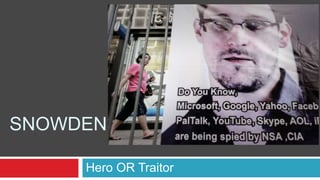
Snowden -Hero OR Traitor
•Download as PPTX, PDF•
5 likes•6,515 views
Edward Snowden revealed classified details of extensive US government surveillance programs to the media in 2013. He is currently living in temporary asylum in Russia after being charged with theft and unauthorized communication of national defense information by the US. Snowden believes he acted correctly to inform the public about surveillance that collected data on innocent people without their knowledge. However, others argue he sabotaged legal government programs and endangered national security. Public opinion polls at the time showed Americans were divided on whether Snowden was a hero or traitor for his actions.
Report
Share
Report
Share
Recommended
Edward Snowden

A description of the events surrounding Edward Snowden and why he is one of the most important Americans. Created as a project for a U.S. History class where we made a presentation on an important American person or event and also made a symbol out of Post-Its, but I took that part out.
NSA Snooping Scandal

- PRISM is a classified US government program to collect internet communications from major internet companies like Google and Facebook.
- It was revealed to the public in 2013 after former NSA contractor Edward Snowden leaked classified documents about the program.
- PRISM collects emails, photos, videos, logs of online chats, file transfers and more, with the stated goal of monitoring communications of non-US citizens outside the US.
C ity of saint paul v. east side boys and selby siders

The city of Saint Paul filed lawsuits against two gangs, the East Side Boys and Selby Siders, under the state's Civil Gang Injunction statute to prevent criminal gang activity during the Rondo Days festival on July 18, 2009. The lawsuits sought to enjoin criminal gang activity by banning gang members from attending the festival in order to preserve the history and give citizens peace during the event. Prior cases in California and Texas had upheld the use of civil gang injunctions.
Intelligence led policing- pole sandbox (webinar 21012019) 

This document discusses using Neo4j and graph databases for intelligence-led policing. It introduces intelligence-led policing as an information-based model that aims to provide strategic knowledge and a targeted approach to crime reduction. The document outlines the POLE data model for representing people, objects, locations, and events in a graph. It then demonstrates Neo4j for implementing a graph database using crime data from Greater Manchester, with nodes for crimes, locations, people, and relationships between them. Finally, it discusses ways the demo could be extended for real-world use, such as adding more detailed relationships and supporting data traceability.
International Crime

The document discusses categories of international crime such as genocide, war crimes, and piracy. It describes universal jurisdiction and the establishment of the International Criminal Court in 2002. It also discusses transnational crimes, causes of transnational crimes, and how countries deal with international crime through measures like extradition treaties, domestic laws, and organizations like Interpol. Effectiveness of dealing with international crime is mixed as state sovereignty concerns remain, international cooperation is still developing, and prosecuting these crimes can be very costly.
Jerry Banks Criminal Complaint

Jerry Banks is accused of kidnapping GD on January 6, 2018 in Danville, Vermont. GD's wife MD reported that a man claiming to be a US Marshal arrested GD for racketeering and took him away in a white vehicle. GD's body was later found shot in Barnet, Vermont. The FBI investigation identified two prepaid phones, a 911 phone and 201 phone, purchased by the same individual around the times of the kidnapping and murder. Surveillance footage showed a bearded white man matching Banks' description purchasing one of the phones. Cell site data placed both phones near the crime scenes around the relevant times. Banks is charged with kidnapping resulting in death.
Foot pursuits training

This document outlines standard operating procedures for foot pursuits by police officers. It defines key terms like foot pursuit, suspect, and supervisor. It describes factors officers should consider before initiating a foot pursuit and their responsibilities during one. It also covers terminating a pursuit, tactical considerations, the supervisor's role, and training requirements. The document provides guidelines to help officers engage in foot pursuits safely and apprehend suspects.
Duest v. state

1. Lloyd Duest was seen carrying a knife and stating his intent to "roll a fag". He was later seen at a gay bar with the victim, John Pope, before Pope's body was discovered stabbed multiple times at his home.
2. Duest was convicted of first-degree murder and sentenced to death. He appealed the conviction.
3. The Supreme Court affirmed the conviction, finding there was sufficient evidence of premeditation based on Duest's statements about getting money from "rolling gay guys", being seen leaving the bar with the victim while carrying a knife, and the multiple stab wounds found on the victim's body.
Recommended
Edward Snowden

A description of the events surrounding Edward Snowden and why he is one of the most important Americans. Created as a project for a U.S. History class where we made a presentation on an important American person or event and also made a symbol out of Post-Its, but I took that part out.
NSA Snooping Scandal

- PRISM is a classified US government program to collect internet communications from major internet companies like Google and Facebook.
- It was revealed to the public in 2013 after former NSA contractor Edward Snowden leaked classified documents about the program.
- PRISM collects emails, photos, videos, logs of online chats, file transfers and more, with the stated goal of monitoring communications of non-US citizens outside the US.
C ity of saint paul v. east side boys and selby siders

The city of Saint Paul filed lawsuits against two gangs, the East Side Boys and Selby Siders, under the state's Civil Gang Injunction statute to prevent criminal gang activity during the Rondo Days festival on July 18, 2009. The lawsuits sought to enjoin criminal gang activity by banning gang members from attending the festival in order to preserve the history and give citizens peace during the event. Prior cases in California and Texas had upheld the use of civil gang injunctions.
Intelligence led policing- pole sandbox (webinar 21012019) 

This document discusses using Neo4j and graph databases for intelligence-led policing. It introduces intelligence-led policing as an information-based model that aims to provide strategic knowledge and a targeted approach to crime reduction. The document outlines the POLE data model for representing people, objects, locations, and events in a graph. It then demonstrates Neo4j for implementing a graph database using crime data from Greater Manchester, with nodes for crimes, locations, people, and relationships between them. Finally, it discusses ways the demo could be extended for real-world use, such as adding more detailed relationships and supporting data traceability.
International Crime

The document discusses categories of international crime such as genocide, war crimes, and piracy. It describes universal jurisdiction and the establishment of the International Criminal Court in 2002. It also discusses transnational crimes, causes of transnational crimes, and how countries deal with international crime through measures like extradition treaties, domestic laws, and organizations like Interpol. Effectiveness of dealing with international crime is mixed as state sovereignty concerns remain, international cooperation is still developing, and prosecuting these crimes can be very costly.
Jerry Banks Criminal Complaint

Jerry Banks is accused of kidnapping GD on January 6, 2018 in Danville, Vermont. GD's wife MD reported that a man claiming to be a US Marshal arrested GD for racketeering and took him away in a white vehicle. GD's body was later found shot in Barnet, Vermont. The FBI investigation identified two prepaid phones, a 911 phone and 201 phone, purchased by the same individual around the times of the kidnapping and murder. Surveillance footage showed a bearded white man matching Banks' description purchasing one of the phones. Cell site data placed both phones near the crime scenes around the relevant times. Banks is charged with kidnapping resulting in death.
Foot pursuits training

