The great cannon has been deployed again
•
0 likes•85 views
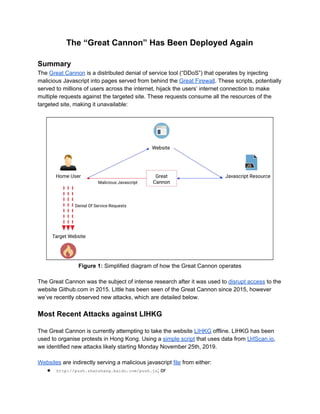
The Great Cannon is a distributed denial of service tool (“DDoS”) that operates by injecting malicious Javascript into pages served from behind the Great Firewall. These scripts, potentially served to millions of users across the internet, hijack the users’ internet connection to make multiple requests against the targeted site. These requests consume all the resources of the targeted site, making it unavailable:
Report
Share
Report
Share
Download to read offline
Recommended
GNUCITIZEN Pdp Owasp Day September 2007

The document discusses potential ways that Web 2.0 technologies could be abused by malicious actors, through five fictional stories. It describes how social networks, APIs, cloud services and other Web 2.0 features could enable new types of malware, spam, botnets and data theft. The stories illustrate techniques like using mashups and feeds to distribute malware, exploiting search and social media to spread worms, using bookmarks for ad-jacking and creating botnets, and abusing aggregators and search engines to conduct reconnaissance. The document warns that legitimate Web 2.0 services could enable large-scale abuse if exploited by attackers.
CloudBots - Harvesting Crypto Currency Like a Botnet Farmer

What happens when computer criminals start using friendly cloud services for malicious activities? In this presentation, we explore how to (ab)use free trials to get access to vast amounts of computing power, storage, and pre-made hacking environments. Oh! Also, we violate the hell out of some terms of service.
We explore just how easy it is to generate massive amounts of unique email addresses; in order to register free trial accounts, deploy code, and distribute commands (C2). We managed to build this cloud-based botnet all for the low cost of $0 and semi-legally. This botnet doesn't get flagged as malware, blocked by web filters, or get taken over. This is the stuff of nightmares!
While riding on the fluffy Kumobot (kumo means cloud in Japanese), it was discovered that we were not the only ones doing this! With the rise of crypto currency we now face the impending rise of botnets that mine for digital gold on someone else's systems with someone else's dime footing the electric bill. Through our efforts in building a cloud-based botnet we built enough tools to share a framework for penetration testers and security researchers. The anti-anti-automation framework will show those tasked with defense exactly what it looks like when their free trial gets assaulted.
Developer in a digital crosshair, 2022 edition - No cON Name

The frequency of attacks on third-party libraries and tools used in software development has dramatically increased in recent years.
Typosquatting, dependency confusion, malicious changes in popular dependencies (UAParser.js, coa, node-ipc...), issues in popular dev tools (Codecov, Homebrew, npm...) or incidents (PHP, GitHub...). In this presentation, I will go over many fascinating, recent examples of these attacks, their causes and effects, and recommend to you how to stay secure when developing software.
IRJET- Browser Extension for Cryptojacking Malware Detection and Blocking

This document proposes a browser extension to detect and block cryptojacking malware. Cryptojacking is when attackers use people's computing power to mine cryptocurrency without permission. The extension would check websites for malicious JavaScript code used for cryptojacking. If found, it would notify users and block the code, allowing users to access the site without their computing power being exploited. It describes how cryptojacking works, related research, and proposes measuring a system's CPU usage and other task performance before and after visiting an infected site to demonstrate cryptojacking's impact. The system architecture includes a front-end browser extension that checks URLs against a back-end database of known cryptojacking sites before allowing or blocking scripts.
Developer in a digital crosshair, 2023 edition - 4Developers

Recent years show a significant increase in attacks against libraries, tools, and infrastructure used in application development, as well as directly against developers and software companies. From fake libraries and malicious changes to popular libraries or programming languages to vulnerabilities in CI/CD infrastructure components.
During the presentation, you will discover a handful of interesting, fresh examples and attack techniques and, perhaps most importantly, learn how to work safely as a programmer. You will find out about typosquatting, dependency confusion, protestware and discover stories of attacks on PHP, Codecov, Homebrew, npm, Ruby Gems, or GitHub.
Attack with-html5

The document discusses various attacks that can be carried out using new features introduced in HTML5, even on websites that do not currently support HTML5. It describes attacks such as cross-site scripting using new HTML5 elements and event attributes, creating reverse web shells using cross-origin resource sharing, bypassing clickjacking defenses using drag and drop APIs and iframe sandboxing, poisoning HTML5 caches, performing client-side remote file inclusion and cross-site posting by controlling AJAX requests, and performing network reconnaissance like port scanning within internal networks using cross-domain XMLHttpRequests and WebSockets. The attacks show that HTML5 introduces new security risks even before its features are widely adopted.
Developer in a digital crosshair, 2022 edition

This presentation takes you through recent attacks aimed at software developers and software companies. First it starts with attacks on libraries you install or have installed (typosquatting, pushing malicious library updates due to maintainer's credential takeover, protestware), even your private ones (dependency confusion). Second it shows attack on tools which are used in software development (package managers). Third, there are examples of attacks onto developer's infrastructure (PHP programming language git sever, GitHub OAuth incident with Heroku and Travis-CI).
Developer in a digital crosshair, 2022 edition - Oh My H@ck!

Attacks on third-party libraries and tools that are often used while developing software have become dramatically frequent.
Among these attacks, one can find dependency confusion, issues in popular dev tools (Codecov, Homebrew, npm...), typosquatting, incidents (PHP, GitHub...), or malicious changes in popular dependencies (UAParser.js, coa, node-ipc...). I will share a lot of gripping real-life examples of such attacks, their causes and effects, and help you stay secure while developing software.
Recommended
GNUCITIZEN Pdp Owasp Day September 2007

The document discusses potential ways that Web 2.0 technologies could be abused by malicious actors, through five fictional stories. It describes how social networks, APIs, cloud services and other Web 2.0 features could enable new types of malware, spam, botnets and data theft. The stories illustrate techniques like using mashups and feeds to distribute malware, exploiting search and social media to spread worms, using bookmarks for ad-jacking and creating botnets, and abusing aggregators and search engines to conduct reconnaissance. The document warns that legitimate Web 2.0 services could enable large-scale abuse if exploited by attackers.
CloudBots - Harvesting Crypto Currency Like a Botnet Farmer

What happens when computer criminals start using friendly cloud services for malicious activities? In this presentation, we explore how to (ab)use free trials to get access to vast amounts of computing power, storage, and pre-made hacking environments. Oh! Also, we violate the hell out of some terms of service.
We explore just how easy it is to generate massive amounts of unique email addresses; in order to register free trial accounts, deploy code, and distribute commands (C2). We managed to build this cloud-based botnet all for the low cost of $0 and semi-legally. This botnet doesn't get flagged as malware, blocked by web filters, or get taken over. This is the stuff of nightmares!
While riding on the fluffy Kumobot (kumo means cloud in Japanese), it was discovered that we were not the only ones doing this! With the rise of crypto currency we now face the impending rise of botnets that mine for digital gold on someone else's systems with someone else's dime footing the electric bill. Through our efforts in building a cloud-based botnet we built enough tools to share a framework for penetration testers and security researchers. The anti-anti-automation framework will show those tasked with defense exactly what it looks like when their free trial gets assaulted.
Developer in a digital crosshair, 2022 edition - No cON Name

The frequency of attacks on third-party libraries and tools used in software development has dramatically increased in recent years.
Typosquatting, dependency confusion, malicious changes in popular dependencies (UAParser.js, coa, node-ipc...), issues in popular dev tools (Codecov, Homebrew, npm...) or incidents (PHP, GitHub...). In this presentation, I will go over many fascinating, recent examples of these attacks, their causes and effects, and recommend to you how to stay secure when developing software.
IRJET- Browser Extension for Cryptojacking Malware Detection and Blocking

This document proposes a browser extension to detect and block cryptojacking malware. Cryptojacking is when attackers use people's computing power to mine cryptocurrency without permission. The extension would check websites for malicious JavaScript code used for cryptojacking. If found, it would notify users and block the code, allowing users to access the site without their computing power being exploited. It describes how cryptojacking works, related research, and proposes measuring a system's CPU usage and other task performance before and after visiting an infected site to demonstrate cryptojacking's impact. The system architecture includes a front-end browser extension that checks URLs against a back-end database of known cryptojacking sites before allowing or blocking scripts.
Developer in a digital crosshair, 2023 edition - 4Developers

Recent years show a significant increase in attacks against libraries, tools, and infrastructure used in application development, as well as directly against developers and software companies. From fake libraries and malicious changes to popular libraries or programming languages to vulnerabilities in CI/CD infrastructure components.
During the presentation, you will discover a handful of interesting, fresh examples and attack techniques and, perhaps most importantly, learn how to work safely as a programmer. You will find out about typosquatting, dependency confusion, protestware and discover stories of attacks on PHP, Codecov, Homebrew, npm, Ruby Gems, or GitHub.
Attack with-html5

The document discusses various attacks that can be carried out using new features introduced in HTML5, even on websites that do not currently support HTML5. It describes attacks such as cross-site scripting using new HTML5 elements and event attributes, creating reverse web shells using cross-origin resource sharing, bypassing clickjacking defenses using drag and drop APIs and iframe sandboxing, poisoning HTML5 caches, performing client-side remote file inclusion and cross-site posting by controlling AJAX requests, and performing network reconnaissance like port scanning within internal networks using cross-domain XMLHttpRequests and WebSockets. The attacks show that HTML5 introduces new security risks even before its features are widely adopted.
Developer in a digital crosshair, 2022 edition

This presentation takes you through recent attacks aimed at software developers and software companies. First it starts with attacks on libraries you install or have installed (typosquatting, pushing malicious library updates due to maintainer's credential takeover, protestware), even your private ones (dependency confusion). Second it shows attack on tools which are used in software development (package managers). Third, there are examples of attacks onto developer's infrastructure (PHP programming language git sever, GitHub OAuth incident with Heroku and Travis-CI).
Developer in a digital crosshair, 2022 edition - Oh My H@ck!

