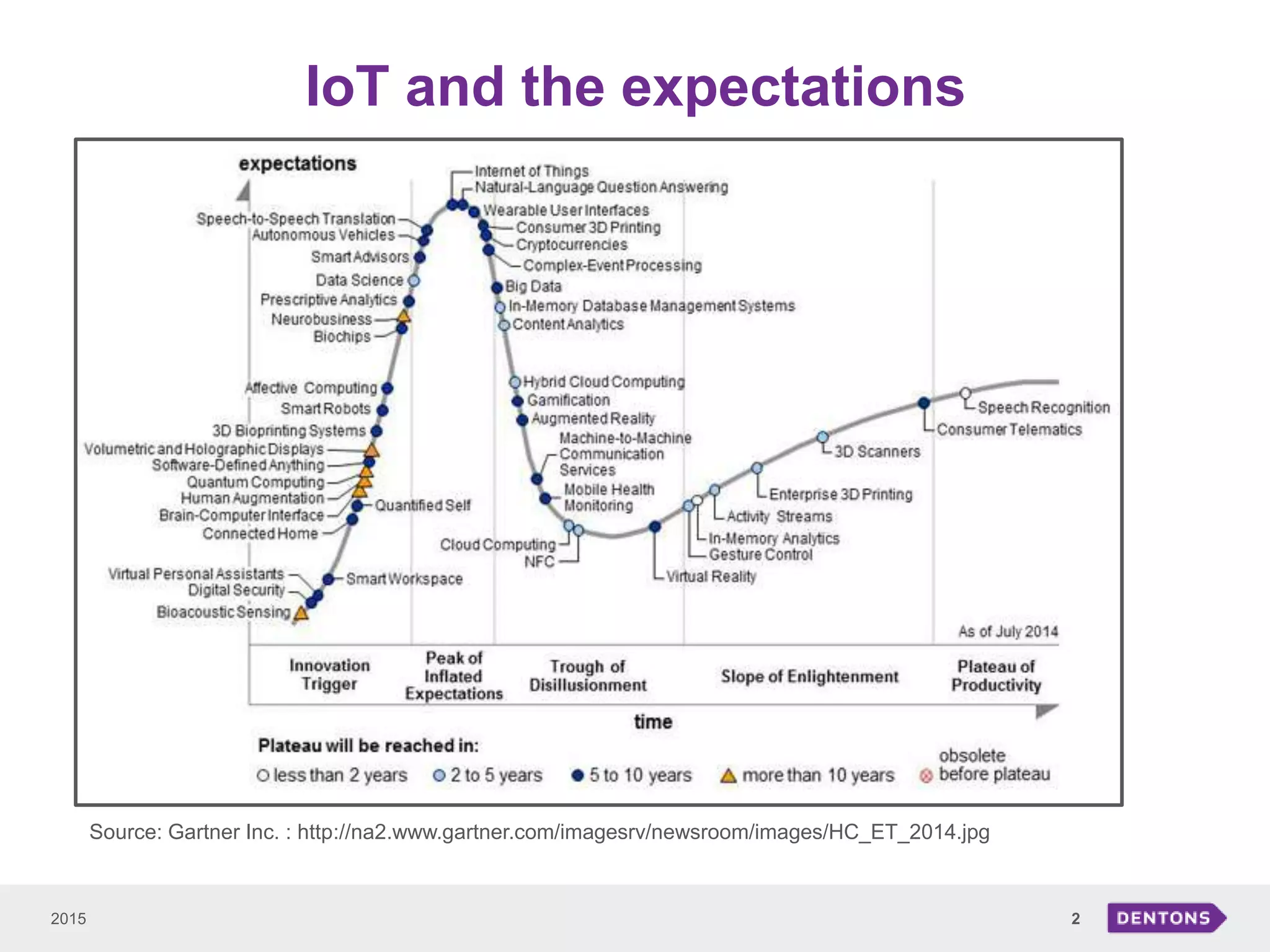
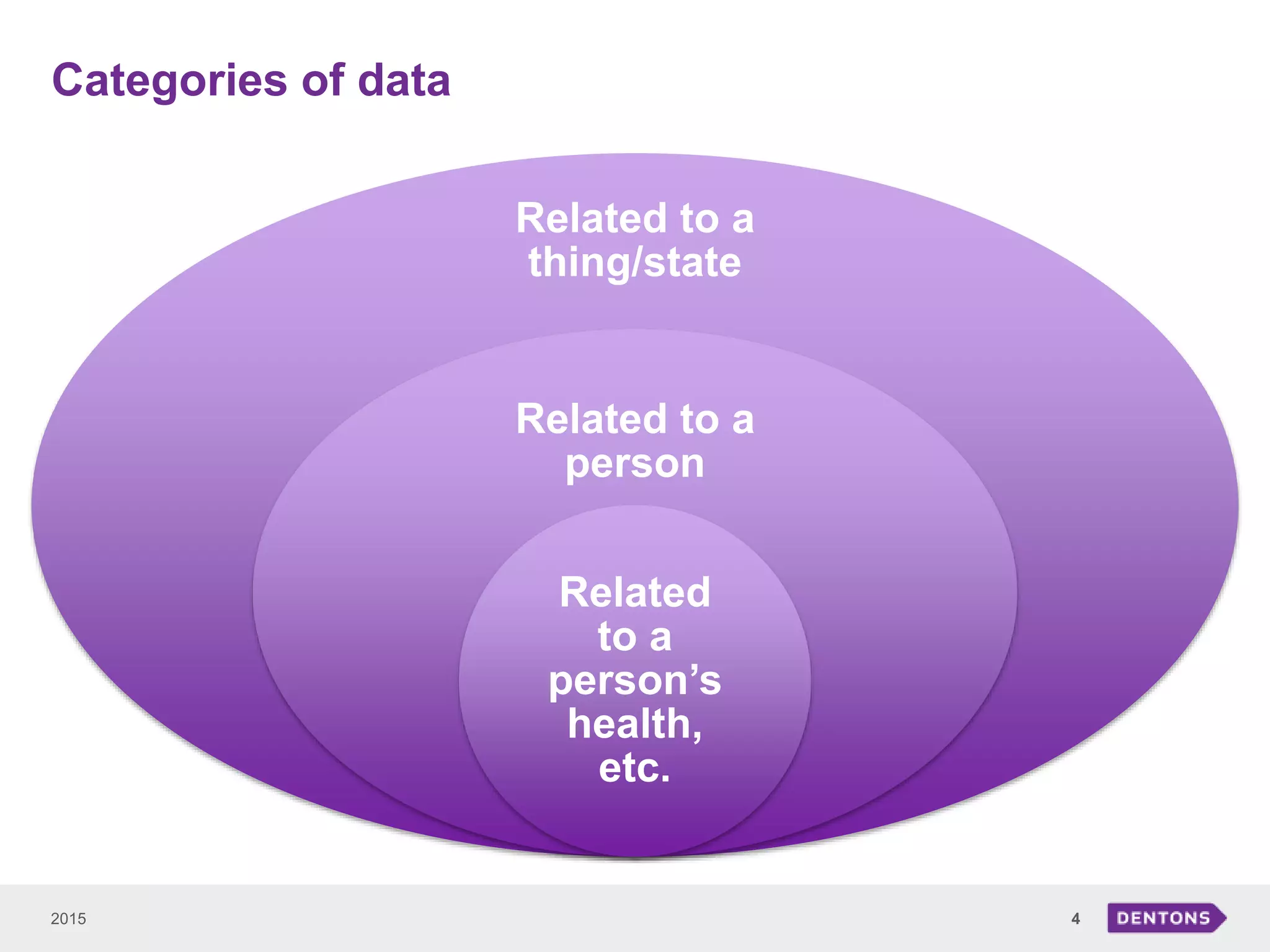
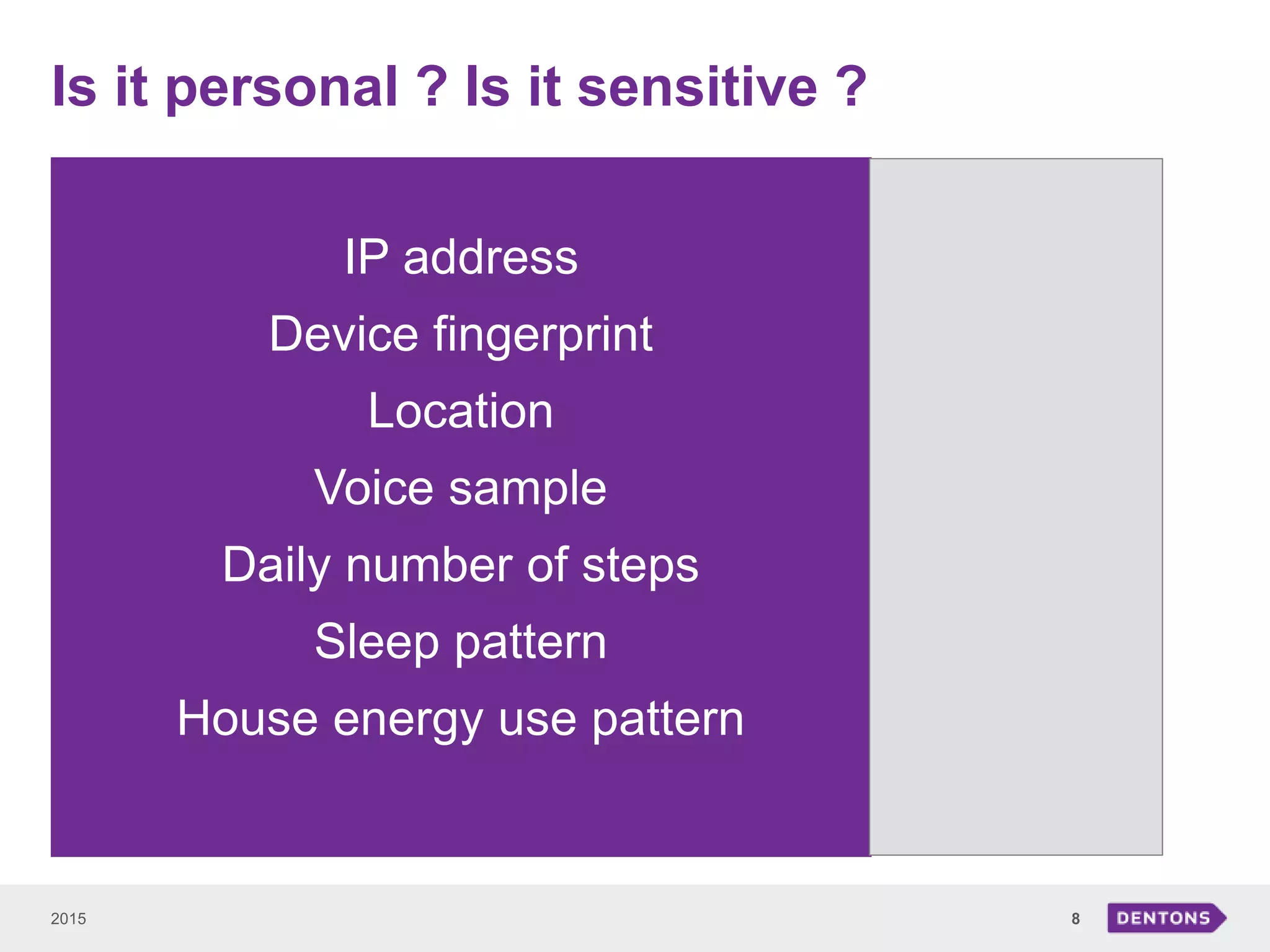
