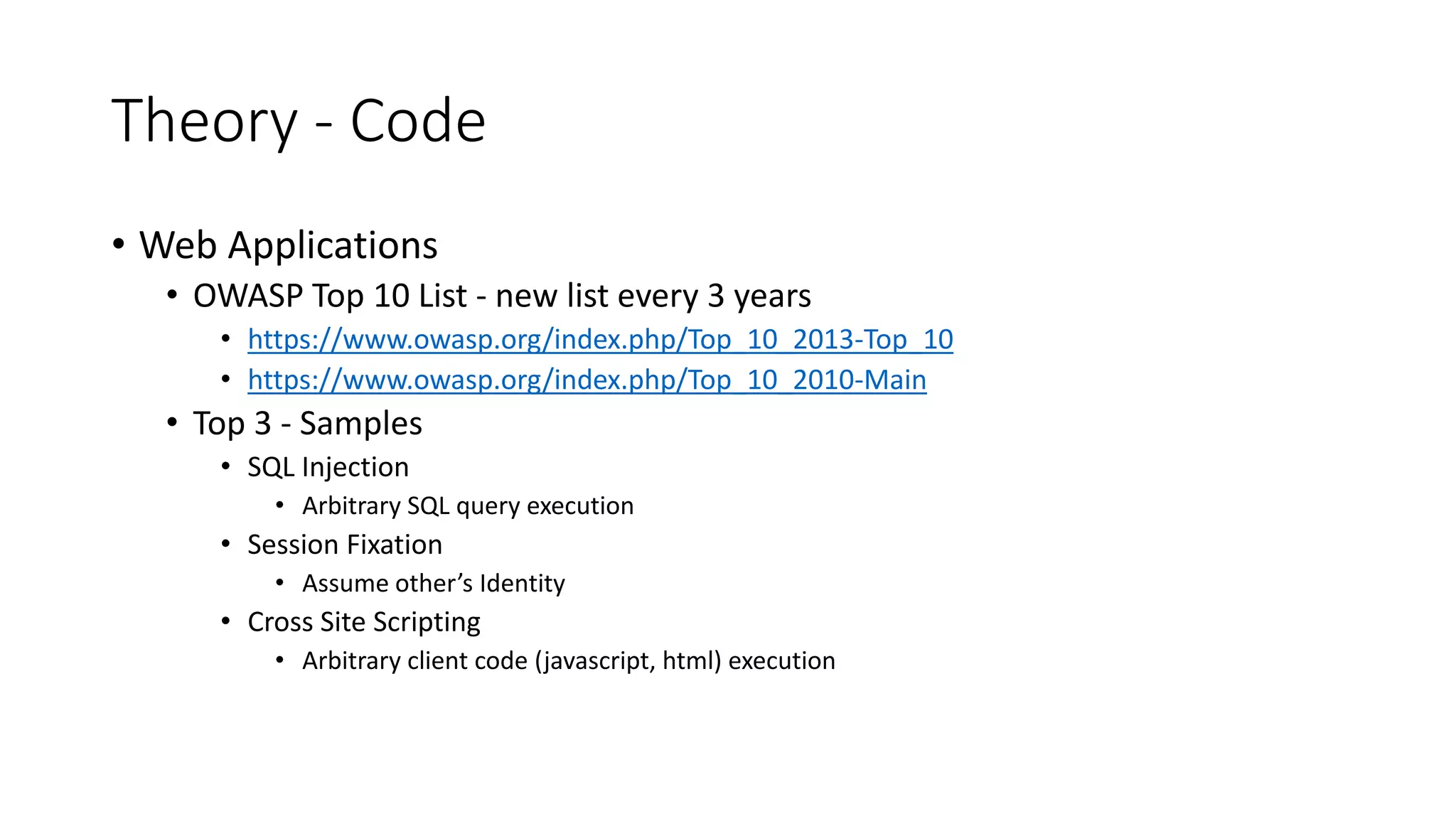
The document discusses secure coding practices, focusing on web application vulnerabilities highlighted by the OWASP Top 10 list, including SQL injection and session fixation. It emphasizes the importance of addressing both security and performance issues, along with practical exercises to understand and mitigate these vulnerabilities. Additionally, the document includes resources for further exploration and suggests measures to prevent exploitation of these vulnerabilities.