Attacks on third-party libraries and tools that are often used while developing software have become dramatically frequent.
Among these attacks, one can find dependency confusion, issues in popular dev tools (Codecov, Homebrew, npm...), typosquatting, incidents (PHP, GitHub...), or malicious changes in popular dependencies (UAParser.js, coa, node-ipc...). I will share a lot of gripping real-life examples of such attacks, their causes and effects, and help you stay secure while developing software.
Cryptojacking - by Vishwaraj101

Cryptojacking involves secretly using a victim's computing resources to mine cryptocurrencies without consent. Attackers can embed cryptojacking scripts on websites through vulnerabilities like cross-site scripting (XSS). When visitors access the infected sites, their browsers' CPUs are used to generate cryptocurrency for the attacker. Other cryptojacking methods include subdomain takeovers, network-level attacks by setting up rogue hotspots, and exploiting remote code execution bugs to install cryptojacking software. Website owners can prevent cryptojacking by fixing security issues, implementing content security policies and HTTPS, and monitoring CPU usage.
JSconf JP - Analysis of an exploited npm package. Event-stream's role in a su...

This document summarizes an analysis of an exploited NPM package called event-stream. It describes how an attacker gained control of the package and added malicious code that was downloaded by thousands of projects whenever their dependencies were updated. The malicious code stole cryptocurrency from wallets containing large amounts. It highlights the risks of supply chain attacks and emphasizes the importance of auditing dependencies, locking versions, and thinking carefully before adding new dependencies to avoid compromising entire projects and their users.
Compromised e commerce_sites_lead_to_web-based_keyloggers

The document discusses a keylogger injection campaign targeting eCommerce sites called "Magecart". It describes how attackers injected JavaScript keylogger code into compromised shopping cart platforms like Magento to steal payment card data. The code captured form fields and sent data to remote attacker sites. The campaign evolved over time from 2016 onward, with attackers refining code and expanding which payment providers were targeted. The document provides examples of keylogger injections on specific compromised sites faber.co.uk and everlast.com.
HallTumserFinalPaper

This document discusses cross-site scripting (XSS) attacks. It begins by defining XSS and explaining that it occurs when an attacker uses a victim's browser to run malicious scripts. There are three main types of XSS attacks: reflected, stored, and DOM-based. The document then discusses the history and evolution of XSS attacks, providing examples over time that increased in scale and sophistication. It covers technical details of how the different XSS attacks work and potential impacts from a professional, social, and ethical perspective. The goal is to raise awareness about XSS vulnerabilities and prevention.
DevOps Automation Principles

The World is full of examples where DevOps Automation principles help in growing and improving companies in every aspect. DevOps isn’t a “thing,” it’s a set of principles which lay the fundamental groundwork of technology, purpose, and people.
STUDY OF DEEP WEB AND A NEW FORM BASED CRAWLING TECHNIQUE

This document describes a study of the deep web and a new form-based crawling technique. It defines the deep web as unindexed web content that can only be accessed by filling out forms. The paper proposes a crawling method that equips web crawlers with appropriate input values to submit forms and retrieve search results. An experiment on people search websites demonstrates the technique, achieving high precision and recall rates in associating forms, domains, and attributes. In conclusion, the form-based crawling approach shows potential for effectively surfacing content from the deep web.
Software management, the seasonal return of DDoS - This Week in Security.pdf

This weekly security summary from F5 discusses several recent cybersecurity events:
- A proof of concept was published for a critical Fortinet vulnerability, leading to mass exploitation attempts.
- Automotive security threats are increasing as vehicles contain more software.
- Over 45,000 VMware ESXi servers reached end of support, leaving them vulnerable.
- A Minecraft server was hit with a record 2.5 terabit DDoS attack launched by the Mirai botnet.
- A pro-Russian group is paying people to participate in DDoS attacks against Western targets.
Chrome Extensions: Masking risks in entertainment

Chorme extensions are plugins for the Chrome web browser that add functionalities to the browsing experience, but can also include risks like information leakage, unauthorized PII access or profiling. Let's see what are some of these applications hiding.
A look at the prevalence of client-side JavaScript vulnerabilities in web app...

A look at the prevalence of client-side JavaScript vulnerabilities in web app...IBM Rational software
The document discusses the results of a research study into the prevalence of client-side JavaScript vulnerabilities in web applications. The study analyzed 675 websites and found that 14% were vulnerable, with 38% of vulnerabilities introduced by third-party JavaScript code. It also found that 94% of vulnerable sites suffered from DOM-based cross-site scripting issues, while only 11% had open redirect issues. The research suggests client-side vulnerabilities are more common than previously believed.Deep and Dark internet Safari, How to hire a hacker? Robbrecht van Amerongen

Deep and Dark internet Safari, How to hire a hacker? Robbrecht van AmerongenGetting value from IoT, Integration and Data Analytics
Deep and Dark internet Safari, How to hire a hacker. Views on how professional cyber crime organizations are. The Digital Demise - by Robin Turner

This document outlines a proposed net art project called "digital demise" that aims to track and document the destruction caused by hackers on a server. The project will monitor hackers' actions on the server, retrieve the data, and use it to dynamically generate graphic content on a separate website. It discusses the technical components, influences, aesthetics, planning, testing, and potential shortcomings of the project.
Case Study: Q2 2014 Global DDoS Attack Report | Akamai Document

The Brobot botnet that devastated banks with DDoS floods in 2013 may be back. And the techniques that built it – exploiting vulnerabilities in the software that powers websites and cloud companies – is all too alive. Get the full details about this cybercrime threat in the Akamai/Prolexic Q1 2014 DDoS attack report, available for a free download at http://bit.ly/1meTkfu
SeanRobertsThesis

The document presents a hierarchical classification of web vulnerabilities organized into two main groups: general vulnerabilities that affect all web servers and service-specific vulnerabilities found in particular web server programs. General vulnerabilities are further divided into three sub-groups: feature abuse involving misuse of legitimate features, unvalidated input where user input is not checked before being processed, and improper design flaws. Validating user input and disabling vulnerable features can help eliminate certain vulnerability types like cross-site scripting resulting from unvalidated input or cross-site tracing from feature abuse. The hierarchy aims to help webmasters understand and address vulnerabilities by grouping similar issues.
A web content analytics

This document proposes a web content analytics architecture to detect malicious JavaScript through real-time analysis of web traffic. It collects HTTP traffic using a proxy server and analyzes web content through static and dynamic analysis. Static analysis includes pattern matching, and dynamic analysis executes scripts to extract API call traces. Traces are clustered and signatures are generated by combining common tokens to detect similar malicious scripts while reducing false positives. The proposed approach analyzes JavaScript obfuscation and HTML5 usage to determine if further dynamic analysis is needed, and refines signatures through comparison to benign scripts. Evaluation showed the refined signatures improved detection rates while reducing false positives.
(In)Security Implication in the JS Universe

JavaScript is the most widely used language cross platforms. This talk will analyze the security concerns from past to present with a peek to the future of this important language. This talk was presented as Keynote at CyberCamp Espana 2014.
JavaScript Supply Chain Security

1) The document discusses software supply chain security and examples of known attacks, including typosquatting, project takeovers, account takeovers, and inserting malware or backdoors into dependencies.
2) It provides details on specific past attacks, such as those on the event-stream, eslint, and electron-native-notify packages, how they were carried out, and their goals.
3) The presentation recommends steps developers can take to help protect their software supply chains, such as carefully managing dependencies, setting up a SECURITY.md file, enabling GitHub security features, and using two-factor authentication.
CS6262_Group9_FinalReport

