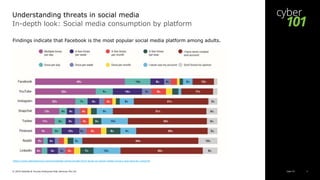
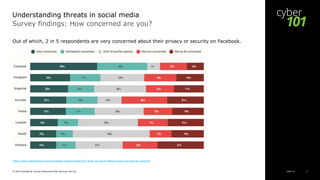
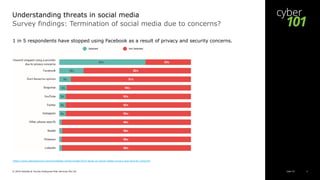
This document discusses threats in social media according to a 2019 study. It finds that most adults use social media daily and have privacy/security concerns. Facebook is the most popular platform but 2 in 5 users are very concerned about privacy/security on it, and 1 in 5 have stopped using it due to such concerns. The document outlines key social media threats like data breaches, phishing/malware, catfishing/deception, and cyberbullying. It provides examples of each and advises users to take precautions like using strong passwords and privacy settings.