This document outlines standard operating procedures for foot pursuits by police officers. It defines key terms like foot pursuit, suspect, and supervisor. It describes factors officers should consider before initiating a foot pursuit and their responsibilities during one. It also covers terminating a pursuit, tactical considerations, the supervisor's role, and training requirements. The document provides guidelines to help officers engage in foot pursuits safely and apprehend suspects.
Duest v. state

1. Lloyd Duest was seen carrying a knife and stating his intent to "roll a fag". He was later seen at a gay bar with the victim, John Pope, before Pope's body was discovered stabbed multiple times at his home.
2. Duest was convicted of first-degree murder and sentenced to death. He appealed the conviction.
3. The Supreme Court affirmed the conviction, finding there was sufficient evidence of premeditation based on Duest's statements about getting money from "rolling gay guys", being seen leaving the bar with the victim while carrying a knife, and the multiple stab wounds found on the victim's body.
Chapter6

The document discusses the history and goals of the US prison system. It describes how prisons evolved from focusing solely on custody in the 1940s-50s to incorporating rehabilitation programs in the 1960s-70s. The three main models of incarceration are the custodial model which focuses on incapacitation and deterrence, the rehabilitation model which emphasizes treatment, and the reintegration model prioritizing community supervision. The document also outlines trends in incarceration rates and prison populations as well as strategies for dealing with overcrowding issues.
Fourth Amendment notes

This document summarizes key aspects of the 4th Amendment regarding search and seizure. It outlines the differences between probable cause and reasonable suspicion, with probable cause requiring a likelihood of criminal activity and reasonable suspicion only requiring articulable facts. It also discusses allowable warrantless searches incident to arrest, with consent, or in hot pursuit. The document notes that while racial profiling is not official policy, some believe it occurs unofficially when race rather than evidence prompts police action.
State v. ulvinen

Helen Ulvinen was convicted of first-degree murder for the killing of Carol Hoffman by Helen's son David Hoffman. David strangled and dismembered his wife Carol. He called his mother Helen to watch the children while he disposed of Carol's body. The Minnesota Supreme Court reversed Helen's conviction. There was no evidence that Helen influenced David's decision to kill his wife. As David's parent, Helen was insulated by statute from guilt as an accomplice after the fact for her conduct. The evidence at best showed that Helen passively acquiesced to David's plan, which is not a criminal offense under Minnesota law.
State v. burrell

Marc Burrell was convicted of manslaughter after shooting and killing Douglas Saari at a house. Burrell claimed he had a lazy eye that made it difficult to see anything to his left. He appealed the conviction, arguing the jury was not instructed that they had to find he voluntarily pulled the trigger. The New Hampshire Supreme Court affirmed the conviction, holding that criminal liability only requires the overall conduct include a voluntary act, not that every single preceding act be voluntary as well.
George lee mims, sr. v. us

George Lee Mims, Sr. was convicted of attempting to rob a bank along with accomplices. They procured weapons and disguises and made two trips to the bank when it was closed. On the second trip, one accomplice placed a gun to a bank employee's head but they left without entering. The Supreme Court reversed Mims' conviction, finding not enough evidence that their conduct went beyond mere preparation to the actual attempted commission of the robbery. The jury was not properly instructed on what constitutes an attempted robbery.
Investigation powerpoint

The document outlines the basics of a crime scene investigation, including the typical roles and processes involved. It discusses the three types of crime scenes (primary, secondary, tertiary), three types of evidence (testimonial, physical, trace), and the four steps CSIs follow (securing the scene, documentation, evidence collection, lab processing). It also describes the five key personnel that may be involved - CSI unit, police officers, district attorney, specialists, and detectives.
State v. snowden

Raymond Snowden met Cora Dean at a club and they left together. They argued over cab fare, Snowden pulled out a knife and cut her throat, severing her spinal cord and causing her death. Snowden then disposed of evidence from the crime. He pled guilty to murder in the first degree. The Supreme Court affirmed the district court's decision, finding that Snowden had sufficient time after meeting Dean to develop the desire to kill her, showing malice aforethought. The court reasoned that Snowden's acts met the statutory definition of deliberate and premeditated murder.
Crimescenebasics ppt

The document provides information about crime scenes and evidence collection. It defines key crime scene terms like primary and secondary crime scenes. It describes different types of evidence like testimonial, physical, and trace evidence. It outlines the crime scene investigation process from interviewing witnesses to documenting and processing the scene to collect evidence. It also lists different forensic science disciplines involved in analyzing evidence and their roles.
State v. ninham

Omer Ninham, who was 14 years old at the time, was convicted of first-degree intentional homicide for his role in beating a man and causing him to fall to his death. He was sentenced to life in prison without the possibility of parole. Ninham appealed his sentence, arguing that it was unconstitutional punishment for a 14-year-old and excessively harsh. The Supreme Court affirmed the lower court's ruling, finding that a life sentence without parole for a 14-year-old convicted of homicide was not categorically unconstitutional. The Court also determined that Ninham's sentence was not disproportionate to his crime and that his family's religious beliefs were not improperly considered in sentencing.
Fs Ch 6

Crime scene reconstruction relies on analyzing physical evidence and witness statements to determine the likely sequence of events surrounding a crime. It requires objectivity from investigators to avoid biases influencing their analysis and conclusions. Deductive and inductive reasoning are used to draw conclusions from evidence, and theories must be falsifiable based on evidence. Limitations include incomplete information and potential biases. A team approach combines different expertise to answer the key questions of who, what, where, when and how regarding the crime. Physical evidence plays a crucial role in supporting or contradicting accounts, and establishing chains of custody is important. Reconstructions can test theories by reenacting possible crime sequences.
State v. stark

Calvin Stark tested positive for HIV in 1988 and was informed by his doctor that he must disclose his status before engaging in sexual activity. Despite this, Stark had unprotected sex with three victims between 1989-1990 without informing them of his HIV status. He was charged with three counts of assault. At his bench trials, Stark was found guilty on all counts. The court affirmed the convictions, finding that the evidence - including Stark being counseled on safe sex practices and testimony from his victims and neighbors - supported the element of intent to inflict bodily harm.
Proposal Report of white-collar crime

This document provides an overview of a research proposal on white-collar crime. It discusses definitions of white-collar crime, types of white-collar crimes, and theoretical frameworks for studying white-collar crime, including criminal-based and crime-based viewpoints. It also outlines objectives, research questions, and methodology for the proposed study, which will examine differences in jail adjustment between white-collar criminals and other criminals based on factors like age, socioeconomic status, criminal history, race, gender, and mental illness. The study aims to test two hypotheses: 1) that white-collar criminals will fare worse in jail than other criminals, or 2) that white-collar criminals will fare better in jail than other criminals.
Criminal Trial Process

