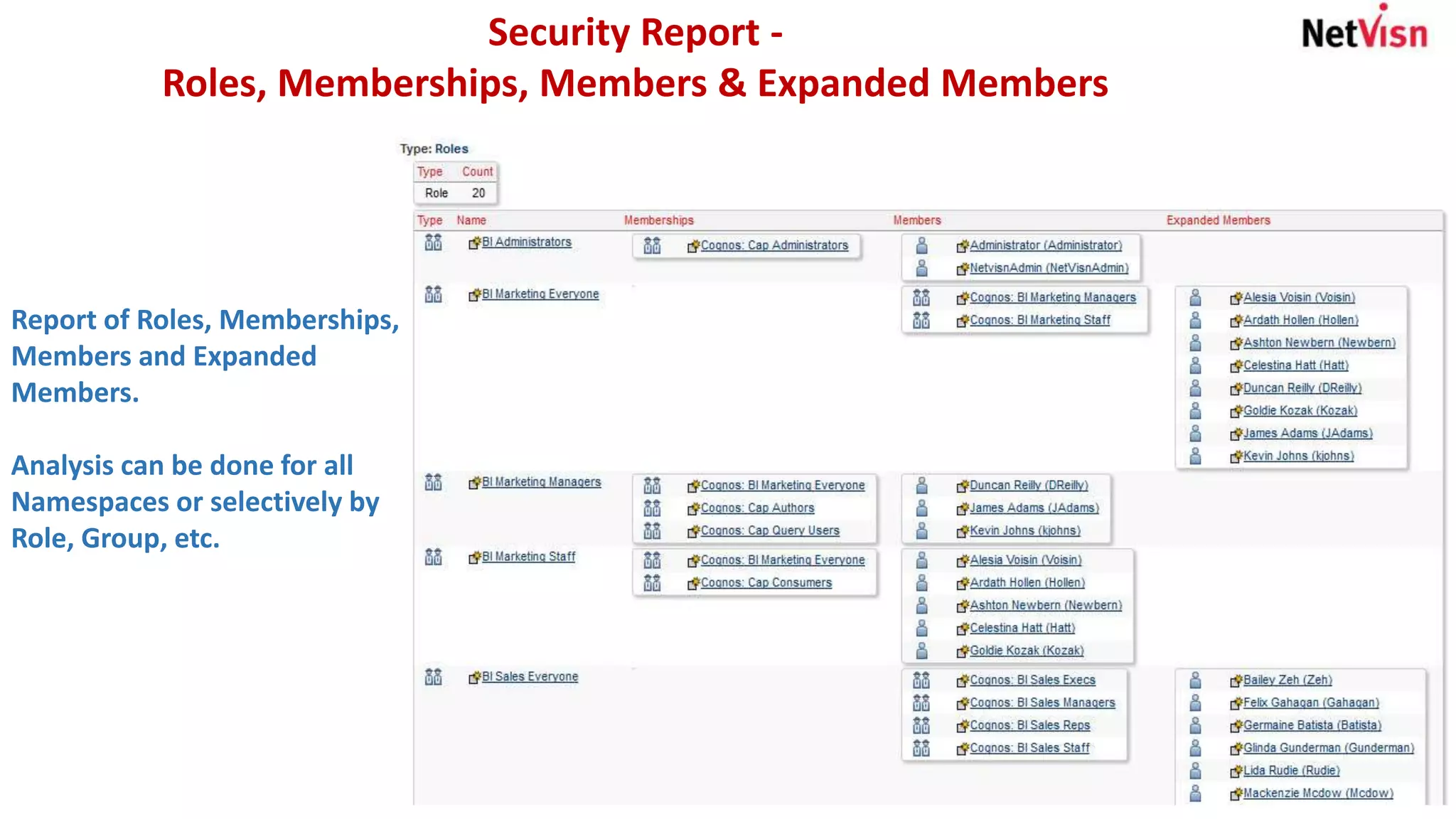
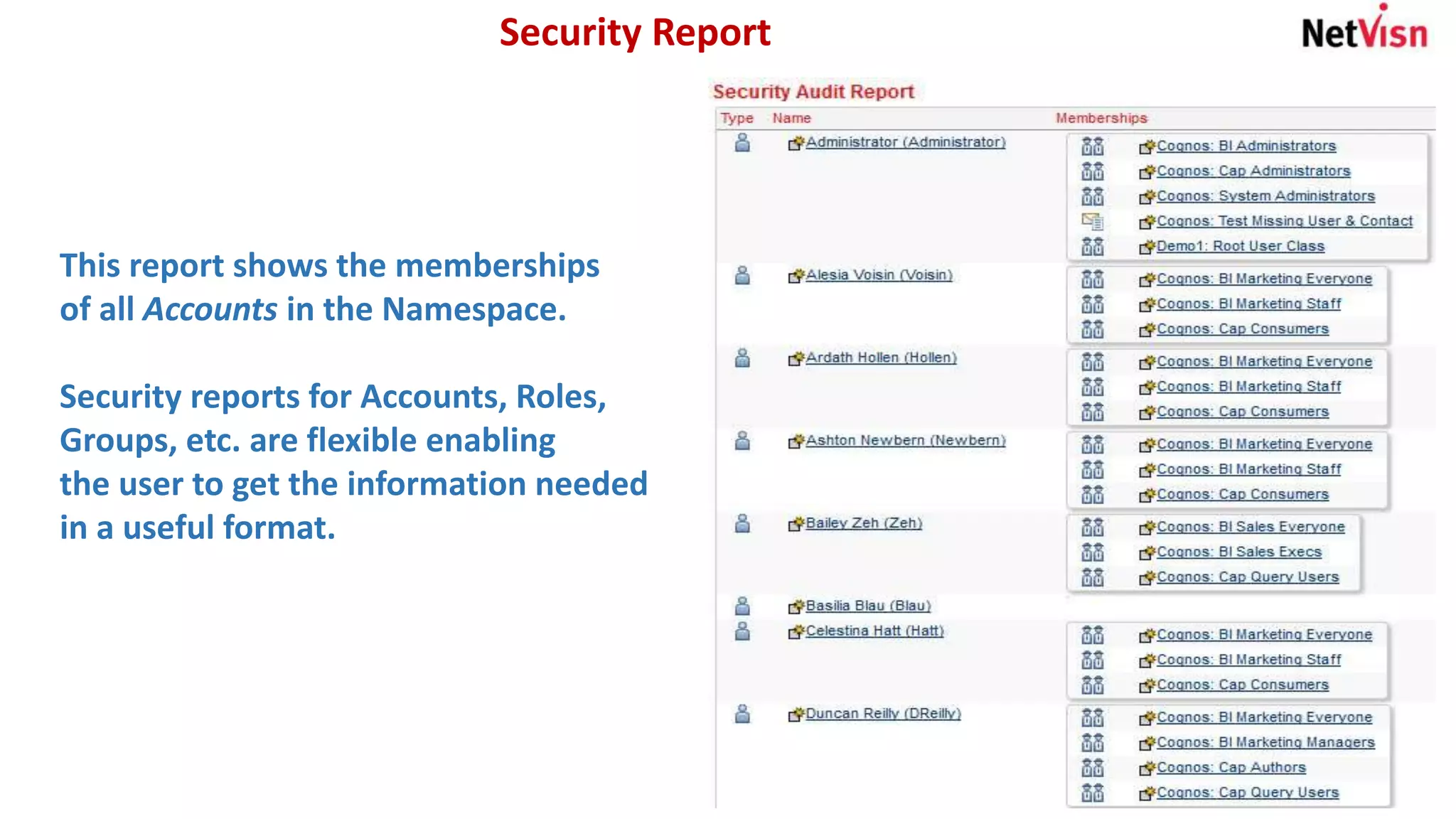
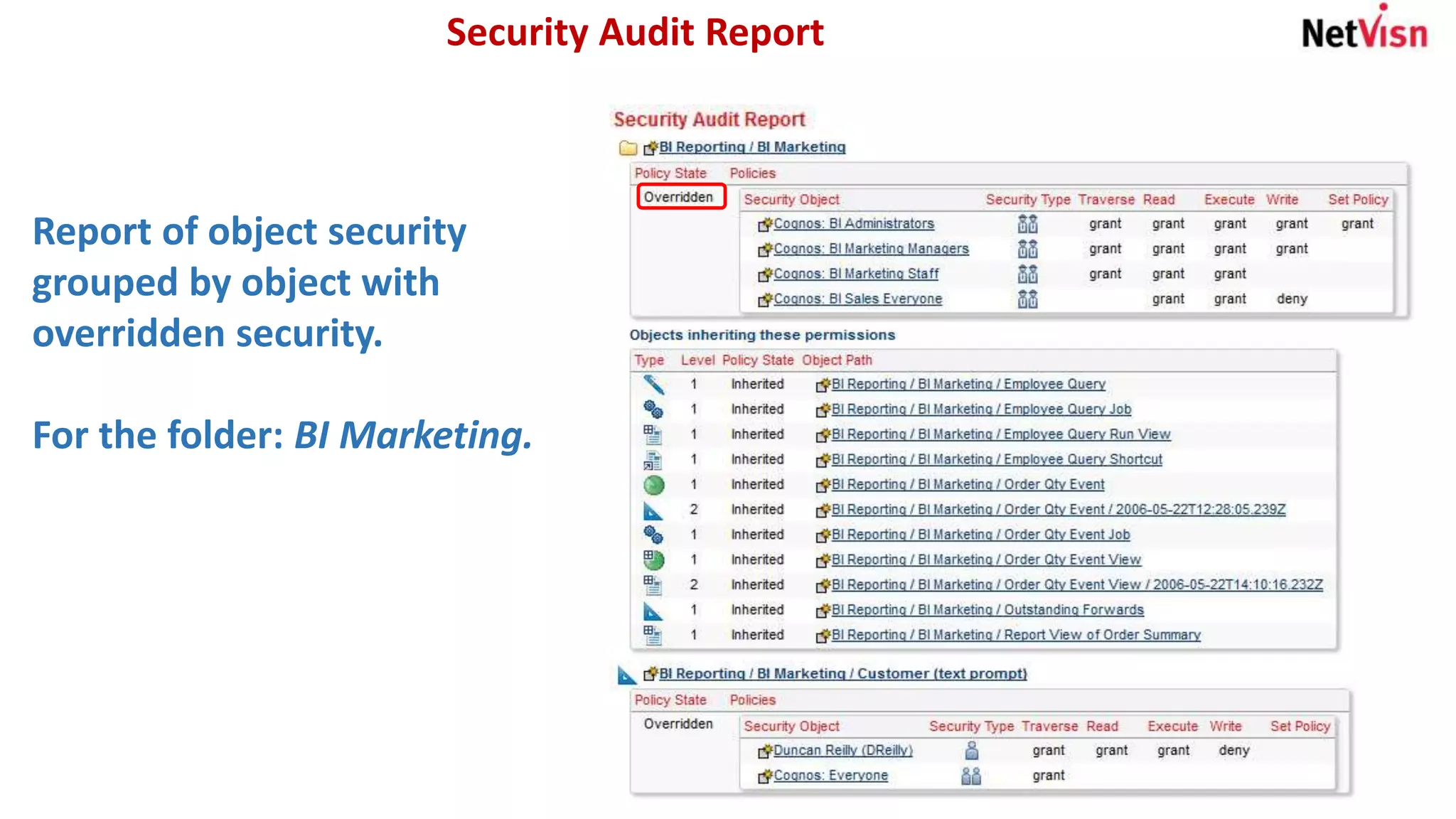
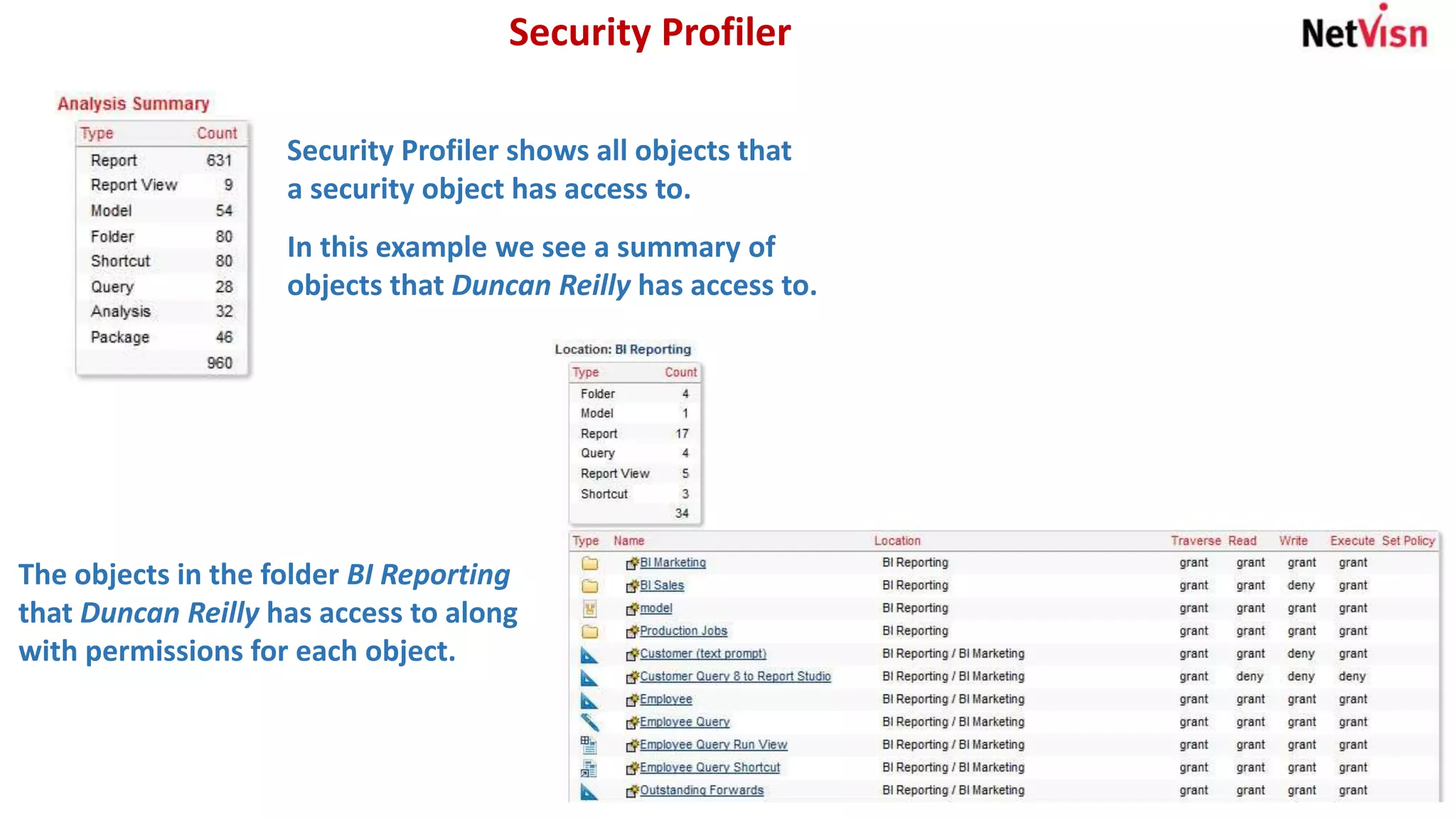
The document outlines various security reports, focusing on roles, memberships, and access for accounts within a namespace. It includes flexible reporting options for analyzing memberships by roles or groups and provides details on object security, particularly for individuals like Duncan Reilly. Additionally, it features a security profiler that highlights objects accessible to specific users along with their permissions.