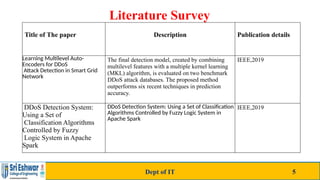
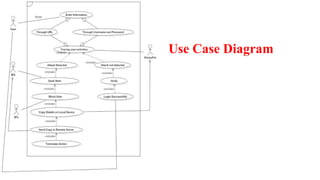
The document discusses a sketch-based defense system called 'Sky Shield' designed to mitigate application layer DDoS attacks, highlighting the growing sophistication and threats of bandwidth DDoS attacks. It outlines the vulnerabilities of the internet to such attacks and presents a methodology for detecting and addressing these threats using advanced techniques and features. The proposed system improves detection accuracy significantly compared to existing methods and incorporates modules for efficient traffic profile management and mitigation actions.
![SKY SHIELD: A SKETCH-BASED
DEFENSE SYSTEM AGAINST
APPLICATION LAYER DDOS ATTACKS
Batch Members:
SHRISENA M(722821205047)
SRIHARAN K(722821205048)
KAVIN K(722821205019)
KIRUTHICK SARAN D(722821205020)
Guided by,
Mr.G.Swaminathan,
Assistant Professor,
Sri Eshwar College of
Engineering
Sri Eshwar College of Engineering
(Autonomous) Coimbatore -
641202.
Department of Information Technology
Third Review [PHASE-I]](https://image.slidesharecdn.com/skyshieldasketchbaseddefensesystemagainstapplicationlayerddosattacks21-241119054335-bd719a6a/75/SKY-SHIELD-A-SKETCH-BASED-DEFENSE-SYSTEM-AGAINST-APPLICATION-LAYER-DDOS-ATTACKS-2-1-pptx-1-2048.jpg)