The document provides an overview of the criminal trial process in New South Wales, Australia. It discusses the different courts' jurisdictions and the types of cases they hear. For example, it states that the Local Court hears summary offenses and conducts committal hearings, while the Supreme Court hears the most serious crimes. It also outlines key aspects of the criminal trial process like pleas and charge negotiation, the use of evidence, and the roles of legal personnel and juries. Overall, the document serves as a reference guide to the New South Wales criminal justice system.
Prison management system

1) The Prison Department of Maharashtra implemented a Prison Management System (PMS) at two Mumbai prisons as a pilot project in 2010 to automate prisoner record keeping and other functions.
2) However, the PMS faced various operational challenges at Arthur Road Prison related to data integration and reporting. It also lacked support after contracts ended.
3) As a result, the department is now evaluating other vendor solutions like those from Goa Electronics and NIC before expanding computerization to other prisons in the state.
"Transformando el Conocimiento Empresarial en Resultados" - Ibm i2

El documento describe cómo i2 se utiliza para el análisis de inteligencia por agencias gubernamentales y empresas privadas. i2 ayuda a visualizar relaciones complejas entre personas, lugares, cosas, fechas y eventos a través de diferentes tipos de análisis como análisis de redes sociales y geoespacial. También se utiliza para investigaciones de fraude en múltiples industrias como seguros, telecomunicaciones y minoristas.
COMUNICADO 333-2023

FGJEM, CONAHO Y SS, DETIENEN A UN PRESUNTO LÍDER DE GRUPO CRIMINAL, GENERADOR DE VIOLENCIA EN TOLUCA
Criminal Investigations (Part One)

This document provides an overview of law enforcement procedures for criminal investigations, including preliminary investigations, securing crime scenes, collecting evidence, and forensic analysis techniques. It discusses protocols for responding to and documenting crime scenes, as well as collecting trace evidence like fingerprints, ballistics, and DNA. Advanced technologies like AFIS, NIBIN, and superglue fuming have improved the ability to identify suspects and link crimes through physical evidence analysis.
State v. jantzi

Peter Jantzi accompanies Diane Anderson to her estranged husband Rex Anderson's house and lets the air out of the tires of Rex's van. Rex chases Peter down a bicycle path and jumps on him, getting stabbed in the abdomen by Peter's knife. Peter is convicted of assault in the 2nd degree. The Court of Appeals affirms the conviction but modifies it to assault in the 3rd degree and remands for resentencing, finding that while Peter knew he had a weapon and an injury could occur, he did not intend to stab Rex.
INTERPOL(FS).pdf

INTERPOL is the world's largest international police organization, with 196 member nations. It facilitates international police cooperation and crime control. INTERPOL provides secure communication channels and access to databases containing criminal intelligence to support international investigations. It also offers specialized police training and operational support to address priority crime areas like drugs, fugitives, terrorism, and human trafficking. Ultimately, INTERPOL aims to create a safer world by enabling law enforcement agencies to combat crime across international borders.
Law Relating to Culpable Homicide & Murder in India.

This document provides an overview of homicide laws in India. It defines different types of homicide such as culpable homicide, murder, and exceptions. Culpable homicide is the killing of a human being without intent to cause death. Murder is a more serious form requiring intent to kill. Lawful homicide includes cases done to uphold the law or in self-defense. Unlawful types include culpable homicide, murder, suicide and homicide by negligent acts. The key aspects of murder under IPC Section 300 are discussed along with illustrations.
Snowden slides

The document discusses the choices facing the US intelligence community in the aftermath of the Edward Snowden leaks. It notes that intelligence community members believe they are exempt from normal societal rules. While most citizens feel Snowden should have acted differently, they are not overly bothered by government surveillance. The document argues that the intelligence community should make a deal to bring Snowden back from exile in exchange for no longer posing a national security threat, in order to demonstrate intelligence and avoid further damaging leaks to US adversaries.
More Related Content
What's hot
Chapter6

The document discusses the history and goals of the US prison system. It describes how prisons evolved from focusing solely on custody in the 1940s-50s to incorporating rehabilitation programs in the 1960s-70s. The three main models of incarceration are the custodial model which focuses on incapacitation and deterrence, the rehabilitation model which emphasizes treatment, and the reintegration model prioritizing community supervision. The document also outlines trends in incarceration rates and prison populations as well as strategies for dealing with overcrowding issues.
Fourth Amendment notes

This document summarizes key aspects of the 4th Amendment regarding search and seizure. It outlines the differences between probable cause and reasonable suspicion, with probable cause requiring a likelihood of criminal activity and reasonable suspicion only requiring articulable facts. It also discusses allowable warrantless searches incident to arrest, with consent, or in hot pursuit. The document notes that while racial profiling is not official policy, some believe it occurs unofficially when race rather than evidence prompts police action.
State v. ulvinen

Helen Ulvinen was convicted of first-degree murder for the killing of Carol Hoffman by Helen's son David Hoffman. David strangled and dismembered his wife Carol. He called his mother Helen to watch the children while he disposed of Carol's body. The Minnesota Supreme Court reversed Helen's conviction. There was no evidence that Helen influenced David's decision to kill his wife. As David's parent, Helen was insulated by statute from guilt as an accomplice after the fact for her conduct. The evidence at best showed that Helen passively acquiesced to David's plan, which is not a criminal offense under Minnesota law.
State v. burrell

Marc Burrell was convicted of manslaughter after shooting and killing Douglas Saari at a house. Burrell claimed he had a lazy eye that made it difficult to see anything to his left. He appealed the conviction, arguing the jury was not instructed that they had to find he voluntarily pulled the trigger. The New Hampshire Supreme Court affirmed the conviction, holding that criminal liability only requires the overall conduct include a voluntary act, not that every single preceding act be voluntary as well.
George lee mims, sr. v. us

George Lee Mims, Sr. was convicted of attempting to rob a bank along with accomplices. They procured weapons and disguises and made two trips to the bank when it was closed. On the second trip, one accomplice placed a gun to a bank employee's head but they left without entering. The Supreme Court reversed Mims' conviction, finding not enough evidence that their conduct went beyond mere preparation to the actual attempted commission of the robbery. The jury was not properly instructed on what constitutes an attempted robbery.
Investigation powerpoint

The document outlines the basics of a crime scene investigation, including the typical roles and processes involved. It discusses the three types of crime scenes (primary, secondary, tertiary), three types of evidence (testimonial, physical, trace), and the four steps CSIs follow (securing the scene, documentation, evidence collection, lab processing). It also describes the five key personnel that may be involved - CSI unit, police officers, district attorney, specialists, and detectives.
State v. snowden

