Embed presentation
Download as PDF, PPTX



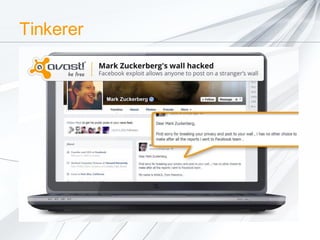





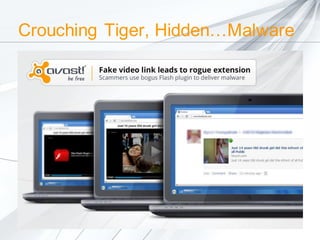
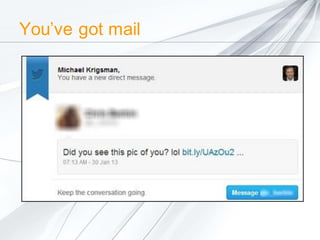
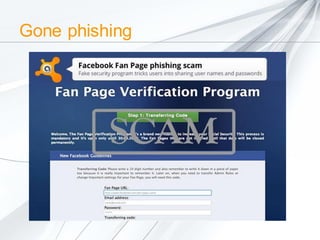

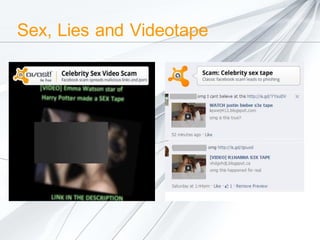



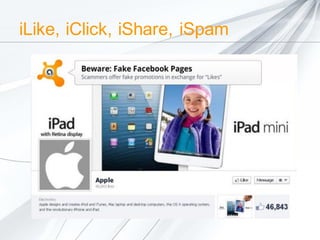



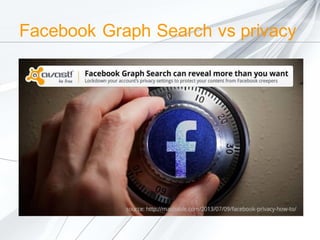
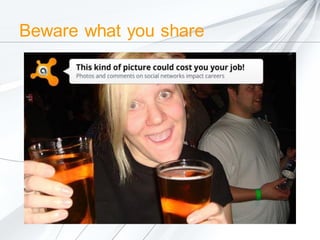





The document discusses security concerns surrounding social media, emphasizing the risks of sharing personal information and the actions of hackers and cybercriminals. It includes quotes about online safety, particularly relating to password management. Various Avast software products for security and protection are mentioned.



