This document describes a system for classifying JavaScript scripts as malicious or benign using static analysis and machine learning techniques. The system crawls websites, extracts JavaScript scripts, and analyzes them to extract over 20 structural and statistical features. These features are used to train machine learning classifiers like decision trees and SVMs. The top predictive features include the number of long variable/function names, direct string assignments, string modifying functions, and escape functions. Evaluating this approach on a dataset of over 10,000 scripts from blacklisted sites found 12 truly malicious scripts. The goal is to develop a lightweight classifier that does not rely on signatures or blacklists to detect never-before-seen malicious scripts.
Ignorance is bliss, but not for MongoDB

The database management system MongoDB is currently being downloaded at an impressive rate: approximately 30 000 times per day. Widely spread, this open source software is today the talk of the town because of a hacking wave that, according to some, was to be expected sooner or later.
bh-usa-07-grossman-WP.pdf

1) The document discusses new hacking techniques that can exploit browsers and access internal corporate networks even when the browser has JavaScript disabled or restricted. These techniques bypass traditional perimeter security measures.
2) One technique uses CSS to steal a user's browsing history without JavaScript. Another obtains the user's internal IP address using a Java applet and then port scans the internal network to find vulnerabilities.
3) The author concludes that a user's browser, when visiting public websites, can potentially be silently hijacked to target and hack resources on the internal corporate network.
Bringing a Cannon to a Knife Fight

The document discusses the "Great Cannon," an offensive cyber weapon used by China to conduct distributed denial-of-service (DDoS) attacks. It summarizes the timeline of the Great Cannon attacks in March-April 2015, which injected malicious JavaScript onto websites to overwhelm targets like GitHub and CloudFront. It then provides background on China's censorship apparatus, known as the "Great Firewall," and possible entities involved in the Great Cannon attacks, including military and intelligence groups. It concludes by considering whether the Great Cannon may be used for more targeted attacks in the future.
Five Reasons Why You Need Cloud Investigation & Response Automation

With more than 60% of corporate data currently stored in the cloud, cloud computing has influenced a true renaissance in how we manage and deliver applications and services. The appeal of migrating to the cloud is clear – greater speed, agility, flexibility, cost savings, and more. However, digital transformation also poses new security challenges -- especially when it comes to forensics and incident response.
This white paper covers five reasons why you need Cloud Investigation and Response Automation to ensure your organization is equipped to efficiently understand and respond to cloud threats.
Developers are there, attackers are there, you need to be there too!
Cloud experts are hard to find
Risk escalates at cloud speed
Multi-cloud is on the rise
Ephemeral means data
disappears in the blink of an eye
Azure Incident Response Cheat Sheet.pdf

This document provides an overview of tools and best practices for incident response in an Azure environment. It summarizes key Azure Active Directory commands for identifying and deactivating compromised user accounts. It also outlines how to identify legacy authentication methods, applications using AD authentication, and snapshots that can be used for forensics. Additional sections cover extracting logs from Azure, restricting administrative access, requiring multi-factor authentication, and enabling logging.
More Related Content
Similar to The great cannon has been deployed again
Cryptojacking - by Vishwaraj101

Cryptojacking involves secretly using a victim's computing resources to mine cryptocurrencies without consent. Attackers can embed cryptojacking scripts on websites through vulnerabilities like cross-site scripting (XSS). When visitors access the infected sites, their browsers' CPUs are used to generate cryptocurrency for the attacker. Other cryptojacking methods include subdomain takeovers, network-level attacks by setting up rogue hotspots, and exploiting remote code execution bugs to install cryptojacking software. Website owners can prevent cryptojacking by fixing security issues, implementing content security policies and HTTPS, and monitoring CPU usage.
JSconf JP - Analysis of an exploited npm package. Event-stream's role in a su...

This document summarizes an analysis of an exploited NPM package called event-stream. It describes how an attacker gained control of the package and added malicious code that was downloaded by thousands of projects whenever their dependencies were updated. The malicious code stole cryptocurrency from wallets containing large amounts. It highlights the risks of supply chain attacks and emphasizes the importance of auditing dependencies, locking versions, and thinking carefully before adding new dependencies to avoid compromising entire projects and their users.
Compromised e commerce_sites_lead_to_web-based_keyloggers

The document discusses a keylogger injection campaign targeting eCommerce sites called "Magecart". It describes how attackers injected JavaScript keylogger code into compromised shopping cart platforms like Magento to steal payment card data. The code captured form fields and sent data to remote attacker sites. The campaign evolved over time from 2016 onward, with attackers refining code and expanding which payment providers were targeted. The document provides examples of keylogger injections on specific compromised sites faber.co.uk and everlast.com.
HallTumserFinalPaper

This document discusses cross-site scripting (XSS) attacks. It begins by defining XSS and explaining that it occurs when an attacker uses a victim's browser to run malicious scripts. There are three main types of XSS attacks: reflected, stored, and DOM-based. The document then discusses the history and evolution of XSS attacks, providing examples over time that increased in scale and sophistication. It covers technical details of how the different XSS attacks work and potential impacts from a professional, social, and ethical perspective. The goal is to raise awareness about XSS vulnerabilities and prevention.
DevOps Automation Principles

The World is full of examples where DevOps Automation principles help in growing and improving companies in every aspect. DevOps isn’t a “thing,” it’s a set of principles which lay the fundamental groundwork of technology, purpose, and people.
STUDY OF DEEP WEB AND A NEW FORM BASED CRAWLING TECHNIQUE

This document describes a study of the deep web and a new form-based crawling technique. It defines the deep web as unindexed web content that can only be accessed by filling out forms. The paper proposes a crawling method that equips web crawlers with appropriate input values to submit forms and retrieve search results. An experiment on people search websites demonstrates the technique, achieving high precision and recall rates in associating forms, domains, and attributes. In conclusion, the form-based crawling approach shows potential for effectively surfacing content from the deep web.
Software management, the seasonal return of DDoS - This Week in Security.pdf

This weekly security summary from F5 discusses several recent cybersecurity events:
- A proof of concept was published for a critical Fortinet vulnerability, leading to mass exploitation attempts.
- Automotive security threats are increasing as vehicles contain more software.
- Over 45,000 VMware ESXi servers reached end of support, leaving them vulnerable.
- A Minecraft server was hit with a record 2.5 terabit DDoS attack launched by the Mirai botnet.
- A pro-Russian group is paying people to participate in DDoS attacks against Western targets.
Chrome Extensions: Masking risks in entertainment

Chorme extensions are plugins for the Chrome web browser that add functionalities to the browsing experience, but can also include risks like information leakage, unauthorized PII access or profiling. Let's see what are some of these applications hiding.
A look at the prevalence of client-side JavaScript vulnerabilities in web app...

A look at the prevalence of client-side JavaScript vulnerabilities in web app...IBM Rational software
The document discusses the results of a research study into the prevalence of client-side JavaScript vulnerabilities in web applications. The study analyzed 675 websites and found that 14% were vulnerable, with 38% of vulnerabilities introduced by third-party JavaScript code. It also found that 94% of vulnerable sites suffered from DOM-based cross-site scripting issues, while only 11% had open redirect issues. The research suggests client-side vulnerabilities are more common than previously believed.Deep and Dark internet Safari, How to hire a hacker? Robbrecht van Amerongen

Deep and Dark internet Safari, How to hire a hacker? Robbrecht van AmerongenGetting value from IoT, Integration and Data Analytics
Deep and Dark internet Safari, How to hire a hacker. Views on how professional cyber crime organizations are. The Digital Demise - by Robin Turner

This document outlines a proposed net art project called "digital demise" that aims to track and document the destruction caused by hackers on a server. The project will monitor hackers' actions on the server, retrieve the data, and use it to dynamically generate graphic content on a separate website. It discusses the technical components, influences, aesthetics, planning, testing, and potential shortcomings of the project.
Case Study: Q2 2014 Global DDoS Attack Report | Akamai Document

The Brobot botnet that devastated banks with DDoS floods in 2013 may be back. And the techniques that built it – exploiting vulnerabilities in the software that powers websites and cloud companies – is all too alive. Get the full details about this cybercrime threat in the Akamai/Prolexic Q1 2014 DDoS attack report, available for a free download at http://bit.ly/1meTkfu
SeanRobertsThesis

The document presents a hierarchical classification of web vulnerabilities organized into two main groups: general vulnerabilities that affect all web servers and service-specific vulnerabilities found in particular web server programs. General vulnerabilities are further divided into three sub-groups: feature abuse involving misuse of legitimate features, unvalidated input where user input is not checked before being processed, and improper design flaws. Validating user input and disabling vulnerable features can help eliminate certain vulnerability types like cross-site scripting resulting from unvalidated input or cross-site tracing from feature abuse. The hierarchy aims to help webmasters understand and address vulnerabilities by grouping similar issues.
A web content analytics

