Embed presentation
Downloaded 54 times





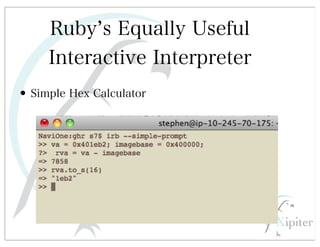
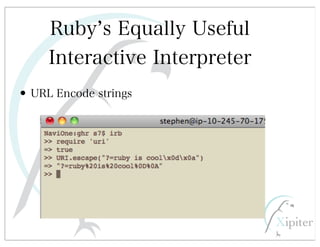
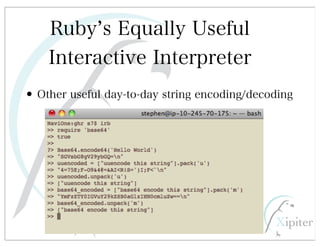
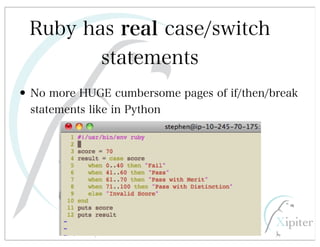
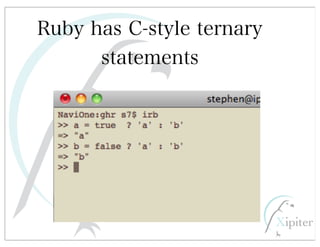
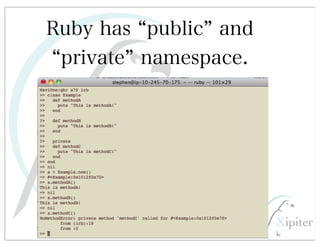
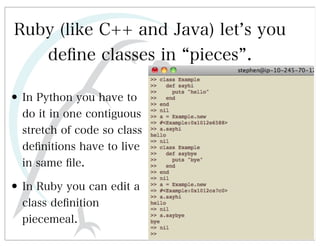
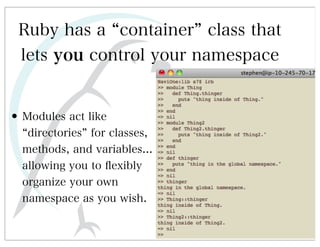
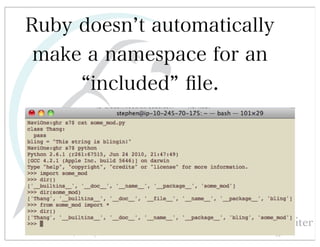
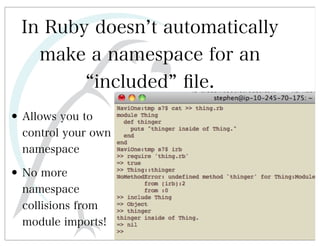