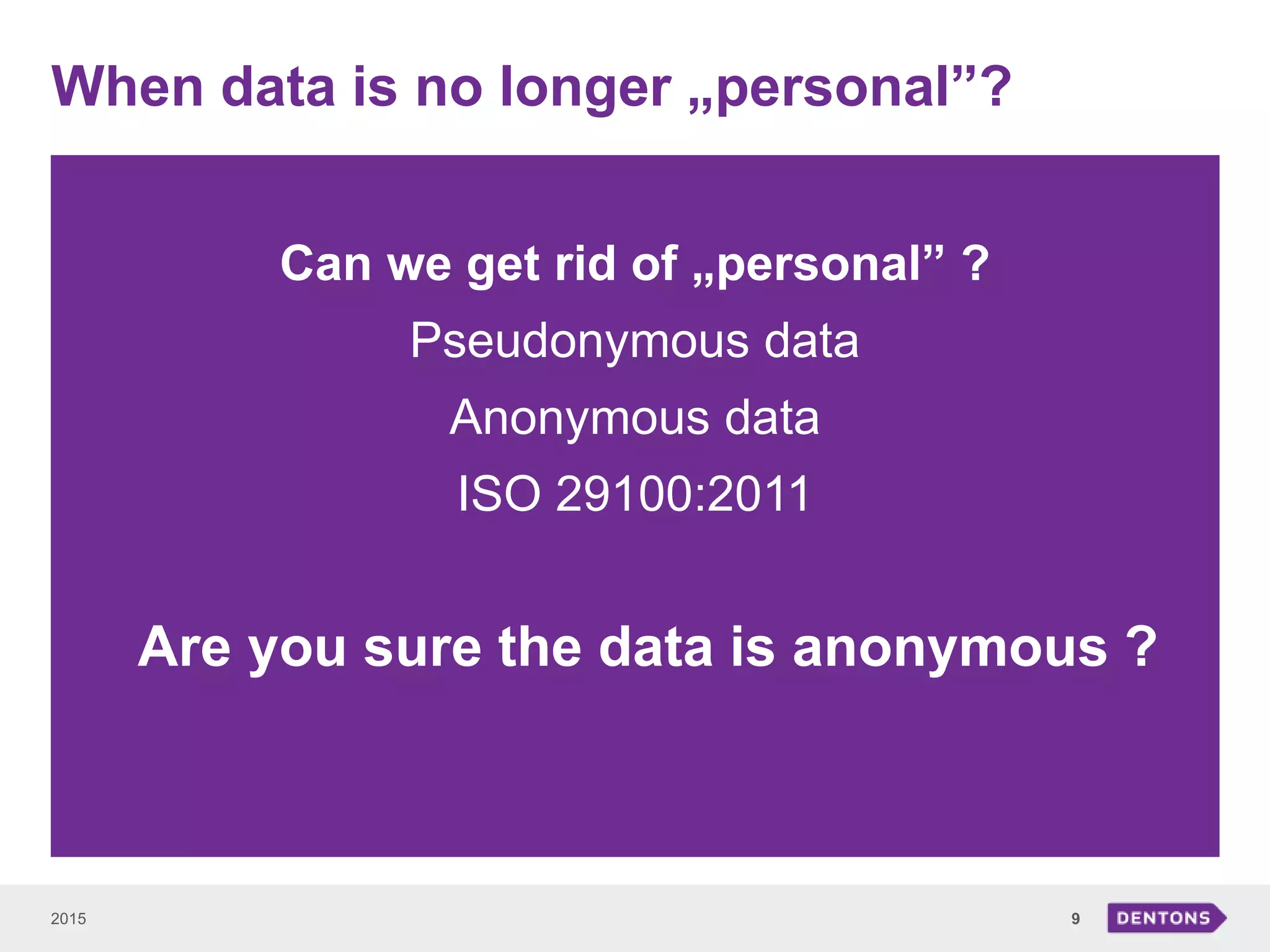
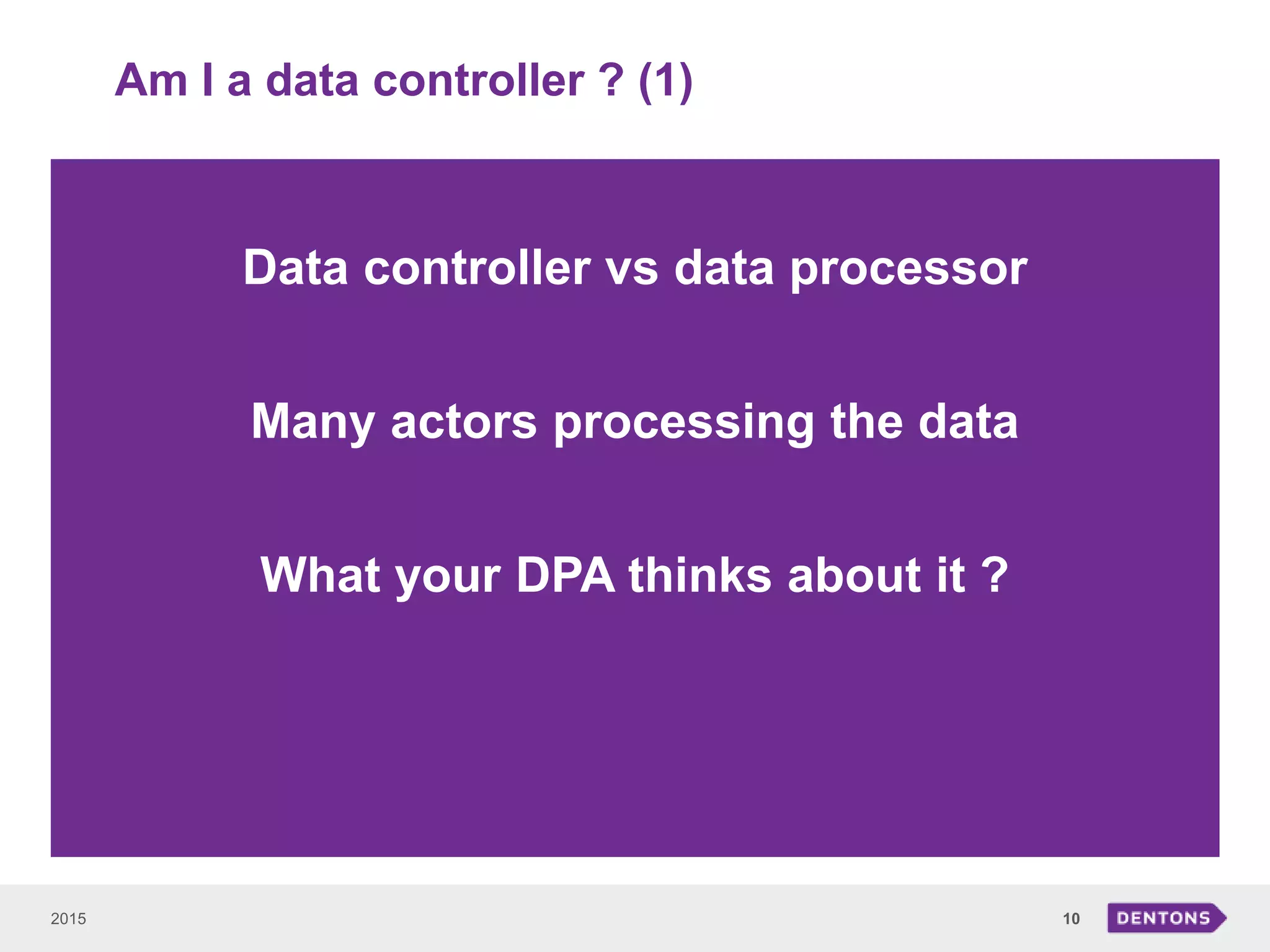