This document proposes a web content analytics architecture to detect malicious JavaScript through real-time analysis of web traffic. It collects HTTP traffic using a proxy server and analyzes web content through static and dynamic analysis. Static analysis includes pattern matching, and dynamic analysis executes scripts to extract API call traces. Traces are clustered and signatures are generated by combining common tokens to detect similar malicious scripts while reducing false positives. The proposed approach analyzes JavaScript obfuscation and HTML5 usage to determine if further dynamic analysis is needed, and refines signatures through comparison to benign scripts. Evaluation showed the refined signatures improved detection rates while reducing false positives.
(In)Security Implication in the JS Universe

JavaScript is the most widely used language cross platforms. This talk will analyze the security concerns from past to present with a peek to the future of this important language. This talk was presented as Keynote at CyberCamp Espana 2014.
JavaScript Supply Chain Security

1) The document discusses software supply chain security and examples of known attacks, including typosquatting, project takeovers, account takeovers, and inserting malware or backdoors into dependencies.
2) It provides details on specific past attacks, such as those on the event-stream, eslint, and electron-native-notify packages, how they were carried out, and their goals.
3) The presentation recommends steps developers can take to help protect their software supply chains, such as carefully managing dependencies, setting up a SECURITY.md file, enabling GitHub security features, and using two-factor authentication.
CS6262_Group9_FinalReport

This document describes a system for classifying JavaScript scripts as malicious or benign using static analysis and machine learning techniques. The system crawls websites, extracts JavaScript scripts, and analyzes them to extract over 20 structural and statistical features. These features are used to train machine learning classifiers like decision trees and SVMs. The top predictive features include the number of long variable/function names, direct string assignments, string modifying functions, and escape functions. Evaluating this approach on a dataset of over 10,000 scripts from blacklisted sites found 12 truly malicious scripts. The goal is to develop a lightweight classifier that does not rely on signatures or blacklists to detect never-before-seen malicious scripts.
Ignorance is bliss, but not for MongoDB

The database management system MongoDB is currently being downloaded at an impressive rate: approximately 30 000 times per day. Widely spread, this open source software is today the talk of the town because of a hacking wave that, according to some, was to be expected sooner or later.
bh-usa-07-grossman-WP.pdf

1) The document discusses new hacking techniques that can exploit browsers and access internal corporate networks even when the browser has JavaScript disabled or restricted. These techniques bypass traditional perimeter security measures.
2) One technique uses CSS to steal a user's browsing history without JavaScript. Another obtains the user's internal IP address using a Java applet and then port scans the internal network to find vulnerabilities.
3) The author concludes that a user's browser, when visiting public websites, can potentially be silently hijacked to target and hack resources on the internal corporate network.
Bringing a Cannon to a Knife Fight

The document discusses the "Great Cannon," an offensive cyber weapon used by China to conduct distributed denial-of-service (DDoS) attacks. It summarizes the timeline of the Great Cannon attacks in March-April 2015, which injected malicious JavaScript onto websites to overwhelm targets like GitHub and CloudFront. It then provides background on China's censorship apparatus, known as the "Great Firewall," and possible entities involved in the Great Cannon attacks, including military and intelligence groups. It concludes by considering whether the Great Cannon may be used for more targeted attacks in the future.
Similar to The great cannon has been deployed again (20)
JSconf JP - Analysis of an exploited npm package. Event-stream's role in a su...

JSconf JP - Analysis of an exploited npm package. Event-stream's role in a su...
Compromised e commerce_sites_lead_to_web-based_keyloggers

Compromised e commerce_sites_lead_to_web-based_keyloggers
STUDY OF DEEP WEB AND A NEW FORM BASED CRAWLING TECHNIQUE

STUDY OF DEEP WEB AND A NEW FORM BASED CRAWLING TECHNIQUE
Software management, the seasonal return of DDoS - This Week in Security.pdf

Software management, the seasonal return of DDoS - This Week in Security.pdf
A look at the prevalence of client-side JavaScript vulnerabilities in web app...

A look at the prevalence of client-side JavaScript vulnerabilities in web app...
Deep and Dark internet Safari, How to hire a hacker? Robbrecht van Amerongen

Deep and Dark internet Safari, How to hire a hacker? Robbrecht van Amerongen
Case Study: Q2 2014 Global DDoS Attack Report | Akamai Document

Case Study: Q2 2014 Global DDoS Attack Report | Akamai Document
More from Christopher Doman
Five Reasons Why You Need Cloud Investigation & Response Automation

With more than 60% of corporate data currently stored in the cloud, cloud computing has influenced a true renaissance in how we manage and deliver applications and services. The appeal of migrating to the cloud is clear – greater speed, agility, flexibility, cost savings, and more. However, digital transformation also poses new security challenges -- especially when it comes to forensics and incident response.
This white paper covers five reasons why you need Cloud Investigation and Response Automation to ensure your organization is equipped to efficiently understand and respond to cloud threats.
Developers are there, attackers are there, you need to be there too!
Cloud experts are hard to find
Risk escalates at cloud speed
Multi-cloud is on the rise
Ephemeral means data
disappears in the blink of an eye
Azure Incident Response Cheat Sheet.pdf

This document provides an overview of tools and best practices for incident response in an Azure environment. It summarizes key Azure Active Directory commands for identifying and deactivating compromised user accounts. It also outlines how to identify legacy authentication methods, applications using AD authentication, and snapshots that can be used for forensics. Additional sections cover extracting logs from Azure, restricting administrative access, requiring multi-factor authentication, and enabling logging.
AWS Incident Response Cheat Sheet.pdf

With the rapid migration to the cloud,
it’s becoming increasingly difficult to keep track
of all of the different data sources, commands,
and tools available from each Cloud Service
Provider (CSP). This cheat sheet was designed
to provide security professionals with an overview
of key best practices, data sources and tools that
they can have at their disposal when responding
to an incident in an AWS environment.
A New Perspective on Resource-Level Cloud Forensics

AWS classifies cloud incidents across three domains: Service, Infrastructure and Application. There has been much previous discussion across the Service and Application domains, see for example the excellent SANS DFIR 2022 Keynote. This talk will focus on the unique challenges and opportunities of responding to incidents in the Infrastructure domain. Cloud Service Providers, such as AWS, GCP and Azure, often introduce artifacts of forensic value when developing features for automation and monitoring of resources. Typically, these artifacts are undocumented and exist purely for the provider's own troubleshooting, but they also provide valuable insight to an investigator analyzing malicious activity on a system. Frequently, this insight surpasses that of “provider-supported” forensic data sources. Most of the discourse around performing forensics in the cloud focuses on provider-level logging. While this is undoubtedly useful, practitioners understand that resource-level forensic analysis is crucial when responding to incidents affecting cloud infrastructure. And much of this knowledge remains opaque and undocumented. In this presentation, Chris Doman, CTO of Cado Security will present novel research of undocumented forensic artifacts from cloud service provider specific operating systems and tools. He will provide the audience with an overview of forensic techniques across cloud compute and serverless environments. He will also discuss native operating system artifacts, contrast them with their cloud equivalents and consider their usefulness in the context of the cloud. Attendees can expect to gain a unique perspective on resource-level cloud forensics and should leave the talk with a host of new data sources and knowledge for performing forensic analysis of cloud resources.
Cloud Forensics Tools

This document lists several cloud forensics tools including Cloud Forensics Utils from Google which is an open source toolkit for analyzing cloud services, Prowler which is an open source tool for security assessment of AWS environments, varc which is a tool from Cado Security for analyzing AWS VPC flow logs, and ThreatResponse which is a cloud-based platform for investigating security incidents and automating response. It also mentions Cado Response which is a commercial platform from Cado Security and an automated forensics orchestrator for Amazon EC2 from AWS.
Cloud Forensics and Incident Response Training.pdf

The document provides an overview of a free training program from Cado Security that covers cloud forensics and incident response fundamentals for AWS, Azure, and GCP, including topics such as digital forensics principles, investigative models, incident response planning, gathering an incident response team, running investigations, and containment and remediation. It also promotes Cado Security's incident response platform for investigating incidents at cloud speed.
AWS Guard Duty Forensics & Incident Response.pdf

"AWS Guard Duty Forensics & Incident Response" provides an overview of the AWS Guard Duty service and its forensic capabilities. AWS Guard Duty is a managed threat detection service that continuously monitors the AWS environment for potential malicious activity. The talk focuses on how Guard Duty can be used for incident response by providing detailed forensic data that can be used to investigate security incidents.
EKS Forensics & Incident Response.pdf

