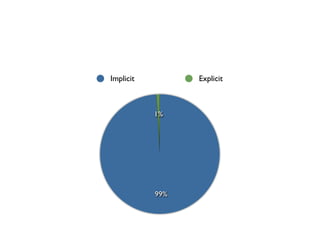
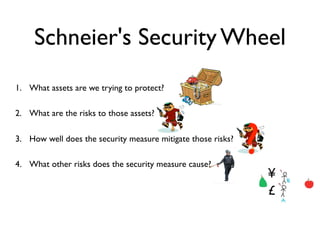
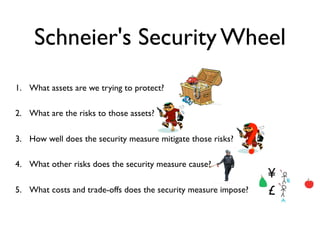
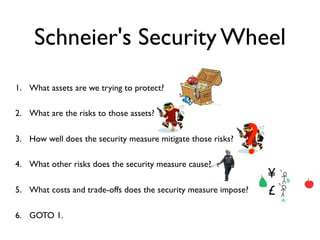
The document discusses threat modeling and how most security measures are implicit rather than explicit. It recommends making threat modeling explicit by following Schneier's Security Wheel to evaluate each security measure: assessing assets, risks, how the measure mitigates risks, new risks it creates, and costs/trade-offs. The speaker argues for bringing all security measures into an explicit threat model, getting diverse input, ensuring each measure addresses credible threats, regularly reviewing the model, and removing outdated measures. The goal is to eliminate "security theater" and make security evaluation everybody's responsibility.