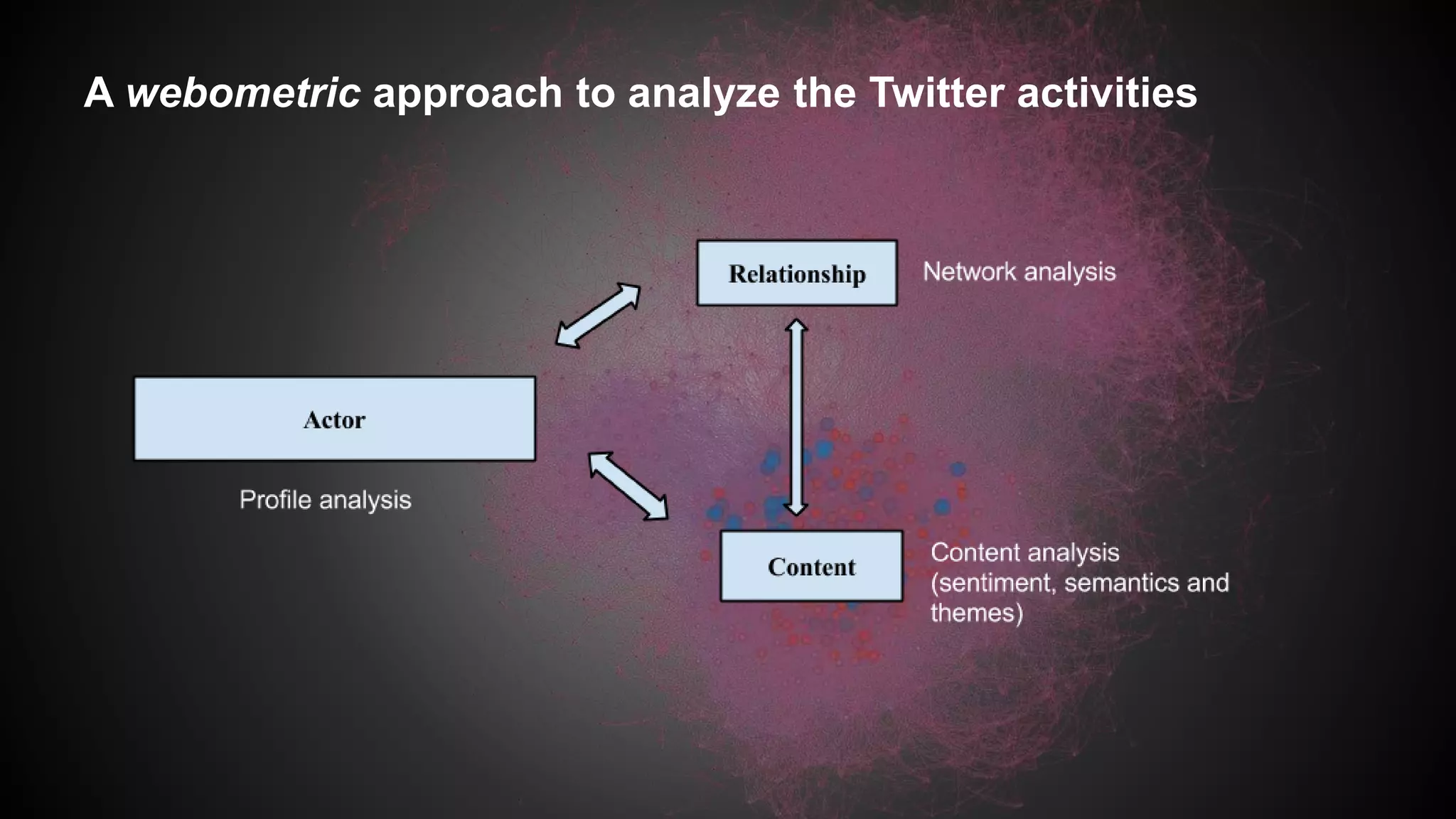
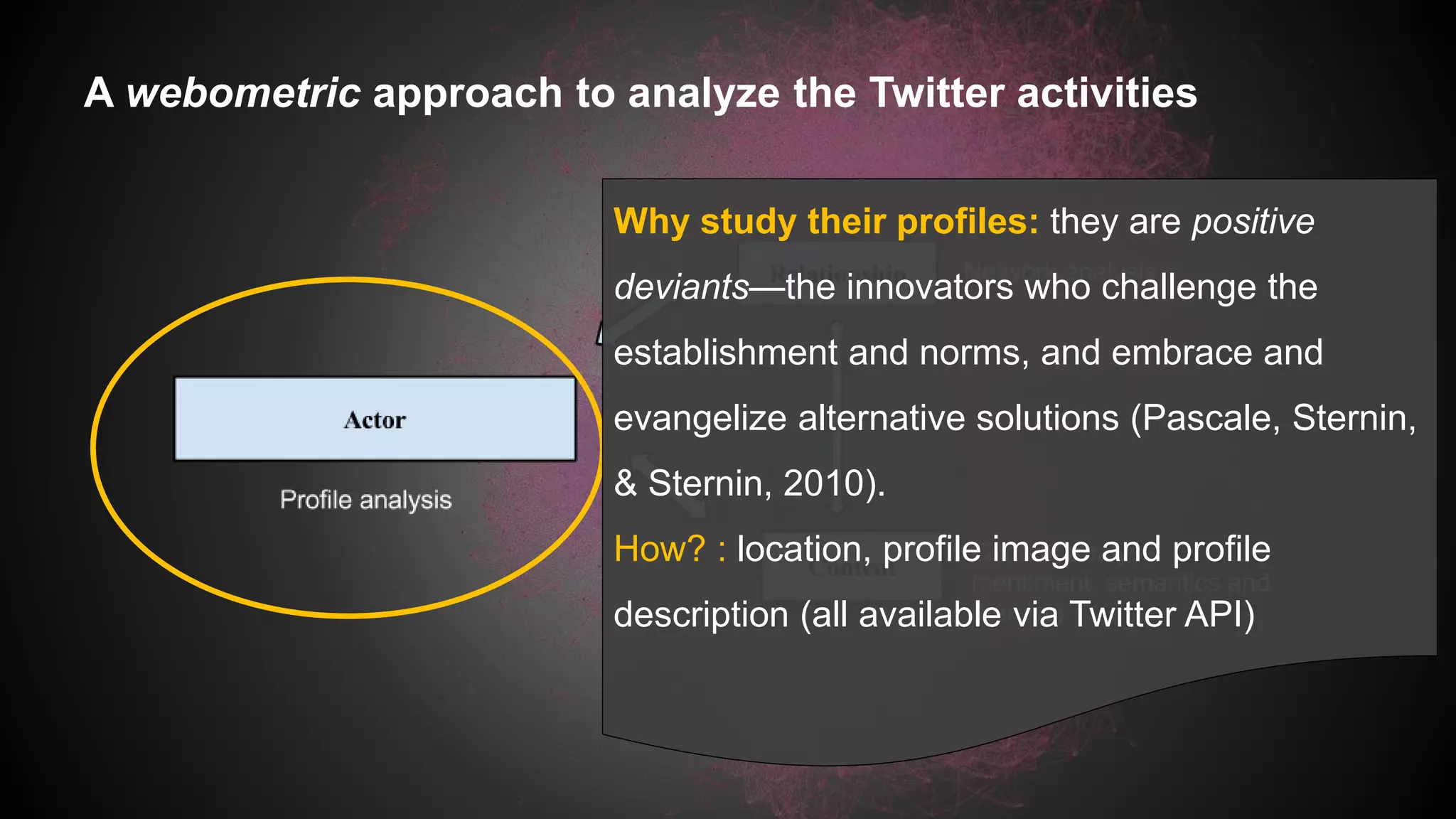
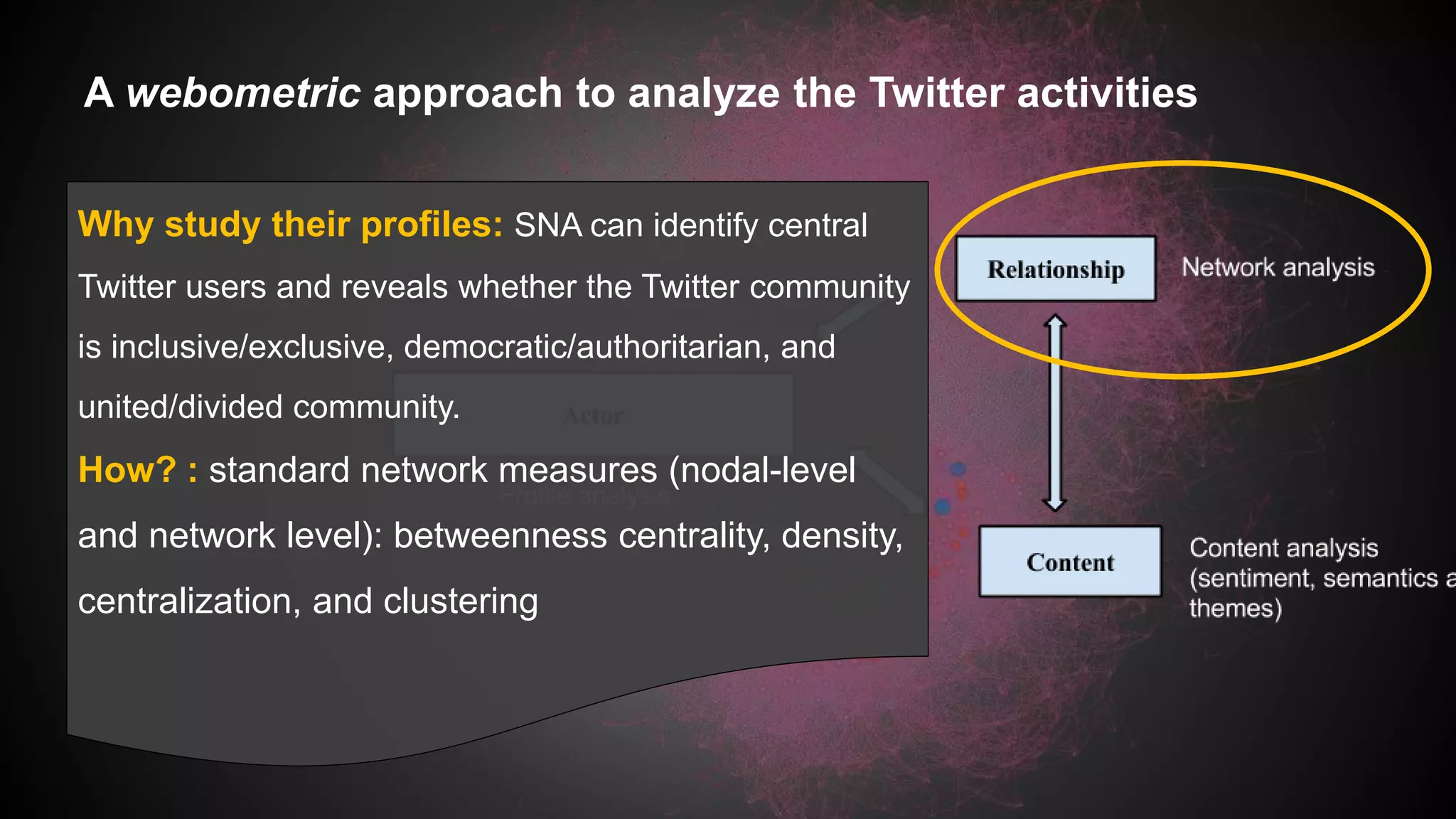
