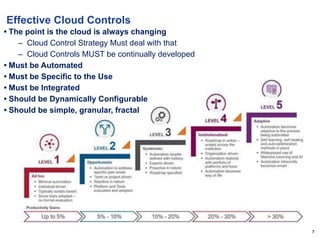
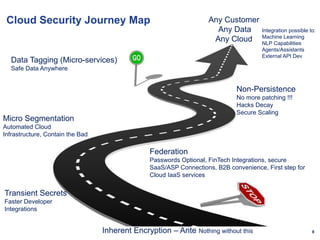
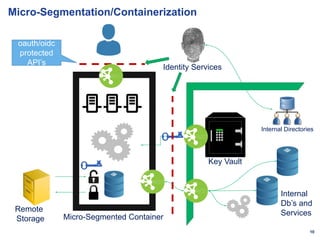
The document discusses cloud security and controls. It notes that cloud infrastructure is constantly changing so cloud security controls must also be continually developed and automated. Effective cloud controls are specific to their use, integrated, dynamically configurable, simple, granular and fractal. Micro-segmentation, inherent encryption, transient secrets, federation, non-persistence and data tagging are important cloud security concepts. Governance in the cloud becomes developing secure patterns and automating them in developer pipelines.