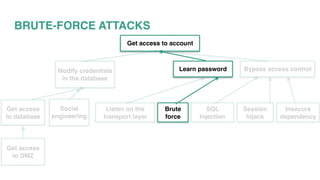
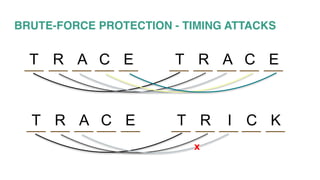
This document discusses various security vulnerabilities and strategies for defending against attacks. It begins by describing common attacks like SQL injection, brute force attacks, and session hijacking. It then outlines approaches to mitigate these risks such as implementing SSL, input validation, secure cookies, and keeping dependencies up-to-date. The document stresses that security is a shared responsibility and must be incorporated into development practices through techniques like writing stories with security acceptance criteria.





















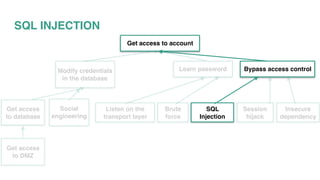



![DATA VALIDATION - SQL INJECTION
// paramaterized
query( "select name from emp where emp_id=$1",
[123] )
// prepared
query( {
name:"emp_name",
text:"select name from emp where emp_id=$1",
values:[123]
})](https://image.slidesharecdn.com/fullstacksurvivingwebsecurity-160713170749/85/Surviving-Web-Security-35-320.jpg)