Raymond Snowden met Cora Dean at a club and they left together. They argued over cab fare, Snowden pulled out a knife and cut her throat, severing her spinal cord and causing her death. Snowden then disposed of evidence from the crime. He pled guilty to murder in the first degree. The Supreme Court affirmed the district court's decision, finding that Snowden had sufficient time after meeting Dean to develop the desire to kill her, showing malice aforethought. The court reasoned that Snowden's acts met the statutory definition of deliberate and premeditated murder.
Crimescenebasics ppt

The document provides information about crime scenes and evidence collection. It defines key crime scene terms like primary and secondary crime scenes. It describes different types of evidence like testimonial, physical, and trace evidence. It outlines the crime scene investigation process from interviewing witnesses to documenting and processing the scene to collect evidence. It also lists different forensic science disciplines involved in analyzing evidence and their roles.
State v. ninham

Omer Ninham, who was 14 years old at the time, was convicted of first-degree intentional homicide for his role in beating a man and causing him to fall to his death. He was sentenced to life in prison without the possibility of parole. Ninham appealed his sentence, arguing that it was unconstitutional punishment for a 14-year-old and excessively harsh. The Supreme Court affirmed the lower court's ruling, finding that a life sentence without parole for a 14-year-old convicted of homicide was not categorically unconstitutional. The Court also determined that Ninham's sentence was not disproportionate to his crime and that his family's religious beliefs were not improperly considered in sentencing.
Fs Ch 6

Crime scene reconstruction relies on analyzing physical evidence and witness statements to determine the likely sequence of events surrounding a crime. It requires objectivity from investigators to avoid biases influencing their analysis and conclusions. Deductive and inductive reasoning are used to draw conclusions from evidence, and theories must be falsifiable based on evidence. Limitations include incomplete information and potential biases. A team approach combines different expertise to answer the key questions of who, what, where, when and how regarding the crime. Physical evidence plays a crucial role in supporting or contradicting accounts, and establishing chains of custody is important. Reconstructions can test theories by reenacting possible crime sequences.
State v. stark

Calvin Stark tested positive for HIV in 1988 and was informed by his doctor that he must disclose his status before engaging in sexual activity. Despite this, Stark had unprotected sex with three victims between 1989-1990 without informing them of his HIV status. He was charged with three counts of assault. At his bench trials, Stark was found guilty on all counts. The court affirmed the convictions, finding that the evidence - including Stark being counseled on safe sex practices and testimony from his victims and neighbors - supported the element of intent to inflict bodily harm.
Proposal Report of white-collar crime

This document provides an overview of a research proposal on white-collar crime. It discusses definitions of white-collar crime, types of white-collar crimes, and theoretical frameworks for studying white-collar crime, including criminal-based and crime-based viewpoints. It also outlines objectives, research questions, and methodology for the proposed study, which will examine differences in jail adjustment between white-collar criminals and other criminals based on factors like age, socioeconomic status, criminal history, race, gender, and mental illness. The study aims to test two hypotheses: 1) that white-collar criminals will fare worse in jail than other criminals, or 2) that white-collar criminals will fare better in jail than other criminals.
Criminal Trial Process

The document provides an overview of the criminal trial process in New South Wales, Australia. It discusses the different courts' jurisdictions and the types of cases they hear. For example, it states that the Local Court hears summary offenses and conducts committal hearings, while the Supreme Court hears the most serious crimes. It also outlines key aspects of the criminal trial process like pleas and charge negotiation, the use of evidence, and the roles of legal personnel and juries. Overall, the document serves as a reference guide to the New South Wales criminal justice system.
Prison management system

1) The Prison Department of Maharashtra implemented a Prison Management System (PMS) at two Mumbai prisons as a pilot project in 2010 to automate prisoner record keeping and other functions.
2) However, the PMS faced various operational challenges at Arthur Road Prison related to data integration and reporting. It also lacked support after contracts ended.
3) As a result, the department is now evaluating other vendor solutions like those from Goa Electronics and NIC before expanding computerization to other prisons in the state.
"Transformando el Conocimiento Empresarial en Resultados" - Ibm i2

El documento describe cómo i2 se utiliza para el análisis de inteligencia por agencias gubernamentales y empresas privadas. i2 ayuda a visualizar relaciones complejas entre personas, lugares, cosas, fechas y eventos a través de diferentes tipos de análisis como análisis de redes sociales y geoespacial. También se utiliza para investigaciones de fraude en múltiples industrias como seguros, telecomunicaciones y minoristas.
COMUNICADO 333-2023

FGJEM, CONAHO Y SS, DETIENEN A UN PRESUNTO LÍDER DE GRUPO CRIMINAL, GENERADOR DE VIOLENCIA EN TOLUCA
Criminal Investigations (Part One)

This document provides an overview of law enforcement procedures for criminal investigations, including preliminary investigations, securing crime scenes, collecting evidence, and forensic analysis techniques. It discusses protocols for responding to and documenting crime scenes, as well as collecting trace evidence like fingerprints, ballistics, and DNA. Advanced technologies like AFIS, NIBIN, and superglue fuming have improved the ability to identify suspects and link crimes through physical evidence analysis.
State v. jantzi

Peter Jantzi accompanies Diane Anderson to her estranged husband Rex Anderson's house and lets the air out of the tires of Rex's van. Rex chases Peter down a bicycle path and jumps on him, getting stabbed in the abdomen by Peter's knife. Peter is convicted of assault in the 2nd degree. The Court of Appeals affirms the conviction but modifies it to assault in the 3rd degree and remands for resentencing, finding that while Peter knew he had a weapon and an injury could occur, he did not intend to stab Rex.
INTERPOL(FS).pdf

INTERPOL is the world's largest international police organization, with 196 member nations. It facilitates international police cooperation and crime control. INTERPOL provides secure communication channels and access to databases containing criminal intelligence to support international investigations. It also offers specialized police training and operational support to address priority crime areas like drugs, fugitives, terrorism, and human trafficking. Ultimately, INTERPOL aims to create a safer world by enabling law enforcement agencies to combat crime across international borders.
Law Relating to Culpable Homicide & Murder in India.

This document provides an overview of homicide laws in India. It defines different types of homicide such as culpable homicide, murder, and exceptions. Culpable homicide is the killing of a human being without intent to cause death. Murder is a more serious form requiring intent to kill. Lawful homicide includes cases done to uphold the law or in self-defense. Unlawful types include culpable homicide, murder, suicide and homicide by negligent acts. The key aspects of murder under IPC Section 300 are discussed along with illustrations.
What's hot (20)
"Transformando el Conocimiento Empresarial en Resultados" - Ibm i2

"Transformando el Conocimiento Empresarial en Resultados" - Ibm i2
Law Relating to Culpable Homicide & Murder in India.