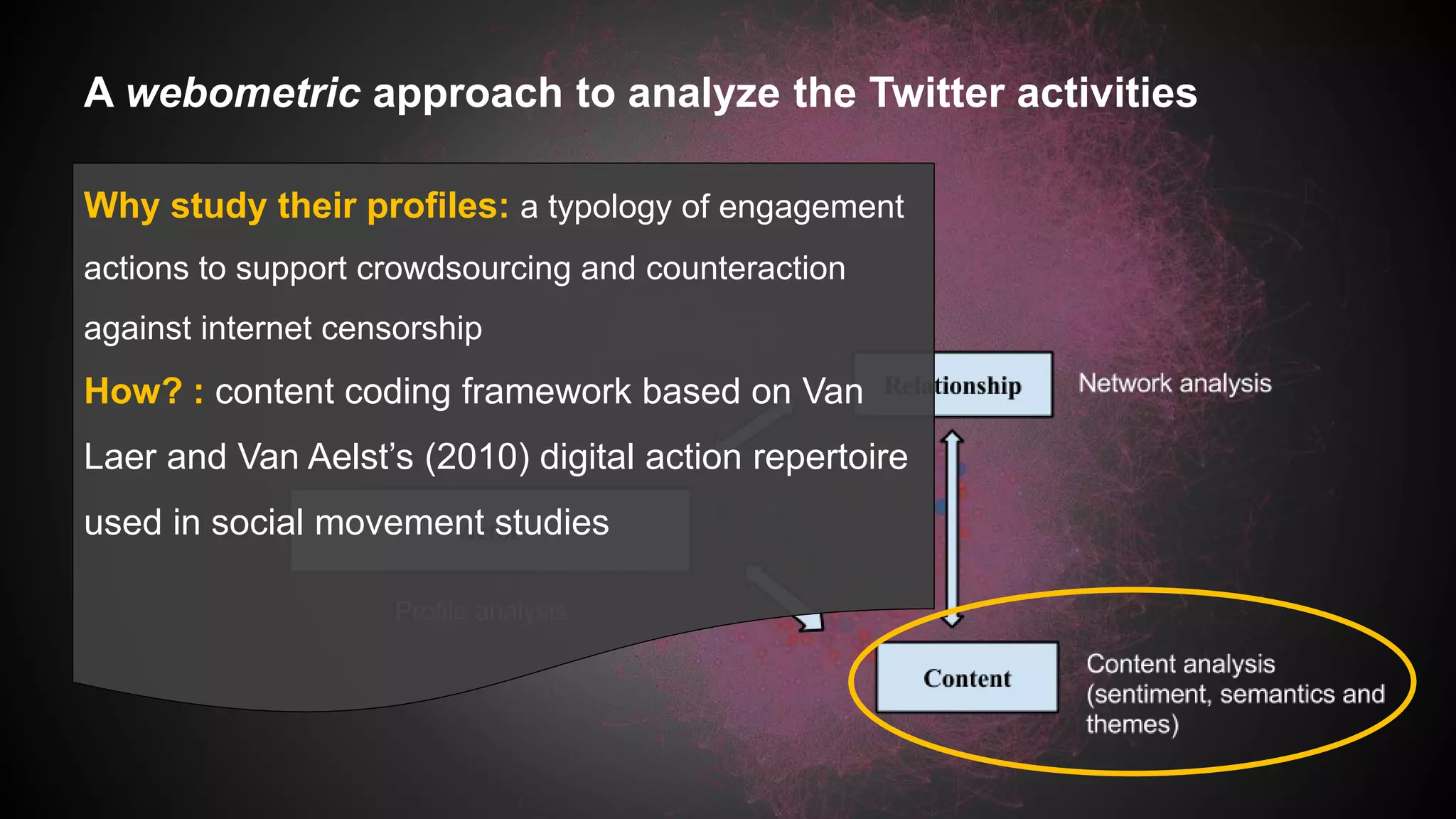
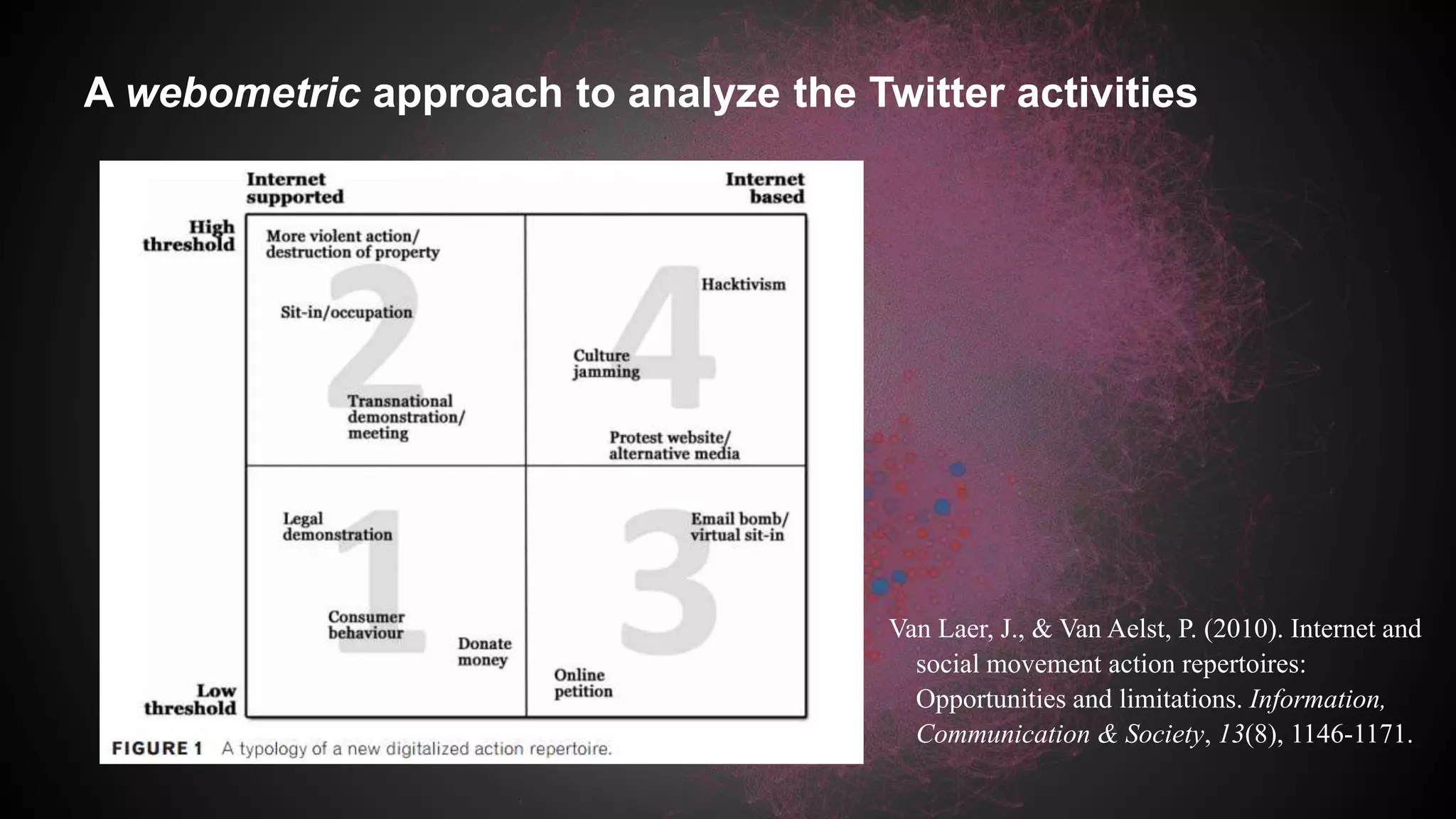
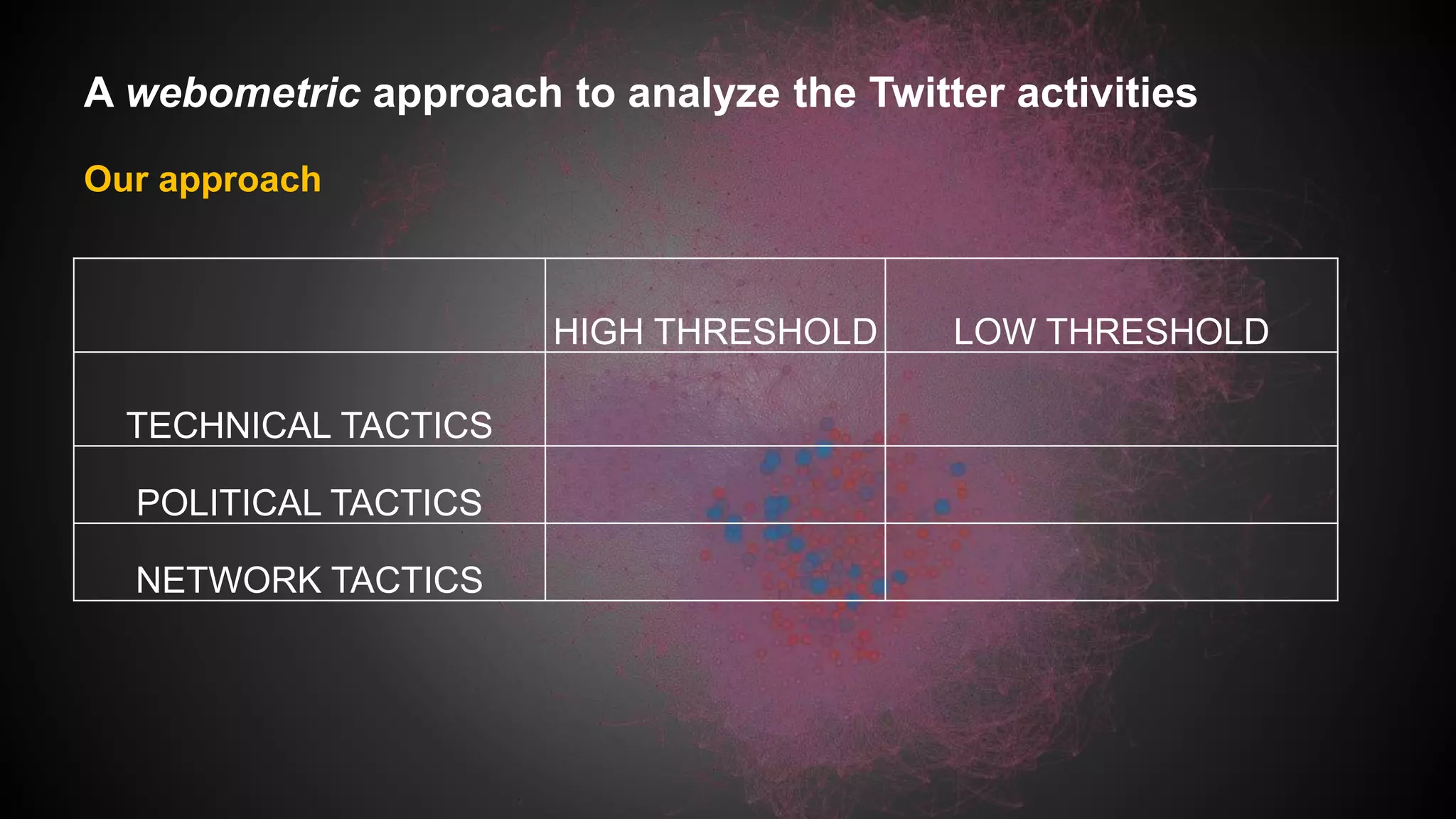
