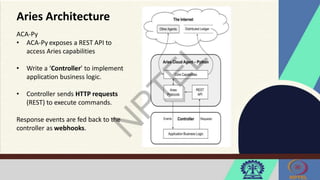
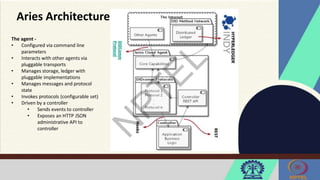
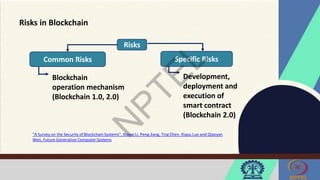
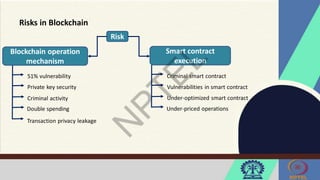
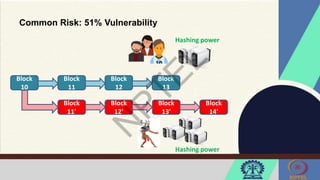
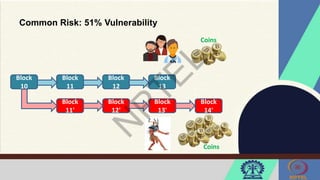
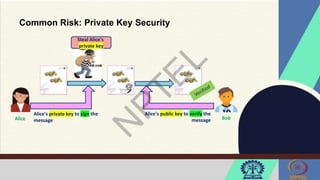
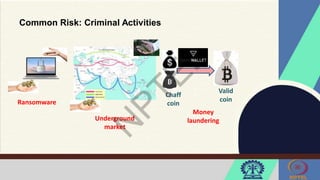
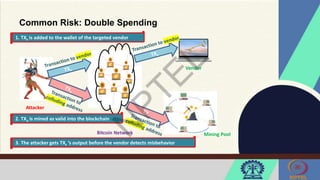
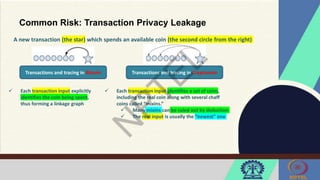
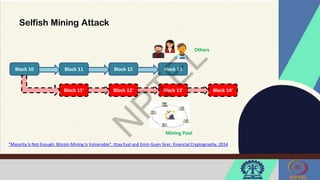
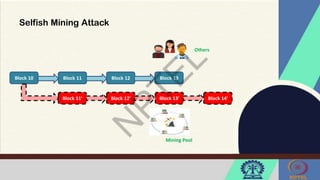
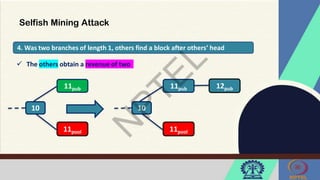
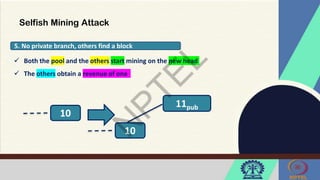
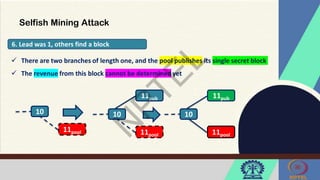
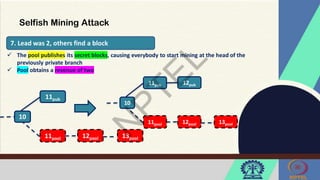
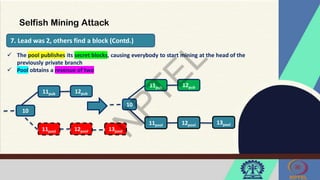
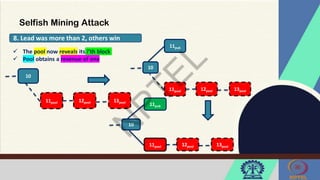
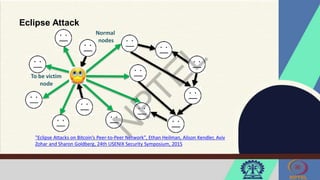
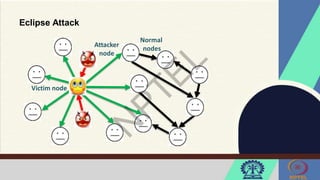
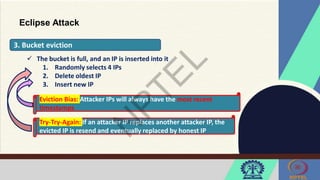
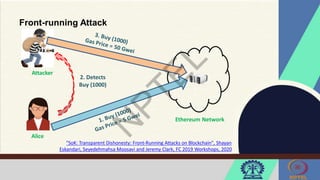
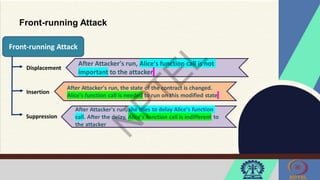
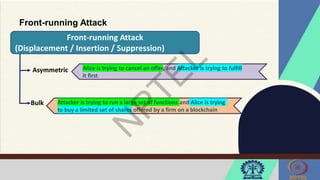
The document discusses Hyperledger Aries, a toolkit for creating and managing verifiable digital credentials using blockchain technology, detailing its architecture, installation, and agent frameworks. It also explores various blockchain security risks, including 51% attacks, private key security, and transaction privacy issues, alongside specific attack strategies like selfish mining and front-running attacks. Finally, it outlines criteria for identifying effective blockchain use cases in enterprises, focusing on business problems, participant roles, and asset management.



























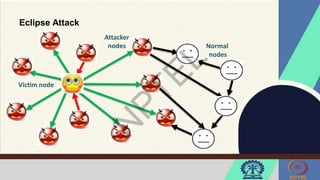
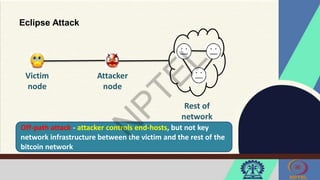
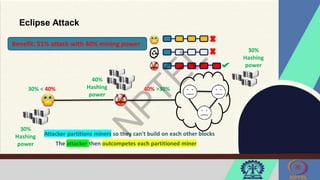
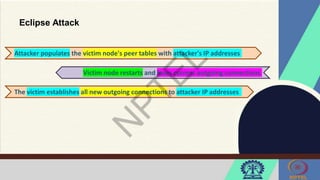


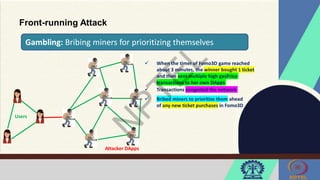
![Front-running Attack
Markets and Exchanges: Spotting a profitable cancellation transaction
[…]
Cancel (order 100)
Breed (cryptokittie 1,
cryptokittie 2)
Buy (order 101)
Bid (Bj)
Register (Bi)
[…] Ethereum Network
(Unordered) mempool
Block Height #N
Register (Bi)
Buy (order 100)
Cancel (order 100)
Buy (order 101)
Bid (Bj)
Breed (cryptokittie 1,
cryptokittie 2)
Reordered Block
Adversarial
miner
mines a
block with
preferred
order](https://image.slidesharecdn.com/week-11-240614034716-89071956/85/Blockchain-Nptel-Online-certification-course-Week-11-pdf-62-320.jpg)