The document summarizes string matching algorithms. It discusses the naive string matching algorithm which checks for matches between the pattern and text string at each possible shift using a loop. It then explains the Rabin-Karp algorithm which uses hashing to quickly filter out invalid shifts. Finally, it describes the Knuth-Morris-Pratt algorithm which preprocesses the pattern to determine the maximum match length at each position to skip unnecessary matching attempts.

![2
1. String Matching :
Let there is an array of text, T[1..n] of length ‘n’.
Let there is a pattern of text, P[1..m] of length ‘m’.
Let T and P are drawn from a finite alphabet .
Here P and T are called ‘Strings of Characters’.
Here, the pattern P occurs with shift s in text T,
if, 0 ≤ s ≤ n – m
and T[s+1..s+m] = P[1..m]
i.e., for 1 ≤ j ≤ m, T[s+j] = P[j]
If P occurs with shift s in T, it is a VALID SHIFT.
Other wise, we call INVALID SHIFT.](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-2-320.jpg)



![6
2. The Naïve String-matching Algorithm :
This algorithm finds all valid shifts using a loop that
checks the condition P[1..m] = T[s+1..s+m] for each
of the n –m + 1 possible values of s.
NAÏVE-STRING-MATCHER(T,P)
1 n = T.length
2 m = P.length
3. for s = 0 to n – m
4. if P[1..m] = = T[s+1..s+m]
5 Print “Pattern occurs with shift s.”](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-6-320.jpg)

![8
3. The Rabin-Karp Algorithm :
Let = {0, 1, 2, … , 9}
Here each character is a decimal digit.
d = | | = 10.
The string 31415 represents 31,415 in radix-d notation.
Let there is a text T[1..n].
Let there is a pattern P[1..m].
Let p denote the corresponding decimal value.
Let ts is the decimal value of the length –m substring
T[s+1..s+m], for s = 0,1,2,..n-m.
ts = p iff T[s+1..s+m] = P[1..m]
s is a valid shift iff ts = p](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-8-320.jpg)
![9
Now, the value of p can be computed using
Horner’s rule as follows:
p = P[1..m] = P[1] P[2] P[3]…P[m]
So, p = P[m] + 10 (P[m-1] + 10 (P[m-2] + … +
10 (P[2] + 10 P[1])…)).
Similarly, one can compute t0 as follows :
t0 = T[m] + 10 (T[m-1] + 10 (T[m-2] + … +
10 (T[2] + 10 T[1])…)).
Here we can compute ts+1 from ts as follows :
ts+1 = 10 (ts – 10m-1 T[s+1 ]) + T[s+m+1].](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-9-320.jpg)
![10
Let q is defined so that dq fits in one computer word
and the above recurrence equation can be written as :
ts+1 = (d (ts – T[s+1] h ) + T[s+m+1]) mod q.
Here, h dm-1 (mod q)
i.e., h is the first digit in the m-digit text window.
Ex-6 : Let m = 5, ts = 31415
Let T[s+m+1] = 2
So, RHS = 10 (ts – 10m-1 T[s+1 ]) + T[s+m+1]
= 10 (31415 – 104 . 3) + 2 = 14150 + 2 = 14152](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-10-320.jpg)
![11
The test ts p (mod q) is a fast heuristic
test to rule out invalid shifts s.
For any value of ‘s’,
if ts p (mod q) is TRUE
and P[1..m] = T[s+1..s+m] is FALSE
then ‘s’ is called SPURIOUS HIT.
Note : a) If ts p (mod q) is TRUE
then ts = p may be TRUE
b) If ts p (mod q) is FALSE
then ts ≠ p is definitely TRUE](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-11-320.jpg)
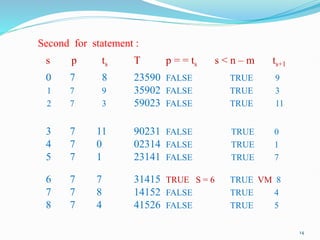
![12
RABIN-KARP-MATCHER (T,P,d,q)
1 n = T.length
2 m = P.length
3 h = dm-1 (mod q)
4 p = 0
5 t0 = 0
6 for i = 1 to m // preprocessing
7 p = (dp + P[i]) mod q
8 t0 = (d t0 + T[i]) mod q
9 for s = 0 to n-m //matching
10 if (p = = ts )
11 if (P[1..m] = T[s+1..s+m])
12 print “Pattern occurs with shift” s
13 if (s < n – m)
14 ts+1 = (d (ts – T[s+1] h ) + T[s+m+1]) mod q.](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-12-320.jpg)