"EKS Forensics & Incident Response" will explore the critical role of Elastic Kubernetes Service (EKS) in incident response and forensic investigations. The presentation will begin by discussing the current threat landscape and the need for organizations to have a well-defined incident response plan in place to mitigate risks effectively.
The speaker will then delve into the various phases of incident response, including preparation, identification, containment, eradication, and recovery. The focus will be on how EKS can be leveraged to perform forensics investigations during the identification phase, with an emphasis on the tools and techniques available for gathering data and analyzing events.
The talk will also cover the unique challenges associated with conducting forensic investigations in a containerized environment and the strategies for overcoming these challenges. Attendees will learn how EKS can facilitate forensic investigations in containerized environments by providing rich telemetry data, monitoring tools, and analysis capabilities.
Finally, the presentation will emphasize the importance of communication and collaboration between security teams and other stakeholders in the organization during an incident. Attendees will leave with a deeper understanding of how EKS can play a vital role in incident response and forensics investigations, and practical strategies for improving their organization's security posture.
AWS IAM Forensics & Incident Response

In today's cloud-based infrastructure, AWS IAM (Identity and Access Management) is one of the most critical components for ensuring security. However, despite the many safeguards in place, IAM-related incidents can occur, ranging from simple misconfigurations to full-blown attacks. In this talk, we will discuss how to perform forensics and incident response for AWS IAM. We will cover the tools and techniques necessary to investigate and identify root causes of IAM incidents. We will also discuss how to mitigate and remediate incidents, as well as how to implement proactive measures to prevent future incidents. By the end of this talk, attendees will have a better understanding of how to effectively handle AWS IAM-related incidents and ensure the security of their AWS environments.
AWS Forensics & Incident Response

Participants will learn how to:
Understand AWS security features and best practices
Conduct forensics investigations in AWS environments
Identify and collect relevant data for investigations
Analyze AWS logs to identify indicators of compromise
Respond to security incidents in AWS
Lambda Forensics & Incident Response.pdf

This talk will focus on the use of AWS Lambda for incident response and forensics. AWS Lambda is a serverless computing service that allows developers to run code without the need for traditional infrastructure. However, this serverless approach can make it challenging to conduct investigations and respond to incidents. In this talk, we will discuss the tools and techniques available for collecting and analyzing data in Lambda environments. We will also cover how to use AWS CloudTrail and AWS Config for real-time threat detection and response. Additionally, we will discuss best practices for securing Lambda functions and preventing incidents from occurring in the first place. Attendees will come away with a solid understanding of how to use Lambda for incident response and forensics and be better equipped to handle security incidents in serverless environments.
Case Studies Denonia - Lambda DFIR.pdf

This talk covers an example of DFIR / responding to an attack in AWS Lambda. It focuses on the malware Denonia.
Cloud Security Fundamentals for Forensics and Incident Response.pdf

As organizations continue to adopt cloud-based infrastructures, the need for effective cloud security measures has become increasingly important. In this talk, we will discuss the fundamentals of cloud security as it pertains to forensics and incident response. We will cover topics such as cloud service models, shared responsibility models, and the various security controls available within cloud environments. We will also discuss common cloud security incidents and how to perform effective incident response and forensics in the cloud. Attendees will leave with a better understanding of how to secure their cloud environments and effectively respond to incidents when they occur.
AWS Detective Forensics & Incident Response.pdf

The AWS Detective Forensics & Incident Response talk will focus on the benefits of using AWS Detective for forensic analysis and incident response. The talk will provide an overview of AWS Detective and its capabilities, including how it can help investigate security incidents and provide visual representations of the investigation results. The talk will also cover key considerations and best practices for implementing effective incident response processes using AWS Detective, such as setting up AWS Detective and integrating it with other AWS services. Additionally, the talk will delve into the importance of forensic analysis in identifying the root cause of security incidents and how AWS Detective can help perform effective forensic investigations. The talk will also include examples of how AWS Detective has been used to detect and remediate security incidents in real-world scenarios, and best practices for using AWS Detective to improve overall security posture.
Google Cloud Forensics & Incident Response

Google Cloud Platform (GCP) provides a variety of services that enable businesses to manage their computing resources in the cloud. However, as with any cloud platform, incidents and cyberattacks can occur, which can compromise the security and privacy of data.
In this talk, we will discuss the process of conducting forensics and incident response investigations on the GCP. We will begin by providing an overview of the GCP security model and the tools available for monitoring and managing security incidents.
We will then dive into the different types of incidents that can occur on the GCP, such as data breaches, unauthorized access, and malware infections. We will cover how to identify these incidents and gather the necessary information for forensic investigation.
Next, we will discuss the forensic investigation process for the GCP. We will cover topics such as evidence collection and preservation, analysis of logs and network traffic, and identification of the root cause of the incident.
Finally, we will discuss best practices for incident response on the GCP, including how to contain and mitigate the impact of an incident, and how to communicate the incident to stakeholders.
GKE Forensics & Incident Response.pdf

This document discusses Google Kubernetes Engine (GKE) forensics and incident response. It provides a link to the GKE documentation on cluster architecture and mentions Cado Security's incident response platform, which offers a free 14-day trial to access unlimited use of their response tools.
AWS SSM Forensics and Incident Response

The document discusses AWS SSM forensics and incident response. It provides three links about AWS SSM logging - one detailing what logging is available in the AWS SSM console, another describing what SSM logs are stored on disk, and a third promoting a 14-day free trial of the Cado Response Platform for incident investigation.
Kubernetes Docker Forensics & Incident Response.pdf

The talk "Kubernetes and Docker Forensics & Incident Response" will focus on the Digital Forensics and Incident Response (DFIR) investigation of containerized environments using Kubernetes and Docker. With the increasing adoption of containerization technologies, it is crucial for organizations to have a robust security strategy in place to handle security incidents.
This talk will cover the key concepts of containerization technologies such as Docker and Kubernetes, and their security implications. We will discuss the forensic techniques and methodologies that can be used to identify the root cause of security incidents in these environments, including container forensics, network traffic analysis, and memory forensics.
The talk will also provide insights into the challenges and limitations of conducting a DFIR investigation in a containerized environment, such as the ephemeral nature of containers and the need for specialized tooling.
Attendees will learn about the best practices for implementing logging and monitoring in Docker and Kubernetes environments, as well as the importance of having a well-defined incident response plan for containerized environments.
Overall, this talk will provide valuable insights into the DFIR investigation of containerized environments using Kubernetes and Docker, and how organizations can better prepare themselves to respond to security incidents in these environments.
Case Studies TeamTNT - AWS & Container Cryptomining Worm DFIR.pdf

The talk "Case Studies TeamTNT - AWS & Container Cryptomining Worm DFIR" goes into the incident response investigation into a container cryptomining worm attack perpetrated by the hacking group TeamTNT. The presentation will focus on the use of AWS and container technology in the attack and how these tools were leveraged in the investigation. Attendees will learn about the tools and techniques used to identify and contain the attack, as well as lessons learned from the incident response. The presentation will cover the importance of monitoring container environments for security threats and implementing best practices for AWS security. Additionally the talk will highlight the use of machine learning and automation in the incident response process. By the end of the presentation, attendees will gain a better understanding of the challenges and opportunities of conducting DFIR investigations in cloud environments and with container technology.
EC2 Forensics & Incident Response.pdf

"EC2 Forensics & Incident Response" will focus on the crucial role of Elastic Compute Cloud (EC2) in incident response and forensics investigations. The presentation will begin by discussing the current threat landscape and the need for organizations to have a robust incident response plan in place to effectively mitigate security risks.
The speaker will then outline the various phases of incident response, including preparation, identification, containment, eradication, and recovery. The talk will emphasize how EC2 can be leveraged to perform forensics investigations during the identification phase, with a focus on the tools and techniques available for collecting data and analyzing events.
The presentation will also cover the unique challenges associated with conducting forensic investigations in the EC2 environment and the strategies for overcoming these challenges. Attendees will learn how to use EC2 monitoring and analysis tools to collect and preserve evidence during investigations.
More from Christopher Doman (20)
Five Reasons Why You Need Cloud Investigation & Response Automation

Five Reasons Why You Need Cloud Investigation & Response Automation
A New Perspective on Resource-Level Cloud Forensics

A New Perspective on Resource-Level Cloud Forensics
Cloud Forensics and Incident Response Training.pdf

Cloud Forensics and Incident Response Training.pdf
Cloud Security Fundamentals for Forensics and Incident Response.pdf

Cloud Security Fundamentals for Forensics and Incident Response.pdf
Kubernetes Docker Forensics & Incident Response.pdf

Kubernetes Docker Forensics & Incident Response.pdf
Case Studies TeamTNT - AWS & Container Cryptomining Worm DFIR.pdf

Case Studies TeamTNT - AWS & Container Cryptomining Worm DFIR.pdf
Recently uploaded
学位认证网(DU毕业证)迪肯大学毕业证成绩单一比一原版制作

