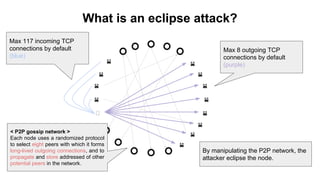
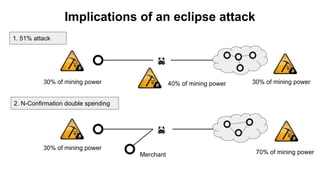
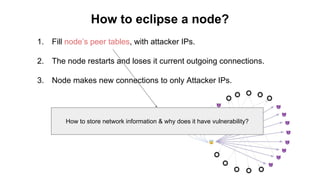
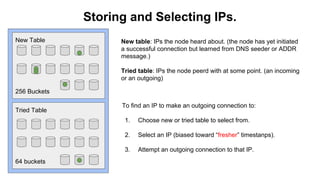
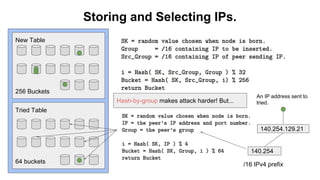
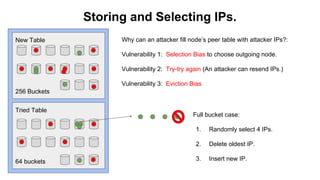
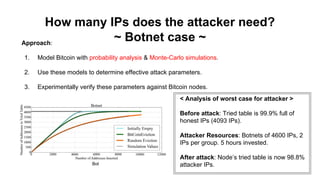
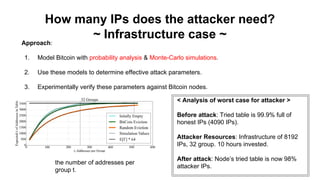
The document discusses eclipse attacks on Bitcoin's peer-to-peer network, where an attacker can isolate a victim node by controlling its connections and allowing the attacker to double-spend with less than 51% of the network's mining power; it analyzes how many IP addresses an attacker would need using botnets or infrastructure to eclipse a node, and proposes several countermeasures that Bitcoin has implemented or could implement to make eclipse attacks more difficult.