![17
COMPUTE-PREFIX-FUNCTION (P) :
1. m = P.length
2. Let [1..m] be a new array
3. [1] = 0
4. k = 0
5. for q = 2 to m
6. while k > 0 and P[k+1] P[q]
7. k = [k]
8. if P[k+1] = = P[q]
9. k = k + 1
10. [q] = k
11. return ](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-17-320.jpg)
![18
Ex-8 (contd…)
P : 1 2 3 4 5 6 7
a b a b a c a
INIT : m = 7 [1] = 0 k = 0
Step : q = 2 :
Here, k = 0 & P[k+1] = a & P[q] = b
So, while : FALSE & if : FALSE
Hence, [2] = 0
Step : q = 3 :
Here, k = 0 & P[k+1] = a & P[q] = a
So, while : FALSE & if : TRUE k = 1
Hence, [3] = 1](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-18-320.jpg)
![19
Step : q = 4 :
Here, k = 1 & P[k+1] = b & P[q] = b
So, while : FALSE & if : TRUE k = 2
Hence, [4] = 2
Step : q = 5 :
Here, k = 2 & P[k+1] = a & P[q] = a
So, while : FALSE & if : TRUE k = 3
Hence, [5] = 3
Step : q = 6 :
Here, k = 3 & P[k+1] = b & P[q] = c
So, while : TRUE k = 1 ( = [3] )
& k = 1 & P[k+1] = b & P[q] = c
while : TRUE k = 0 ( = [1] )
if : FALSE ([P[1] = = P[6])
Hence, [6] = 0](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-19-320.jpg)
![20
Step : q = 7 :
Here, k = 0 & P[k+1] = a & P[q] = a
So, while : FALSE &
if : TRUE (P[1] = = P[7] )
k = 1
Hence, [7] = 1
Hence the array is as follows :
q : 1 2 3 4 5 6 7
: 0 0 1 2 3 0 1
Hence, this returns the value : 1](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-20-320.jpg)
![21
KMP-MATCHER (T,P) :
1. n = T.length
2. m = P.length
3. = COMPUTE-PREFIX-FUNCTION(P)
4. q = 0
5. for i = 1 to n
6. while q > 0 and P[q+1] T[i]
7. q = [q]
8. if P[q+1] = = T[i]
9. q = q + 1
10. if q = = m
11. print ”Pattern occurs with shift” i - m
12. q = [q]](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-21-320.jpg)
![22
Ex-8 contd..
KMP-Matcher (T,P) :
INIT : n = 15 m = 7 =1 q = 0
----------------------------------------------------------------------------------------
i q C1 C2 wh q= [q] if q++ if print q= [q]
-------------------------------------------------------------------
1 0 F T F --- F ---- F ---- ----
2 0 F F F --- T q = 1 F ---- ----
3 1 T T T q = 0 F ---- F ---- ----
4 0 F T F --- F ---- F ---- ----
5 0 F F F --- T q = 1 F ---- ----](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-22-320.jpg)
![23
-----------------------------------------------------------------------------------------------
i q C1 C2 wh q= [q] if q++ if print q= [q]
-----------------------------------------------------------------------------------------------
6 1 T F F --- T q=2 F ---- ----
7 2 T F F --- T q=3 F ---- ----
8 3 T F F --- T q=4 F ---- ----
9 4 T F F --- T q=5 F ---- ----
10 5 T F F --- T q=6 F ---- ----
11 6 T F F --- T q=7 F shift 4 q=1
12 1 T T T q=0 F ---- F ---- ----
13 0 F F F ---- T q=1 F ---- ----
14 1 T T T q=0 F ---- F ---- ----
15 0 F F F ---- T q=1 F ---- ----
-----------------------------------------------------------------------------------------------](https://image.slidesharecdn.com/14959892-240327090212-c922b90b/85/String-Matching-Algorithms-Advance-algorithm-23-320.jpg)