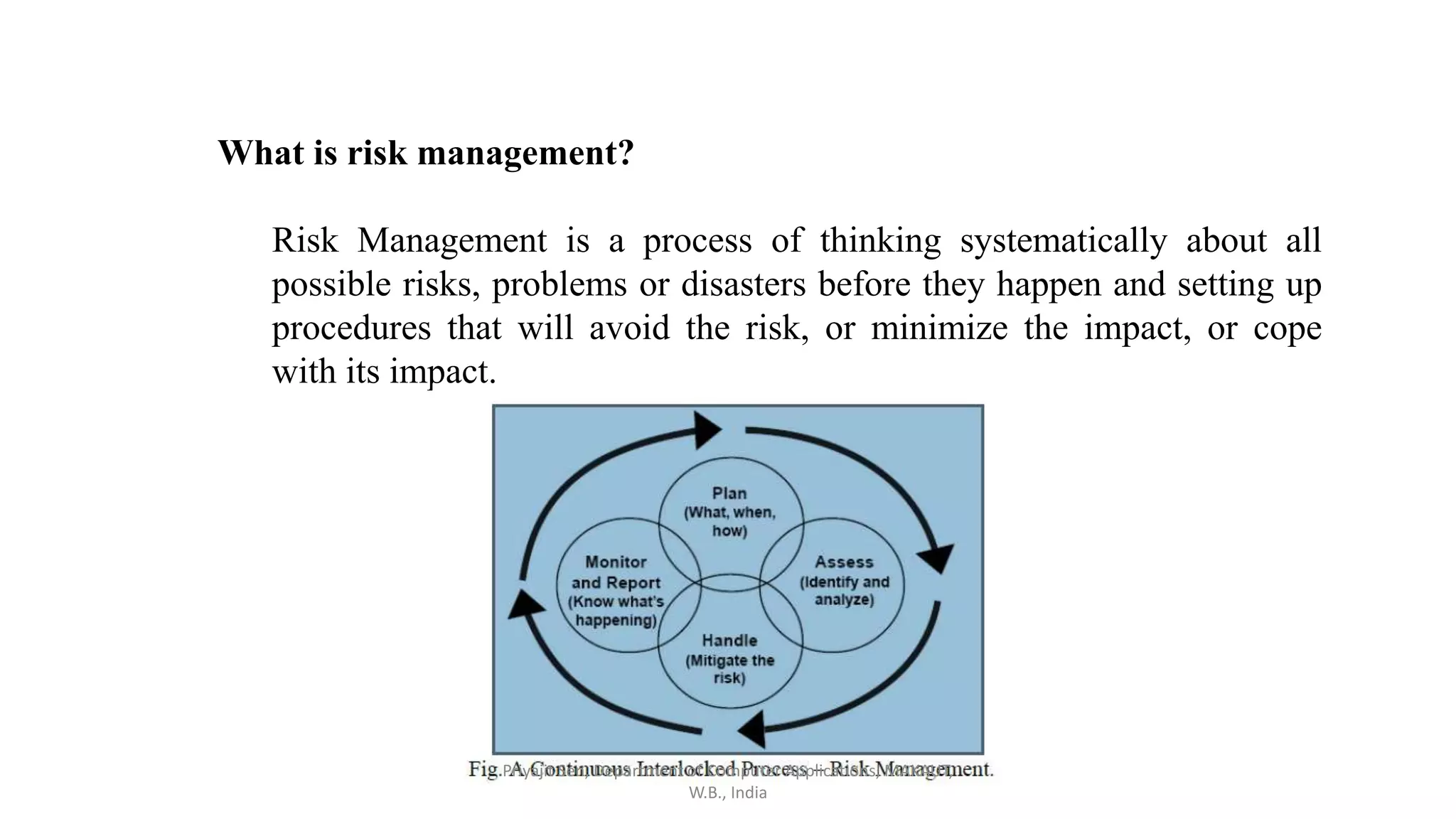
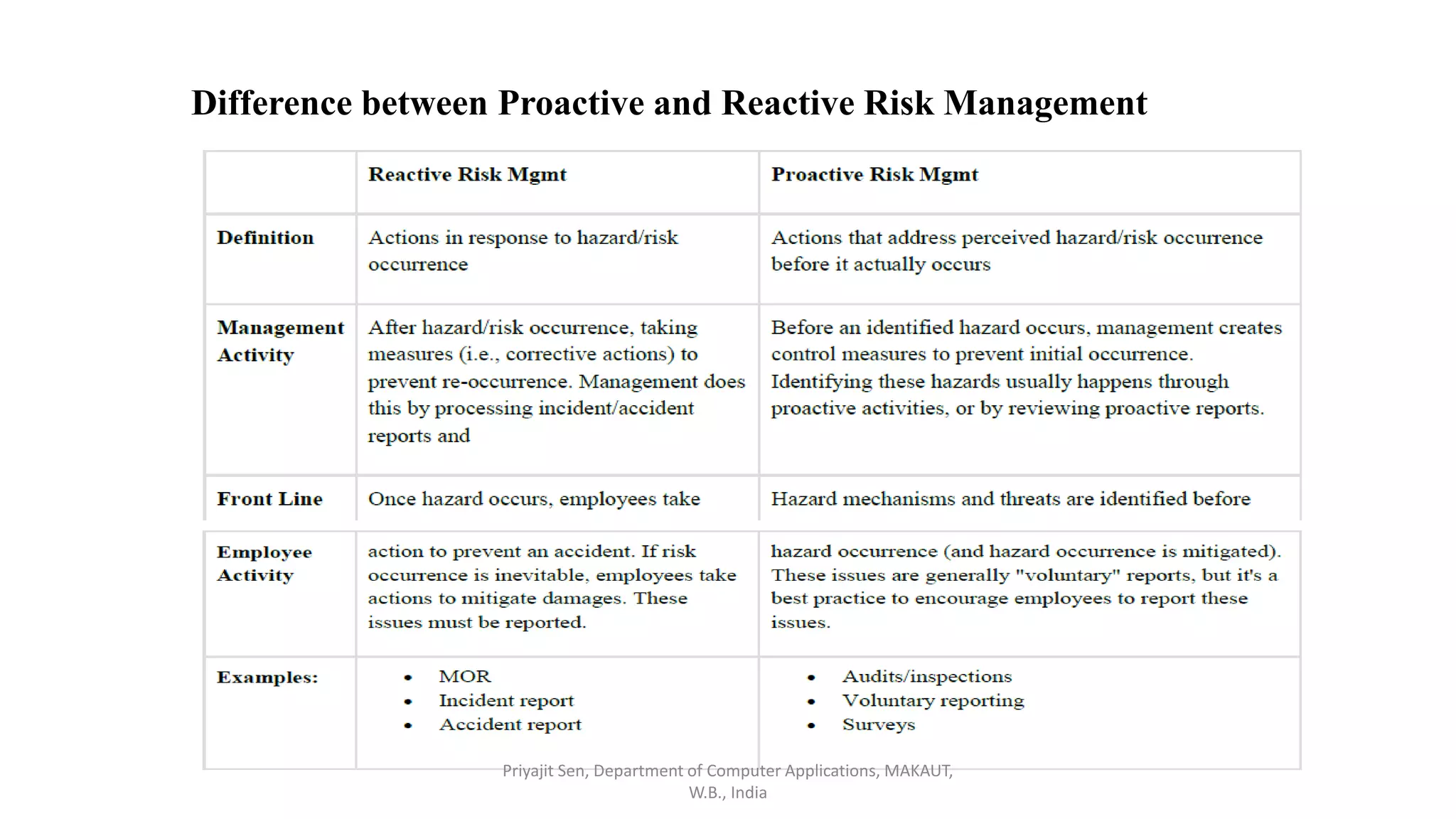
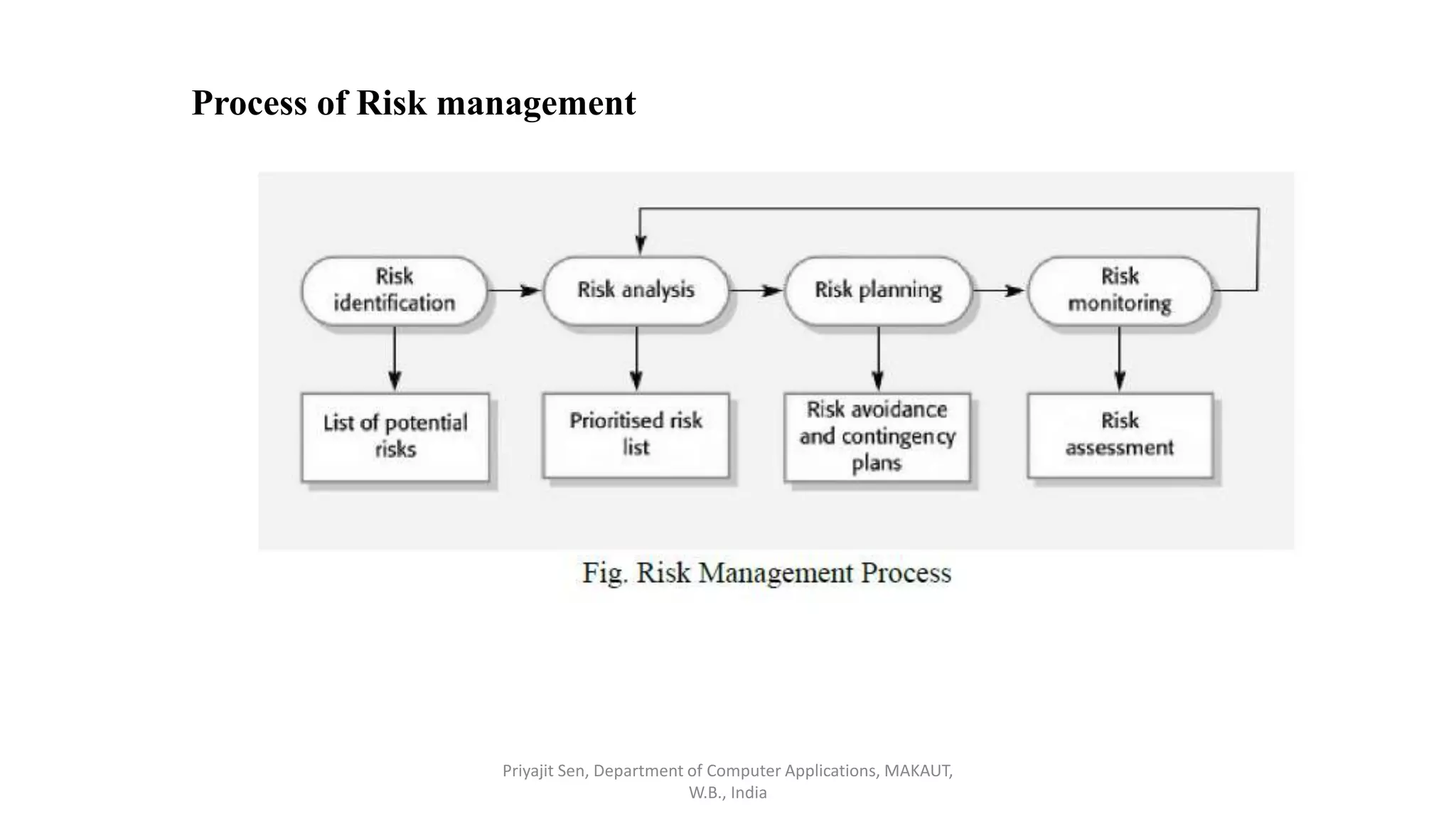
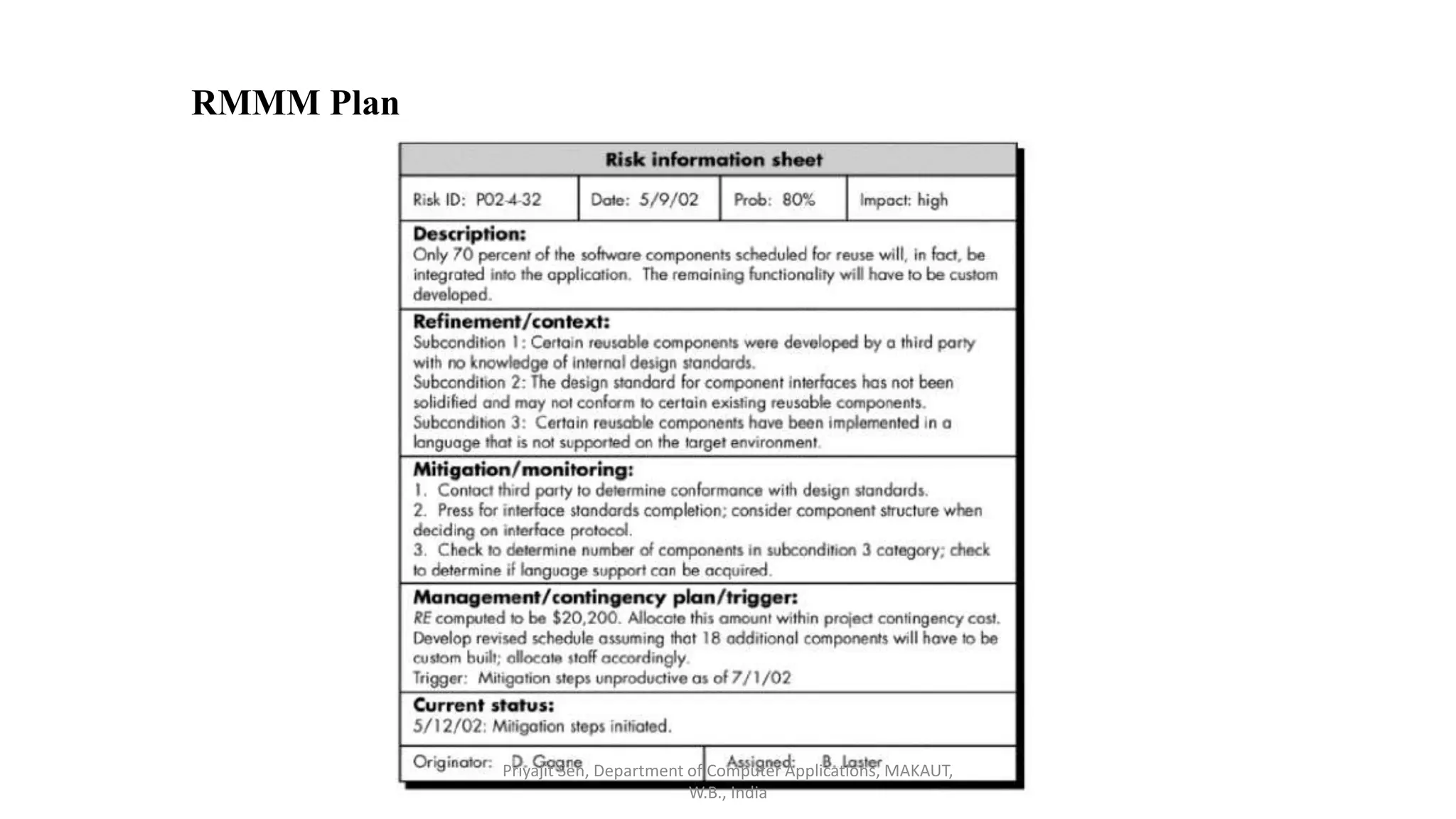
