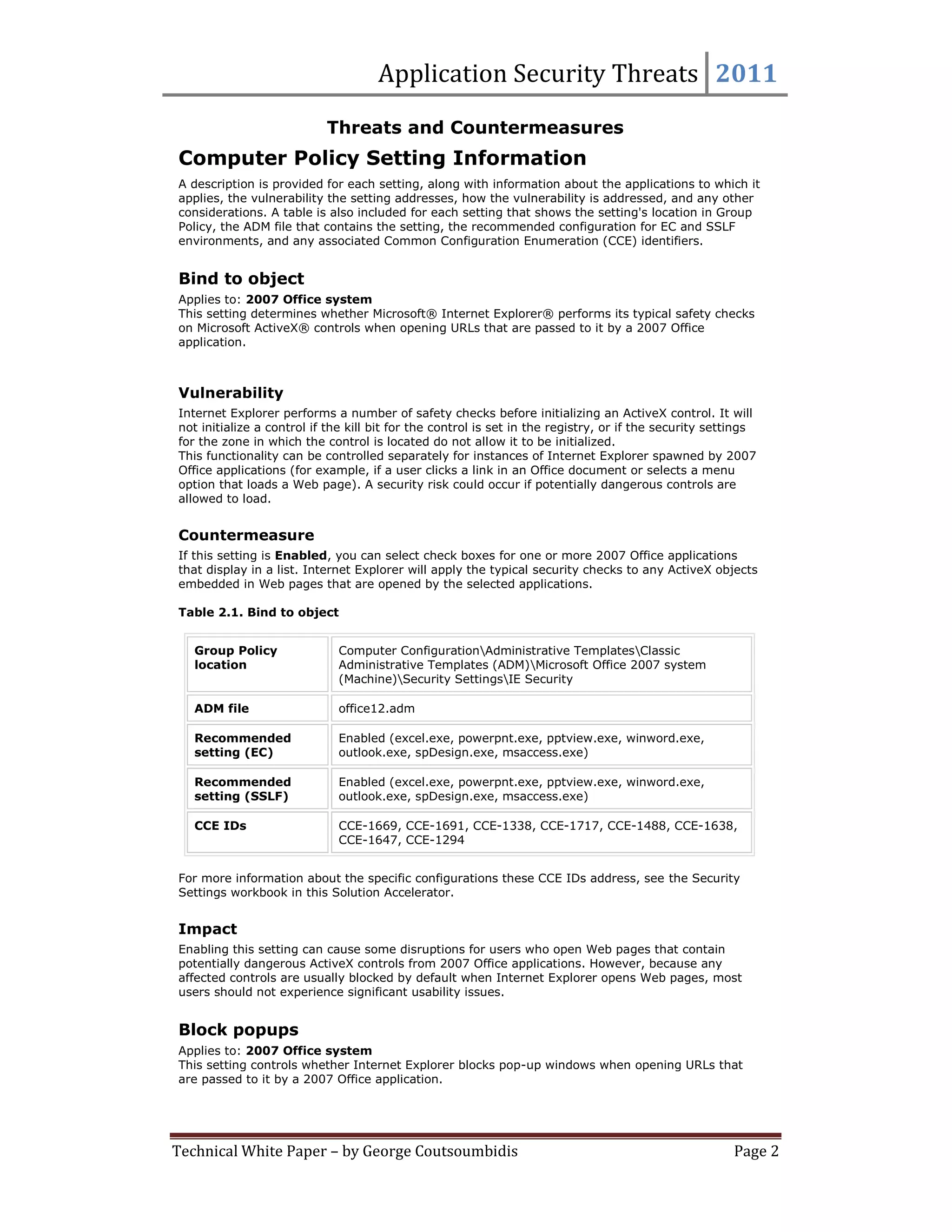
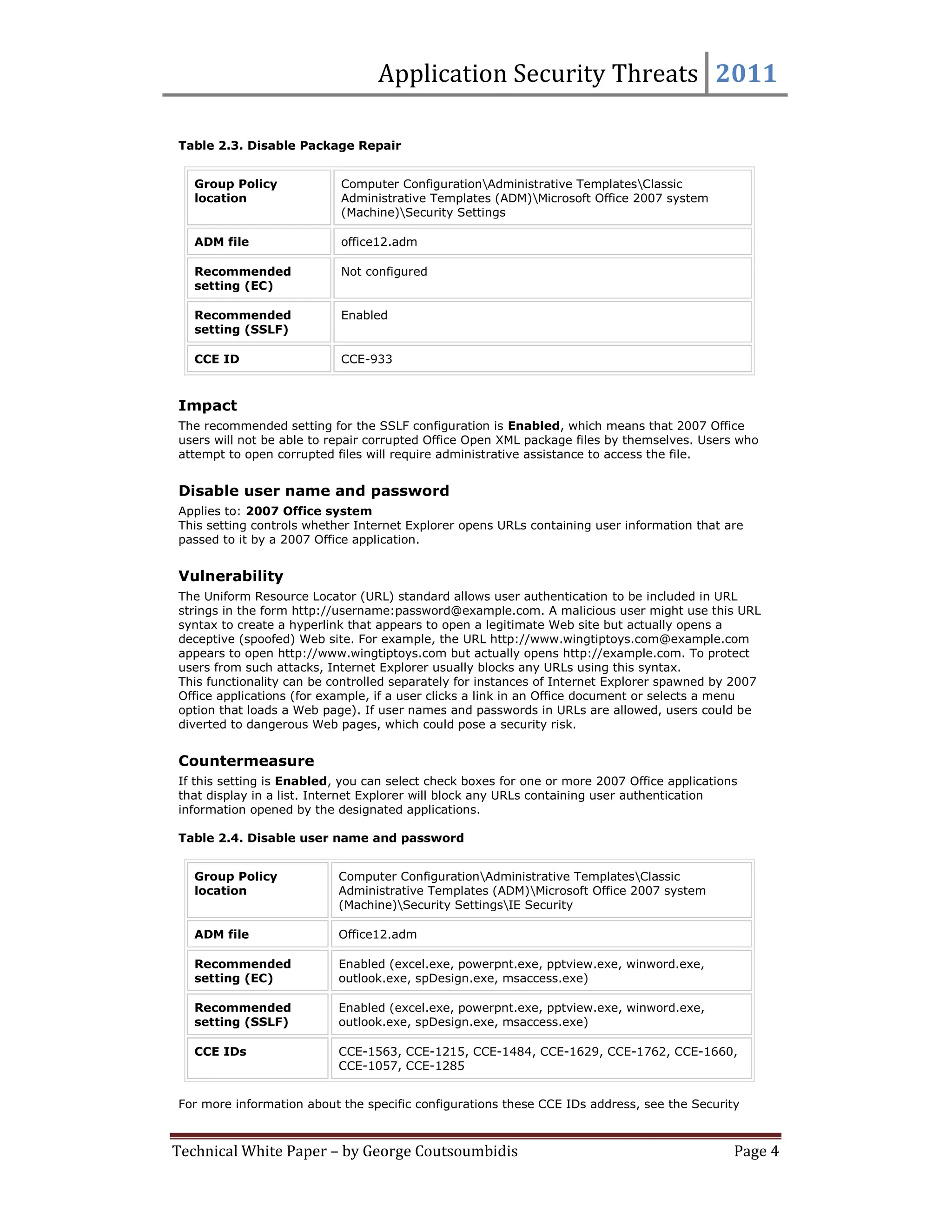
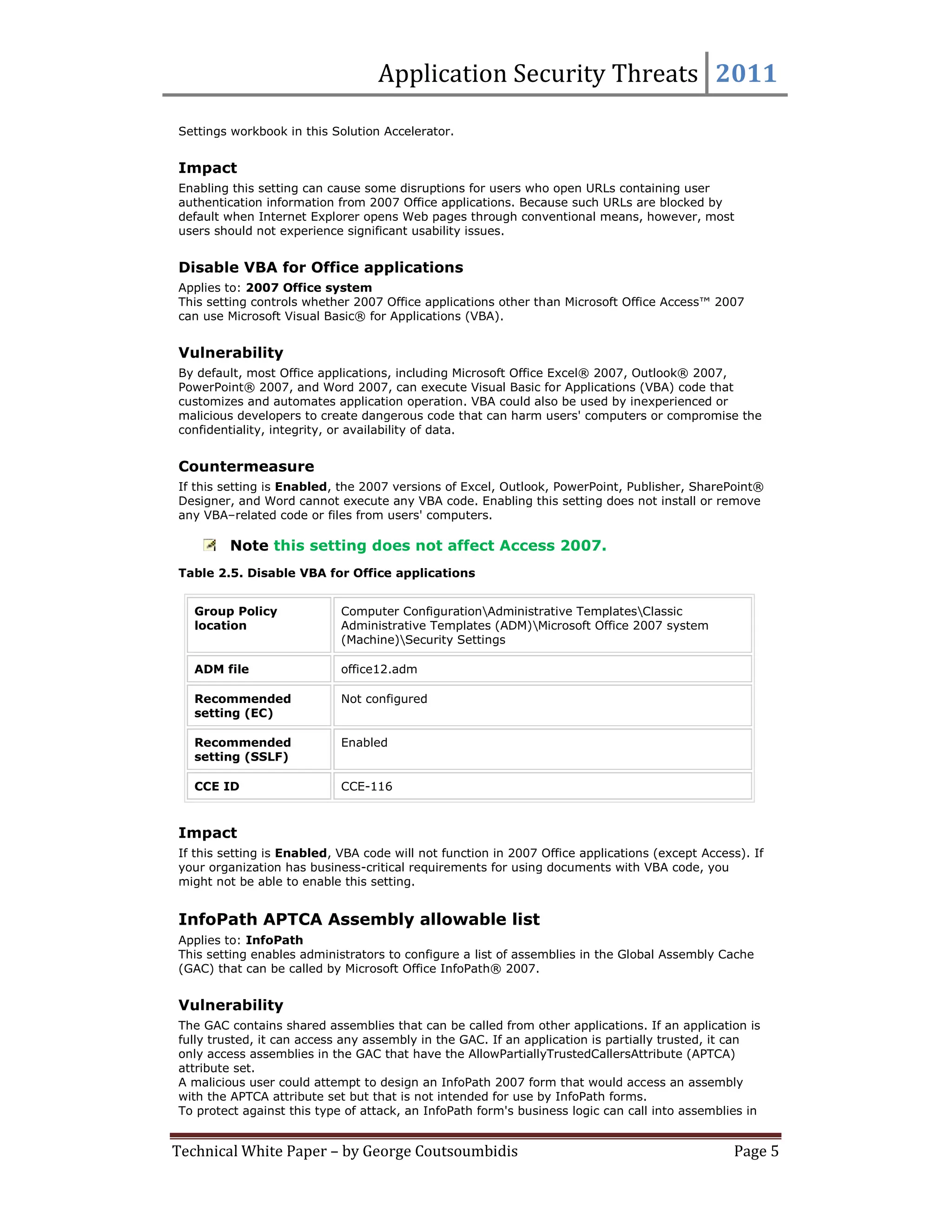