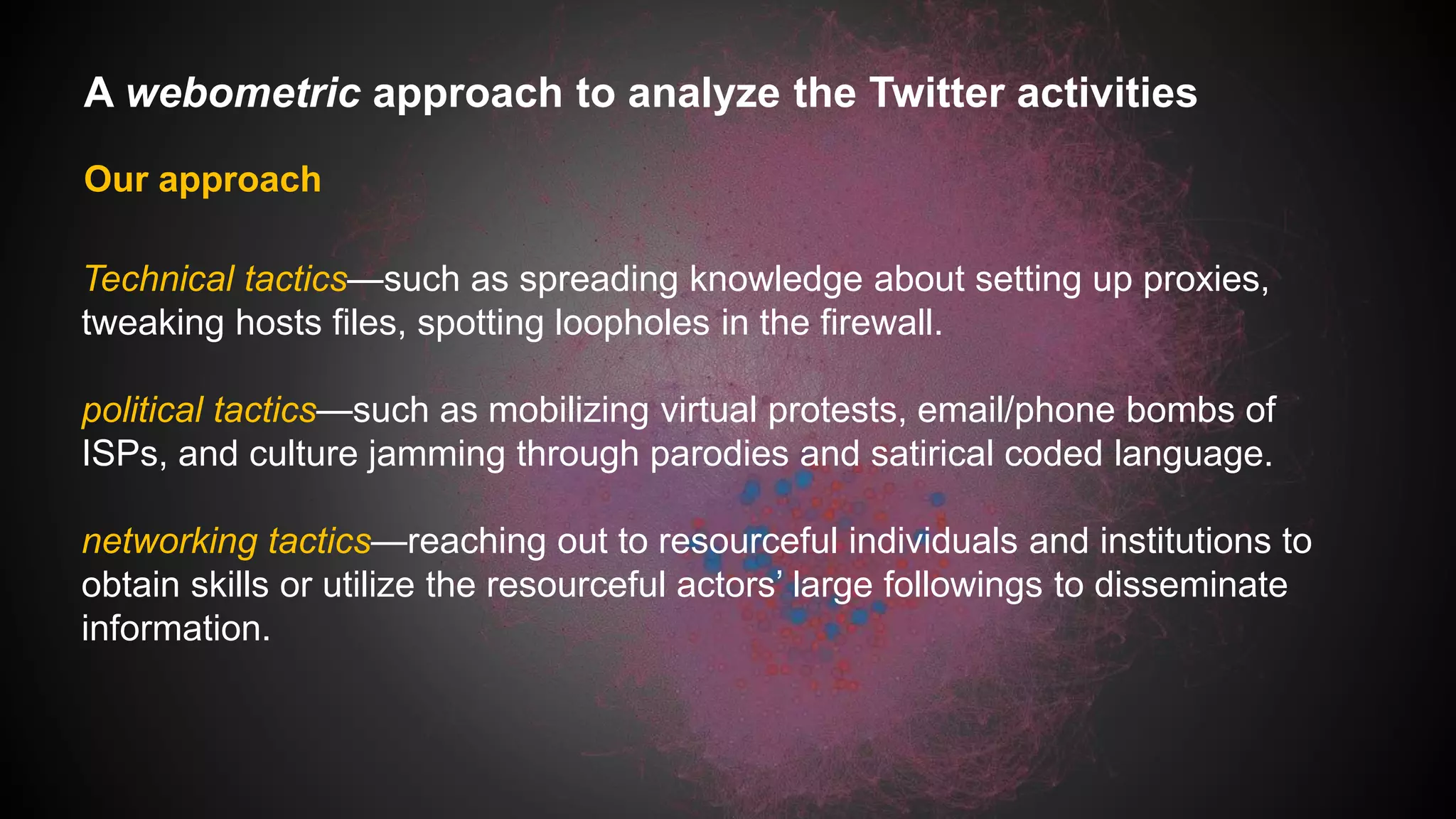
This document discusses a study analyzing the Twitter activities of Chinese users discussing and mobilizing around internet censorship. It provides background on China's censorship policies and innovations used to bypass them. The study uses Twitter data from 2014 and network, content, and demographic analyses to understand how users interact, tactics used, and characteristics of central users in the censorship discussion network. The goal is to understand how Web 2.0 platforms facilitate technological and political strategies to crowdsource responses to censorship.