Law Relating to Culpable Homicide & Murder in India.
Viewers also liked
Snowden slides

The document discusses the choices facing the US intelligence community in the aftermath of the Edward Snowden leaks. It notes that intelligence community members believe they are exempt from normal societal rules. While most citizens feel Snowden should have acted differently, they are not overly bothered by government surveillance. The document argues that the intelligence community should make a deal to bring Snowden back from exile in exchange for no longer posing a national security threat, in order to demonstrate intelligence and avoid further damaging leaks to US adversaries.
Elon musk

Elon Musk is a South African-born American entrepreneur and industrial designer. He is the founder, CEO and Chief Engineer at SpaceX, founder of Tesla, and co-founder of Neuralink and The Boring Company. Musk was born in South Africa in 1971 and moved to Canada at age 18. He graduated from the University of Pennsylvania with a degree in physics and economics. He co-founded Zip2 and later made millions from its sale to Compaq. He then co-founded X.com which merged with Confinity to form PayPal, which was later acquired by eBay for $1.5 billion. In 2002 Musk founded SpaceX, with the goal of reducing space transportation costs to enable the
Elon Musk

Elon Musk is a South African-born American entrepreneur and industrialist who founded SpaceX, Tesla Motors, and Neuralink. He is the CEO of both SpaceX and Tesla, where he oversees the development of advanced rockets, electric vehicles, and brain-computer interfaces. His ultimate goal is to make humanity a multi-planetary species by establishing human colonies on Mars.
Elon Musk- Visionary, Leader, Entrepreneur

A leadership-themed presentation that explores Elon Musk's incredible achievements and his ability to lead others in his pursuit of a better future.
Having founded five companies and being the CEO of the leading fully electric company (Tesla) and the first private spaceflight company (SpaceX), Musk is truly one of the most extraordinary humans alive today.
Entrepreneur Elon musk

This slide is about a great entrepreneur named Elon Musk. He is the founder of Tesla Motors, SpaceX, Hyperloop, SolarCity and many others. This man is dedicated to change our society with "green energy".
Viewers also liked (6)
Similar to Snowden -Hero OR Traitor
Reply to below posting in a paragraph of at least five sentences by.docx

Reply to below posting in a paragraph of at least five sentences by asking questions, reflecting on your own experience, challenging assumptions, pointing out something new you learned, offering suggestions.
1)
Edward Snowden is a hero or a criminal
Edward Snowden, a low-level private contractor to the US-based National Security Agency (NSA), breached moral confidentiality and secrecy obligations by engaging in unauthorized accessing, retrieving and/or releasing of a large volume of confidential data from NSA to the press and, possibly, to foreign powers. Edward Snowden (born June 21, 1983) is a computer programmer who worked as a subcontractor for the National Security Agency (NSA). Snowden collected top-secret documents regarding NSA domestic surveillance practices that he found disturbing and leaked them. During his years of IT work, Snowden had noticed the far reach of the NSA's everyday surveillance.
“While working for Booz Allen, Snowden began copying top-secret NSA documents.”
(Biography.com, 2019) After he had compiled a large store of documents, Snowden told his NSA supervisor that he needed a leave of absence for medical reasons, stating he had been diagnosed with epilepsy. On May 20, 2013, Snowden took a flight to Hong Kong, China. (Biography.com, 2019)
As mentioned by author Rouse in her article referring, he leaked and also raised questions about data sovereignty and how secure a company's data really is if it's stored by a cloud provider based in the United States. In 2014, almost 90% of respondents to a survey commissioned by security consultancy NTT Communications said they were changing their cloud-buying behavior as a result of Snowden’s revelations. Just over half said they are carrying out greater due diligence on cloud providers than ever before, and more than four-fifths responded that they would seek out more training on data protection laws. (Rouse, 2015)
Snowden has also been accused of irregularities under the Espionage Law for knowingly discovering mysterious national security data. When these charges were opened, newspapers quickly guaranteed that he was accused of undercover work. Such cases are not exactly accurate. Undercover work is commonly characterized as
"the act of spying ... to acquire data on plans and exercises, particularly from an external government."
(Richa, (2015) Although there have been hypotheses as to whether the nations to which Snowden fled (Russia and China) have kept their records, there is still no evidence that he has continued to his advantage or helped them easily as would be the case. The situation with great recognition. (Richa, (2015)
Contrary to Snowden’s claim about wanting to stand up for his fellow Americans, the information he leaked actually created more harm than good.
“The majority of the information that he shared is about the U.S. spying on foreign nations and not its domestic operations.”
(Rachel Segal, 2019) As such, he risked damaging America’s relatio.
Case 9 Security vs Privacy

The document discusses various revelations about NSA surveillance programs from documents leaked by Edward Snowden. It describes how the NSA collects vast amounts of metadata from telecommunications companies like Verizon on all Americans. It also discusses the PRISM program through which the NSA gains access to data from major tech companies. The document outlines the Boundless Informant tool used by the NSA to track global surveillance and maps which countries have the most metadata collected. It discusses the debate around whether Snowden should be considered a whistleblower or leaker and the espionage charges filed against him.
Edward J. Snowden, the thirty-year-old former National Security Agen.docx

Edward J. Snowden, the thirty-year-old former National Security Agency contractor who handed over a treasure trove of classified documents about U.S. government surveillance to the Washington Post and Britain's Guardian, is a hero to some and a traitor to others. He claims to have acted out of a sense of outrage over the NSA's indiscriminate collection of the phone and internet records of Americans, decrying the danger such intrusive government oversight poses to democracy and privacy. Snowden subsequently fled to Hong Kong, and from there to Moscow. His eventual destination appears to be Ecuador, Cuba, or Venezuela.
Snowden's efforts to elude U.S. authorities cast an ambiguous light on his motives; the countries where he has sought refuge are not known for upholding the sort of democratic values he claims to be defending. While demanding accountability from the U.S. government, he appears to be seeking immunity for his own actions. Snowden's purposes and fate, however, should be of secondary concern. However misguided his actions may have been, they have reopened a much-needed debate about the reach and authority of what is often called the National Security State. While defending the NSA programs, even President Barack Obama seems to welcome that debate. "You can't have 100 percent security and also then have 100 percent privacy and zero inconvenience," Obama noted when asked about Snowden's leaks. "We're going to have to make some choices as a society. ... There are trade-offs involved."
Administration officials and members of Congress say the government's extensive surveillance programs are crucial to preventing terrorist attacks, and that Snowden has done real damage to efforts to keep Americans safe. Because almost all the relevant information remains classified, it is difficult to assess that claim. NSA officials have now promised to make public details of some of the dozens of terrorist plots they say the massive data-collection effort, called Prism, has helped thwart. That sort of disclosure is long overdue. Although Prism was approved by the Foreign Intelligence Surveillance Act court and is monitored by the intelligence committees of Congress, many Americans were shocked to learn that the government now stores their phone and internet records for possible use in future investigations. While the government is prohibited from listening to the tracked calls, it uses sophisticated algorithms to trace calling patterns. If a series of related calls seems suspicious, the NSA or FBI then gets a warrant from the FISA court to investigate further. No abuse of those procedures has come to light. Still, the mere existence of such records in the government's hands, information that might easily be exploited for political purposes, should concern every American.
It is axiomatic that fighting clandestine terrorist groups requires clandestine methods. Sources and allies must be protected; in preemptive actions the element of surprise must be prese.
Article CritiqueThis assignment provides you with an opportunity t.docx