24小时办理【微信176555708】【毕业证明信-推荐信做学费单】成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,留信网认证。网上存档永久可查!
degree,Transcripts(一对一服务包括毕业院长签字,专业课程,学位类型,专业或教育领域,以及毕业日期.不要忽视这些细节.这两份文件同样重要!毕业证成绩单文凭留信网学历认证!)如果您是以下情况,我们都能竭诚为您解决实际问题:【公司采用定金+余款的付款流程,以最大化保障您的利益,让您放心无忧】
1、在校期间,因各种原因未能顺利毕业,拿不到官方迪肯大学毕业证+微信176555708;
2、面对父母的压力,希望尽快拿到;
3、不清楚流程以及材料该如何准备;
4、回国时间很长,忘记办理毕业证丢失 学历认证《迪肯大学毕业证》微信176555708《DU学位证书购买》
学位证书验证;
5、回国马上就要找工作,办给用人单位看;
6、企事业单位必须要求办理学历证书 英文《迪肯大学毕业证》微信176555708《DU学位证书购买》
本科毕业证书扫描件的;
微信176555708面向迪肯大学毕业留学生提供以下服务:
【★迪肯大学毕业证、成绩单等全套材料,从防伪到印刷,从水印到钢印烫金,与学校100%相同】
【★大学学历 硕士学位《迪肯大学毕业证》微信176555708《DU学位证书购买》
硕士毕业证】
【★毕业证书范本】
【★真实留信认证,留信网入库存档,可查】
主营项目:
a.办理海外毕业证认证《迪肯大学毕业证》微信176555708《DU学位证书购买》
学位证书英文版,改成绩单,Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
b.真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
c.真实教育部国外学历学位认证,教育部存档,教育部留服网站100%可查.
d.留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
e.招聘中介代理:本公司诚聘各地代理人员以及留学生,如果你有业余时间,有兴趣就请联系我们,我们会给到您的回报!期待您的加盟:一朝办理,终身受益(本信息长期有效)互惠互利,为广大海内外学子及有需要的人士在事业上跨过这道门槛!
【业务选择办理准则】
1.如果您只是为了的应付父母亲戚朋友看下迪肯大学毕业证,那么办理一份学位即可
2.如果您是为了回国找工作,只是进私营企业或者外企,那么办理一份多大学历认证有时间限制吗《迪肯大学毕业证》微信176555708《DU学位证书购买》
毕业证丢失补办即可,因为私营企业或者外企是不能查询学位真假的!
3.如果您是要进国企银行事业单位考公务员等就需办理真实学历认证!
诚招代理:本公司诚聘当地合作代理人员,如果你有业余时间,有兴趣就请联系我们。
重新申请毕业证书(RMIT毕业证)皇家墨尔本理工大学毕业证成绩单精仿办理

不能毕业办理【RMIT毕业证【微信176555708】皇家墨尔本理工大学文凭学历】【微信176555708】【皇家墨尔本理工大学文凭学历证书】【皇家墨尔本理工大学毕业证书与成绩单样本图片】毕业证书补办 Fake Degree做学费单【毕业证明信-推荐信】成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,留信网认证。网上存档永久可查!全套服务:皇家墨尔本理工大学皇家墨尔本理工大学本科学位证成绩单真实回国人员证明 #真实教育部认证。让您回国发展信心十足#铸就十年品质!信誉!实体公司!可以视频看办公环境样板如需办理真实可查可以先到公司面谈勿轻信小中介黑作坊!
可以提供皇家墨尔本理工大学钢印 #水印 #烫金 #激光防伪 #凹凸版 #最新版的毕业证 #百分之百让您绝对满意
印刷DHL快递毕业证 #成绩单7个工作日真实大使馆教育部认证1个月。为了达到高水准高效率
请您先以qq或微信的方式对我们的服务进行了解后如果有皇家墨尔本理工大学皇家墨尔本理工大学本科学位证成绩单帮助再进行电话咨询。
国外毕业证学位证成绩单如何办理:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作皇家墨尔本理工大学毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
制作毕业证书(ANU毕业证)莫纳什大学毕业证成绩单官方原版办理

在线办理莫纳什大学毕业证【微信:176555708】(ANU毕业证书)成绩单学位证【微信:176555708】,留信认证(真实可查,永久存档)纸张工艺/offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。#一整套莫纳什大学文凭证件办理#—包含莫纳什大学莫纳什大学毕业证文凭证书学历认证|使馆认证|归国人员证明|教育部认证|留信网认证永远存档教育部学历学位认证查询办理国外文凭国外学历学位认证#我们提供全套办理服务。
一整套留学文凭证件服务:
一:莫纳什大学莫纳什大学毕业证文凭证书毕业证 #成绩单等全套材料从防伪到印刷水印底纹到钢印烫金
二:真实使馆认证(留学人员回国证明)使馆存档
三:真实教育部认证教育部存档教育部留服网站永久可查
四:留信认证留学生信息网站永久可查
国外毕业证学位证成绩单办理方法:
1客户提供办理莫纳什大学莫纳什大学毕业证文凭证书信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
教育部文凭学历认证认证的用途:
如果您计划在国内发展那么办理国内教育部认证是必不可少的。事业性用人单位如银行国企公务员在您应聘时都会需要您提供这个认证。其他私营 #外企企业无需提供!办理教育部认证所需资料众多且烦琐所有材料您都必须提供原件我们凭借丰富的经验帮您快速整合材料让您少走弯路。
实体公司专业为您服务如有需要请联系我: 微信176555708
Search Result Showing My Post is Now Buried

Search results burying my post that used to rank before Google's March 2024 algorithm update.
国外证书(Lincoln毕业证)新西兰林肯大学毕业证成绩单不能毕业办理

退学办理新西兰林肯大学毕业证【微信176555708】学历认证怎么做:原版仿制新西兰林肯大学电子版成绩单毕业证认证【新西兰林肯大学毕业证成绩单】、新西兰林肯大学文凭证书成绩单复刻offer录取通知书、购买Lincoln圣力嘉学院本科毕业证、【新西兰林肯大学毕业证办理Lincoln毕业证书哪里买】、新西兰林肯大学 Offer在线办理Lincoln Offer新西兰林肯大学Bachloer Degree。1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:微信176555708我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
7完成交易删除客户资料
高精端提供以下服务:
一:新西兰林肯大学新西兰林肯大学毕业证文凭证书全套材料从防伪到印刷水印底纹到钢印烫金
二:真实使馆认证(留学人员回国证明)使馆存档
三:真实教育部认证教育部存档教育部留服网站可查
四:留信认证留学生信息网站可查
五:与学校颁发的相关证件1:1纸质尺寸制定(定期向各大院校毕业生购买最新版本毕,业证成绩单保证您拿到的是鲁昂大学内部最新版本毕业证成绩单微信176555708)
A.为什么留学生需要操作留信认证?
留信认证全称全国留学生信息服务网认证,隶属于北京中科院。①留信认证门槛条件更低,费用更美丽,并且包过,完单周期短,效率高②留信认证虽然不能去国企,但是一般的公司都没有问题,因为国内很多公司连基本的留学生学历认证都不了解。这对于留学生来说,这就比自己光拿一个证书更有说服力,因为留学学历可以在留信网站上进行查询!
B.为什么我们提供的毕业证成绩单具有使用价值?
查询留服认证是国内鉴别留学生海外学历的唯一途径但认证只是个体行为不是所有留学生都操作所以没有办理认证的留学生的学历在国内也是查询不到的他们也仅仅只有一张文凭。所以这时候我们提供的和学校颁发的一模一样的毕业证成绩单就有了使用价值。
Explore-Insanony: Watch Instagram Stories Secretly

Instagram has become one of the most popular social media platforms, allowing people to share photos, videos, and stories with their followers. Sometimes, though, you might want to view someone's story without them knowing.
Ready to Unlock the Power of Blockchain!

Imagine a world where data flows freely, yet remains secure. A world where trust is built into the fabric of every transaction. This is the promise of blockchain, a revolutionary technology poised to reshape our digital landscape.
Toptal Tech is at the forefront of this innovation, connecting you with the brightest minds in blockchain development. Together, we can unlock the potential of this transformative technology, building a future of transparency, security, and endless possibilities.
Discover the benefits of outsourcing SEO to India

"Discover the benefits of outsourcing SEO to India! From cost-effective services and expert professionals to round-the-clock work advantages, learn how your business can achieve digital success with Indian SEO solutions.
留学学历(UoA毕业证)奥克兰大学毕业证成绩单官方原版办理

制做办理奥克兰大学学历证书<176555708微信>【毕业证明信-推荐信做学费单>【微信176555708】【制作UoA毕业证文凭认证奥克兰大学毕业证成绩单购买】【UoA毕业证书】{奥克兰大学文凭购买}】成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,>【制作UoA毕业证文凭认证奥克兰大学毕业证成绩单购买】【UoA毕业证书】{奥克兰大学文凭购买}留信网认证。
奥克兰大学学历证书<微信176555708(一对一服务包括毕业院长签字,专业课程,学位类型,专业或教育领域,以及毕业日期.不要忽视这些细节.这两份文件同样重要!毕业证成绩单文凭留信网学历认证!)[留学文凭学历认证(留信认证使馆认证)奥克兰大学毕业证成绩单毕业证证书大学Offer请假条成绩单语言证书国际回国人员证明高仿教育部认证申请学校等一切高仿或者真实可查认证服务。
多年留学服务公司,拥有海外样板无数能完美1:1还原海外各国大学degreeDiplomaTranscripts等毕业材料。海外大学毕业材料都有哪些工艺呢?工艺难度主要由:烫金.钢印.底纹.水印.防伪光标.热敏防伪等等组成。而且我们每天都在更新海外文凭的样板以求所有同学都能享受到完美的品质服务。
国外毕业证学位证成绩单办理方法:
1客户提供办理奥克兰大学奥克兰大学硕士毕业证成绩单信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
— — — — 我们是挂科和未毕业同学们的福音我们是实体公司精益求精的工艺! — — — -
一真实留信认证的作用(私企外企荣誉的见证):
1:该专业认证可证明留学生真实留学身份同时对留学生所学专业等级给予评定。
2:国家专业人才认证中心颁发入库证书这个入网证书并且可以归档到地方。
3:凡是获得留信网入网的信息将会逐步更新到个人身份内将在公安部网内查询个人身份证信息后同步读取人才网入库信息。
4:个人职称评审加20分个人信誉贷款加10分。
5:在国家人才网主办的全国网络招聘大会中纳入资料供国家500强等高端企业选择人才。
Should Repositories Participate in the Fediverse?