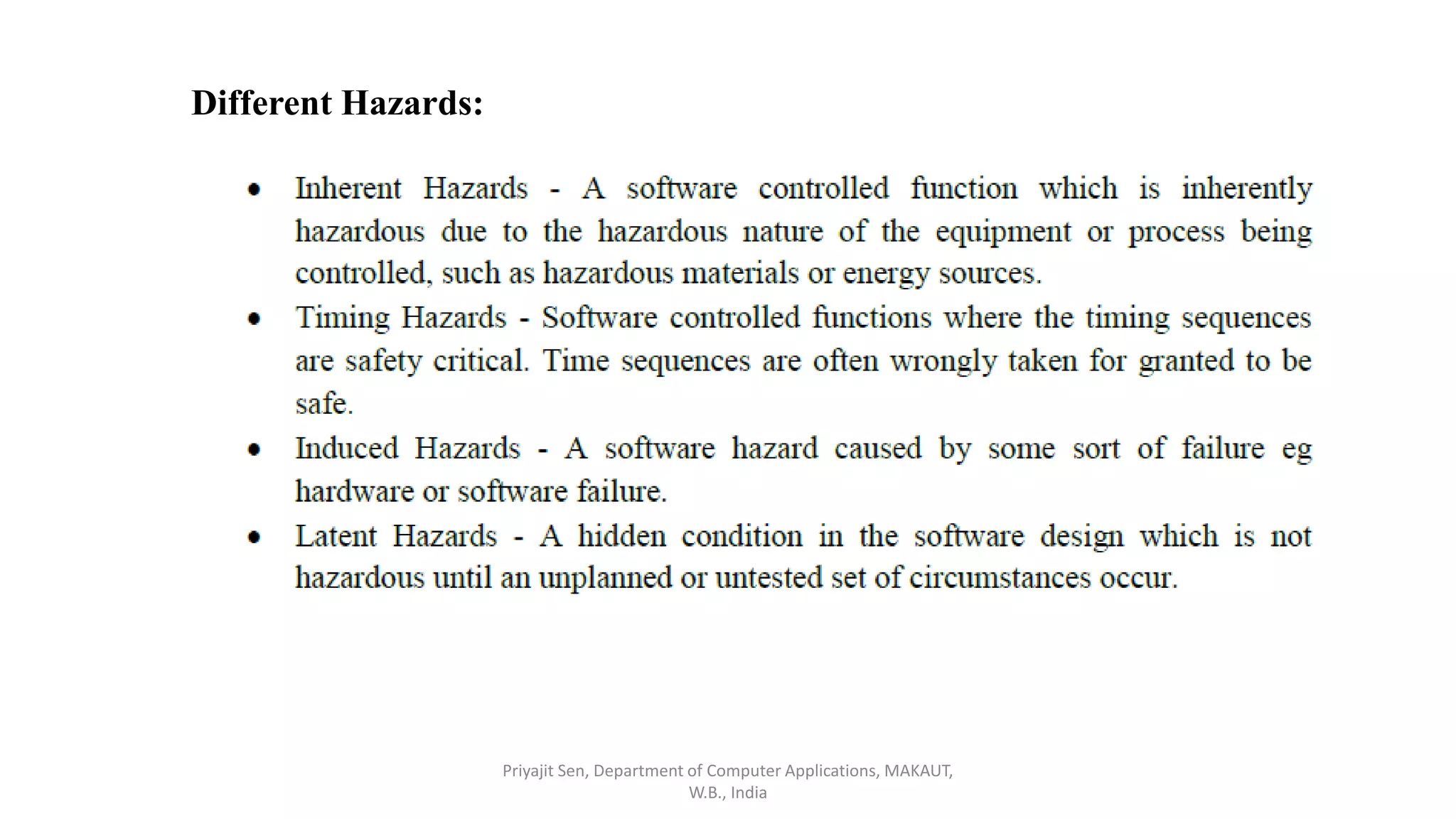
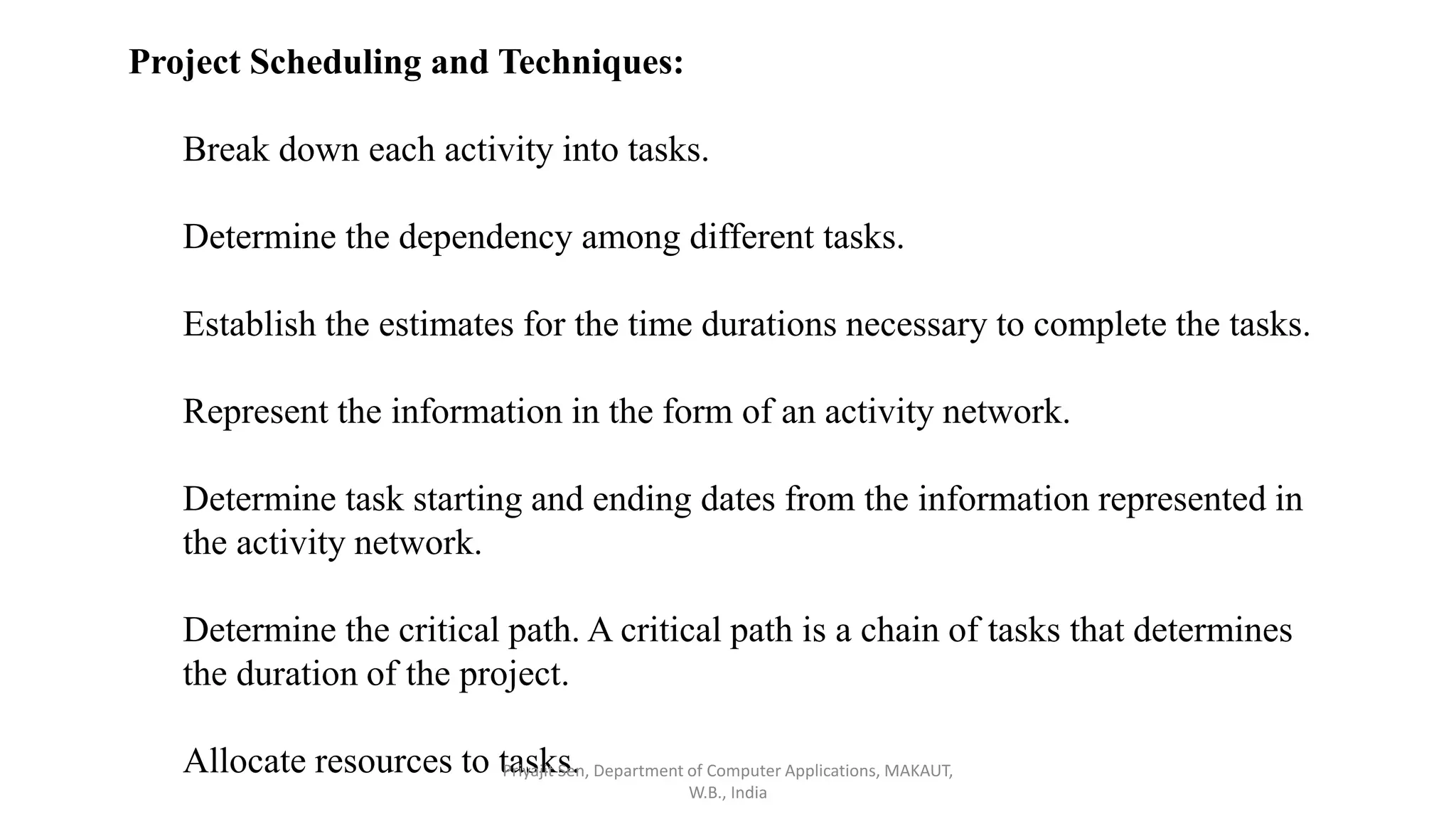
This document discusses risk analysis and management. It defines risk as a potential problem that may or may not occur, with uncertainty and potential losses. Risk management is described as a process of systematically considering possible risks, problems, or disasters before they happen to avoid or minimize impacts. Reactive risk management responds after incidents, while proactive risk management attempts to reduce future risks. Key aspects of risk management include identification, assessment, mitigation, and monitoring of project, product, and business risks. Various risk analysis techniques are also outlined.