Article Critique
This assignment provides you with an opportunity to read an article and then to share your thoughts about the article by critiquing the details, including the decisions made.In order to access the resource below, you must first log into the myCSU Student Portal and access the AcademicOneFile database within the CSU Online Library.This article includes details and assertions about the ethical choices/decisions made by Edward J. Snowden, a formerNational Security Agency (NSA) contractor. Here is the reference citation for the article:Securing our liberty. (2013). Commonweal, 140(12), 5.After reading the article, draft a two-page response by discussing the U.S. government’s decision to acquire phone andinternet data without disclosing its intentions to citizens. For this assignment, consider the NSA as an organization (i.e.,business) and Snowden as a manager. How have the decisions of this event impacted the fairness of the U.S.government, its citizens, and Snowden? How did ethics, perhaps, influence Snowden’s decision to leak information? Inthis event, what is the greater good and also the consequences/sacrifices of that greater good? Based on the details ofthis event, what can we learn about making important decisions as a leader and manager?This event was covered by several news and media organizations, so there should be plenty of articles in the library.Conduct a bit more research in the online library related to this event involving Edward Snowden and the U.S.government—see what else you can discover about the event to determine an appropriate punishment, if any, forSnowden’s conduct. Include at least one additional source from the library in your response.The purpose of this assignment is for you to think critically about managers (and other leaders) making importantdecisions, and the process managers use to make important decisions. Consider how important it is to collect all of thefacts before making an important decision, such as those involving fairness and ethics.Use APA Style to format your response. Proofread your work, and submit it in Blackboard for grading.Information about accessing the Blackboard Grading Rubric for this assignment is provided below.
Below is the article.
Edward J. Snowden, the thirty-year-old former National Security Agency contractor who handed over a treasure trove of classified documents about U.S. government surveillance to the Washington Post and Britain's Guardian, is a hero to some and a traitor to others. He claims to have acted out of a sense of outrage over the NSA's indiscriminate collection of the phone and internet records of Americans, decrying the danger such intrusive government oversight poses to democracy and privacy. Snowden subsequently fled to Hong Kong, and from there to Moscow. His eventual destination appears to be Ecuador, Cuba, or Venezuela.
Snowden's efforts to elude U.S. authorities cast an ambiguous light on his motives; the countries where he has sought refuge.
(Lim Jun Hao) G8 Individual Essay for BGS

The key issues at the crux of the Snowden affair are government surveillance and its impact on citizens' privacy and democracy. The main stakeholders are governments who conduct surveillance in the name of national security, citizens whose data is being collected, and large corporations that assist with data collection. Citizens should be concerned because ubiquitous surveillance could threaten democratic ideals and turn countries into police states, especially if data falls into the wrong hands. While surveillance may be necessary to combat terrorism, current methods have flaws and do not respect citizens' right to privacy or representation.
The Operations Of The National Security Agency

The National Security Agency (NSA) has been a United States intelligence agency since 1952. It works under the Department of Defense to monitor communications and data from foreign intelligence sources around the world, including terrorist organizations. Many of the NSA's operations are secret, involving activities like electronic surveillance, phone record collection, and software hacking sanctioned by the government to protect national security. The agency uses these tactics to gather intelligence on foreign targets, though its surveillance of American citizens without warrants has also been controversial.
Final Copy Cyber Crime Research Essay

Edward Snowden leaked documents revealing the NSA was conducting mass surveillance programs like PRISM to collect data on American and foreign citizens. This raised debates on privacy violations versus national security. The document argues mass surveillance is justified for precautionary reasons in dealing with cyber threats from non-state actors and hostile states that exploit ambiguity. It also claims targeted surveillance would be ineffective given how cyber attacks can emerge from anywhere without links to sponsors. While revealing secret programs, mass surveillance has been publicly known and legally permitted for decades through laws like the Patriot Act.
Argument for Snowden Clemency

Paper written to present a case for Edward Snowden's clemency, an assignment completed for a Business Ethics course.
Securing our libertyCommonweal. 140.12 (July 12, 2013) p5.Cop.docx

Securing our liberty
Commonweal. 140.12 (July 12, 2013): p5.
Copyright: COPYRIGHT 2013 Commonweal Foundation
http://www.cweal.org/
Listen
Full Text:
Edward J. Snowden, the thirty-year-old former National Security Agency contractor who handed over a treasure trove of classified documents about U.S. government surveillance to the Washington Post and Britain's Guardian, is a hero to some and a traitor to others. He claims to have acted out of a sense of outrage over the NSA's indiscriminate collection of the phone and internet records of Americans, decrying the danger such intrusive government oversight poses to democracy and privacy. Snowden subsequently fled to Hong Kong, and from there to Moscow. His eventual destination appears to be Ecuador, Cuba, or Venezuela.
Snowden's efforts to elude U.S. authorities cast an ambiguous light on his motives; the countries where he has sought refuge are not known for upholding the sort of democratic values he claims to be defending. While demanding accountability from the U.S. government, he appears to be seeking immunity for his own actions. Snowden's purposes and fate, however, should be of secondary concern. However misguided his actions may have been, they have reopened a much-needed debate about the reach and authority of what is often called the National Security State. While defending the NSA programs, even President Barack Obama seems to welcome that debate. "You can't have 100 percent security and also then have 100 percent privacy and zero inconvenience," Obama noted when asked about Snowden's leaks. "We're going to have to make some choices as a society. ... There are trade-offs involved."
Administration officials and members of Congress say the government's extensive surveillance programs are crucial to preventing terrorist attacks, and that Snowden has done real damage to efforts to keep Americans safe. Because almost all the relevant information remains classified, it is difficult to assess that claim. NSA officials have now promised to make public details of some of the dozens of terrorist plots they say the massive data-collection effort, called Prism, has helped thwart. That sort of disclosure is long overdue. Although Prism was approved by the Foreign Intelligence Surveillance Act court and is monitored by the intelligence committees of Congress, many Americans were shocked to learn that the government now stores their phone and internet records for possible use in future investigations. While the government is prohibited from listening to the tracked calls, it uses sophisticated algorithms to trace calling patterns. If a series of related calls seems suspicious, the NSA or FBI then gets a warrant from the FISA court to investigate further. No abuse of those procedures has come to light. Still, the mere existence of such records in the government's hands, information that might easily be exploited for political purposes, should concern every American.
It is axiomatic that fighting clande.
Case study: Edward Snowden