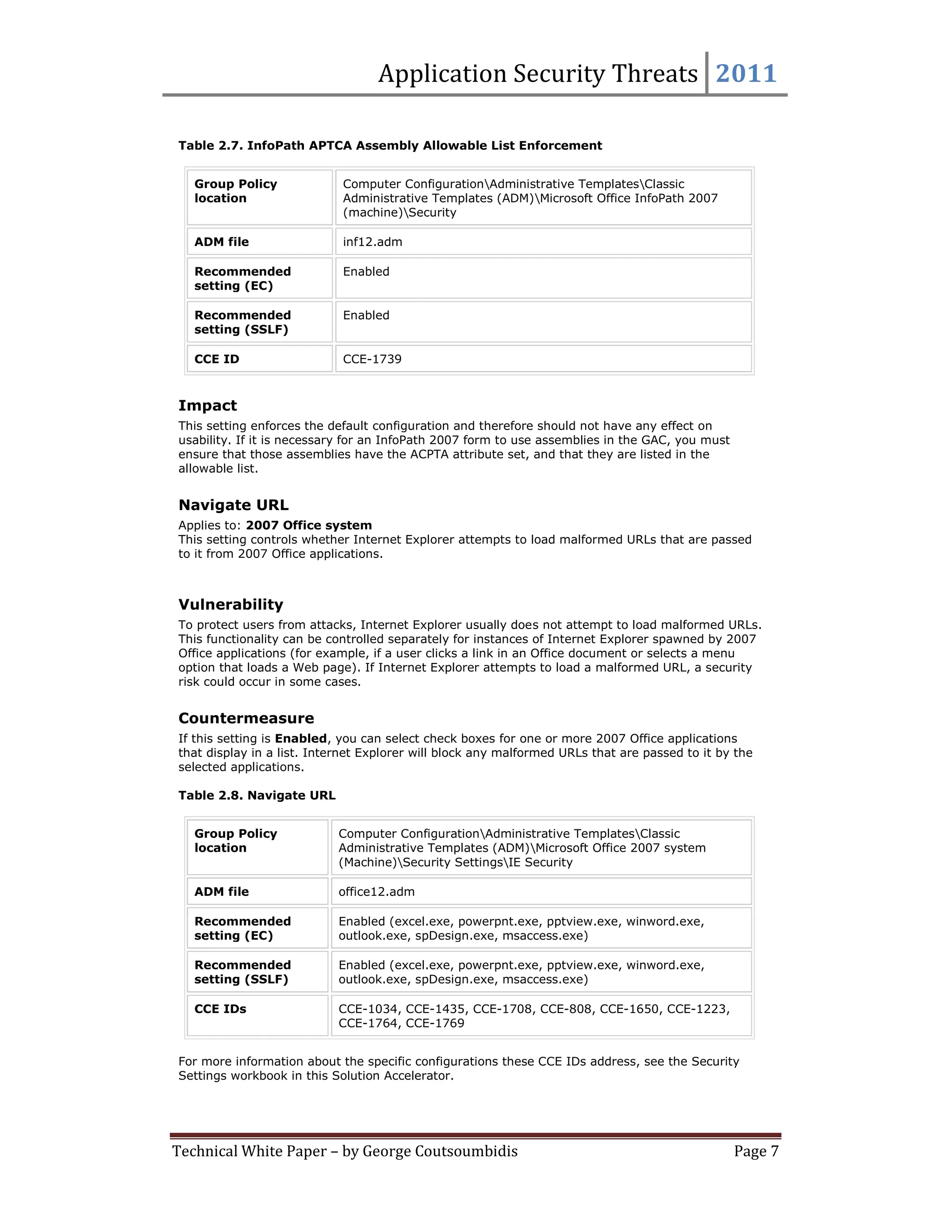
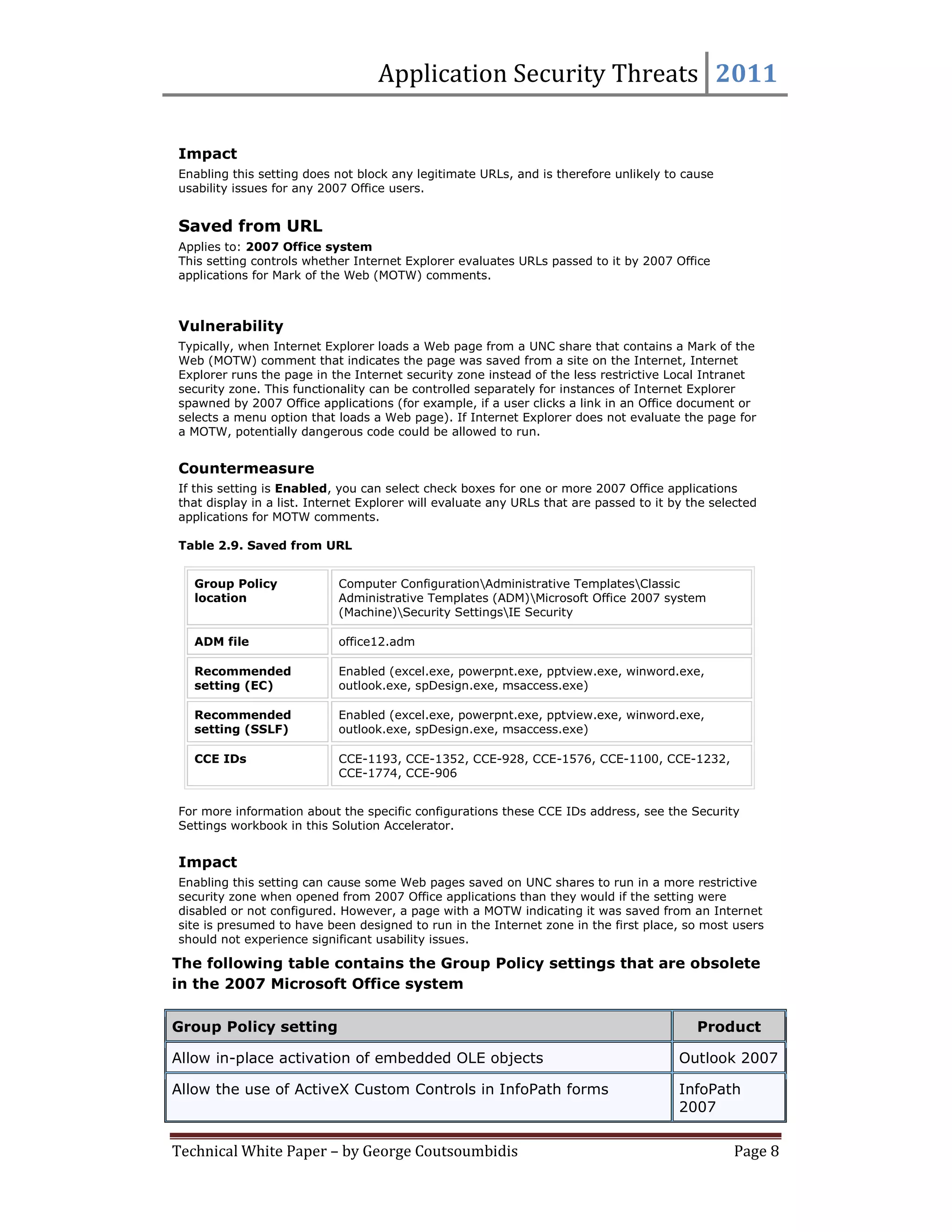
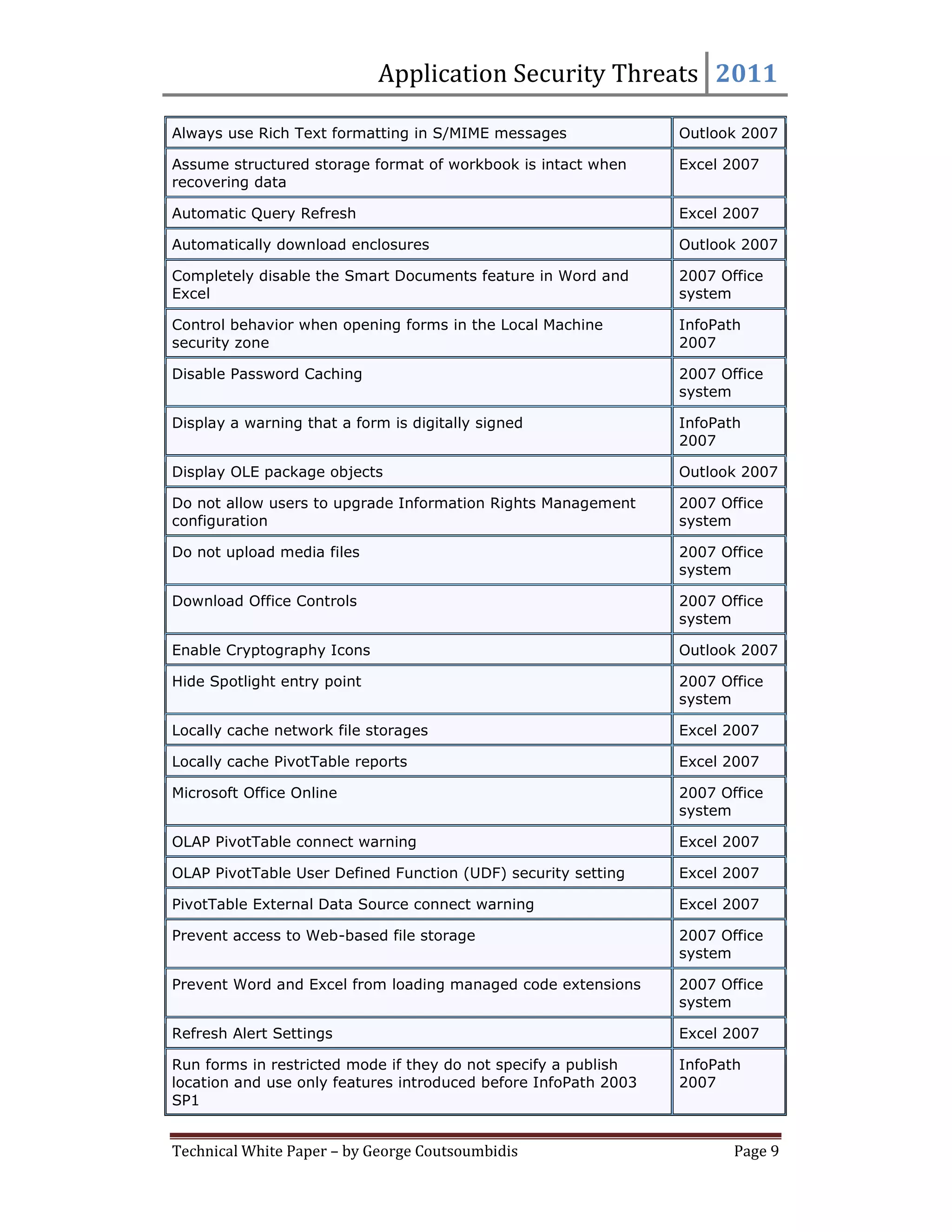
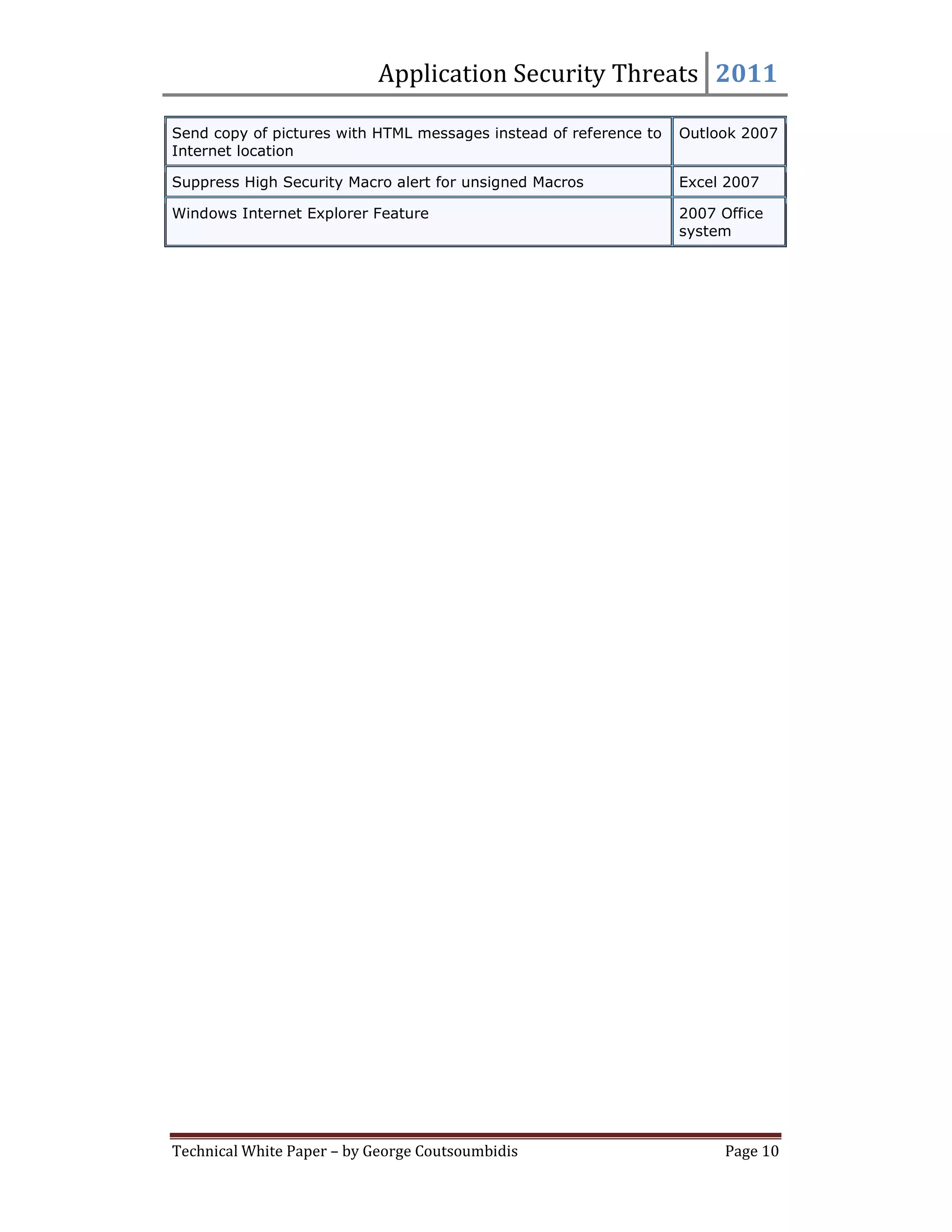
This document provides summaries for 9 settings related to application security threats in Microsoft Office 2007. Each setting summary describes the vulnerability addressed, the recommended countermeasure of enabling the setting for various Office applications, and potential impact. The settings control whether Internet Explorer performs typical safety checks on ActiveX controls opened from Office, blocks popups, and more. Enabling the settings can disrupt users in rare cases but provides protection from security risks.