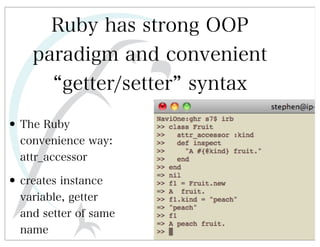



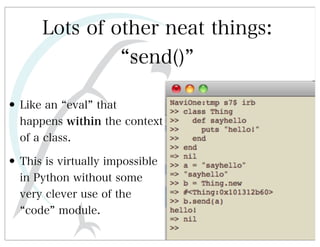

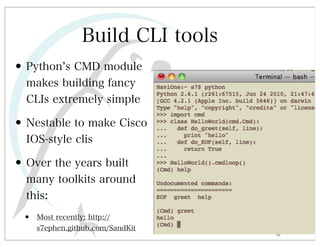
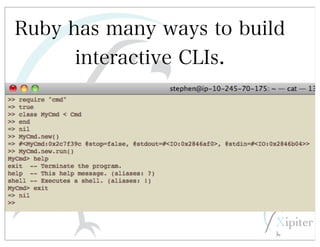
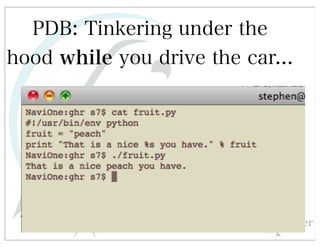
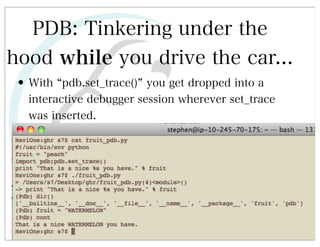
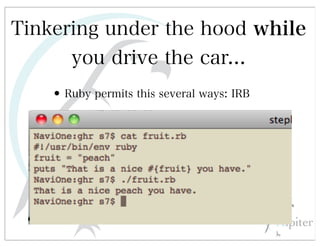
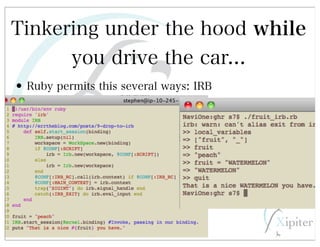
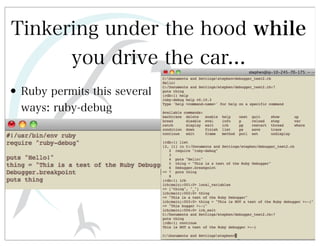


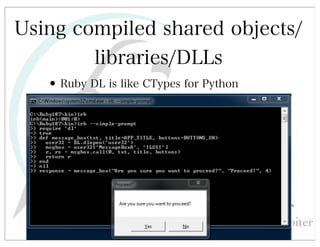
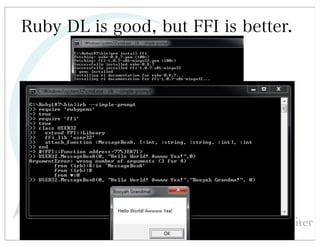


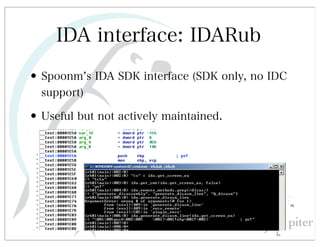

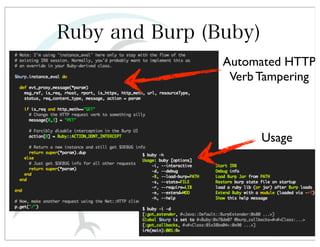


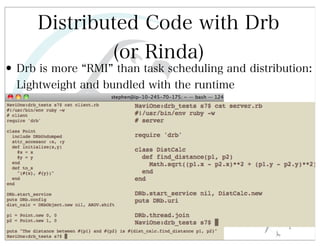
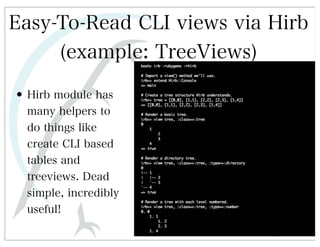
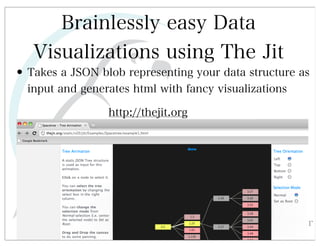


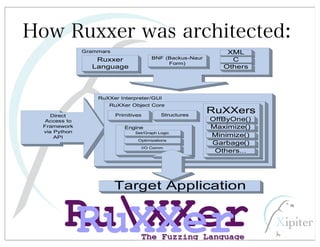

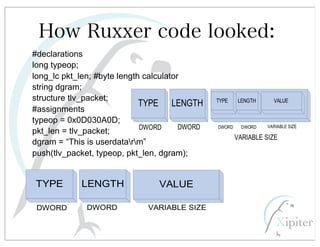

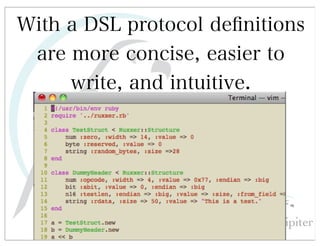



This document discusses automated HTTP verb tampering. It provides links to GitHub repositories containing code for modifying HTTP requests in Ruby, including changing the verb type and adding custom payloads. Specifically, it links to code that allows modifying the user32 library in Ruby, generating TLV packets to embed data, and a presentation on Ruby meta-fuzzing techniques and another GitHub project for HTTP request manipulation in Ruby.

























