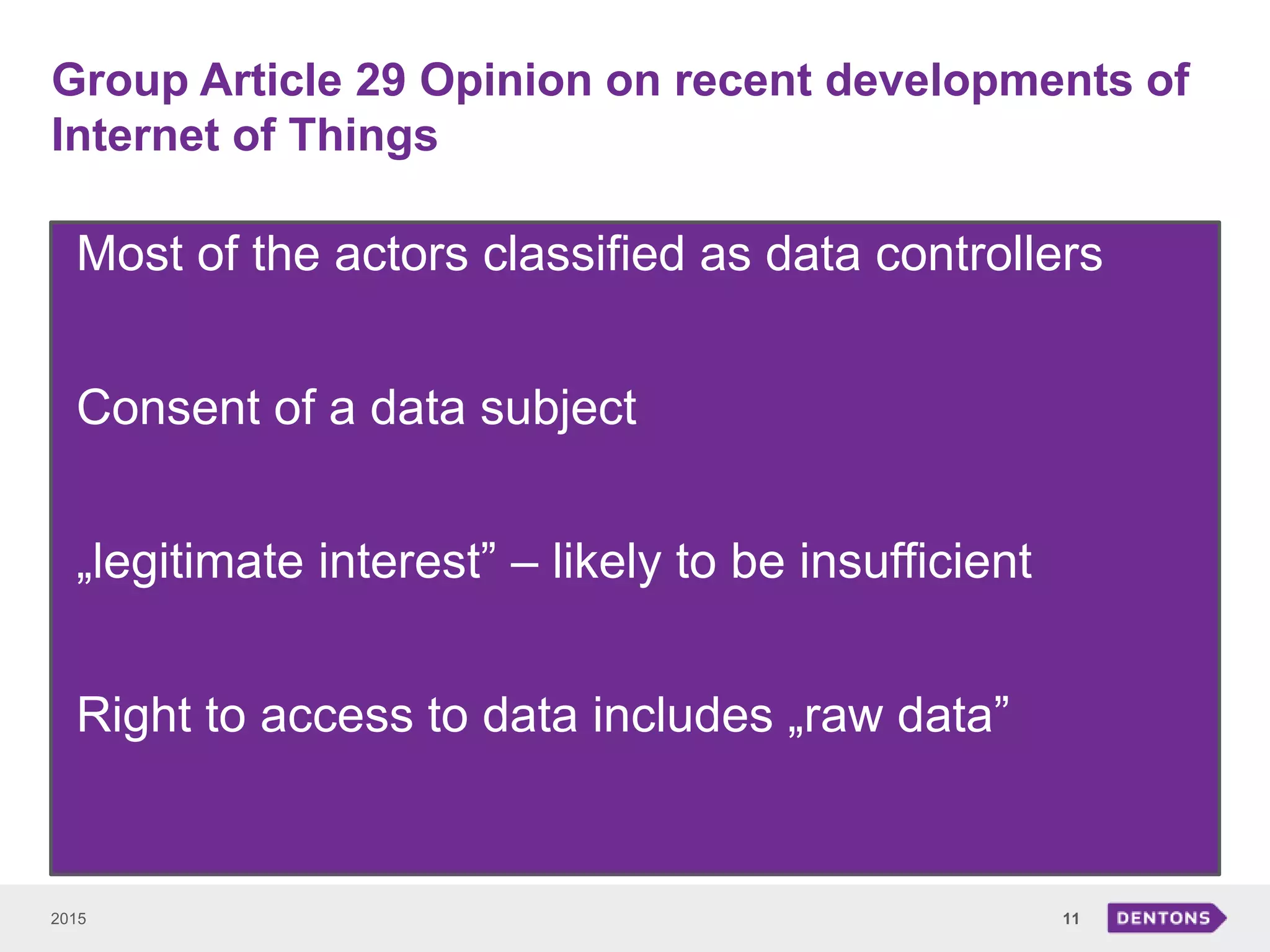
This document summarizes a seminar on legal issues related to the Internet of Things. It discusses definitions of IoT, categories of data collected, applicable laws around personal data protection, telecommunications, and cybersecurity. It also examines issues around determining data controllers, anonymizing personal data, critical infrastructure regulations, and ownership of IoT-collected business data.