Presentation for OR2024 making the case that repositories could play a part in the "fediverse" of distributed social applications
制作原版1:1(Monash毕业证)莫纳什大学毕业证成绩单办理假

退学买莫纳什大学毕业证>【微信176555708】办理莫纳什大学毕业证成绩单【微信176555708】Monash毕业证成绩单Monash学历证书Monash文凭【Monash毕业套号文凭网认证莫纳什大学毕业证成绩单】【哪里买莫纳什大学毕业证文凭Monash成绩学校快递邮寄信封】【开版莫纳什大学文凭】Monash留信认证本科硕士学历认证1:1完美还原海外各大学毕业材料上的工艺:水印阴影底纹钢印LOGO烫金烫银LOGO烫金烫银复合重叠。文字图案浮雕激光镭射紫外荧光温感复印防伪。
可办理以下真实莫纳什大学存档留学生信息存档认证:
1莫纳什大学真实留信网认证(网上可查永久存档无风险百分百成功入库);
2真实教育部认证(留服)等一切高仿或者真实可查认证服务(暂时不可办理);
3购买英美真实学籍(不用正常就读直接出学历);
4英美一年硕士保毕业证项目(保录取学校挂名不用正常就读保毕业)
留学本科/硕士毕业证书成绩单制作流程:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询莫纳什大学莫纳什大学毕业证offer);
2开始安排制作莫纳什大学毕业证成绩单电子图;
3莫纳什大学毕业证成绩单电子版做好以后发送给您确认;
4莫纳什大学毕业证成绩单电子版您确认信息无误之后安排制作成品;
5莫纳什大学成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
— — — — — — — — — — — 《文凭顾问微信:176555708》
Gen Z and the marketplaces - let's translate their needs

The product workshop focused on exploring the requirements of Generation Z in relation to marketplace dynamics. We delved into their specific needs, examined the specifics in their shopping preferences, and analyzed their preferred methods for accessing information and making purchases within a marketplace. Through the study of real-life cases , we tried to gain valuable insights into enhancing the marketplace experience for Generation Z.
The workshop was held on the DMA Conference in Vienna June 2024.
办理毕业证(UPenn毕业证)宾夕法尼亚大学毕业证成绩单快速办理

官方原版办理宾夕法尼亚大学毕业证【微信176555708】学历认证怎么做:原版仿制宾夕法尼亚大学电子版成绩单毕业证认证【宾夕法尼亚大学毕业证成绩单】、宾夕法尼亚大学文凭证书成绩单复刻offer录取通知书、购买UPenn圣力嘉学院本科毕业证、【宾夕法尼亚大学毕业证办理UPenn毕业证书哪里买】、宾夕法尼亚大学 Offer在线办理UPenn Offer宾夕法尼亚大学Bachloer Degree。(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
学历顾问:微信:176555708
成绩单ps(UST毕业证)圣托马斯大学毕业证成绩单快速办理

一比一原版制作UST毕业证【微信176555708】圣托马斯大学毕业证书原版↑制作圣托马斯大学学历认证文凭办理圣托马斯大学留信网认证,留学回国办理毕业证成绩单文凭学历认证【微信176555708】专业为海外学子办理毕业证成绩单、文凭制作,学历仿制,回国人员证明、做文凭,研究生、本科、硕士学历认证、留信认证、结业证、学位证书样本、美国教育部认证百分百真实存档可查】(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
学历顾问:微信:176555708
Understanding User Behavior with Google Analytics.pdf

Unlocking the full potential of Google Analytics is crucial for understanding and optimizing your website’s performance. This guide dives deep into the essential aspects of Google Analytics, from analyzing traffic sources to understanding user demographics and tracking user engagement.
Traffic Sources Analysis:
Discover where your website traffic originates. By examining the Acquisition section, you can identify whether visitors come from organic search, paid campaigns, direct visits, social media, or referral links. This knowledge helps in refining marketing strategies and optimizing resource allocation.
User Demographics Insights:
Gain a comprehensive view of your audience by exploring demographic data in the Audience section. Understand age, gender, and interests to tailor your marketing strategies effectively. Leverage this information to create personalized content and improve user engagement and conversion rates.
Tracking User Engagement:
Learn how to measure user interaction with your site through key metrics like bounce rate, average session duration, and pages per session. Enhance user experience by analyzing engagement metrics and implementing strategies to keep visitors engaged.
Conversion Rate Optimization:
Understand the importance of conversion rates and how to track them using Google Analytics. Set up Goals, analyze conversion funnels, segment your audience, and employ A/B testing to optimize your website for higher conversions. Utilize ecommerce tracking and multi-channel funnels for a detailed view of your sales performance and marketing channel contributions.
Custom Reports and Dashboards:
Create custom reports and dashboards to visualize and interpret data relevant to your business goals. Use advanced filters, segments, and visualization options to gain deeper insights. Incorporate custom dimensions and metrics for tailored data analysis. Integrate external data sources to enrich your analytics and make well-informed decisions.
This guide is designed to help you harness the power of Google Analytics for making data-driven decisions that enhance website performance and achieve your digital marketing objectives. Whether you are looking to improve SEO, refine your social media strategy, or boost conversion rates, understanding and utilizing Google Analytics is essential for your success.
办理新西兰奥克兰大学毕业证学位证书范本原版一模一样

原版一模一样【微信:741003700 】【新西兰奥克兰大学毕业证学位证书】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留学挂科(UofM毕业证)明尼苏达大学毕业证成绩单复刻办理

精仿办理明尼苏达大学学历证书<176555708微信>【毕业证明信-推荐信做学费单>【微信176555708】【制作UofM毕业证文凭认证明尼苏达大学毕业证成绩单购买】【UofM毕业证书】{明尼苏达大学文凭购买}】成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,>【制作UofM毕业证文凭认证明尼苏达大学毕业证成绩单购买】【UofM毕业证书】{明尼苏达大学文凭购买}留信网认证。
明尼苏达大学学历证书<微信176555708(一对一服务包括毕业院长签字,专业课程,学位类型,专业或教育领域,以及毕业日期.不要忽视这些细节.这两份文件同样重要!毕业证成绩单文凭留信网学历认证!)(留信学历认证永久存档查询)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
◆◆◆◆◆ — — — — — — — — 【留学教育】留学归国服务中心 — — — — — -◆◆◆◆◆
【主营项目】
一.毕业证【微信:176555708】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【微信:176555708】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分→ 【关于价格问题(保证一手价格)
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
选择实体注册公司办理,更放心,更安全!我们的承诺:可来公司面谈,可签订合同,会陪同客户一起到教育部认证窗口递交认证材料,客户在教育部官方认证查询网站查询到认证通过结果后付款,不成功不收费!
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
学历顾问:微信:176555708
Recently uploaded (20)
Explore-Insanony: Watch Instagram Stories Secretly

Explore-Insanony: Watch Instagram Stories Secretly
Gen Z and the marketplaces - let's translate their needs

Gen Z and the marketplaces - let's translate their needs
Understanding User Behavior with Google Analytics.pdf