A summary of an article describing some of the effects of Edward Snowden's revelations on the process of performing Background Investigations (BI) into prospective US-government staff.
Krempley 1POL 300GoogleMulti-National Corporations, Inter.docx

Krempley 1
POL 300
Google/Multi-National Corporations, International Surveillance, and Human Rights
Abstract
The many news reports on cyber security, identity theft, Wikileaks, and NSA intelligence gathering programs over the past few years have shown the international community that the World Wide Web is anything but a safe place to store sensitive information, or any information for that matter. This study will examine how closely multi-national corporations in the information technology sector, such as Google, are involved with national governments on these issues. The study will analyze events in the U.S. and China and attempt to uncover whether or not these have directly infringed upon peoples’ basic human rights.
Question
With emerging information regarding the NSA's PRISM program and China's "Golden Shield Project", has either country directly infringed on peoples' basic human rights?
Hypothesis
As more information is uncovered regarding the true nature of the aims of these internationally implemented programs, it has become increasingly clear that there have been multiple violations of peoples' human rights in both the United States and China with their respective monitoring programs.
The NSA and the PRISM Project
"Since September 11th, 2001, the United States government has dramatically increased the ability of its intelligence agencies to collect and investigate information on both foreign subjects and US citizens. Some of these surveillance programs, including a secret program called PRISM, capture the private data of citizens who are not suspected of any connection to terrorism or any wrongdoing." (Sottek&Kopstein, 2013) Under the guise of a "war on terror", the United States government has consistently upped its efforts to gather as much information as possible regarding the activities of international and domestic citizens alike. Most U.S. citizens were wholly unaware that the government had been running a secret filtration program to determine threat levels of individual citizens both domestically and abroad. This PRISM project and its intentions have recently been leaked in the Edward Snowden fiasco that took the country and the media by storm.
"PRISM is a tool used by the US National Security Agency (NSA) to collect private electronic data belonging to users of major internet services like Gmail, Facebook, Outlook, and others. It’s the latest evolution of the US government’s post-9/11 electronic surveillance efforts, which began under President Bush with the Patriot Act, and expanded to include the Foreign Intelligence Surveillance Act (FISA) enacted in 2006 and 2007." (Sottek&Kopstein, 2013) FISA, "...may be the most powerful court you have never heard of -- operating out of a bunker-like complex blocks from the Capitol and the White House -- sealed tightly to prevent eavesdropping.The FISA Court's larger mission is to decide whether to grant certain types of government requests-- wiretapping, data anal ...
Edward Snowden was a whistleblower and former NSA contractor, in the.docx

Edward Snowden was a whistleblower and former NSA contractor, in the employment of Booz Allen Hamilton. In 2013, Snowden, left his home in Hawaii and traveled to Hong Kong for the express purpose of leaking top secret document to a journalist there. There is no question, when Edward Snowden leaked US intelligence documents he revealed the shocking extent of global mass surveillance in cyberspace. He showed how governments were secretly hoovering up huge chunks of our personal communications, including private emails, phone locations, web histories and so much more. All without our consent. Whether you believe Snowden to be a traitor, or a patriot and whistleblower, he certainly changed the world with his revelations. He has sparked a global debate, which initiated the passage of new laws intended to increase our protection from government prying. For the first time in 40 years, the United States passed new laws to control government surveillance. Globally, technology companies have stepped up efforts to personal information. Develop a research paper as to the laws that Snowden broke, whether what he did was right, wrong or necessary. Debate whether Snowden placed our country at risk by revealing US surveillance techniques, or whether he has made private citizen more aware of government snooping. Conclude by giving a consensus of the group as to whether Snowden is a patriot or traitor, and explain whether Snowden should be pardoned and permitted to return to the United States.
.
Similar to Snowden -Hero OR Traitor (12)
Reply to below posting in a paragraph of at least five sentences by.docx

Reply to below posting in a paragraph of at least five sentences by.docx
Edward J. Snowden, the thirty-year-old former National Security Agen.docx

Edward J. Snowden, the thirty-year-old former National Security Agen.docx
Article CritiqueThis assignment provides you with an opportunity t.docx

Article CritiqueThis assignment provides you with an opportunity t.docx
Securing our libertyCommonweal. 140.12 (July 12, 2013) p5.Cop.docx

Securing our libertyCommonweal. 140.12 (July 12, 2013) p5.Cop.docx
Krempley 1POL 300GoogleMulti-National Corporations, Inter.docx

Krempley 1POL 300GoogleMulti-National Corporations, Inter.docx
Edward Snowden was a whistleblower and former NSA contractor, in the.docx

Edward Snowden was a whistleblower and former NSA contractor, in the.docx
Recently uploaded
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-und-domino-lizenzkostenreduzierung-in-der-welt-von-dlau/
DLAU und die Lizenzen nach dem CCB- und CCX-Modell sind für viele in der HCL-Community seit letztem Jahr ein heißes Thema. Als Notes- oder Domino-Kunde haben Sie vielleicht mit unerwartet hohen Benutzerzahlen und Lizenzgebühren zu kämpfen. Sie fragen sich vielleicht, wie diese neue Art der Lizenzierung funktioniert und welchen Nutzen sie Ihnen bringt. Vor allem wollen Sie sicherlich Ihr Budget einhalten und Kosten sparen, wo immer möglich. Das verstehen wir und wir möchten Ihnen dabei helfen!
Wir erklären Ihnen, wie Sie häufige Konfigurationsprobleme lösen können, die dazu führen können, dass mehr Benutzer gezählt werden als nötig, und wie Sie überflüssige oder ungenutzte Konten identifizieren und entfernen können, um Geld zu sparen. Es gibt auch einige Ansätze, die zu unnötigen Ausgaben führen können, z. B. wenn ein Personendokument anstelle eines Mail-Ins für geteilte Mailboxen verwendet wird. Wir zeigen Ihnen solche Fälle und deren Lösungen. Und natürlich erklären wir Ihnen das neue Lizenzmodell.
Nehmen Sie an diesem Webinar teil, bei dem HCL-Ambassador Marc Thomas und Gastredner Franz Walder Ihnen diese neue Welt näherbringen. Es vermittelt Ihnen die Tools und das Know-how, um den Überblick zu bewahren. Sie werden in der Lage sein, Ihre Kosten durch eine optimierte Domino-Konfiguration zu reduzieren und auch in Zukunft gering zu halten.
Diese Themen werden behandelt
- Reduzierung der Lizenzkosten durch Auffinden und Beheben von Fehlkonfigurationen und überflüssigen Konten
- Wie funktionieren CCB- und CCX-Lizenzen wirklich?
- Verstehen des DLAU-Tools und wie man es am besten nutzt
- Tipps für häufige Problembereiche, wie z. B. Team-Postfächer, Funktions-/Testbenutzer usw.
- Praxisbeispiele und Best Practices zum sofortigen Umsetzen
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
Climate Impact of Software Testing at Nordic Testing Days