Understanding User Behavior with Google Analytics.pdf
The great cannon has been deployed again
- 1. The “Great Cannon” Has Been Deployed Again Summary The Great Cannon is a distributed denial of service tool (“DDoS”) that operates by injecting malicious Javascript into pages served from behind the Great Firewall. These scripts, potentially served to millions of users across the internet, hijack the users’ internet connection to make multiple requests against the targeted site. These requests consume all the resources of the targeted site, making it unavailable: Figure 1: Simplified diagram of how the Great Cannon operates The Great Cannon was the subject of intense research after it was used to disrupt access to the website Github.com in 2015. Little has been seen of the Great Cannon since 2015, however we’ve recently observed new attacks, which are detailed below. Most Recent Attacks against LIHKG The Great Cannon is currently attempting to take the website LIHKG offline. LIHKG has been used to organise protests in Hong Kong. Using a simple script that uses data from UrlScan.io, we identified new attacks likely starting Monday November 25th, 2019. Websites are indirectly serving a malicious javascript file from either: ● http://push.zhanzhang.baidu.com/push.js; or
- 2. ● http://js.passport.qihucdn.com/11.0.1.js Normally these URLs serve standard analytics tracking scripts. However, for a certain percentage of requests the Great Cannon swaps these on the fly with malicious code: Figure 2: Malicious code served from the Great Cannon The code attempts to repeatedly request the following resources through an image proxy on the LIHKG website (at https://i.lih.kg/540/ ) in order to overwhelm the LIHKG website and prevent it from being accessible: ● https://66.media.tumblr.com/e06eda7617fb1b98cbaca0edf9a427a8/tumblr_oqrv3wHXoz1sehac7o1 _540.gif ● https://live.staticflickr.com/65535/48978420208_76b67bec15_o.gif ● https://i.loli.net/2019/09/29/hXHglbYpykUGIJu.gif ● https://na.cx/i/XibbJAS.gif ● https://na.cx/i/UHr3Dtk.gif ● https://na.cx/i/9hjf7rg.gif ● https://na.cx/i/qKE4P2C.gif ● https://na.cx/i/0Dp4P29.gif ● https://na.cx/i/mUkDptW.gif ● https://na.cx/i/ekL74Sn.gif ● https://i.ibb.co/ZBDcP9K/LcSzXUb.gif ● https://na.cx/i/6hxp6x9.gif ● https://img.eservice-hk.net/upload/2018/08/09/181951_60e1e9bedea42535801bc785b6f48e7a.g if ● https://na.cx/i/E3sYryo.gif ● https://na.cx/i/ZbShS2F.gif ● https://na.cx/i/LBppBac.gif ● http://i.imgur.com/5qrZMPn.gif ● https://na.cx/i/J3q35jw.gif ● https://na.cx/i/QR7JjSJ.gif ● https://na.cx/i/haUzqxN.gif ● https://na.cx/i/3hS5xcW.gif ● https://na.cx/i/z340DGp.gif ● https://luna.komica.org/23/src/1573785127351.gif ● https://image.ibb.co/m10EAH/Atsps_Smd_Pc.gif ● https://img.eservice-hk.net/upload/2018/06/02/213756_d33e27ec27b054afcc911be1411b5e5a.g if ● https://media.giphy.com/media/9LZTc9dQjAAL5jmuCK/giphy.gif ● https://img.eservice-hk.net/upload/2018/06/13/171314_55de6aac9af0e3c086b83bf433493004.g if
- 3. These may seem like an odd selection of websites and memes to target, however these meme images appear on the LIHKG forums so the traffic is likely intended to blend in with normal traffic. The URLs are appended to the LIHKG image proxy url (eg; https://na.cx/i/6hxp6x9.gif becomes https://i.lih.kg/540/https://na.cx/i/6hxp6x9.gif?t=6009966493) which causes LIHKG to perform the bandwidth and computationally expensive task of taking a remote image, changing it’s size, then serving it to the user. Impact It is unlikely these sites will be seriously impacted. This is partly due to LIHKG sitting behind the anti-DDoS service Cloudflare, and partly due to some bugs in the malicious Javascript code. We won’t discuss the bugs here as it would provide suggestions on how to improve the attack. Still, it is disturbing to see an attack tool with the potential power of the Great Cannon in use more regularly, and again causing collateral damage to US based file-hosting services. Mitigations These attacks would not be successful if the following resources were served over HTTPS instead of HTTP: ● http://push.zhanzhang.baidu.com/push.js ● http://js.passport.qihucdn.com/11.0.1.js You may want to consider blocking these URLs when not sent over HTTPS. Timeline of Historical Great Cannon Incidents Below we have described previous Great Cannon attacks, including previous attacks against LIHKG in September 2019. 2015: GreatFire and GitHub During the 2015 attacks, DDoS scripts were sent in response to requests sent to a number of domains, for both Javascript and HTML pages served over HTTP from behind the Great Firewall. A number of distinct stages and targets were identified: ● March 3 to March 6, 2015: Initial, limited test firing of the Great Cannon starts. ● March 10: Real attacks start against a Chinese-language news site (Sinasjs.cn). ● March 13: New attacks against an organisation that monitors censorship (GreatFire.org).
- 4. Figure 3: Snippet of the code used in early Great Cannon attacks. Later scripts were improved to not require external javascript libraries. ● March 25: Attacks against GitHub.com start, targeting content hosted from the site GreatFire.org and a Chinese edition of the New York Times. This resulted in a global outage of the GitHub service. Figure 4: The URLs targeted in the attack against Github.com. ● March 26th - Attacks began using code hidden with the Javascript obfuscator “packer”:
- 5. Figure 5: Snippet of the obfuscated code. Current attacks continue to use the same obfuscation. Research by CitizenLab identified multiple likely points where the malicious code is injected. The Great Cannon operated probabilistically, injecting return packets to a certain percentage of requests for Javascript from certain IP addresses. As noted by commentators at the time, the same functionality could also be used to insert exploitation code to enable “Man-on-the-side” attacks to compromise key targets. 2017 and Onward: Attacks against Mingjingnews In August 2017, Great Cannon attacks against a Chinese-language news website (Mingjingnews.com) were identified by a user on Stack Overflow. The code in the 2017 attack is significantly re-written and is largely unchanged in the attacks were seen in 2019. Figure 6: An excerpt of the code to target Mingjingnews.com in 2017.
- 6. We have continued to see attacks against Mingjingnews in the last year. 2019: Attacks Against Hong Kong Democracy Movement On August 31, 2019, the Great Cannon initiated an attack against a website (lihkg.com) used by members of the Hong Kong democracy movement to plan protests. The Javascript code is very similar to the packed code used in the attacks against Mingjingnews observed in 2017 and onward, and the code was served from at least two locations: - http://push.zhanzhang.baidu.com/push.js - http://js.passport.qihucdn.com/11.0.1.js Initial versions targeted a single page on lihkg.com. Figure 7: The Javascript code originally targeting lihkg.com. Later versions targeted multiple pages and attempted (unsuccessfully) to bypass Cloudflare DDoS mitigations that the website owners had implemented. Figure 8: The Javascript code later targeting lihkg.com.
- 7. Detection We detect the Great Cannon serving malicious Javascript with the following Suricata rules from Alien Labs and Emerging Threats Open. alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"AV INFO JS File associated with Great Cannon DDoS"; flow:to_server,established; content:"GET"; http_method; content:"push.js"; http_uri; content:"push.zhanzhang.baidu.com"; http_host; flowbits:set,AVCannonDDOS; flowbits:noalert; classtype:misc-activity; sid:xxx; rev:1;) alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"AV INFO JS File associated with Great Cannon DDoS"; flow:to_server,established; content:"GET"; http_method; content:"11.0.1.js"; http_uri; content:"js.passport.qihucdn.com"; http_host; flowbits:set,AVCannonDDOS; flowbits:noalert; classtype:misc-activity; sid:xxx; rev:1;) alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"AV INFO Potential DDoS attempt related to Great Cannon Attacks"; flow:established,to_client; content:"200"; http_stat_code; file_data; content:"isImgComplete"; flowbits:isset,AVCannonDDOS; reference:url,otx.alienvault.com/pulse/5d6d4da02ee2b6fbff703067; classtype:policy-violation; sid:xxx; rev:1;) alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"AV INFO JS File associated with Great Cannon DDoS"; flow:to_server,established; content:"GET"; http_method; content:"hm.js"; http_uri; content:"hm.baidu.com"; http_host; flowbits:set,AVCannonDDOS; flowbits:noalert; classtype:misc-activity; sid:xxx; rev:1;) alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"AV MALWARE GreatCannon Malicous JScript Inbound"; flow:established,to_client; content:"200"; http_stat_code; file_data; content:"!function(n){"; depth:1000; content:"1e9*n[a][s](9*n[a][g]())+n[a][s](999999999*n[a][g]())"; distance:0; content:"n[y]=3e5,n[_]=1482184792,n[p]=1e6"; distance:0; reference:url,otx.alienvault.com/pulse/5d6d4da02ee2b6fbff703067; classtype:trojan-activity; sid:xxx; rev:1;) ET WEB_CLIENT Great Cannon DDoS JS M1 sid:2027961 ET WEB_CLIENT Great Cannon DDoS JS M2 sid:2027962 ET WEB_CLIENT Great Cannon DDoS JS M3 sid:2027963 ET WEB_CLIENT Great Cannon DDoS JS M4 sid:2027964 Additional indicators and code samples are available in the Open Threat Exchange pulse.