My slides at Nordic Testing Days 6.6.2024
Climate impact / sustainability of software testing discussed on the talk. ICT and testing must carry their part of global responsibility to help with the climat warming. We can minimize the carbon footprint but we can also have a carbon handprint, a positive impact on the climate. Quality characteristics can be added with sustainability, and then measured continuously. Test environments can be used less, and in smaller scale and on demand. Test techniques can be used in optimizing or minimizing number of tests. Test automation can be used to speed up testing.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

ここ3000字までしか入らないけどタイトルの方がたくさん文字入ると思います。
Programming Foundation Models with DSPy - Meetup Slides

Prompting language models is hard, while programming language models is easy. In this talk, I will discuss the state-of-the-art framework DSPy for programming foundation models with its powerful optimizers and runtime constraint system.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
AI 101: An Introduction to the Basics and Impact of Artificial Intelligence

Imagine a world where machines not only perform tasks but also learn, adapt, and make decisions. This is the promise of Artificial Intelligence (AI), a technology that's not just enhancing our lives but revolutionizing entire industries.
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

ABSTRACT: A prima vista, un mattoncino Lego e la backdoor XZ potrebbero avere in comune il fatto di essere entrambi blocchi di costruzione, o dipendenze di progetti creativi e software. La realtà è che un mattoncino Lego e il caso della backdoor XZ hanno molto di più di tutto ciò in comune.
Partecipate alla presentazione per immergervi in una storia di interoperabilità, standard e formati aperti, per poi discutere del ruolo importante che i contributori hanno in una comunità open source sostenibile.
BIO: Sostenitrice del software libero e dei formati standard e aperti. È stata un membro attivo dei progetti Fedora e openSUSE e ha co-fondato l'Associazione LibreItalia dove è stata coinvolta in diversi eventi, migrazioni e formazione relativi a LibreOffice. In precedenza ha lavorato a migrazioni e corsi di formazione su LibreOffice per diverse amministrazioni pubbliche e privati. Da gennaio 2020 lavora in SUSE come Software Release Engineer per Uyuni e SUSE Manager e quando non segue la sua passione per i computer e per Geeko coltiva la sua curiosità per l'astronomia (da cui deriva il suo nickname deneb_alpha).
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/building-and-scaling-ai-applications-with-the-nx-ai-manager-a-presentation-from-network-optix/
Robin van Emden, Senior Director of Data Science at Network Optix, presents the “Building and Scaling AI Applications with the Nx AI Manager,” tutorial at the May 2024 Embedded Vision Summit.
In this presentation, van Emden covers the basics of scaling edge AI solutions using the Nx tool kit. He emphasizes the process of developing AI models and deploying them globally. He also showcases the conversion of AI models and the creation of effective edge AI pipelines, with a focus on pre-processing, model conversion, selecting the appropriate inference engine for the target hardware and post-processing.
van Emden shows how Nx can simplify the developer’s life and facilitate a rapid transition from concept to production-ready applications.He provides valuable insights into developing scalable and efficient edge AI solutions, with a strong focus on practical implementation.Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for life science domain, where you retriever information from biomedical knowledge graphs using LLMs to increase the accuracy and performance of generated answers
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
“I’m still / I’m still / Chaining from the Block”

“An Outlook of the Ongoing and Future Relationship between Blockchain Technologies and Process-aware Information Systems.” Invited talk at the joint workshop on Blockchain for Information Systems (BC4IS) and Blockchain for Trusted Data Sharing (B4TDS), co-located with with the 36th International Conference on Advanced Information Systems Engineering (CAiSE), 3 June 2024, Limassol, Cyprus.
Recently uploaded (20)
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU
Climate Impact of Software Testing at Nordic Testing Days

Climate Impact of Software Testing at Nordic Testing Days
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...
Programming Foundation Models with DSPy - Meetup Slides

Programming Foundation Models with DSPy - Meetup Slides
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
AI 101: An Introduction to the Basics and Impact of Artificial Intelligence

AI 101: An Introduction to the Basics and Impact of Artificial Intelligence
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

Cosa hanno in comune un mattoncino Lego e la backdoor XZ?
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for Life Science to increase LLM accuracy
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Snowden -Hero OR Traitor
- 2. Who is Edward Snowden Edward Joseph Snowden, June 21, 1983 (age 30), Wilmington, North Carolina Residence: Russia (temporary asylum) Nationality: American Occupation: System administrator Known for :Revealing details of classified United States government surveillance programs Criminal charge :Theft of government property, unauthorized communication of national defence information, and wilful communication of classified intelligence to an unauthorized person (June 2013). Awards :Sam Adams Award
- 3. How NSA Works? The NSA plays "three degrees of Kevin Bacon." e.g. With a phone with 260 contacts , 4,569,760,000 other people can be monitored Real Time Access to Phone and Internet Traffic The NSA asks for information companies already have The NSA sifts through everything that crosses the border. The NSA assumes you're foreign until proven otherwise
- 4. Issue? Guardian started publishing a series of exposes revealing NSA operated a major web of spying programs in May 2013. Snowden identity was revealed on 9th June.
- 5. Correctness of his actions NSA Claims wiretapping was not intrusion to US citizens Privacy but legitimate way to intercept terrorist activities or communications “ he wasn’t blowing the whistle on anything illegal; he was exposing something that failed to meet his own standards of propriety. The question, of course, is whether the government can function when all of its employees (and contractors) can take it upon themselves to sabotage the programs they don’t like. That’s what Snowden has done.”
- 6. Correctness of his actions Snowden contends that he simply wanted the public to know that government was watching and recording people who were doing no wrong. “to inform the public as to that which is done in their name and that which is done against them”
- 7. The NSA view of Americans What People Think Polls between June and August 2013
- 9. Discussions 1.What is the NSA mission? How deep is the involvement of corporate America in this whole scheme? Is Security of country is more important than Privacy? Credit:Mapsofworld
- 10. Widescreen Test Pattern (16:9) Aspect Ratio Test (Should appear circular) 4x3 16x9
